Oh Snap! More Lemmings: Local Privilege Escalation Vulnerability Discovered in snap-confine (CVE-2021-44731)
Table of Contents
- About snap-confine
- Potential Impact of Oh Snap! More Lemmings Vulnerability
- Vulnerability Disclosure Timeline
- Proof of Concept Video of Oh Snap! More Lemmings Exploit
- Vulnerability Summary
- Technical Details of Oh Snap! More Lemmings Vulnerability
- Solution: How to Patch the Oh Snap! More Lemmings Vulnerability
- Discover Vulnerable Linux Servers Using Qualys VMDR
- Detect Impacted Assets with Threat Protection
- Track Vulnerability with VMDR Dashboard
- Vendor References
- Frequently Asked Questions (FAQs)

The Qualys Research Team has discovered multiple vulnerabilities in the snap-confine function on Linux operating systems, the most important of which can be exploited to escalate privilege to gain root privileges. Qualys recommends security teams apply patches for these vulnerabilities as soon as possible.
Free Trial
Quickly Identify Your Vulnerable Web Applications Using Our Cloud Platform
About snap-confine
Snap is a software packaging and deployment system developed by Canonical for operating systems that use the Linux kernel. The packages, called snaps, and the tool for using them, snapd, work across a range of Linux distributions and allow upstream software developers to distribute their applications directly to users. Snaps are self-contained applications running in a sandbox with mediated access to the host system. Snap-confine is a program used internally by snapd to construct the execution environment for snap applications.
Potential Impact of Oh Snap! More Lemmings Vulnerability
Successful exploitation of this vulnerability allows any unprivileged user to gain root privileges on the vulnerable host. Qualys security researchers have been able to independently verify the vulnerability, develop an exploit, and obtain full root privileges on default installations of Ubuntu.
As soon as the Qualys Research Team confirmed the vulnerability, we engaged in responsible vulnerability disclosure and coordinated with both vendor and open-source distributions in announcing this newly discovered vulnerability.
Vulnerability Disclosure Timeline
- 2021-10-27: We sent our advisory and proofs-of-concepts to security@ubuntu.
- 2021-11-10: We sent our advisory and proofs-of-concepts (without the snap-confine vulnerabilities) to secalert@redhat.
- 2021-12-29: We sent a write-up and the patch for the systemd vulnerability to linux-distros@openwall.
- 2022-01-10: We published our write-up on the systemd vulnerability (https://www.openwall.com/lists/oss-security/2022/01/10/2).
- 2022-01-12: Red Hat filed the glibc vulnerabilities upstream (https://sourceware.org/bugzilla/show_bug.cgi?id=28769 and https://sourceware.org/bugzilla/show_bug.cgi?id=28770).
- 2022-01-20: We sent a write-up and the patches for the util-linux vulnerabilities to linux-distros@openwall.
- 2022-01-24: We published our write-up on the util-linux vulnerabilities (https://www.openwall.com/lists/oss-security/2022/01/24/2).
- 2022-01-24: We published our write-up on the glibc vulnerabilities (https://www.openwall.com/lists/oss-security/2022/01/24/4).
- 2022-02-03: We sent our advisory and Ubuntu sent their patches for the snap-confine vulnerabilities to linux-distros@openwall.
- 2022-02-17: Coordinated Release Date (5:00 PM UTC) for the snap-confine
- vulnerabilities.
Proof of Concept Video of Oh Snap! More Lemmings Exploit
Vulnerability Summary
| CVE | Description |
|---|---|
| CVE-2021-44731 | Race condition in snap-confine’s setup_private_mount() |
| CVE-2021-44730 | Hardlink attack in snap-confine’s sc_open_snapd_tool() |
| CVE-2021-3996 | Unauthorized unmount in util-linux’s libmount |
| CVE-2021-3995 | Unauthorized unmount in util-linux’s libmount |
| CVE-2021-3998 | Unexpected return value from glibc’s realpath() |
| CVE-2021-3999 | Off-by-one buffer overflow/underflow in glibc’s getcwd() |
| CVE-2021-3997 | Uncontrolled recursion in systemd’s systemd-tmpfiles |
Technical Details of Oh Snap! More Lemmings Vulnerability
The technical details of Oh Snap! More Lemmings vulnerabilities can be found at https://www.qualys.com/2022/02/17/cve-2021-44731/oh-snap-more-lemmings.txt.
Free Trial
Quickly Identify Your Vulnerable Web Applications Using Our Cloud Platform
Solution: How to Patch the Oh Snap! More Lemmings Vulnerability
Current Qualys customers can search the vulnerability knowledgebase for CVE-2021-44731 to identify all the QIDs and assets vulnerable for this vulnerability.
Other interested parties can start a free Qualys VMDR trial to get full access to the QIDs (detections) for CVE-2021- 44731, where all vulnerable assets can be identified.
Qualys QID Coverage
Qualys is releasing the QIDs in the table below as they become available, starting with vulnsigs version VULNSIGS-2.5.407-2 and in Linux Cloud Agent manifest version lx_manifest-2.5.407.2-1
| QID | Title | VulnSigs Version |
|---|---|---|
| 376419 | Snap-Confine Local Privilege Escalation Vulnerability (Oh Snap! More Lemmings) | VULNSIGS-2.5.407-2 / LX_MANIFEST- VULNSIGS-2.5.407.2-1 |
Discover Vulnerable Linux Servers Using Qualys VMDR
The following instructs current Qualys customers on how to detect Oh Snap! More Lemmings in their environment.
Identify Assets Running Ubuntu Operating System
The first step in managing this critical vulnerability and reducing risk is identification of all assets running Ubuntu OS. Qualys VMDR makes it easy to identify such assets.
operatingSystem.name:”Ubuntu”
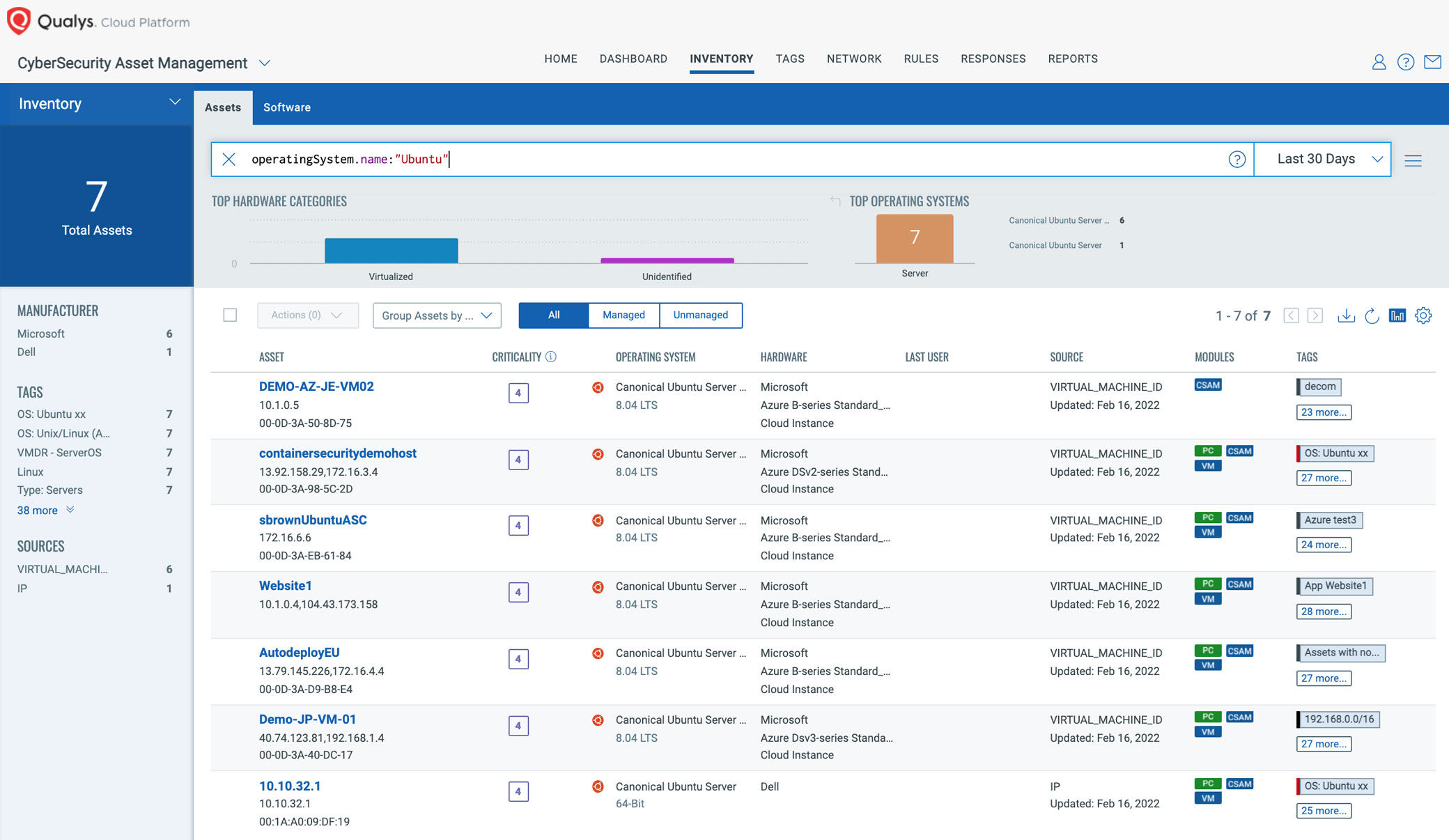
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’; let’s say: “Ubuntu Systems”. This helps by automatically grouping existing hosts with the above vulnerabilities as well as any new assets that spin up in your environment. Tagging makes these grouped assets available for querying, reporting, and management throughout Qualys Cloud Platform.
Prioritize Based on RTIs
Using Qualys VMDR, the Oh Snap! More Lemmings vulnerability can be prioritized using the following real-time threat indicators (RTIs):
Predicted_High_Risk
Privilege_Escalation
Easy_Exploit
High_Lateral_Movement
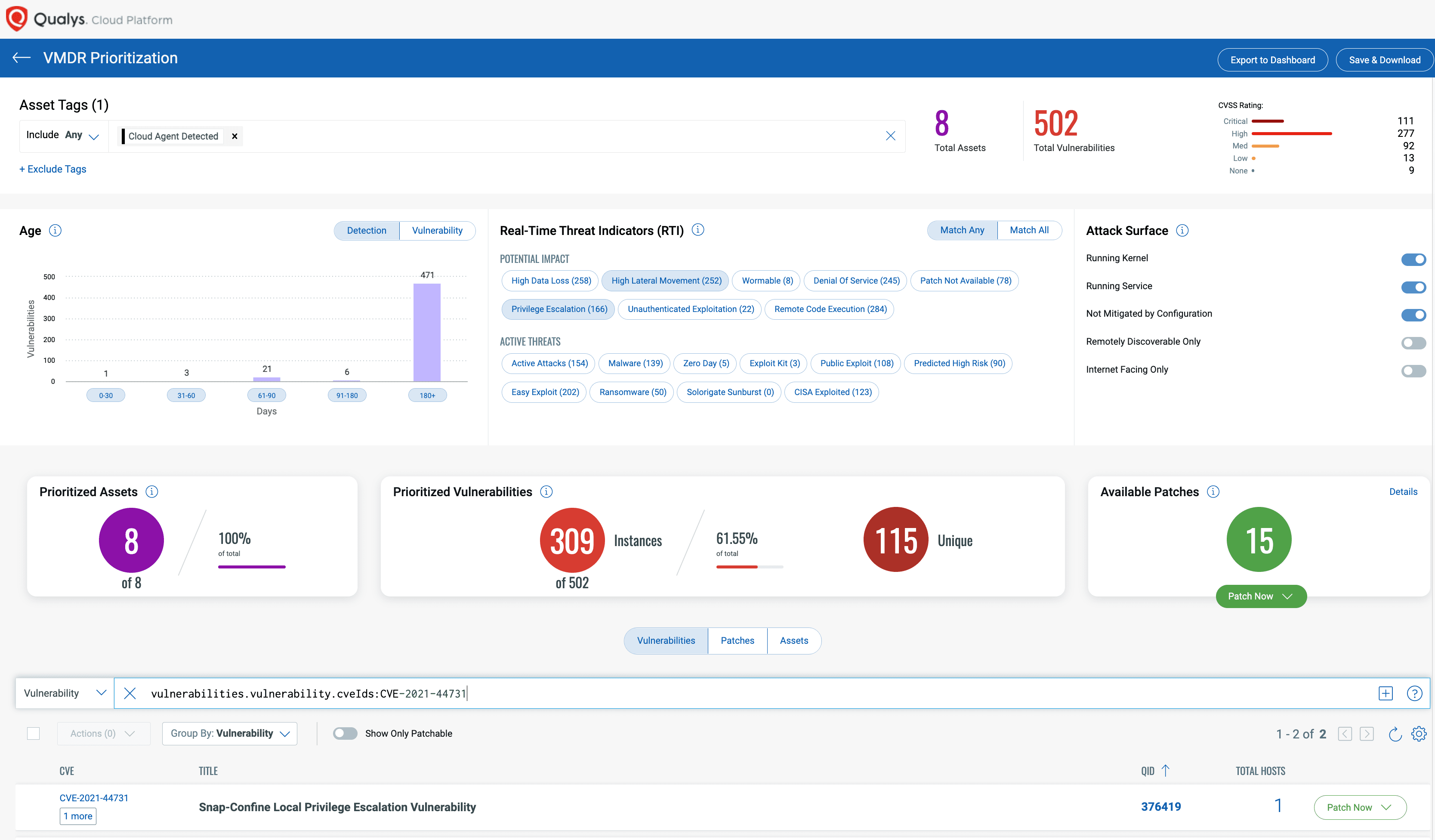
Patch With Qualys VMDR
We expect vendors to release patches for this vulnerability in the short term. Qualys Patch Management can be used to deploy those patches to vulnerable assets, when available.
Using the same prioritization based on RTI method as described above, customers can use the “patch now” button found to the right of the vulnerability to add Oh Snap! More Lemmings to a patch job. Once patches are released, Qualys will find the relevant patches for this vulnerability and automatically add those patches to a patch job. This will allow customers to deploy those patches to vulnerable devices, all from Qualys Cloud Platform.
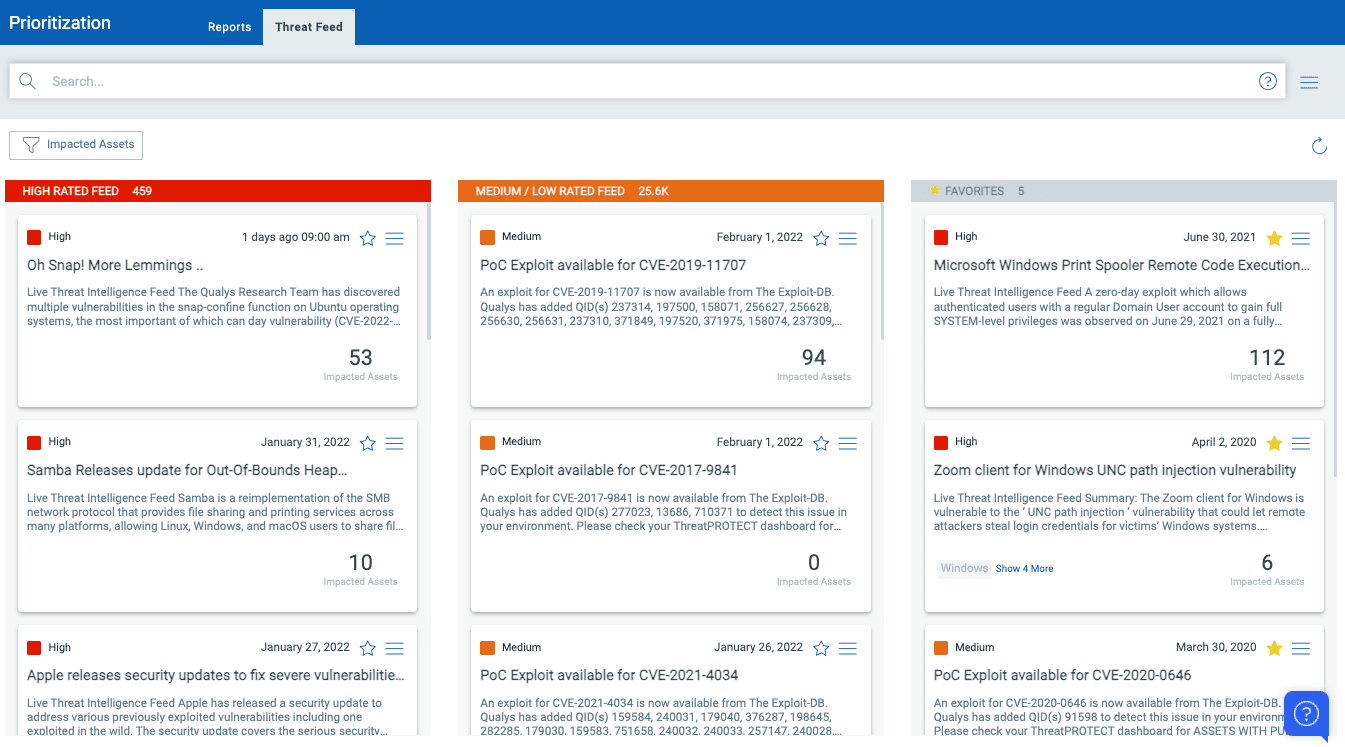
Detect Impacted Assets with Threat Protection
Qualys VMDR also enables you to automatically map assets vulnerable to Oh Snap! More Lemmings vulnerabilities using Threat Protect.
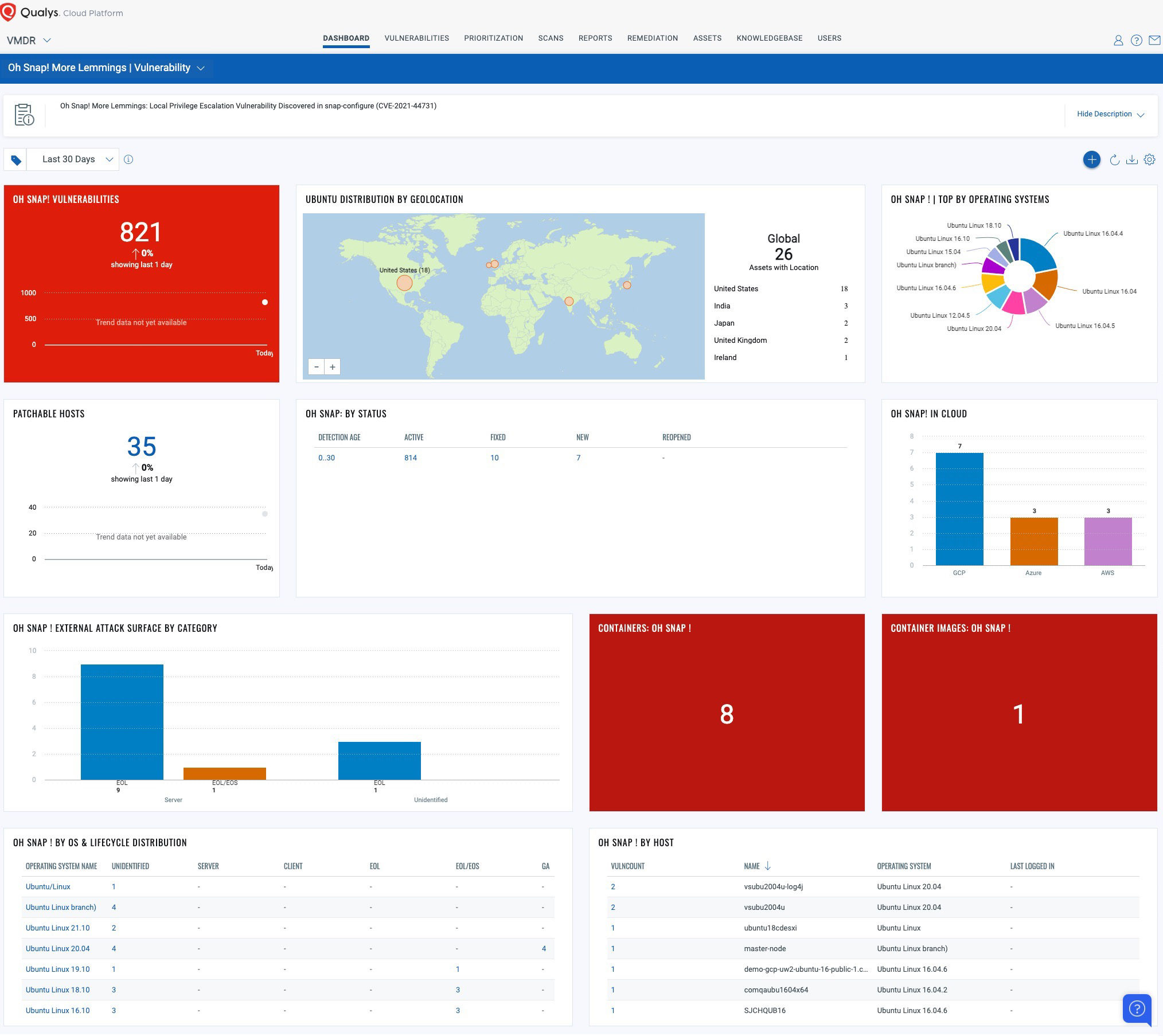
Track Vulnerability with VMDR Dashboard
With VMDR Unified Dashboard, you can track this vulnerability, impacted hosts, their status, and overall management in real time. With trending enabled for dashboard widgets, you can keep track of these vulnerability trends in your environment using the “Oh Snap! More Lemmings” Dashboard.
Vendor References
https://www.qualys.com/2022/02/17/cve-2021-44731/oh-snap-more-lemmings.txt
Frequently Asked Questions (FAQs)
Will the Qualys Research Team publish exploit code for this vulnerability?
No. Not at this time.
Are there any mitigations for this vulnerability?
No.
Is this vulnerability remotely exploitable?
No. But if an attacker can log in as any unprivileged user, the vulnerability can be quickly exploited to gain root privileges.
Why is the vulnerability named “Oh Snap! More Lemmings Kit”?
This is a pun intended on the name of the vulnerable application snap-confine.
I have snap patch updated to latest 2.54.3. Is Qualys not updated their sig yet as it is still showing vulnerable from the agent.
“Affected Versions:
As of now, all the versions of snap package manager are vulnerable”