Detect Exploitation Attempts With Qualys XDR (Beta)
Last updated on: December 18, 2022
Table of Contents
The recently announced Log4JShell / CVE-2021-44228 exploit is the latest reminder of why it’s so important to maintain an enterprise-wide view of your security posture.
The heart of the exploit centers around misuse of the JNDI lookup function built into log4j.
Impact: There are multiple proofs of concept exploits circulating making this vulnerability easy for both skilled and novice attackers to leverage.
How do I know if my systems are being attacked? Exploit attempts leveraging JNDI lookups are logged by perimeter devices such as firewalls, web proxies and web application firewalls logs in the requested URL. This means that a good log management program can act as the enterprise’s early warning system to alert the enterprise of suspicious behavior.
While Qualys XDR is still in beta, customers using this tool can leverage the capabilities below to identify and generate alerts for log4j related exploit attempts. Qualys is also maintaining a blog post dedicated to this issue for customers seeking to learn how Qualys can proactively identify and remediate vulnerable systems. Additionally, the Qualys EDR team has prepared detailed information on how Qualys EDR can identify and prevent log4j exploits.
Log4Shell Event Search:
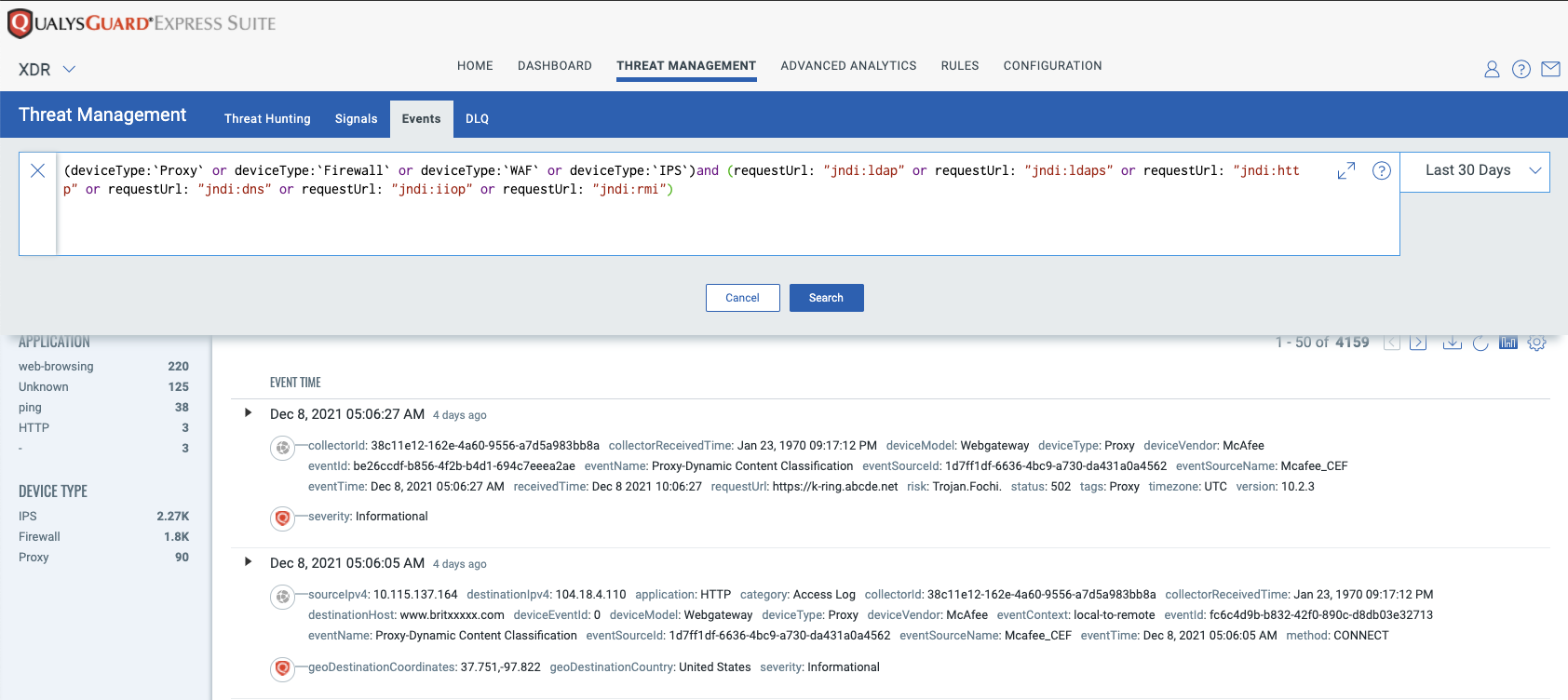
Qualys XDR beta customers can perform real-time searches using the following QQL query to find suspicious events related to Log4Shell/CVE-2021-44228. Using this method, the enterprise can determine not only if an exploit attempt is happening now but also confirm if any attempts had been recorded even before the vulnerability had been announced by going back in time and searching historical events:
(deviceType:`Proxy` or deviceType:`Firewall` or deviceType:`WAF` or deviceType:`IPS`) and (requestUrl: "jndi:ldap" or requestUrl: "jndi:ldaps" or requestUrl: "jndi:http" or requestUrl: "jndi:dns" or requestUrl: "jndi:iiop" or requestUrl: "jndi:rmi")
QQL modifiers for sourceIpv4 / sourceDomain can be added to search the string above for targeted suspicious sources of interest:
and sourceIpv4: "10.10.10.10"
and sourceDomain: "badguy.com"These QQL search terms can of course be used as standalone terms to show all logged events from the IP / domain of interest.
Proactive alert generation:
Beta customers can reach out to xdr@qualys.com for targeted XDR rules for Log4Shell activity.
Additionally, XDR custom correlation rules can be easily and quickly created using the known exploit URL conditions by leveraging the XDR Rule Editor.
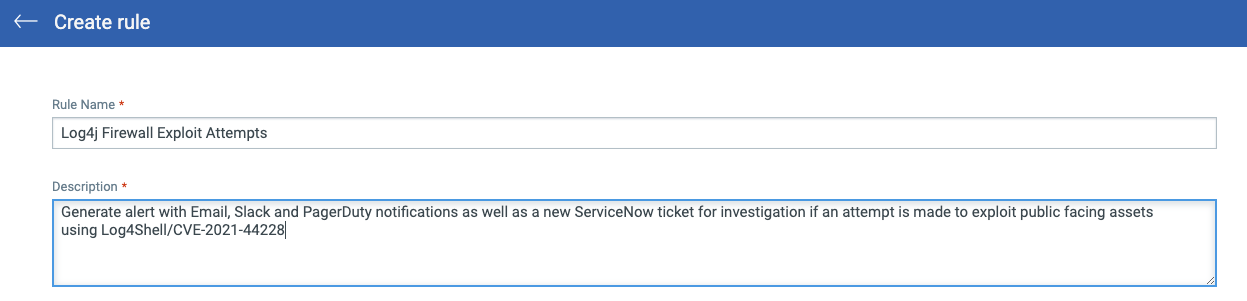
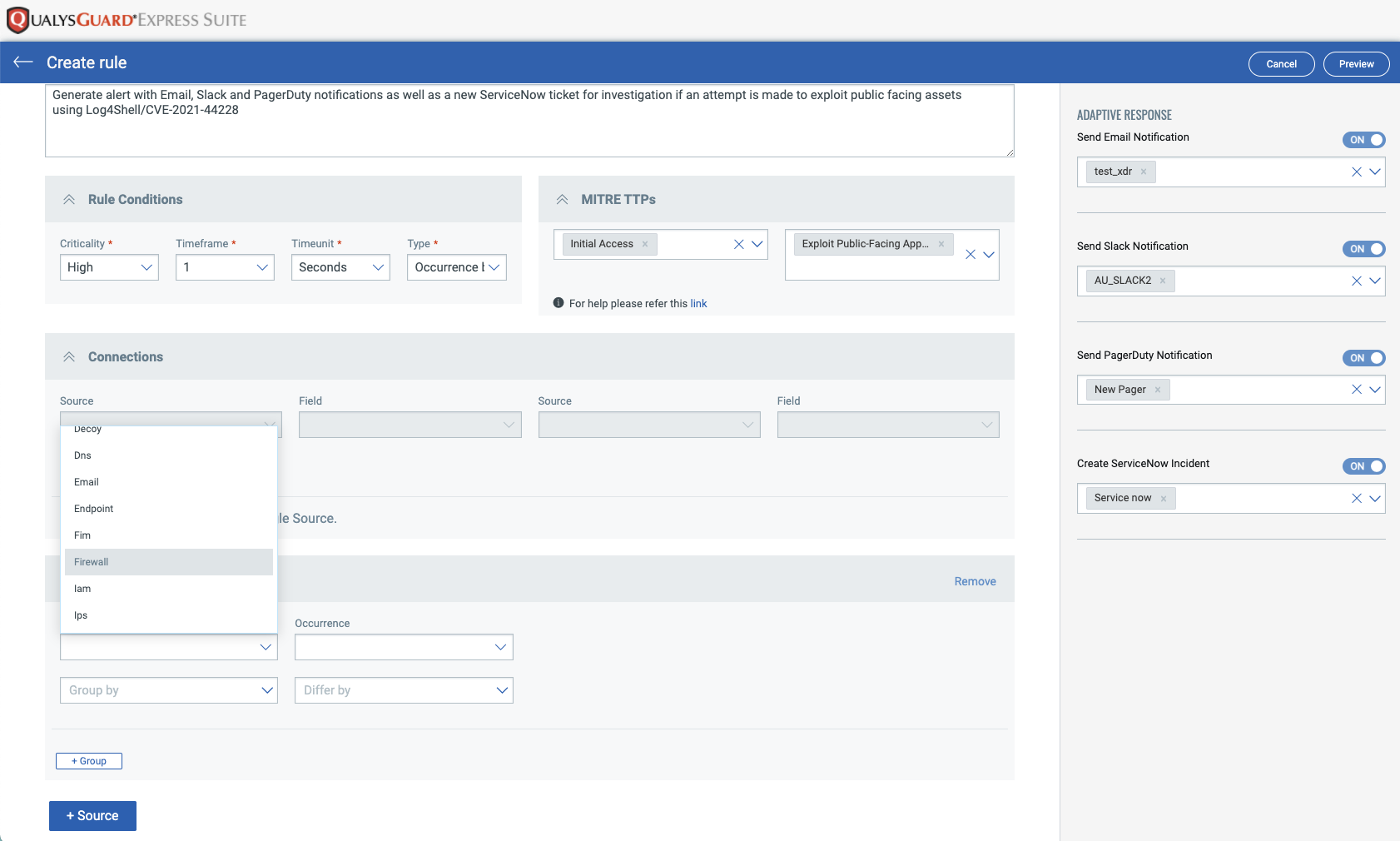
Simply go to XDR -> Rules -> New Rule to create the new rule. Start by giving the rule a descriptive name and meaningful description:
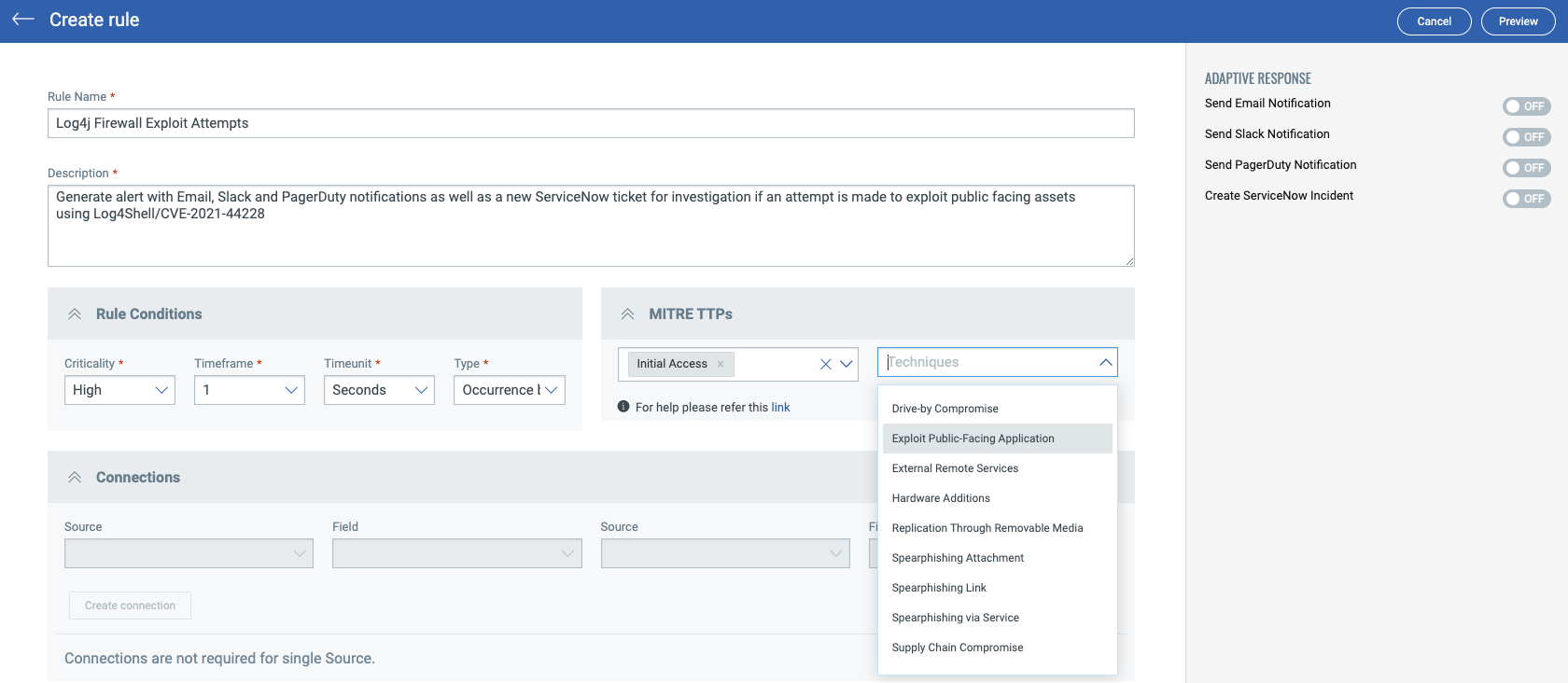
The intuitive editor screens allow the user to add rule conditions matching known exploit information, including optionally specifying the MITRE ATT&CK mapping for this alert:
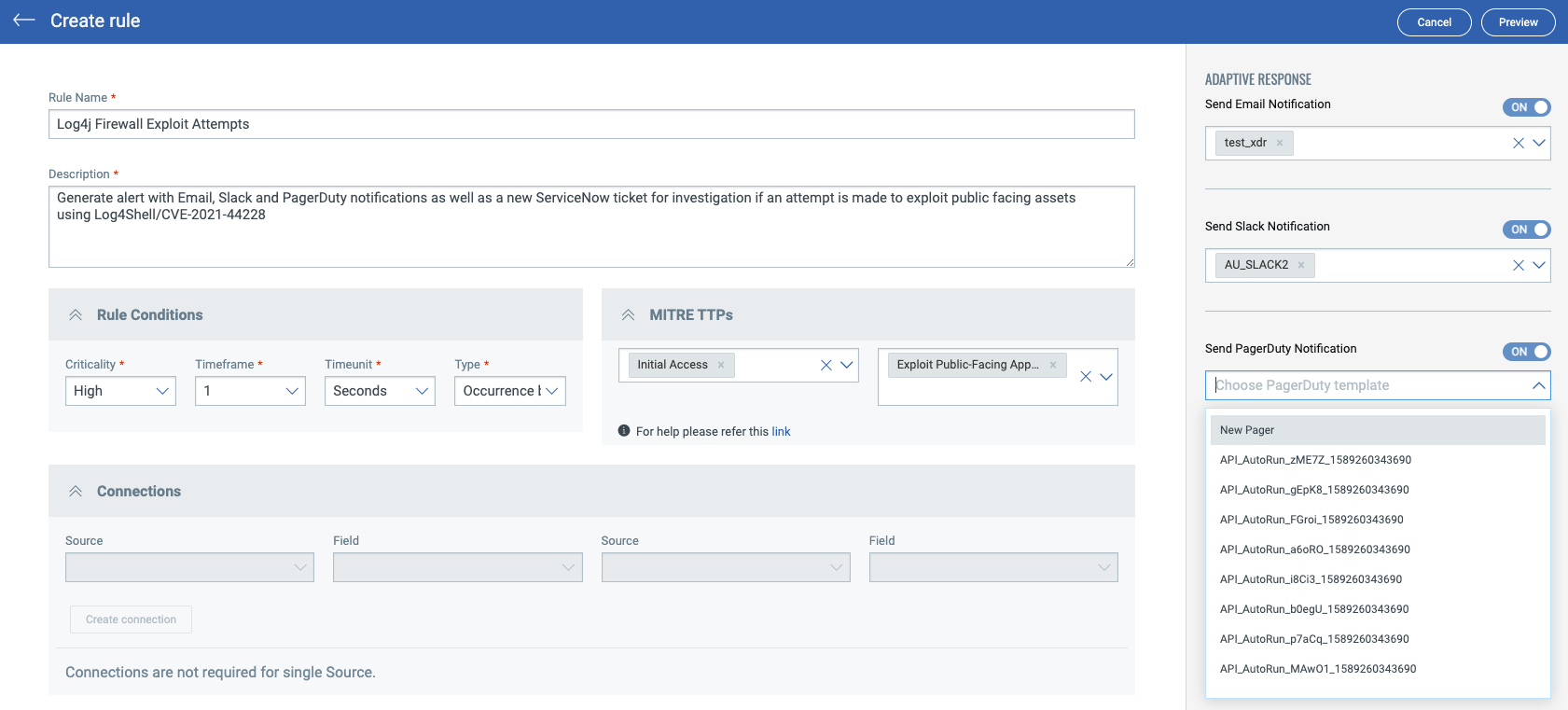
XDR also includes several automated response options (Email, Slack, PagerDuty and ServiceNow) which can be easily assigned using pre-existing templates or through creating a new template. This can be used to generate an alert to the appropriate teams including opening a ServiceNow incident ticket automatically when the rule fires.
Next, select the log source – in this case, we want to ensure our perimeter firewalls report on any exploit attempts witnessed.
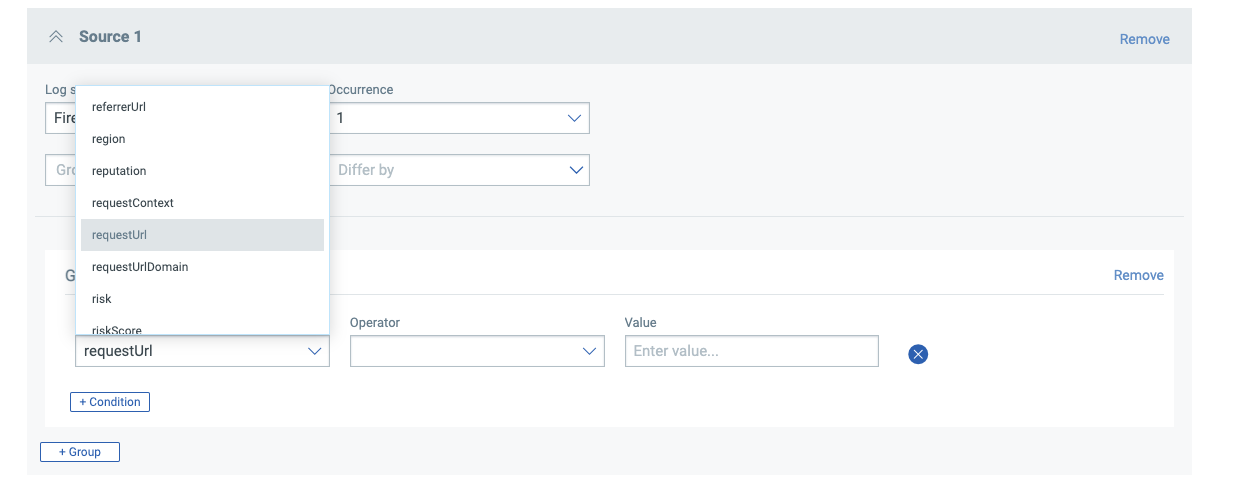
Now we can begin to build out the rule using easy and intuitive pulldown menus to build out the conditions:
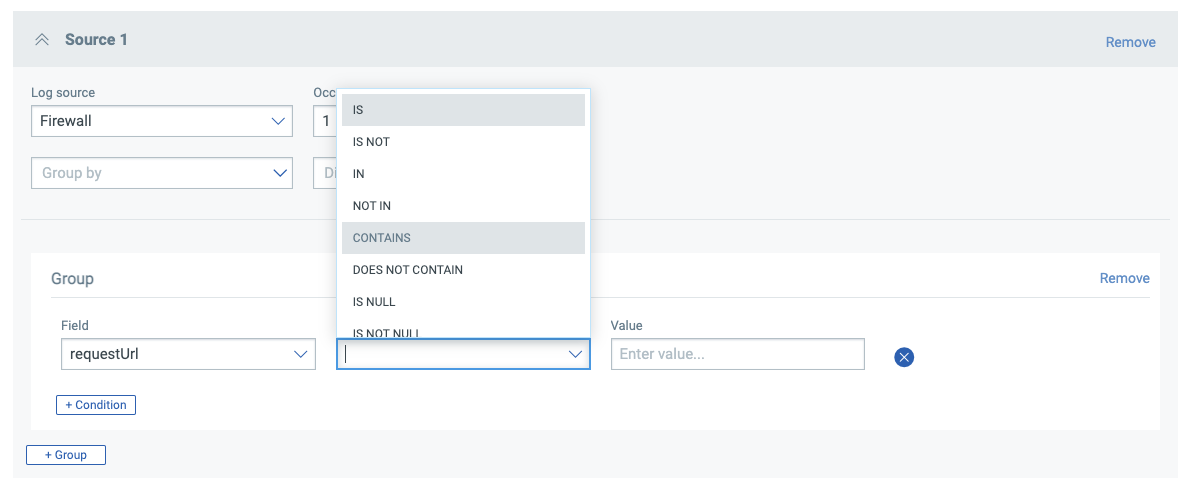

Once our conditions are defined, clicking Preview (top right) will show the final rule and allow us to save this into the rule library:
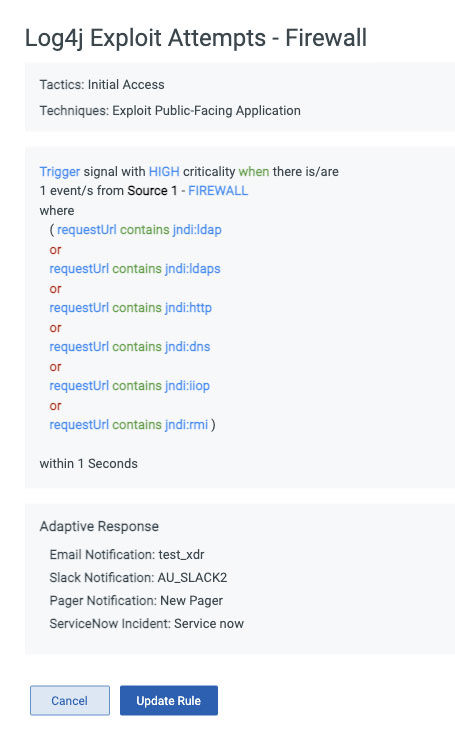
Once saved, the rule can be easily enabled:
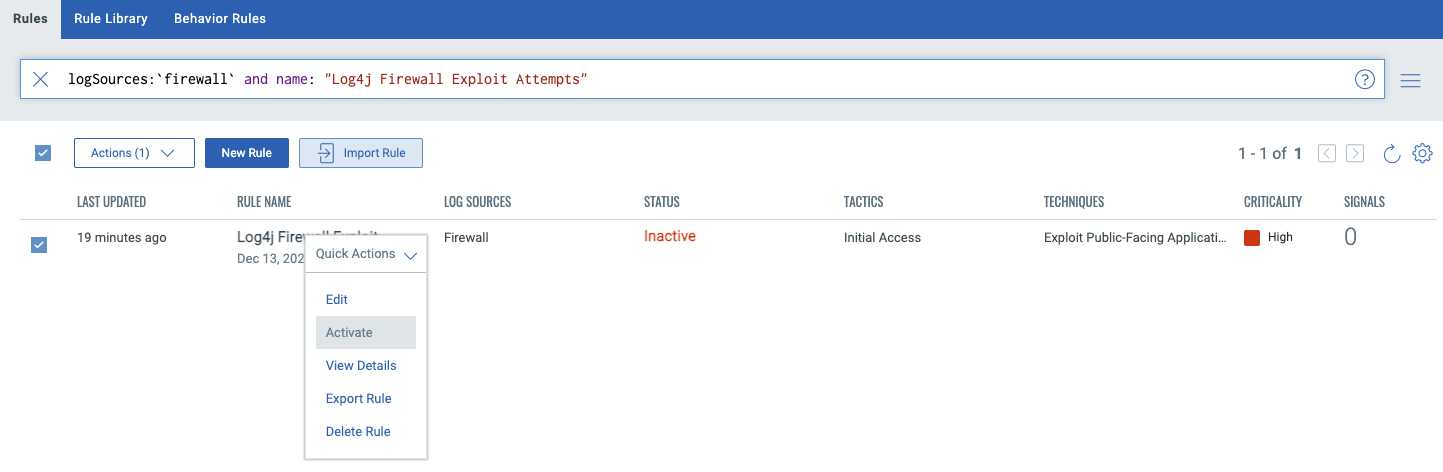
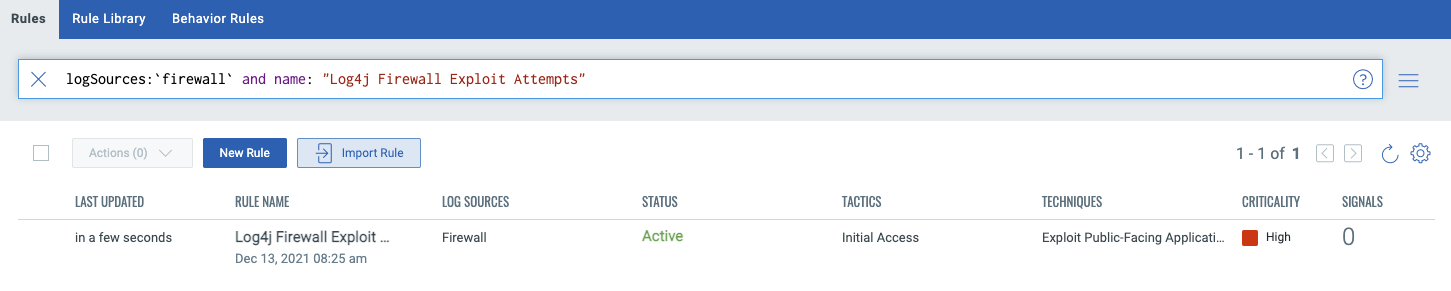
At this point, our rule is now active and any incoming exploit attempts will create signals in XDR as well as associated alerts to the appropriate personnel to ensure any active exploits are quickly investigated and remediated. This same process can be enabled for proxies and web application firewalls as well; this is entirely dependent upon which devices are deployed in the environment.
Advanced Topics:
Exclusions:
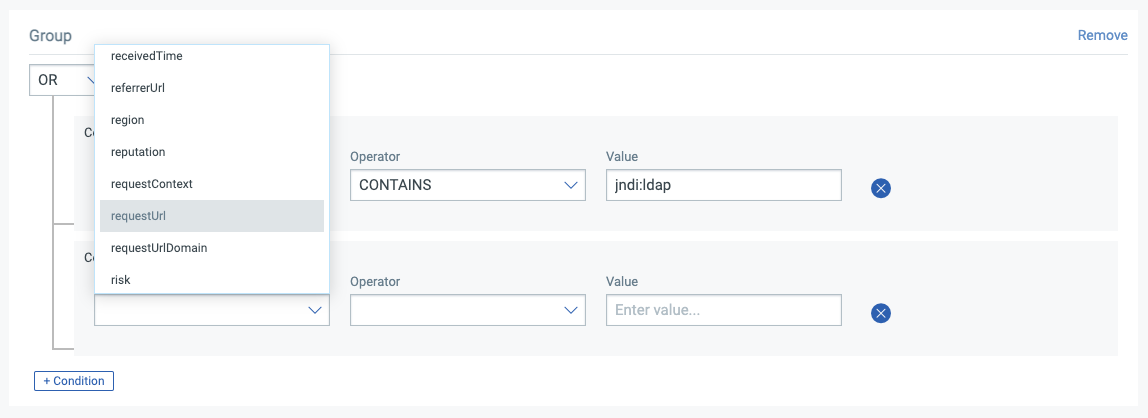
Exclusions can be added to the example rule discussed above by adding an additional condition group in the Rule Editor as shown below:
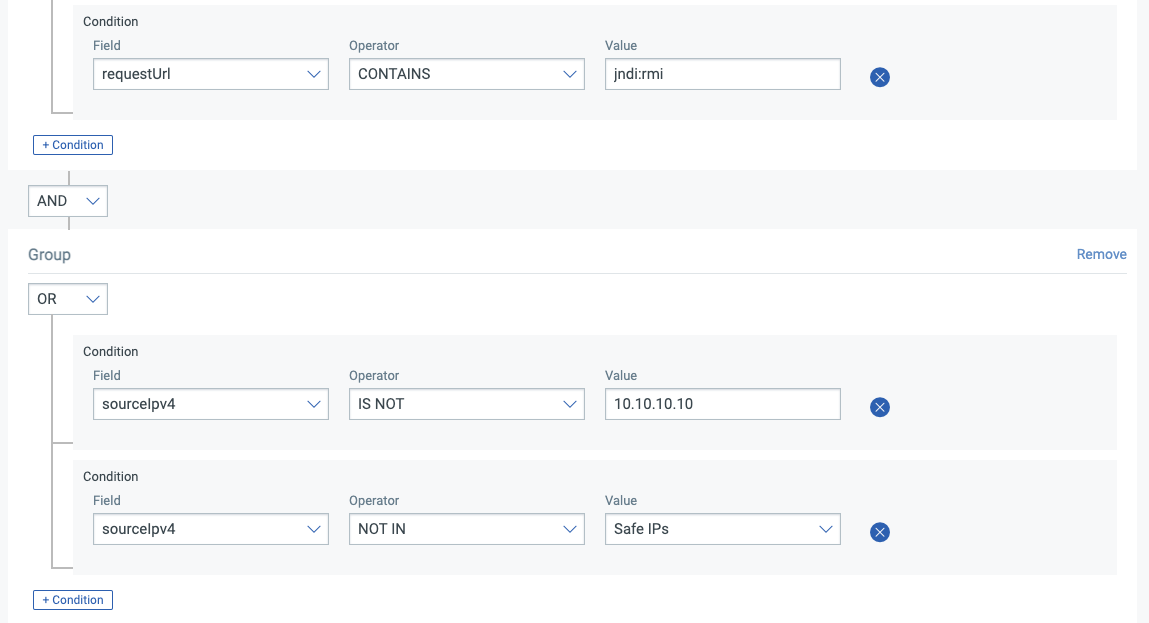
Individual IPs can be added to the allow list. Lists of allowed IPs can also be populated. This is helpful to ensure that the infrastructure being used to find vulnerable systems doesn’t trigger false positive alerts.
Threat Intelligence:
Several commercial threat intelligence providers have added known attack infrastructure associated with Log4JShell/CVE-2021-44228 to their standard threat feeds. This provides the ability to correlate ingested logs against a large number of known indicators (IP address, domain, etc) and to automatically adjust correlation as the provider adds updated indicators.
XDR includes the ability to consume threat feeds natively for automatic alert generation in several formats; for details on XDR’s threat intelligence functions please see the Online Help menu on the XDR home page.
Beta customers who have questions about this article or would like assistance on the topics covered please contact xdr@qualys.com.