Microsoft & Adobe Patch Tuesday (January 2022) – Microsoft 126 Vulnerabilities with 9 Critical, Adobe 41 Vulnerabilities, 22 critical
Microsoft Patch Tuesday – January 2022
Microsoft patched 126 vulnerabilities in their January 2022 Patch Tuesday release. Out of these, nine are rated as critical severity. As of this writing, none of the 126 vulnerabilities are known to be actively exploited.
Microsoft has fixed problems in their software including Remote Code Execution (RCE) vulnerabilities, privilege escalation security flaws, spoofing bugs, and Denial of Service (DoS) issues.
Critical Microsoft Vulnerabilities Patched
CVE-2022-21907 – HTTP Protocol Stack Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10. This vulnerability affects Windows Servers configured as a webserver. To exploit this vulnerability an unauthenticated attacker could send a specially crafted packet to a vulnerable server utilizing the HTTP Protocol Stack to process packets. This vulnerability is known to be wormable. Exploitability Assessment: Exploitation More Likely.
CVE-2022-21849 – Windows IKE Extension Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10. This vulnerability affects systems with Internet Key Exchange (IKE) version 2. While at this time the details of this vulnerability are limited, a remote attacker could trigger multiple vulnerabilities when the IPSec service is running on the Windows system without being authenticated. Exploitability Assessment: Exploitation Less Likely.
CVE-2022-21846 – Microsoft Exchange Server Remote Code Execution Vulnerability
This vulnerability was discovered and reported to Microsoft by National Security Agency (NSA). This vulnerability has a CVSSv3.1 score of 9.0/10. This vulnerability’s attack is limited at the protocol level to a logically adjacent topology. This means it cannot simply be done across the internet, but instead needs something specifically tied to the target. Good examples would include the same shared physical network (such as Bluetooth or IEEE 802.11), logical network (e.g. local IP subnet), or from within a secure or otherwise limited administrative domain (e.g. MPLS, secure VPN to an administrative network zone). This is common to many attacks that require man-in-the-middle type setups or that rely on initially gaining a foothold in another environment. Exploitability Assessment: Exploitation More Likely.
CVE-2022-21837 – Microsoft SharePoint Server Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.3/10. An attacker can use this vulnerability to gain access to the domain and could perform remote code execution on the SharePoint server to elevate themselves to SharePoint admin. Assessment: Exploitation Less Likely.
CVE-2022-21840 – Microsoft Office Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10. This vulnerability can only be exploited if the user opens a specifically crafted file.
In the case of an email attack, an attacker might take advantage of the vulnerability by emailing the victim a specially constructed file and convincing them to open it.
An attacker might host a website (or utilize a compromised website that accepts or hosts user-provided content) that contains a specially crafted file tailored to exploit a vulnerability in a web-based attack scenario. Exploitability Assessment: Exploitation Less Likely.
Adobe Patch Tuesday – January 2022
Adobe released updates to fix 41 CVEs affecting Adobe Acrobat and Reader, Bridge, Illustrator, InCopy and InDesign. Of these 41 vulnerabilities, 22 are treated as Critical. Adobe has released security updates for Adobe Acrobat and Reader for Windows and macOS. These updates address multiple critical, important, and moderate vulnerabilities. Successful exploitation could lead to arbitrary code execution, memory leak, application denial of service, security feature bypass and privilege escalation.
Discover and Prioritize Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:`50118` OR qid:`91851` OR qid:`91852` OR qid:`91853` OR qid:`91854` OR qid:`110398` OR qid:`110399` OR qid:`376232`)

Respond by Patching
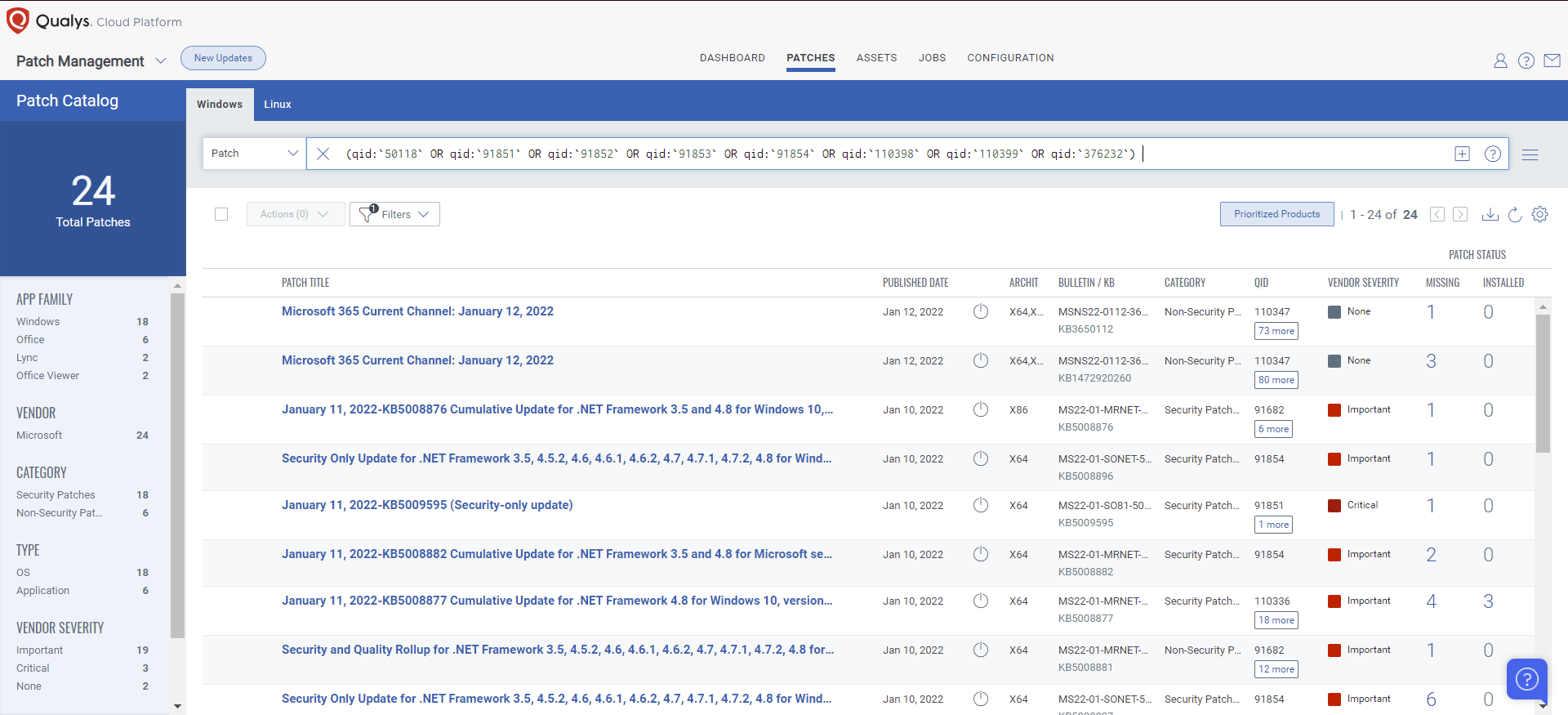
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday.
qid:`50118` OR qid:`91851` OR qid:`91852` OR qid:`91853` OR qid:`91854` OR qid:`110398` OR qid:`110399` OR qid:`376232`)
Patch Tuesday Dashboard
The annual Patch Tuesday dashboard is available in our online Community: Dashboard Toolbox – Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard
Webinar Series: This Month in Vulnerabilities and Patches
To help customers leverage the seamless integration between Qualys VMDR and Patch Management and reduce the median time to remediate critical vulnerabilities, the Qualys Research team is hosting a monthly webinar series:
This Month in Vulnerabilities and Patches.
We will discuss this month’s high-impact vulnerabilities, including those that are part of January 2022 Patch Tuesday. We will walk you through the steps to address the key vulnerabilities using Qualys VMDR and Patch Management.
We will cover the significant vulnerabilities published this month:
- Microsoft Patch Tuesday, January 2022
- Adobe Patch Tuesday, January 2022
Join us live or watch on-demand!

About Patch Tuesday
Patch Tuesday QIDs are published as Security Alerts, typically late in the evening on the day of Patch Tuesday, followed shortly thereafter by query updates for the annual dashboard community article.
Contributor
Debra M. Fezza Reed, Solutions Architect, Subject Matter Expert Dashboards and Reporting