NSA Alert: Topmost CVEs Actively Exploited By People’s Republic of China State-Sponsored Cyber Actors
On October 6, 2022, the United States National Security Agency (NSA) released a cybersecurity advisory on the Chinese government—officially known as the People’s Republic of China (PRC) states-sponsored cyber actors’ activity to seek national interests. These malicious cyber activities attributed to the Chinese government targeted, and persist to target, a mixture of industries and organizations in the United States. They provide the top CVEs used since 2020 by the People’s Republic of China (PRC) states-sponsored cyber actors as evaluated by the National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), and Federal Bureau of Investigation (FBI). The PRC malicious actor continues to exploit known vulnerabilities to target U.S. and vigorously allied networks and software and hardware companies to rob intellectual property and develop access to sensitive networks.
They stated that PRC state-sponsored cyber activities as one of the most significant and dynamic threats to U.S. government and civilian networks. The PRC state-sponsored cyber actors persist in targeting government and critical infrastructure networks with an increasing array of new and adaptive techniques. Some could pose a considerable risk to Information Technology Sector, telecommunications organizations, Defense Industrial Base (DIB) Sector, and other critical infrastructure organizations.
PRC state-sponsored cyber actors continue to exploit known vulnerabilities and use publicly available tools to target victims. Here is a list of 20 publicly known vulnerabilities (CVEs) published by the NSA, along with affected products and associated Qualys VMDR QID(s) for each vulnerability:
| Vendor | CVE | Vulnerability Type | Qualys QID(s) |
|---|---|---|---|
| Apache Log4j | CVE-2021-44228 | Remote Code Execution | 730302, 150441, 150440, and more |
| Pulse Connect Secure | CVE-2019-11510 | Arbitrary File Read | 38771 |
| GitLab CE/EE | CVE-2021-22205 | Remote Code Execution | 375475 |
| Atlassian | CVE-2022-26134 | Remote Code Execution | 730514, 376657, 150523 |
| Microsoft Exchange | CVE-2021-26855 | Remote Code Execution | 50107, 50108 |
| F5 Big-IP | CVE-2020-5902 | Remote Code Execution | 38791, 373106 |
| VMware vCenter Server | CVE-2021-22005 | Arbitrary File Upload | 216265, 216266 |
| Citrix ADC | CVE-2019-19781 | Path Traversal | 372685, 150273, 372305 |
| Cisco Hyperflex | CVE-2021-1497 | Command Line Execution | 730070 |
| Buffalo WSR | CVE-2021-20090 | Relative Path Traversal | NA |
| Atlassian Confluence Server and Data Center | CVE-2021-26084 | Remote Code Execution | 150368, 375839, 730172 |
| Hikvision Webserver | CVE-2021-36260 | Command Injection | NA |
| Sitecore XP | CVE-2021-42237 | Remote Code Execution | 14012 |
| F5 Big-IP | CVE-2022-1388 | Remote Code Execution | 150511, 730489, 376577 |
| Apache | CVE-2022-24112 | Authentication Bypass by Spoofing | 730361 |
| ZOHO | CVE-2021-40539 | Remote Code Execution | 375840 |
| Microsoft | CVE-2021-26857 | Remote Code Execution | 50107 |
| Microsoft | CVE-2021-26858 | Remote Code Execution | 50107 |
| Microsoft | CVE-2021-27065 | Remote Code Execution | 50107 |
| Apache HTTP Server | CVE-2021-41773 | Path Traversal | 150373, 150372, 710595 and more |
NSA stated that the threat actors use virtual private networks (VPNs) to obscure their activities and establish initial access. Multiple CVEs indicated in Table 1 let the actors stealthily acquire unauthorized access into sensitive networks, after which they pursue to develop persistence and reposition laterally to other internally connected networks.
The NSA highlights how the People’s Republic of China (PRC) has targeted and compromised significant telecom establishments and network service providers mostly by exploiting publicly known vulnerabilities. Networks affected have varied from small office/home office (SOHO) routers to medium and large enterprise networks.
PRC state-sponsored cyber actors readily exploit vulnerabilities to compromise unpatched network devices. The devices, such as Small Office/Home Office (SOHO) routers and Network Attached Storage (NAS) devices, serve as additional access points to route command and control (C2) traffic and act as means to conduct network intrusions on other entities. Furthermore, cyber defenders often overlook these devices, who work to maintain and keep pace with frequent software patching of Internet-facing services and endpoint devices.
Detect & Prioritize 20 Publicly Known Vulnerabilities using VMDR 2.0
Qualys released several remote and authenticated QIDs for commonly exploited vulnerabilities. You can search for these QIDs in Qualys VMDR 2.0, Vulnerabilities tab by using the following QQL query:
vulnerabilities.vulnerability.cveIds: [CVE-2021-44228, CVE-2019-11510, CVE-2021-22205, CVE-2022-26134, CVE-2021-26855, CVE-2020-5902, CVE-2021-22005, CVE-2019-19781, CVE-2021-1497, CVE-2021-20090, CVE-2021-26084, CVE-2021-36260, CVE-2021-42237, CVE-2022-1388, CVE-2022-24112, CVE-2021-40539, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065, CVE-2021-41773]
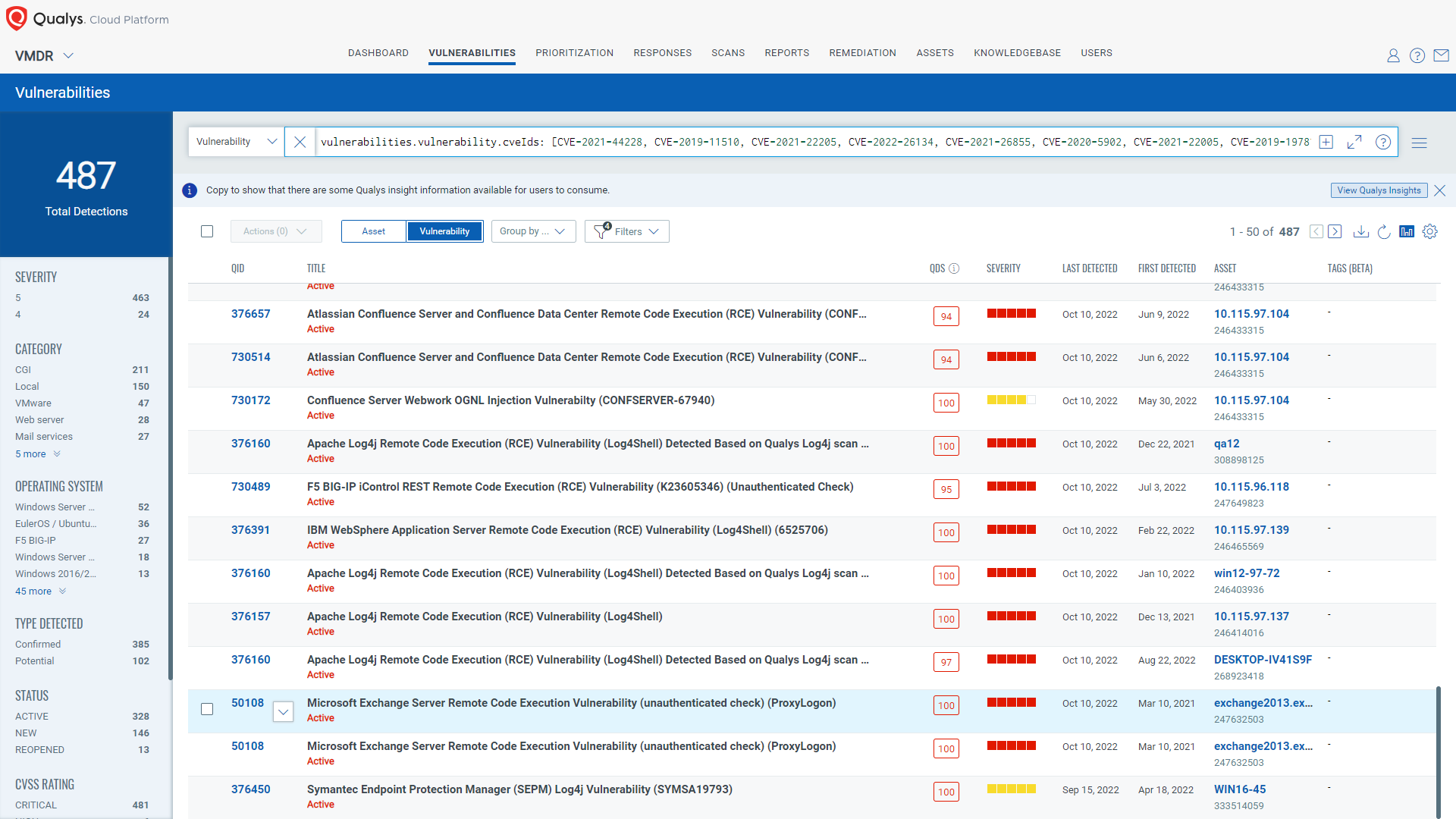
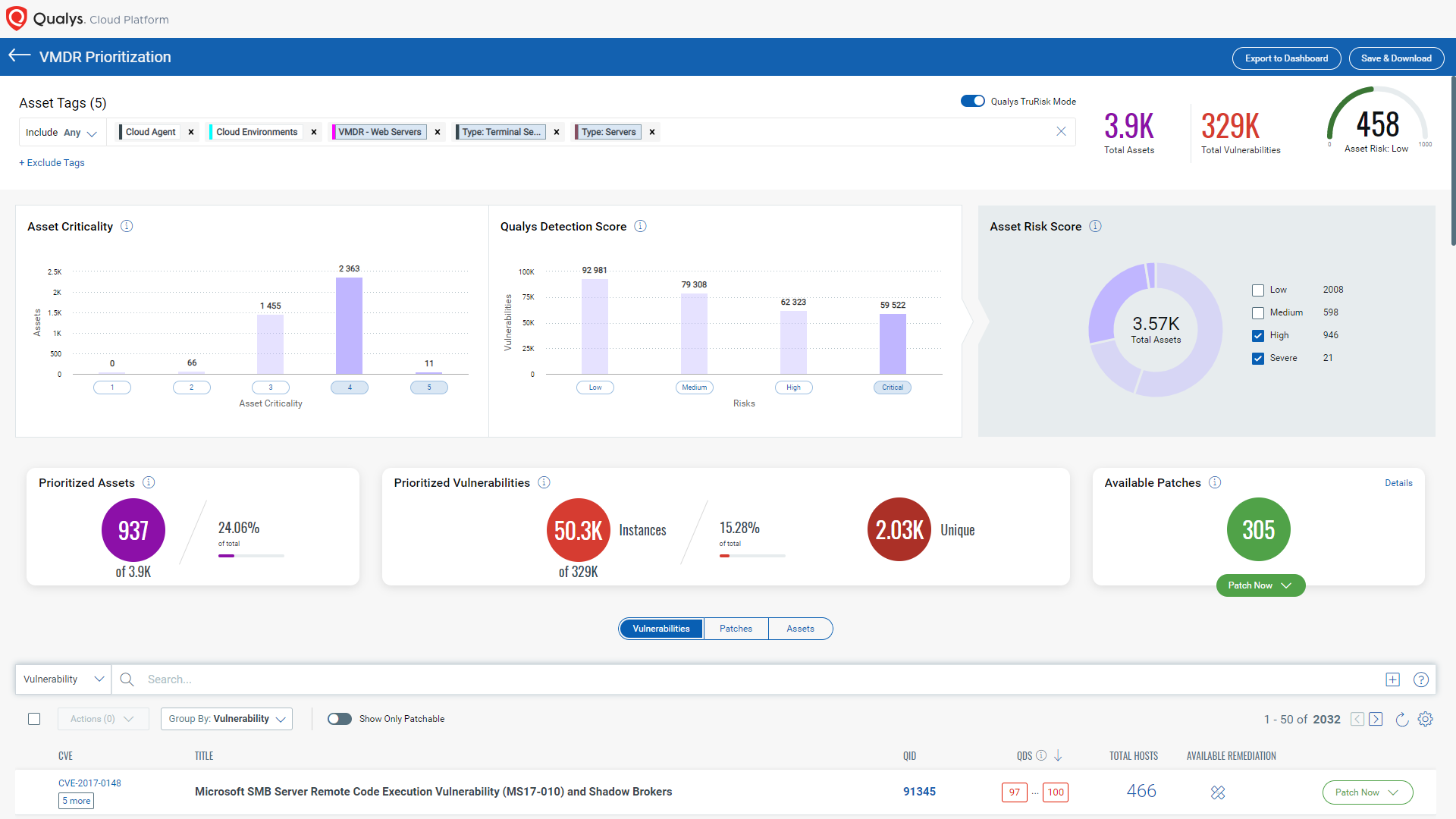
Using, Qualys VMDR 2.0, you can also effectively prioritize these vulnerabilities using the Qualys TruRisk.
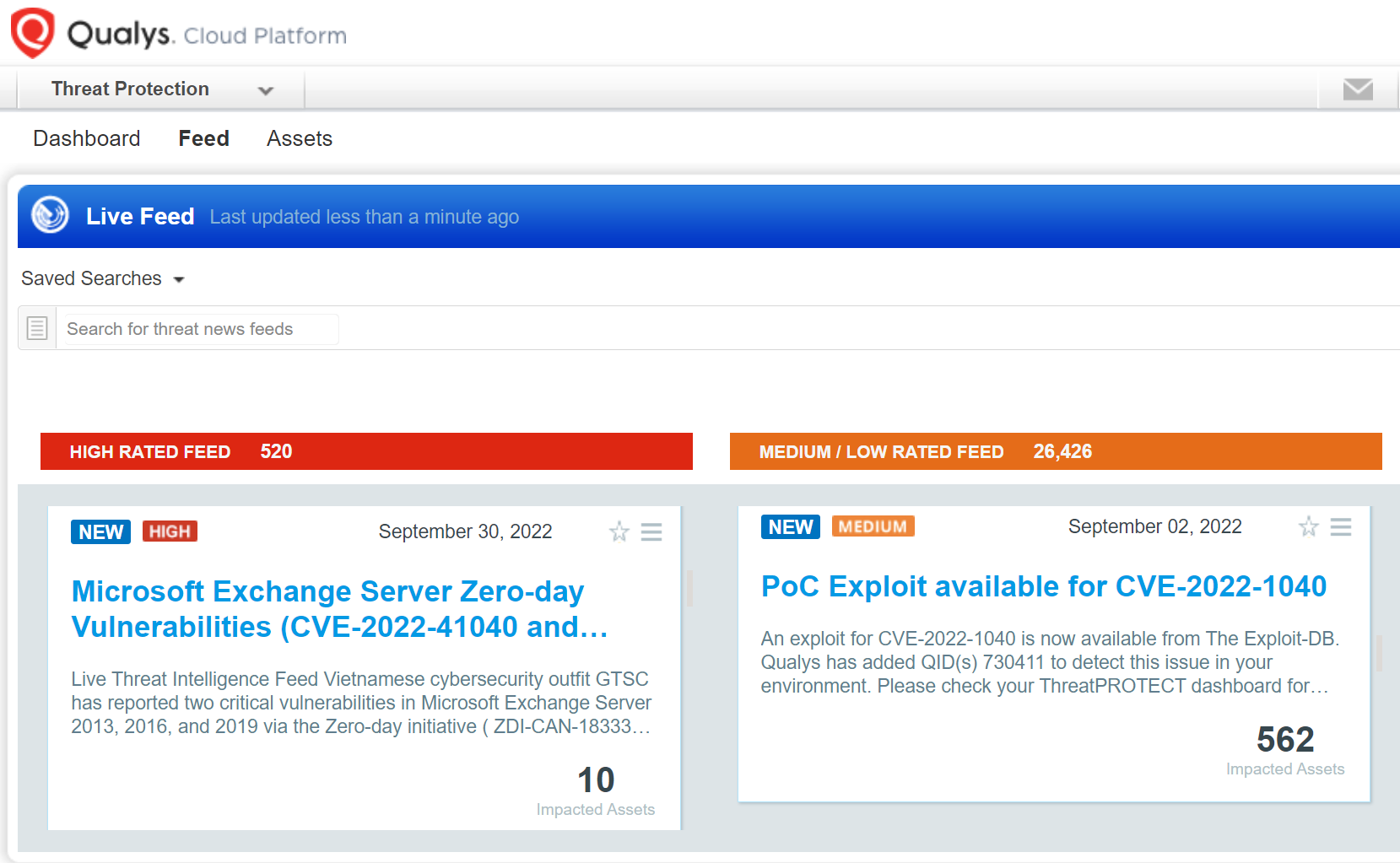
Identify Vulnerable Assets using Qualys Threat Protection
In addition, you can locate vulnerable hosts through Qualys Threat Protection by simply clicking on the impacted hosts. This helps in effectively identifying and tracking this vulnerability.
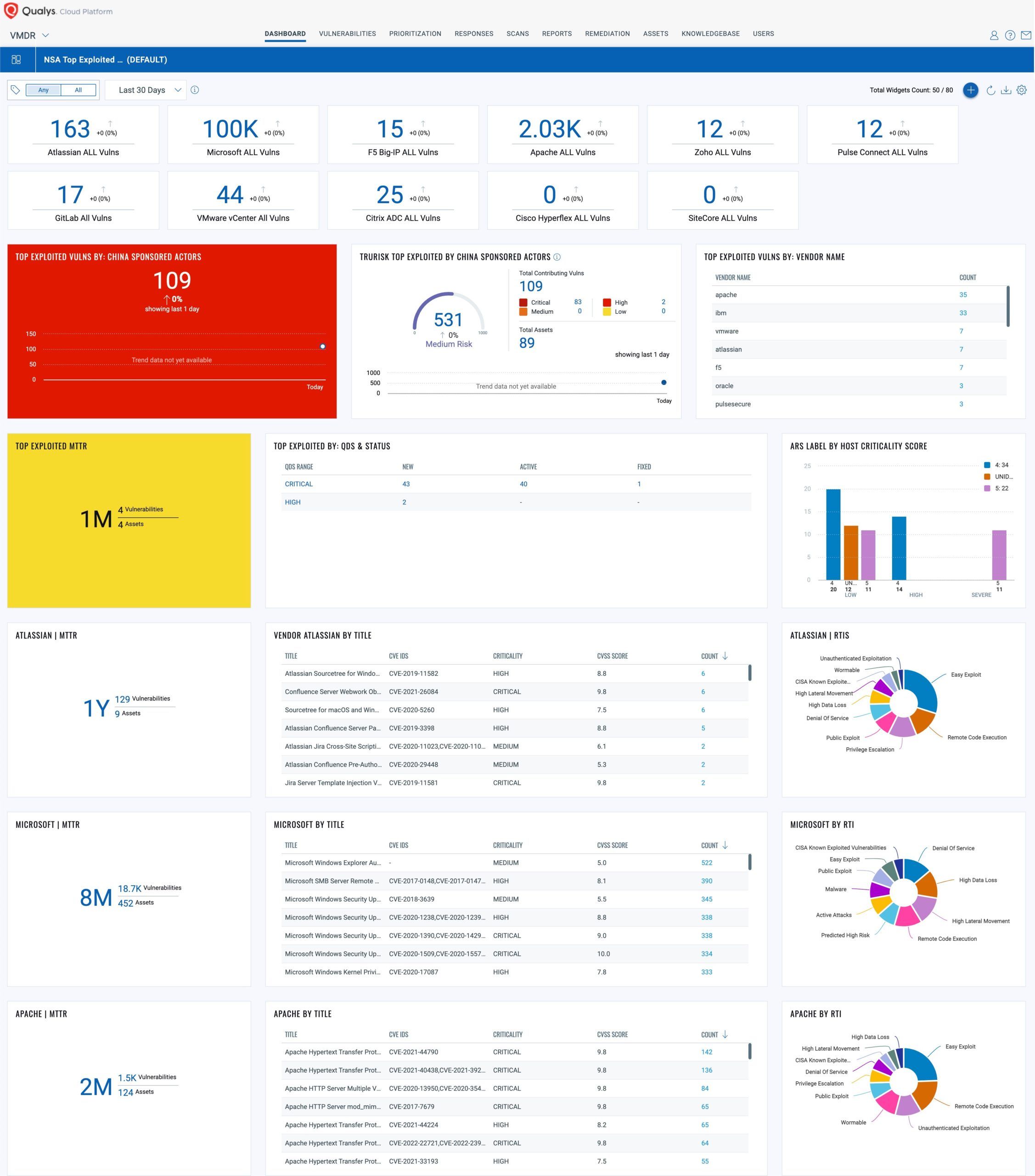
Using the Qualys Unified Dashboard, you can track, impacted hosts, their status, and overall management in real time. With trending enabled for dashboard widgets, you can keep track of the vulnerability trends in your environment.
Read the Article (Qualys Customer Portal): NSA Top Exploited CVEs | China State Actors
Recommendations & Mitigations
The NSA, CISA, and FBI recommend U.S. and allied governments, critical infrastructure, and private sector organizations use the mitigation guidance provided to boost their defensive posture and decrease the threat of compromise from PRC state-sponsored threat cyber actors.
Here is a summary of mitigations guidance provided by the NSA:
- Update, prioritize and patch vulnerable systems as soon as possible, as listed in this article and the list provided by CISA KEV.
- Utilize phishing-resistant multi-factor authentication and require all accounts with a unique and strong password.
- Block obsolete or unused protocols at the network edge.
- Upgrade or replace end-of-life devices.
- Move toward the Zero Trust security model.
- Enable robust logging of Internet-facing systems and monitor the logs for anomalous activity.
One of the soundest methods that organizations of all sizes could stay on top of these vulnerabilities and end-of-life (EOL) network/device infrastructure as noted by NSA general mitigations guidelines is to catalog the infected assets and apply patches as soon as possible. This could be an effortless process if the corps utilize the power of Qualys VMDR 2.0. You can start your Qualys VMDR 2.0 trial for automatically identifying, detecting, and patching the high-priority commonly exploited vulnerabilities.
Contributors
- Felix Jimenez Saez, Director, Product Management, Qualys
- Swapnil Ahirrao, Principal Product Manager, VMDR, Qualys
What happened to the dashboard?