AvosLocker Ransomware Behavior Examined on Windows & Linux
AvosLocker is a ransomware group that was identified in 2021, specifically targeting Windows machines. Now a new variant of AvosLocker malware is also targeting Linux environments. In this blog, we examine the behavior of these two AvosLocker Ransomware in detail.
AvosLocker is a relatively new ransomware-as-a-service that was first spotted in late June 2021. The attackers use spam email campaigns as initial infection vectors for the delivery of the ransomware payload. During the encryption, process files are appended with the “.avos” extension. An updated variant appends with the extension “.avos2”. Similarly, the Linux version appends with the extension “.avoslinux”.
After every successful attack, the AvosLocker gang releases the names of their victims on the Dark Leak website hosted on the TOR network and provides exfiltrated data for sale. URL structure: hxxp://avosxxx…xxx[.]onion
The AvosLocker gang also advertises their latest ransomware variants on the Dark Leak website. URL structure: hxxp://avosjonxxx…xxx[.]onion
The gang has claimed, “The AvosLocker’s latest Windows variant is one of the fastest in the market with highly scalable threading and selective ciphers.” They offer an affiliate program that provides ransomware-as-a-service (RaaS) for potential partners in crime.
Recently they have added support for encrypting Linux systems, specifically targeting VMware ESXi virtual machines. This allows the gang to target a wider range of organizations. It also possesses the ability to kill ESXi VMs, making it particularly nasty.
According to deepweb research by Cyble Research Labs, the Threats Actors of AvosLocker ransomware groups are exploiting Microsoft Exchange Server vulnerabilities using Proxyshell, compromising the victim’s network.
CVEs involved in these exploits are CVE-2021-34473, CVE-2021-31206, CVE-2021-34523, and CVE-2021-31207.
Technical Analysis of AvosLocker Windows Variant
Command-Line Options
The following figure shows a sample of Command-Line Options.
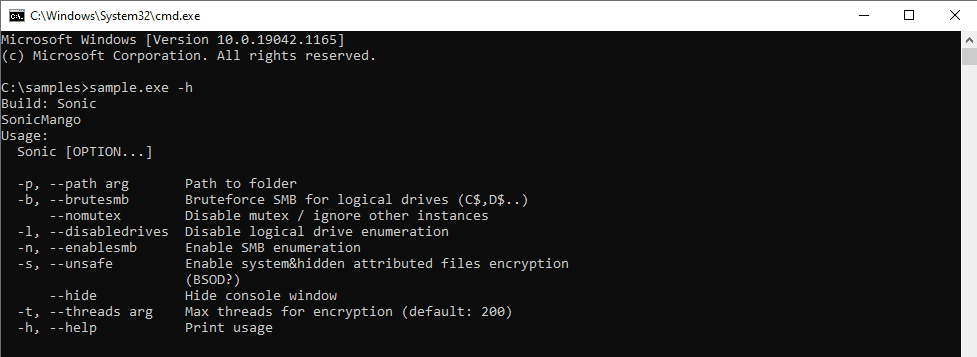
The available options allow for control over items like enabling/disabling SMB brute force, mutex creation, or control over the concurrent number of threads.
If no options are given, the malware runs with default options as shown in figure 2, where it ignores encryption of network drives and SMB share. It runs 200 threads concurrently of its file encryption routine.

While execution, the malware console displays detailed information about its progress on the screen (fig. 3).

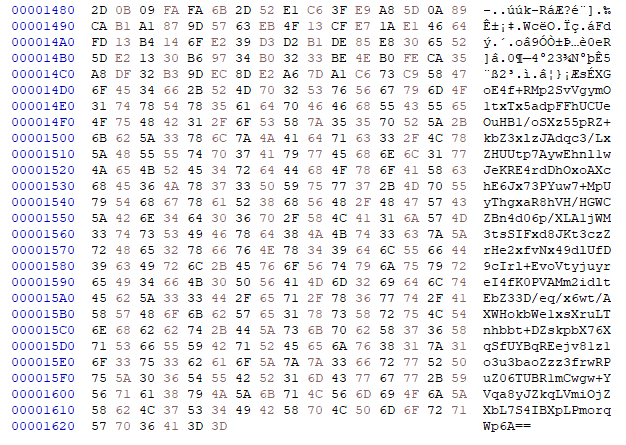
Most of the strings in the malware are kept in the XOR encrypted format. The decryption routines are similar, only registers and keys are different (fig. 4). Strings are decrypted just before their use.

Initially, the malware collects the command line options provided while launching the application (fig. 5).

Then it decrypts the mutex name “Cheic0WaZie6zeiy” and checks whether it is already running or not to avoid multiple instances (fig. 6).

As shown in figure 7, AvosLocker uses multi-threaded tactics. It calls the below APIs to create multiple instances of worker threads into memory and share file paths among multiple threads. Smartly utilizing the computing power of multi-core CPUs.
APIs called:
- CreateIoCompletionPort()
- PostQueuedCompletionStatus()
- GetQueuedCompletionPort()
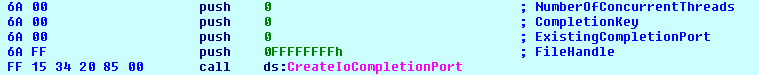
The code creates multiple threads in a loop (fig. 8). The threads are set to the highest priority for encrypting data quickly.
AvosLocker ransomware performs a recursive sweep through the file system (fig. 9), searches for attached drives, and enumerates network resources using API WNetOpenEnum() and WnetEnumResource().

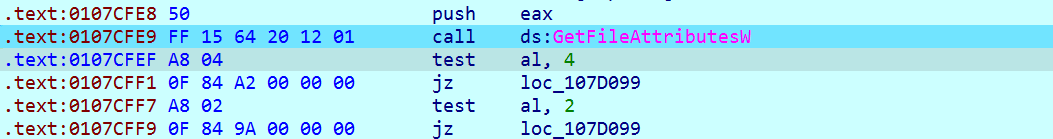
Before selecting the file for encryption, it checks for file attributes and skips it if “FILE_ATTRIBUTE_HIDDEN” or “FILE_ATTRIBUTE_SYSTEM” as shown in figure 10.
Once the file attribute check is passed, it performs the file extension check. It skips files from encryption if its extension gets matched with one of the extensions shown in figure 11.
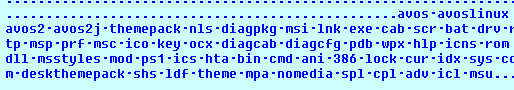
It also contains the list of files and folders that need to be skipped from the encryption (fig. 12).
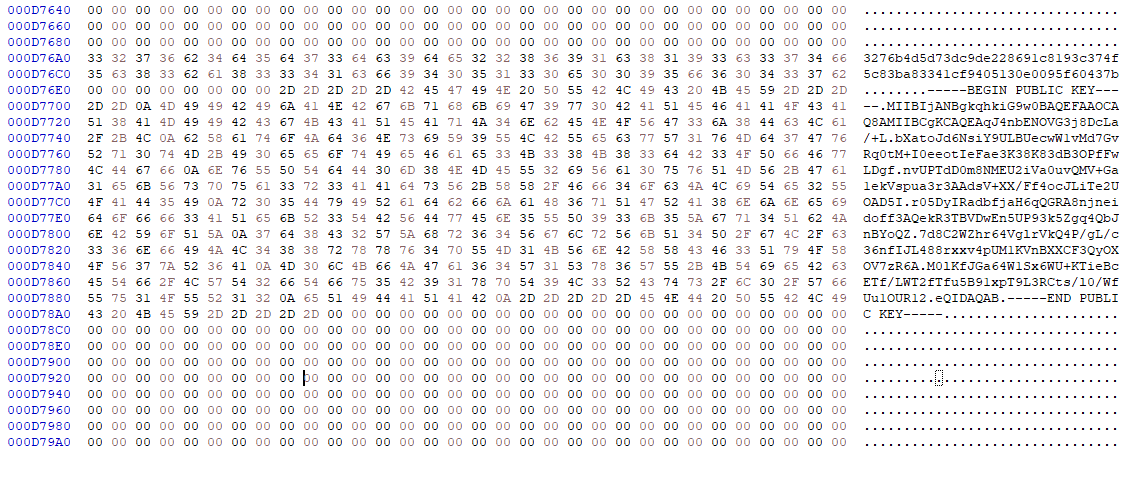
AvosLocker uses RSA encryption, and it comes with a fixed hardcoded ID and RSA Public Key of the attacker (fig. 13).
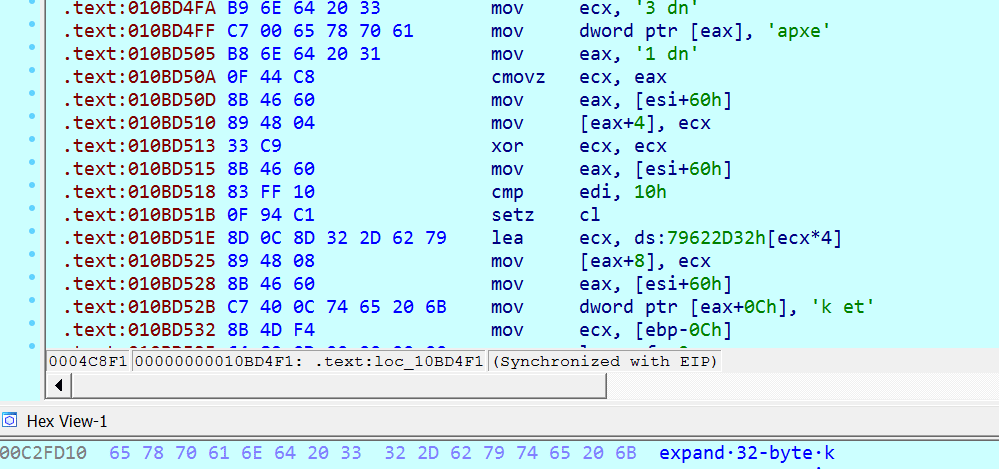
After file encryption using RSA, it uses the ChaCha20 algorithm to encrypt encryption-related information (fig. 14).
It appends this encryption-related information (fig. 15) at the end of the file with Base64 encoded format.
Then it appends the “avo2” extension to the file using MoveFileWithprogressW (fig. 16).

As seen in figure 17, it has appended “avos2” extensions.

It writes a ransom note (fig. 18) named “GET_YOUR_FILES_BACK.txt” to each encrypted directory before encryption of the file.

The ransom note instructs the user to not to shut down the system in case encryption is in progress to avoid file corruption. It asks the victim to visit the onion address with the TOR browser to pay the ransom and to obtain the decryption key to decrypt the application or files.
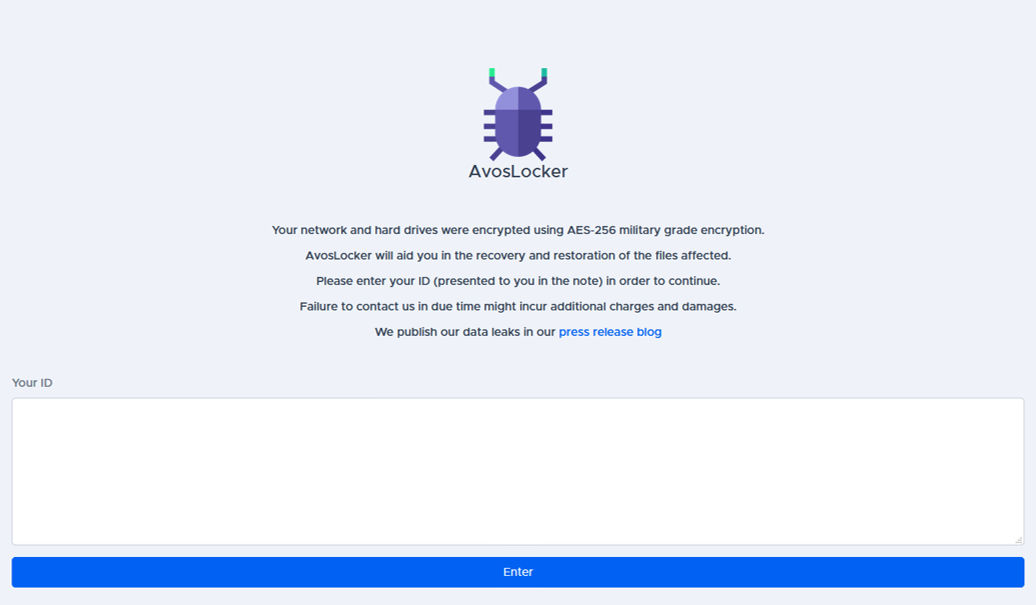
AvosLocker Payment System
After submitting the “ID” mentioned on the ransom note to AvosLocker’s website (fig. 19), the victim will be redirected to the “payment” page.
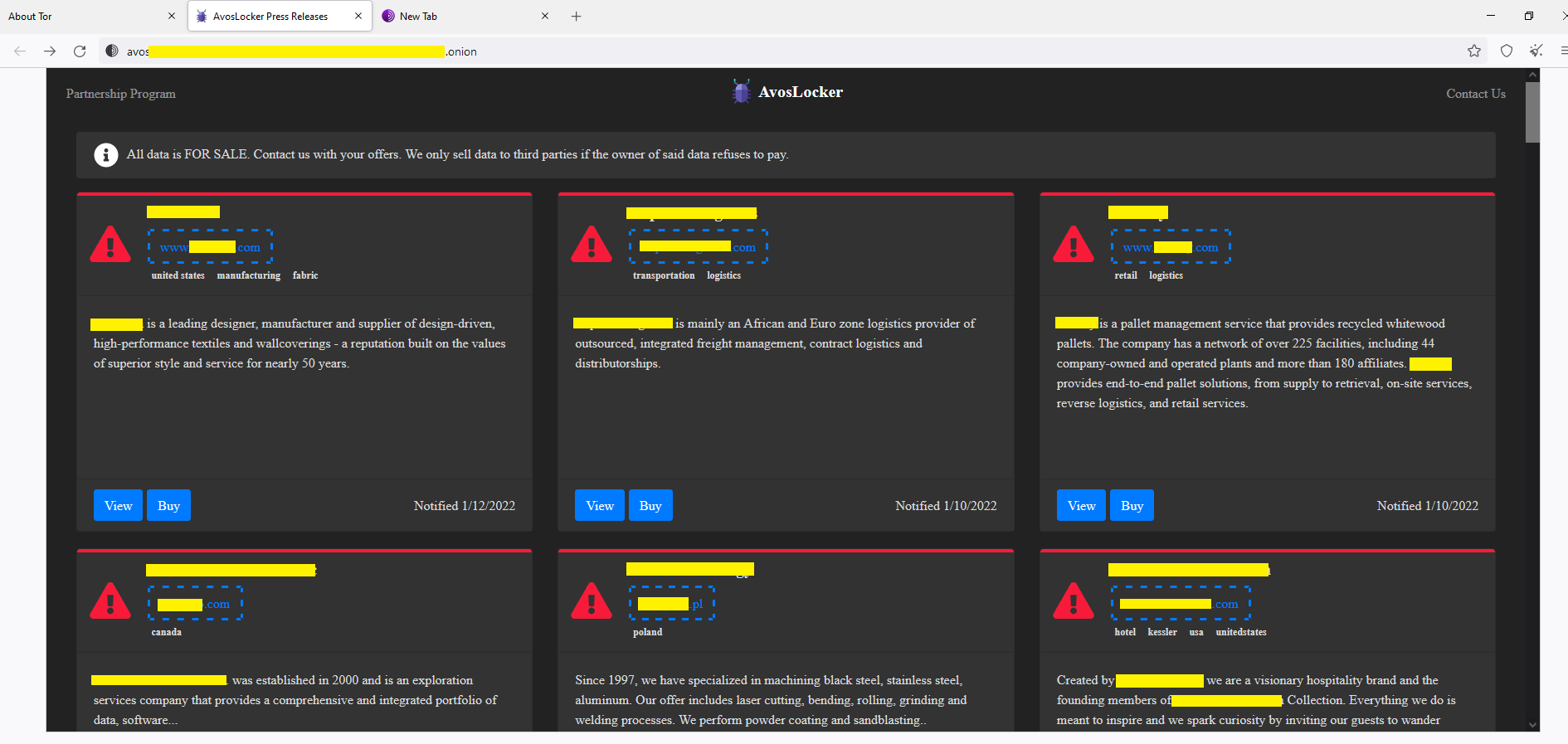
If the victim fails to pay the ransom, the attacker then puts the victim’s data up for sale. Figure 20 shows the list of victims (redacted for obvious reasons) mentioned on the site.
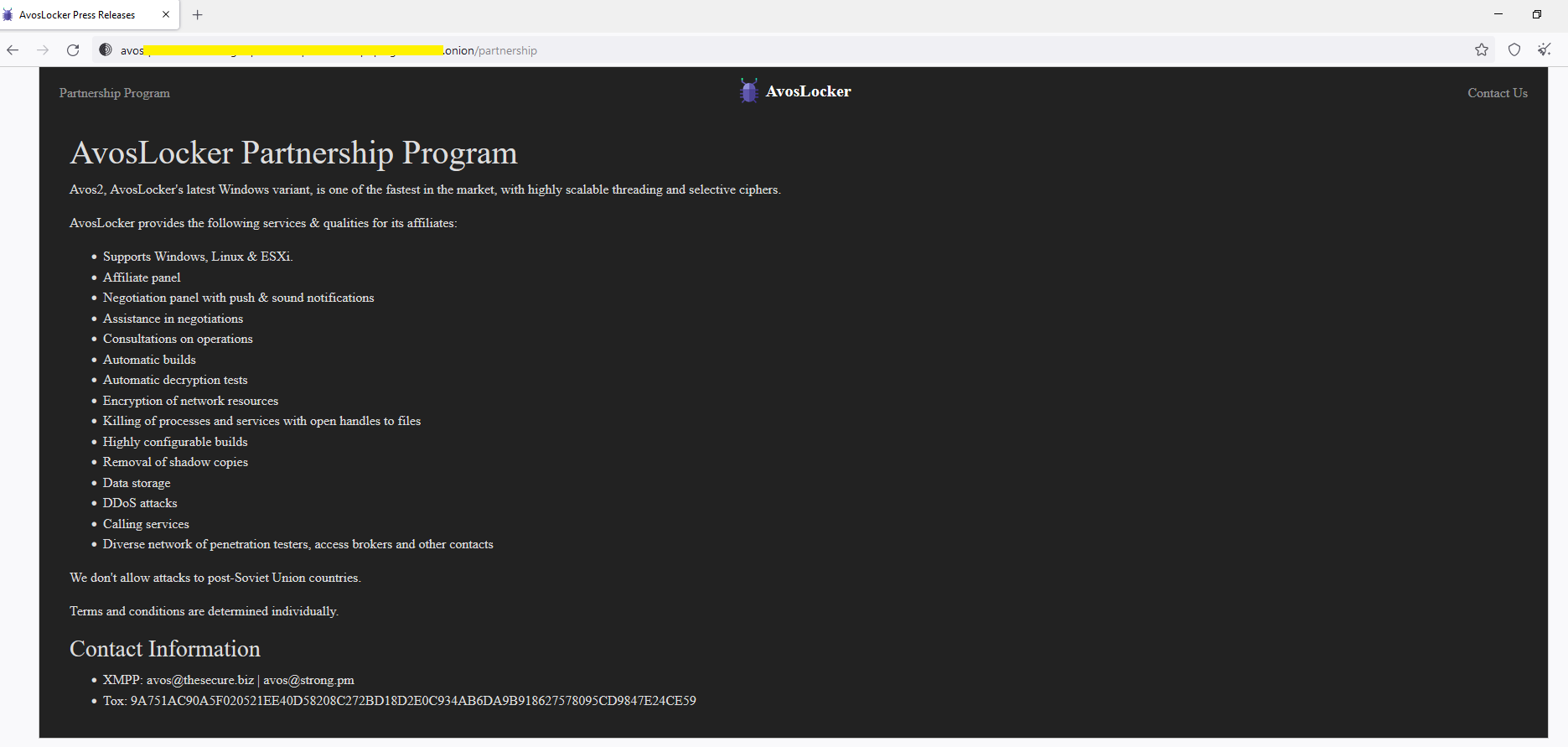
AvosLocker also offers an affiliate program that provides ransomware-as-a-service (RaaS). They provide “helpful” services to clients such as:
- Supports Windows, Linux & ESXi.
- Affiliate panel
- Negotiation panel with push & sound notifications
- Assistance in negotiations
- Consultations on operations
- Automatic builds
- Automatic decryption tests
- Encryption of network resources
- Killing of processes and services with open handles to files
- Highly configurable builds
- Removal of shadow copies
- Data storage
- DDoS attacks
- Calling services
- Diverse network of penetration testers, access brokers and other contacts
Technical Analysis of AvosLocker Linux Variant
In this case, the AvosLocker malware arrives as an elf file. As shown in figure 22, the analyzed file is x64 based Linux executable file.

It’s a command-line application having some command-line options (fig. 23).

The <Thread count> parameter as shown above represents the number of threads that can be created to encrypt files simultaneously. It possesses the capability to kill ESXi VMs based on the parameter provided while executing.
Upon execution, the malware first collects information about the number of threads that need to be created. Then it checks for string “vmfs” in the file path provided as a command-line argument (fig. 24).

After that, it also checks for string “ESXi” in the file path provided as a command-line argument (fig. 25).
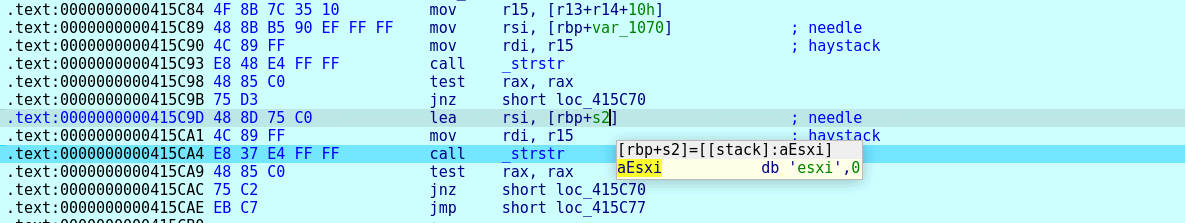
If this parameter is found, then it calls a routine to kill the running ESXi virtual machine (fig. 26).

The command used for killing the ESXi virtual machine is as shown in figure 27.

Further, AvosLocker drops a ransom note file (fig. 28) at the targeted directory.

After that, it starts creating a list of files that must be encrypted. Before adding a file path to the list, it checks whether it is a regular file or not (fig. 29). Only regular files are added to the encryption list.
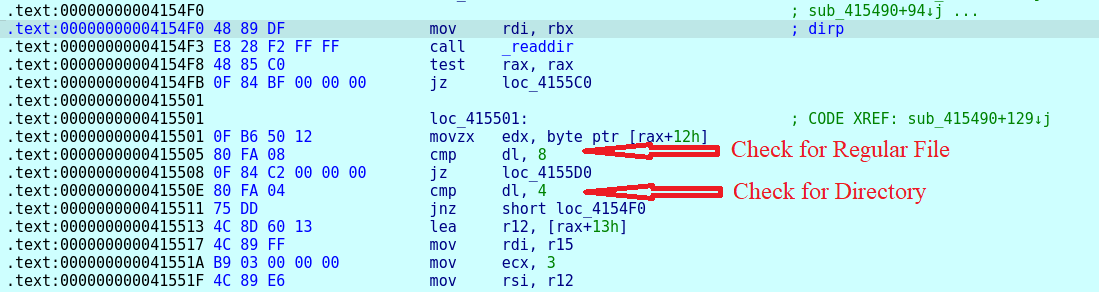
AvosLocker skips the ransom note file and any files with the extension “avoslinux” from adding into the encryption list (fig. 30).

Then it calls the mutex lock/unlock API for thread synchronization as shown in figure 31.
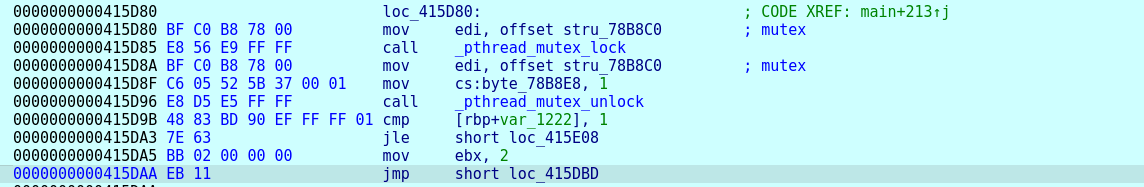
Based on the number of threads specified, it creates concurrent CPU threads (fig. 32). This helps in encrypting different files simultaneously at a very fast speed.

AvosLocker’s Linux variant makes use of Advanced Encryption Standard (AES) and elliptic-curve cryptography (ECC) algorithms for data encryption.
File-related information along with the encryption key used might be encrypted and then encoded with base 64 formats. This encoded information is added at the end of each encrypted file (fig. 33).

Figure 34 shows the malware appending the extension “.avoslinux” to the encrypted file names.
Before starting file encryption, it creates a ransom note named “README_FOR_RESTORE “. The content of this ransom note is shown in figure 35.

The ransom note instructs the victim not to shut down the system in case encryption is in progress to avoid file corruption. It asks the victim to visit the onion address with a TOR browser to pay the ransom and to obtain the decryption key and decryption application.
Indicators of Compromise (IOCs):
Windows: C0A42741EEF72991D9D0EE8B6C0531FC19151457A8B59BDCF7B6373D1FE56E02
Linux: 7C935DCD672C4854495F41008120288E8E1C144089F1F06A23BD0A0F52A544B1
URL: hxxp://avosjon4pfh3y7ew3jdwz6ofw7lljcxlbk7hcxxmnxlh5kvf2akcqjad[.]onion. hxxp://avosqxh72b5ia23dl5fgwcpndkctuzqvh2iefk5imp3pi5gfhel5klad[.]onion
TTP Map:
| Initial Access | Execution | Defense Evasion | Discovery | Impact |
|---|---|---|---|---|
| Phishing (T1566) | User Execution (T1204) | Obfuscated Files or Information (T1027) | System Information Discovery (T1082) | Data Encrypted for Impact (T1486) |
| File and Directory Discovery (T1083) | Inhibit System Recovery (T1490) |