Remediate Your Vulnerable Lenovo Systems with Qualys Custom Assessment and Remediation
Table of Contents
Lenovo disclosed Multi-Vendor BIOS Security Vulnerabilities in September 2022 that affect multiple Lenovo devices. These are high severity vulnerabilities that have the potential of resulting in information disclosure, privilege escalation, and denial of service. Here are the related CVEs:
- CVE-2021-28216 – Tianocore reported a fixed pointer vulnerability in TianoCore EDK II BIOS that may allow an attacker with local access and elevated privileges to execute arbitrary code
- CVE-2022-40137 – A buffer overflow in the WMI SMI Handler in some Lenovo models may allow an attacker with local access and elevated privileges to execute arbitrary code
- CVE-2022-40134 – An information leak vulnerability in the SMI Set BIOS Password SMI Handler in some Lenovo models may allow an attacker with local access and elevated privileges to read SMM memory
- CVE-2022-40135 – An information leak vulnerability in the Smart USB Protection SMI Handler in some Lenovo models may allow an attacker with local access and elevated privileges to read SMM memory
- CVE-2022-40136 – An information leak vulnerability in SMI Handler used to configure platform settings over WMI in some Lenovo models may allow an attacker with local access and elevated privileges to read SMM memory
As part of its remediation efforts, Lenovo has fixed these issues with the latest BIOS updates for impacted devices. Please refer to: Lenovo System Update for Windows 11, 10 & 7 (32-bit, 64-bit) – Desktop, Notebook, Workstation.
How Qualys Can Help
Qualys helps streamline the patching process, enabling cybersecurity practitioners to write custom logic to detect vulnerable assets and remediate them by installing the Lenovo System Update.
Qualys CSAM with External Attack Surface Management
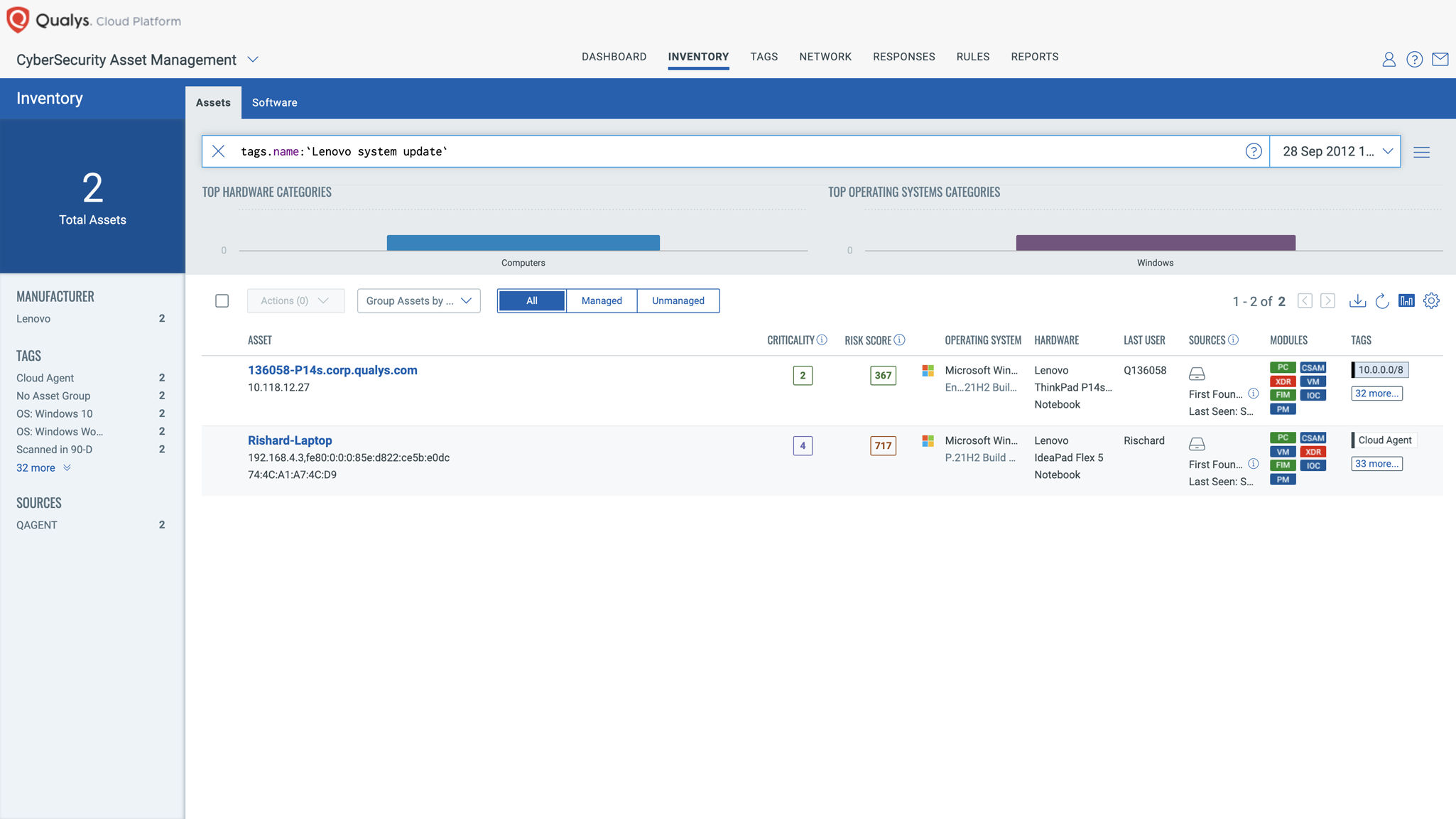
Leverage Qualys Cyber Security Asset Management (CSAM) to create a dynamic tag for all Lenovo assets with operating systems such as Windows 7, 10, and 11 with 32-bit or 64-bit architecture. Use the following Qualys Query Language (QQL) strings:
(operatingSystem.name:'Windows 7' or operatingSystem.name:'Windows 10' or operatingSystem.name:'Windows 11') and (operatingSystem.architecture:`64-Bit` or operatingSystem.architecture:`32-Bit`) and hardware.manufacturer:'Lenovo'
Qualys Custom Assessment and Remediation
Use Qualys Custom Assessment and Remediation to create scripts that check for vulnerable assets based on the BIOS version. Then distribute updates for software, drivers, and BIOS if the vulnerable BIOS version is detected.
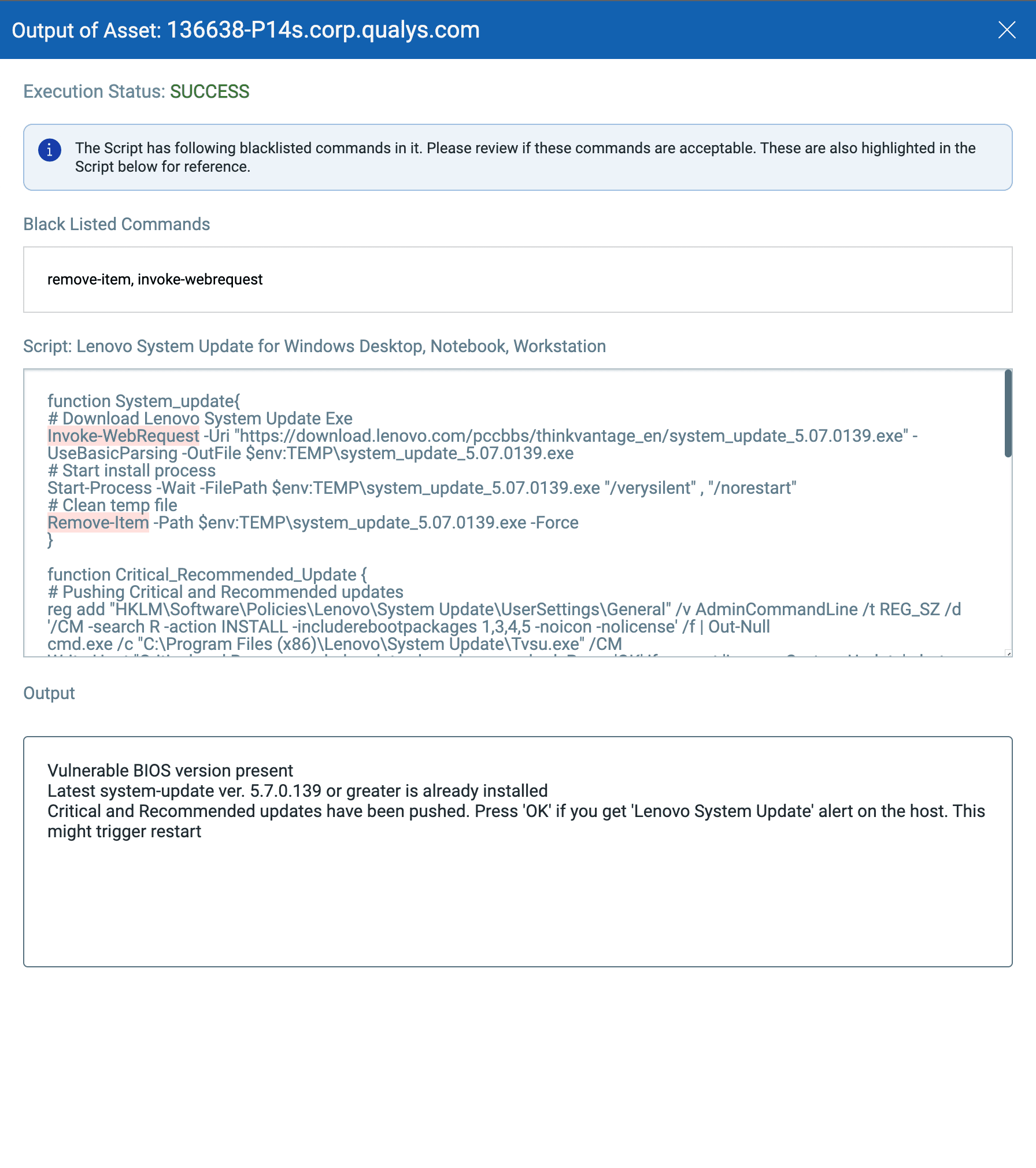
Reference this script under Qualys Script Library on GitHub: Lenovo System Update for Windows Desktop, Notebook, Workstation. This script can be used to:
- Check for vulnerable BIOS version on host
- Check for the latest Lenovo system update version, if a vulnerable BIOS version is detected
- Push the critical and recommended updates based on system update version 5.7.0.139 or greater
- Install the latest system update (i.e. system_update_5.07.0139.exe) and push the Critical and Recommended updates
- Patch and reboot
Add this script under Qualys Custom Assessment and Remediation, and then execute it on the asset tag created above.
Script execution will trigger a job to display the script output on each host.
Conclusion
Using Qualys CSAM’s exhaustive inventory information and our no-code scripting capabilities, it’s easy to remediate vulnerable Lenovo devices.
If your organization is not yet a Qualys customer, make your Security Operations more productive and efficient within your enterprise’s existing processes, programs, and workflows without relying on IT Ops. Stop inventing new security processes to address immediate threats by using one unified platform, and one dashboard.
Try It for Free
Sign up for a no-cost trial of Qualys Custom Assessment and Remediation.
Read More:
- Qualys Custom Assessment and Remediation Datasheet
- Qualys CAR API User Guide
- Qualys CAR Script Library on GitHub
- Qualys CAR Getting Start Guide
Contributors
- Mukesh Choudhary, Compliance Research Analyst, Qualys
- Mohd Anas Khan, Compliance Research Analyst, Qualys