Leeloo Multipath: Authorization bypass and symlink attack in multipathd (CVE-2022-41974 and CVE-2022-41973)
The Qualys Research Team has discovered two vulnerabilities in multipathd, the most important of which can be exploited for authorization bypass. Qualys recommends security teams apply patches for these vulnerabilities as soon as possible.
The Qualys Research Team combined these two vulnerabilities with the third vulnerability in another package installed by default on Ubuntu Server and obtained full root privileges on Ubuntu Server 22.04; other releases are probably also exploitable. We will publish this third vulnerability, and the complete details of this local privilege escalation, in an upcoming advisory next month.
About multipathd
The multipathd daemon oversees checking for failed paths. When this happens, it will reconfigure the multipath map the path belongs to so that this map regains its maximum performance and redundancy. The multipathd daemon runs as a root in the default installation of Linux Operating Systems like Ubuntu Server.
Potential Impact of Leeloo Multipath
Successful exploitation of the three vulnerabilities allows any unprivileged user to gain root privileges on the vulnerable host. Qualys security researchers have independently verified the vulnerability, developed an exploit and obtained full root privileges on default installations of Ubuntu.
As soon as the Qualys Research Team confirmed the vulnerability, we engaged in responsible vulnerability disclosure and coordinated with vendors and open-source distributions to announce this newly discovered vulnerability.
Technical Details of Leeloo Multipath
The technical details of Leeloo Multipath vulnerabilities can be found at:
https://www.qualys.com/2022/10/24/leeloo-multipath/leeloo-multipath.txt
Disclosure Timeline:
- 2022-08-24: Advisory sent to security@suse
- 2022-10-10: Advisory and patches sent to linux-distros@openwall
- 2022-10-24: Coordinated Release Date (15:00 UTC)
Qualys QID Coverage
Qualys is releasing the QIDs in the table below as they become available, starting with vulnsigs version VULNSIGS-2.5.615-2 and in Linux Cloud Agent manifest version lx_manifest-2.5.615.2-1
| QID | Title |
|---|---|
| 752706 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3711-1) |
| 752707 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3710-1) |
| 752709 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3709-1) |
| 752711 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3708-1) |
| 752703 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3707-1) |
| 752704 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3713-1) |
| 752705 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3712-1) |
| 752706 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3711-1) |
| 752707 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3710-1) |
| 752709 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3709-1) |
| 160167 | Oracle Enterprise Linux Security Update for device-mapper-multipath (ELSA-2022-7186) |
| 752711 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3708-1) |
| 752703 | SUSE Enterprise Linux Security Update for multipath-tools (SUSE-SU-2022:3707-1) |
| 240785 | Red Hat Update for device-mapper-multipath (RHSA-2022:7186) |
| 240788 | Red Hat Update for device-mapper-multipath (RHSA-2022:7185) |
| 240789 | Red Hat Update for device-mapper-multipath (RHSA-2022:7188) |
| 240790 | Red Hat Update for device-mapper-multipath (RHSA-2022:7192) |
Please check Qualys Vulnerability Knowledgebase for the full list of coverage for these vulnerabilities.
Discover Vulnerable Linux Servers Using Qualys VMDR
The following instructs current Qualys customers on how to detect Leeloo Multipath in their environment.
Identify Assets Running Ubuntu Operating System
The first step in managing this critical vulnerability and reducing risk is identification of all assets running Linux OS. Qualys VMDR makes it easy to identify such assets.
operatingSystem.name:”Linux”
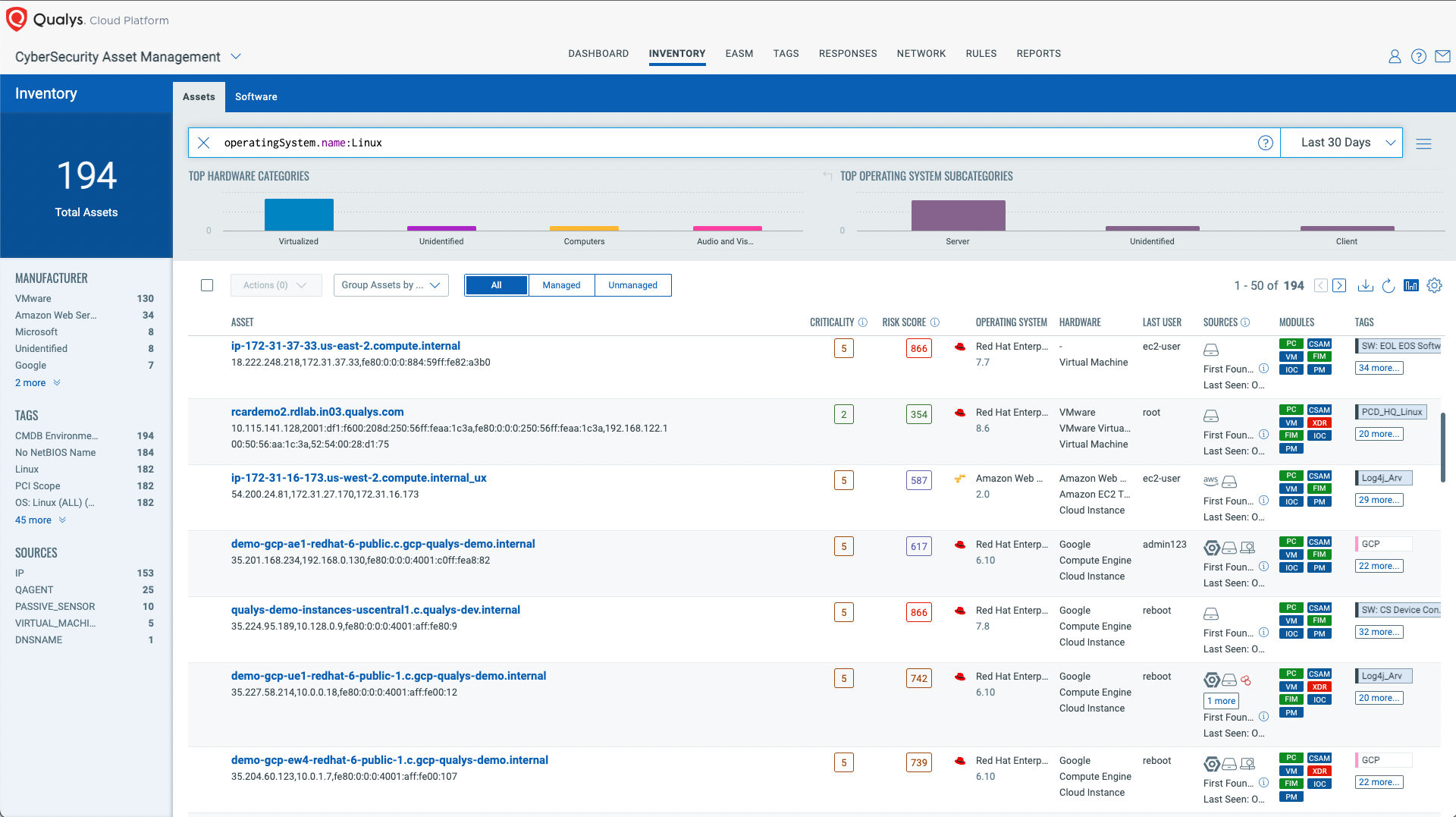
Once the hosts are identified, they can be grouped together with a ‘dynamic tag’; let’s say: “Linux Systems”. This helps by automatically grouping existing hosts with the above vulnerabilities as well as any new assets that spin up in your environment. Tagging makes these grouped assets available for querying, reporting, and management throughout Qualys Cloud Platform.
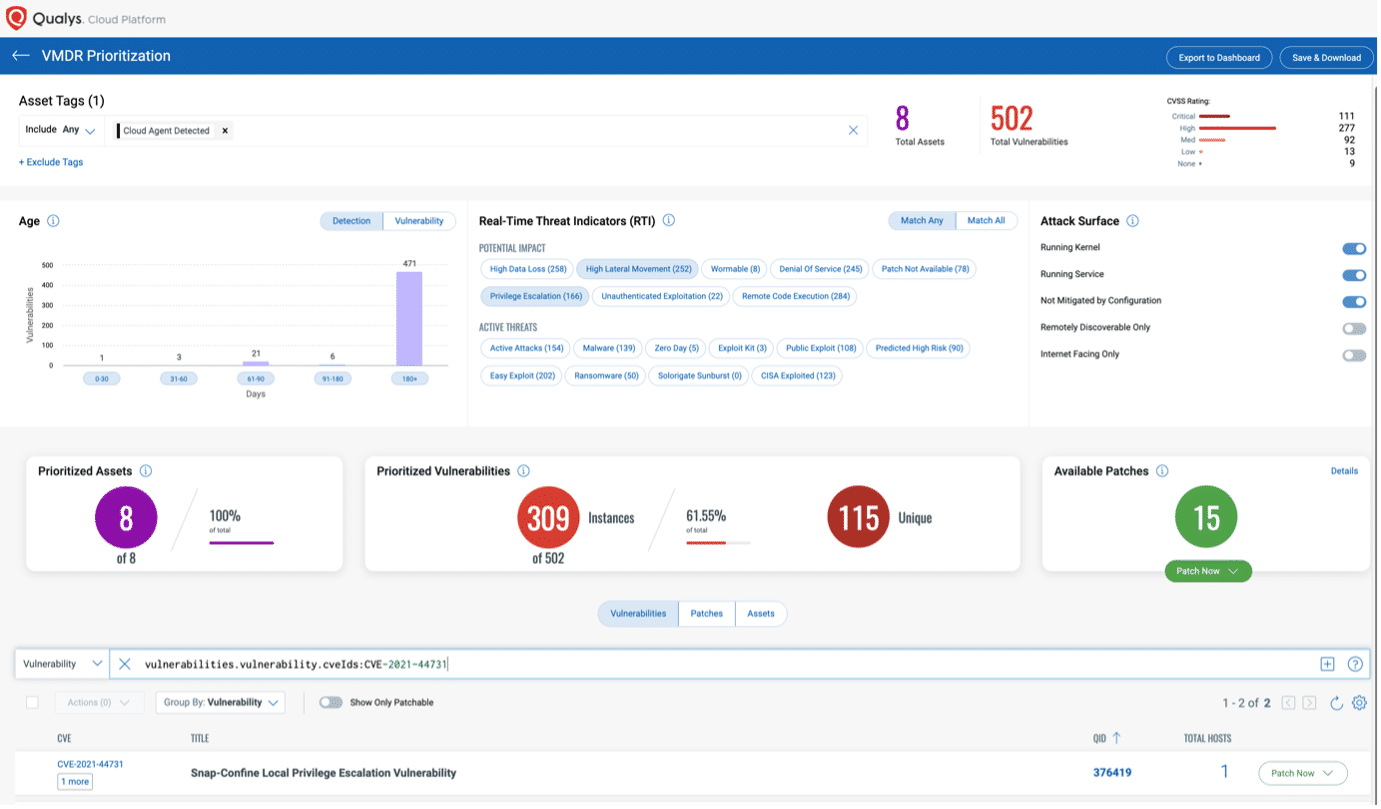
Prioritize Based on RTIs
Using Qualys VMDR, the Leeloo Multipath vulnerability can be prioritized using the following real-time threat indicators (RTIs):
- Predicted_High_Risk
- Privilege_Escalation
- Easy_Exploit
- High_Lateral_Movement
Patch With Qualys VMDR
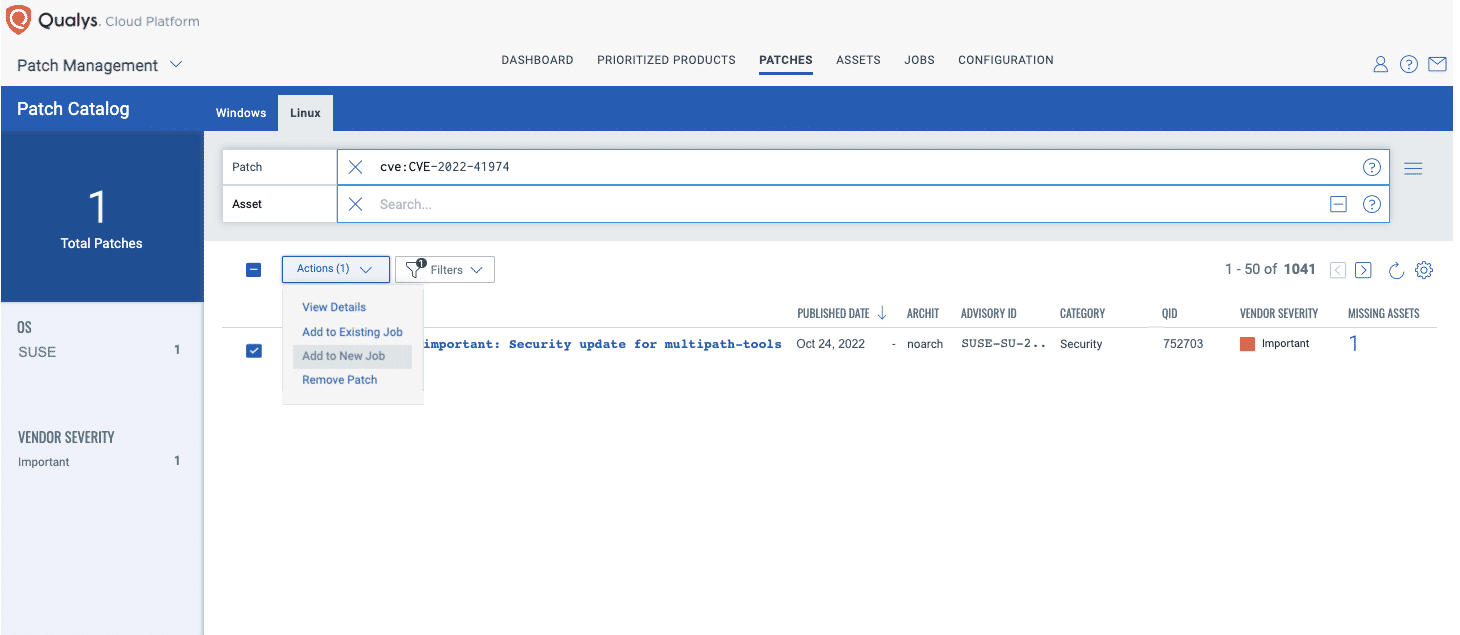
We expect vendors to release patches for this vulnerability in the short term. Qualys Patch Management can be used to deploy those patches to vulnerable assets, when available.
Using the same prioritization based on RTI method as described above, customers can use the “patch now” button found to the right of the vulnerability to add Leeloo Multipath to a patch job. Once patches are released, Qualys will find the relevant patches for this vulnerability and automatically add those patches to a patch job. This will allow customers to deploy those patches to vulnerable devices, all from Qualys Cloud Platform.
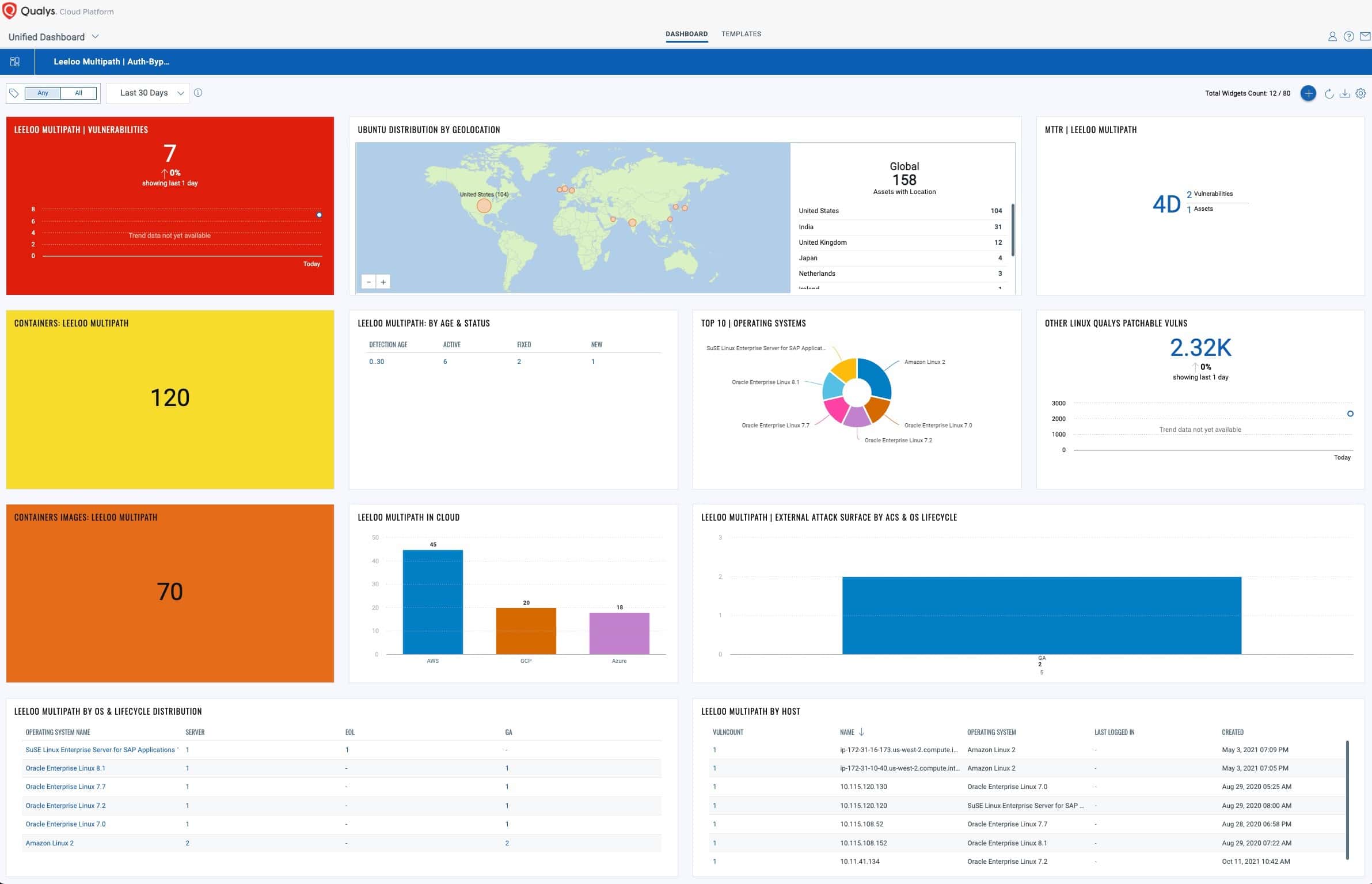
Gain exposure visibility and remediation tracking with Unified Dashboard
With the Qualys Unified Dashboard, you can track the vulnerability exposure within your organization and view your impacted hosts, their status, distribution across environments and overall management in real-time, allowing you to see your MTTR. “Leeloo Multipath” Dashboard.
View and download the “Leeloo Multipath” dashboard
Vendor References
https://www.qualys.com/2022/10/24/leeloo-multipath/leeloo-multipath.txt
Frequently Asked Questions (FAQs)
Will the Qualys Research Team publish exploit code for this vulnerability?
No. Not at this time.
Are there any mitigations for this vulnerability?
No.
Is this vulnerability remotely exploitable?
No. But if an attacker can log in as an unprivileged user, the vulnerability can be quickly exploited to gain root privileges.
Why is the vulnerability named “Leeloo Multipath”?
This is a pun/reference to “Leeloo Multipass” (which is actually related to authentication and authorization) from the movie “The Fifth Element”.
https://en.wikipedia.org/wiki/The_Fifth_Element
What is the maximum impact of these vulnerabilities?
An attacker who has unprivileged access to an unpatched Linux system can exploit these vulnerabilities to obtain full root privileges; i.e., this is a Local Privilege Escalation to administrator privileges.
What can an attacker do with these vulnerabilities?
The first vulnerability is an authorization bypass (CVE-2022-41974) that allows an unprivileged attacker to trigger the second vulnerability, a symlink attack (CVE-2022-41973). This allows the attacker to create files and directories in arbitrary places of the filesystem.
How would an attacker exploit these vulnerabilities?
To the best of our knowledge, these two vulnerabilities are not powerful enough to lead to full root privileges on their own. However, we were able to combine them with a third vulnerability that we discovered in another package, and obtained full root privileges on Ubuntu Server.
We will publish this third vulnerability, and hence this complete exploit chain (of these three otherwise unexploitable vulnerabilities), in an upcoming advisory.
Should organizations patch these vulnerabilities urgently?
No, not urgently, since this is a Local Privilege Escalation that (to the best of our knowledge) requires an additional vulnerability to be successfully exploited. Nonetheless, since this additional vulnerability will become public in a few weeks, the multipathd vulnerabilities should be patched as part of a normal patch management life cycle.
Are there any mitigations that organizations can apply for these vulnerabilities in case they are not able to patch?
To the best of our knowledge, no.
Do these vulnerabilities affect only SuSE Operating System? If no, why was disclosed to the SUSE Security Team?
These vulnerabilities affect all Linux distributions; multipathd is a common Linux daemon, especially on servers. For example, our complete exploit chain targets the default installation of Ubuntu Server. We contacted the SUSE Security Team because one of multipathd’s most active developers works for SUSE, so they were able to put us in direct contact with him, via encrypted email.
Contributors:
- Felix Jimenez Director of Product Management
- Saeed Abbasi Manager, Vulnerability Signatures