Risk-based Vulnerability Management Combined With A Cyber Risk Management Platform
Recent insights from IDC’s recent report, Worldwide Device Vulnerability Management Forecast, 2023–2027: Evolving Beyond Scanning (Feb. 2023), provide a sobering look at the future of what cybersecurity stacks may look like in a few years.
As the name suggests, this report took a deep dive into the Vulnerability Management (VM) space – but it did not stop there. Since VM is such a cornerstone of any modern enterprise cybersecurity stack, the insights, and data apply to nearly every other adjacent cybersecurity solution. From SIEM, UEBA, Patch Management, Asset Management, and – you guessed it – Cyber Asset Attack Surface Management (CAASM), VM plays a central role.
– Michelle Abraham, research director, Security, and Trust at IDC.
Vulnerability scanning is evolving into vulnerability management, which will integrate attack surface management and cybersecurity asset management in the future.
Read More
Download the Worldwide Device Vulnerability Management Forecast, 2023–2027: Evolving Beyond Scanning here
Michelle Abraham of IDC sees conventional VM solutions in a stage of forced evolution, if you will, that will incorporate cyber asset management as well.
At Qualys, we couldn’t agree more.
Vulnerability Management Foundational Element to Manage Cyber Risk
While the fact that VM will play a marquis role in the evolution of cybersecurity may not be Earth-shattering news, IDC’s take on how the cybersecurity ecosystem is changing VM is relevant and incredibly timely from our perspective.
For Qualys, we have long known that Vulnerability Management needs – must be so much more for our customers. With the release of VMDR in 2020 and VMDR with TruRisk in 2022, we have been pushing the envelope of what even defines VM for years.
– IDC, Worldwide Device Vulnerability Management Forecast
Device vulnerability management is already being used by 82.1% of U.S. organizations with more than 500 employees.
For the modern hybrid enterprise, Vulnerability Management is often seen as a necessity and is a cornerstone for any well-defined cyber risk management program. Organizations that maintain an accurate inventory of all their assets, and can detect, prioritize, and patch high-risk vulnerabilities on a weekly basis, based on their level of risk, are much more likely to maintain good cyber hygiene and fare better in terms of managing cyber risk than organizations that simply chase the latest “shiny object” in an attempt to reduce risk.
Qualys has consistently proved how organizations can do that with the power of Qualys cloud platform. Here’s how…
Expanded Visibility Through Consolidation
As referenced by IDC, VM must find ways to integrate attack surface management and cybersecurity asset management capabilities to give organizations the reach they need to protect themselves from new cyber risks stemming from external internet-facing assets and applications. VM offerings that do not adequately support this need will become obsolete.
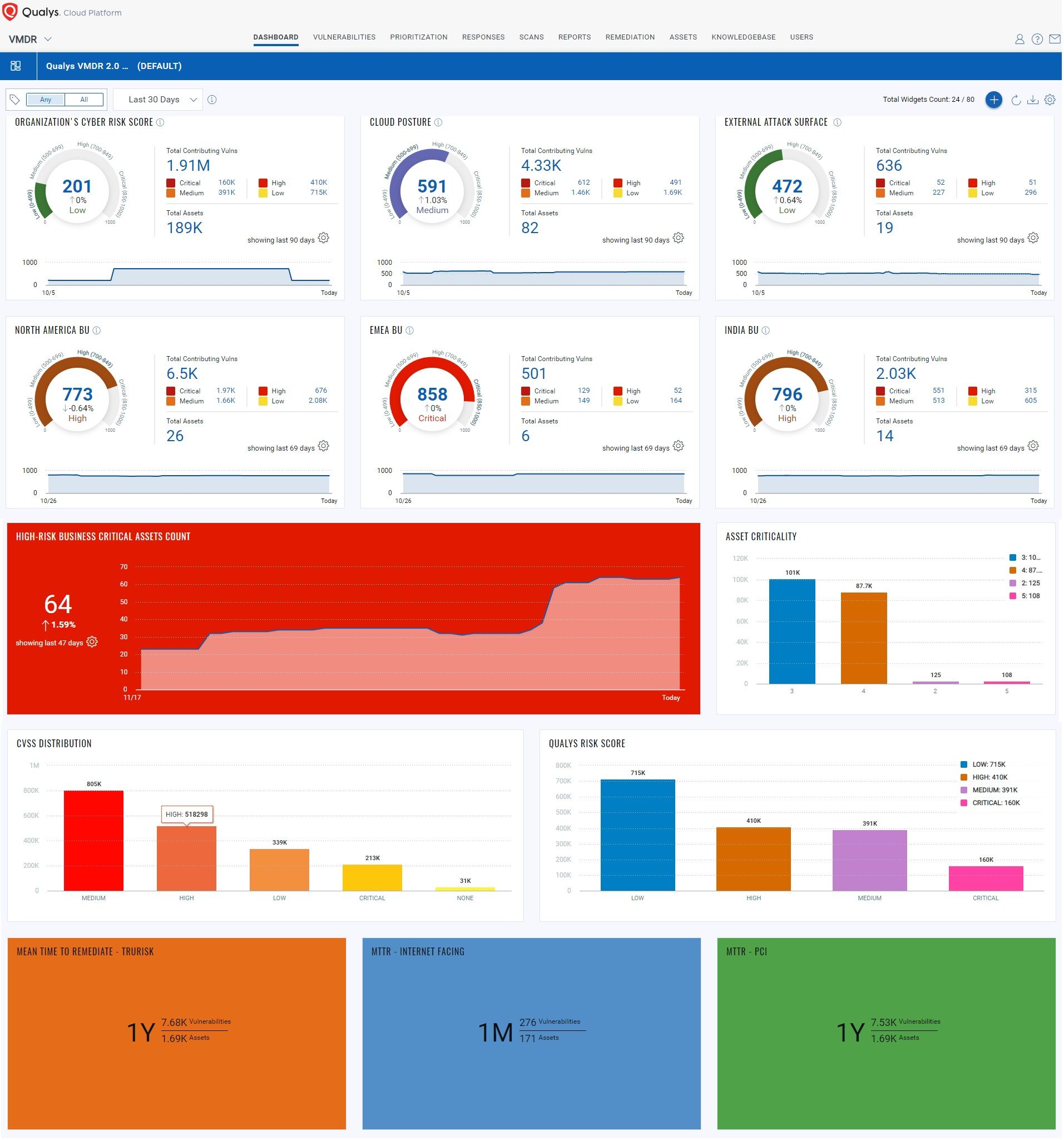
With Qualys VMDR, customers access a platform approach that natively integrates the remediation functions of Qualys PM, policy compliance functions of Qualys PC, and external attack surface management (EASM) functions of Qualys CSAM. All are available from one vendor and operationalized via a single intuitive dashboard. Where other VM vendors require third-party solutions, Qualys can scale at the liberty of customer demand.
The Need for Speed
From research from the Qualys Threat Research Unit (TRU) we know definitively from over 2.3 billion observed vulnerabilities that threat actors are about 2x faster than conventional security stakeholders. That cannot continue. VM solutions must increase the pace at which they can identify both known and zero-day vulnerabilities. To do this, not only must VM solutions be lightweight and high-performance, but they also need to continuously incorporate extensive threat research from both internal and external sources.
With Qualys VMDR, customers are empowered with 25+ threat intelligence feeds coupled with the ever evolving and continuously updated Qualys Threat Database, bolstering threat detection that is as much as 6x faster than industry peers and remediation that is highly targeted.
Don’t forget – get the Qualys Threat Research Report
Bridging the Gap between IT and Security Efforts
Most enterprise VM solutions are managed by security teams, while patch management programs are managed by IT. However, what does the process look like when security teams identify thousands of vulnerabilities that must be patched daily? How many steps does it take for IT to remediate these vulnerabilities and report back to security teams? Often this process is as imagined; slow, cumbersome, and full of spreadsheets. This work cycle between security and IT is yet another issue of consternation for most enterprises which is commonly called the IT-Security Gap. This gap must be bridged.
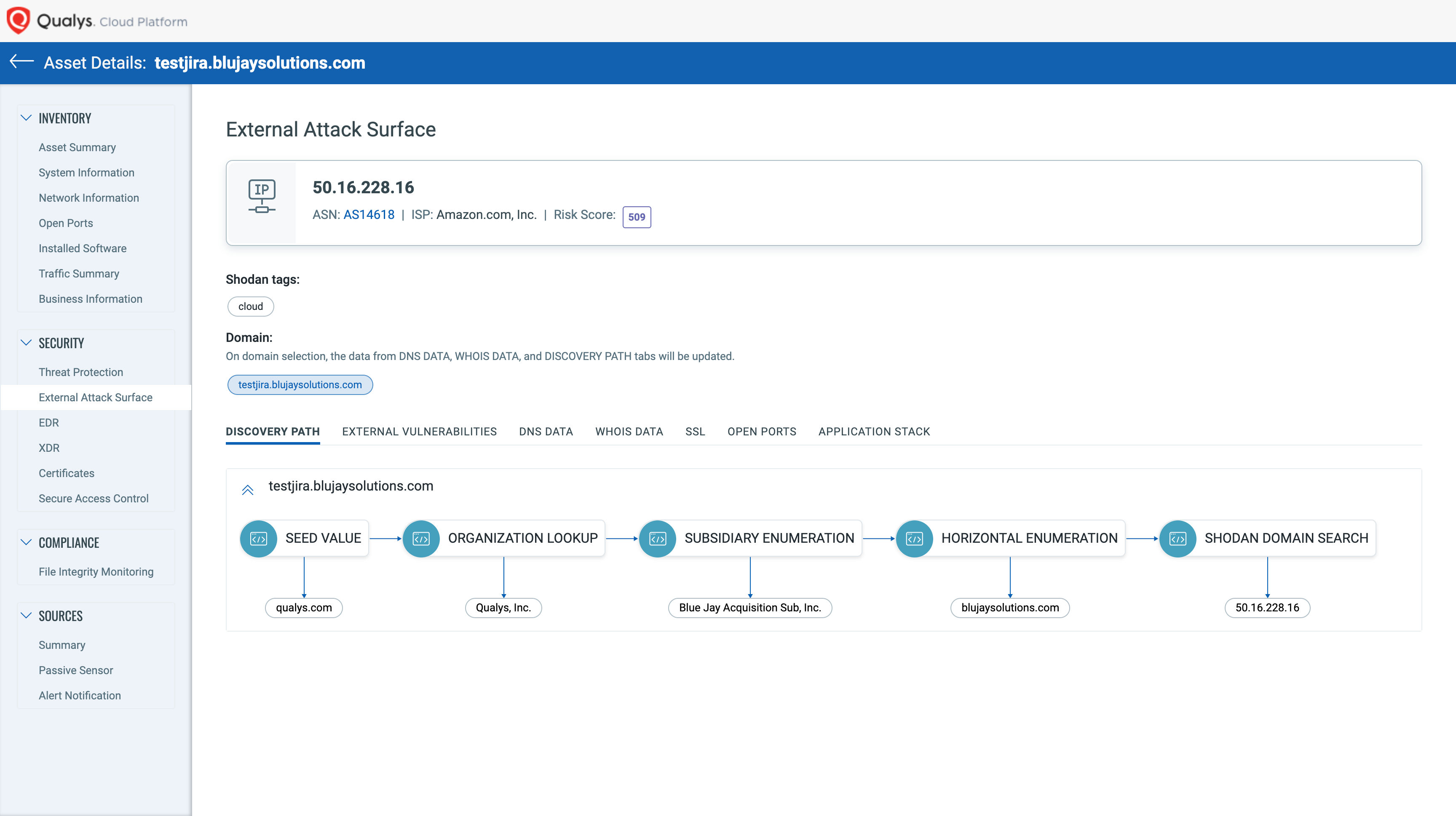
At Qualys, we have taken a keen interest in brining IT and security teams closer together. By integrating with ITSM tools, such as ServiceNow and Jira, Qualys is unifying interdepartmental workflows within VMDR to vastly reduce MTTR and simplify IT-Security collaboration.
To learn more about the integration between Qualys and ServiceNow, watch the recent
A Risk-based Approach to Reduce Cyber Risk
In addition to expanded visibility, rapid vulnerability detection, and ITSM integrations, understanding cyber risk exposure in real-time is increasingly essential. For example, with thousands of vulnerabilities logged daily, how can security and IT teams best prioritize remediation actions when CVSS does not accurately measure criticality according to business impact? How can security stakeholders accurately measure the risk posture over time? Furthermore, how can they prove that their security programs are reducing their organization’s exposure to cyber risk? With many industries frantically exploring savings on cyber insurance premiums, measuring and managing cyber risk is a board-level issue.
– IDC, Worldwide Device Vulnerability Management Forecast
In September 2022, Cowbell introduced adaptive cyberinsurance where coverage is dynamic and based on an organization’s cyberexposure. In a partnership with Qualys, organizations that use Qualys VMDR and Cowbell may receive discounted premiums based on their TruRisk score.
With Qualys TruRisk, included as part of VMDR, customers not only gain an enterprise-grade VM solution, but also a cyber risk management platform. TruRisk’s customizable and transparent cyber risk methodology, cybersecurity stakeholders can reduce critical vulnerabilities by up to 40% while being able to better communicate cyber risk exposure to external stakeholders. Furthermore, with Enterprise TruRisk Management, organizations gain a unified view of cyber risk that turns internal and external data feeds into actionable insights.
A biased but accurate takeaway on VM
The recent research from IDC is that it substantiates the Qualys product vision of VM not only providing detection and response but being able to support native asset inventories, ingestion of external data, External Attack Surface Management (EASM), and cyber risk management capabilities.
To learn more how VMDR, TruRisk, and EASM can help your organization scale security well into the future, go to: https://www.qualys.com/apps/vulnerability-management-detection-response/
Get your copy of the Worldwide Device Vulnerability Management Forecast, 2023–2027: Evolving Beyond Scanning.