Progress MOVEit Transfer Vulnerability Being Actively Exploited

Table of Contents
- Vulnerability Analysis
- Active Exploitation
- Detecting the Vulnerability
- Remediating the Vulnerability
- Leverage Qualys Custom Assessment and Remediation (CAR) To Mitigate Risk
- Detecting Exploitation
- Discover Vulnerable Instances Using Qualys Web Application Scanning (WAS)
- Detection via File Integrity Monitoring
On June 2nd, CVE-2023-34362 was published against the Progress MOVEit Transfer product and was quickly added to CISA’s Known Exploited Vulnerabilities Catalog. MOVEit Transfer is a managed file transfer solution available as an on-premise solution that enables file transfer between business partners and customers. The vulnerability effects all versions before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5), and 2023.0.1 (15.0.1). Organizations that are running this software are urged to patch this critical vulnerability as quickly as possible.
As of this writing, Shodan shows more than 2500 assets running Progress MOVEit Transfer. However, Qualys External Attack Surface Management (EASM) can discover externally facing MOVEit Transfer instances on internet-facing assets from its external sources in the Application Stack section of EASM Assets:
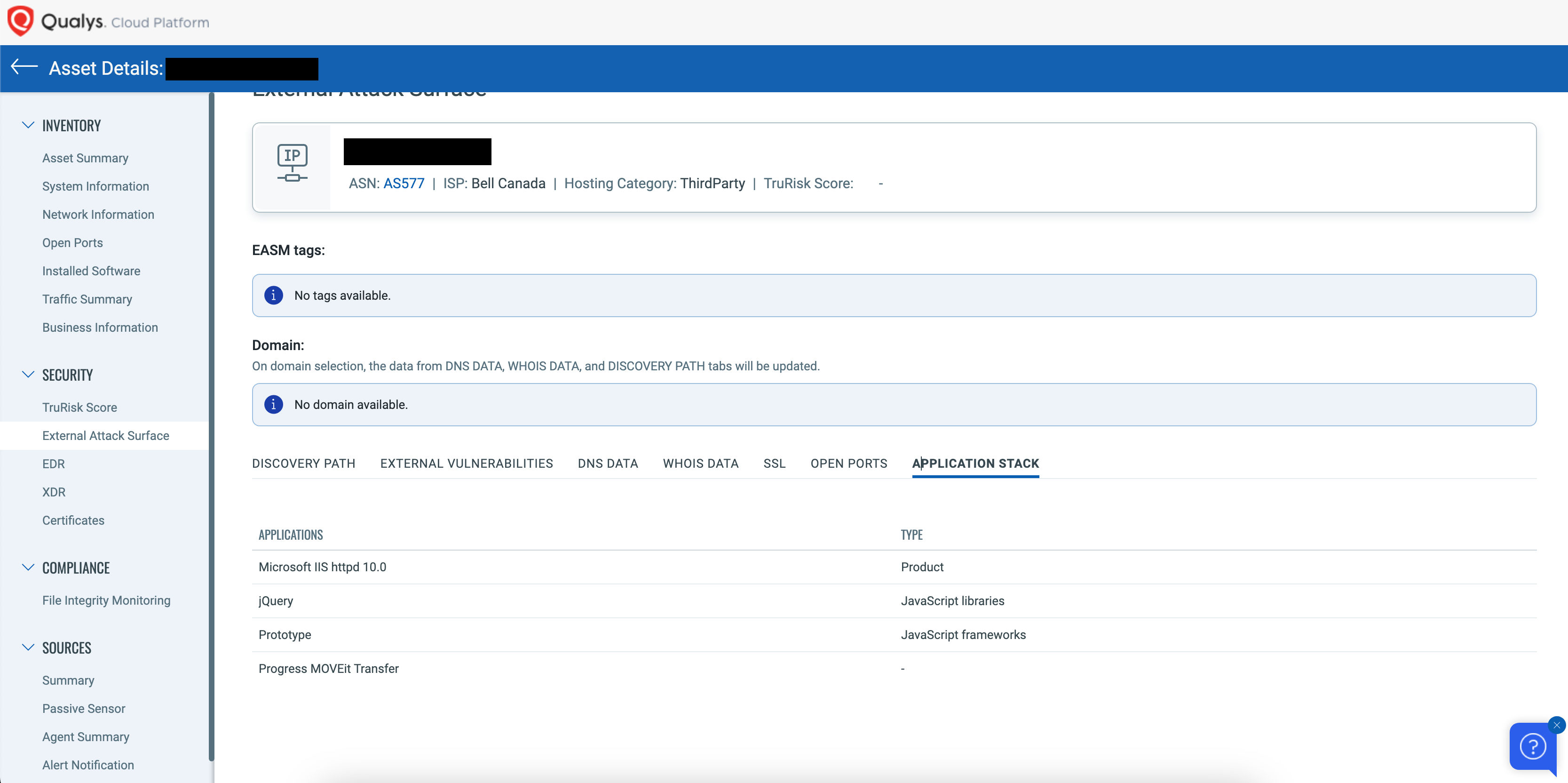
To quickly see all instances of MOVEIt on externally exposed assets, using the EASM Application Stack Details report, you can see all your externally exposed assets with this software, even if they have not been scanned by VMDR.
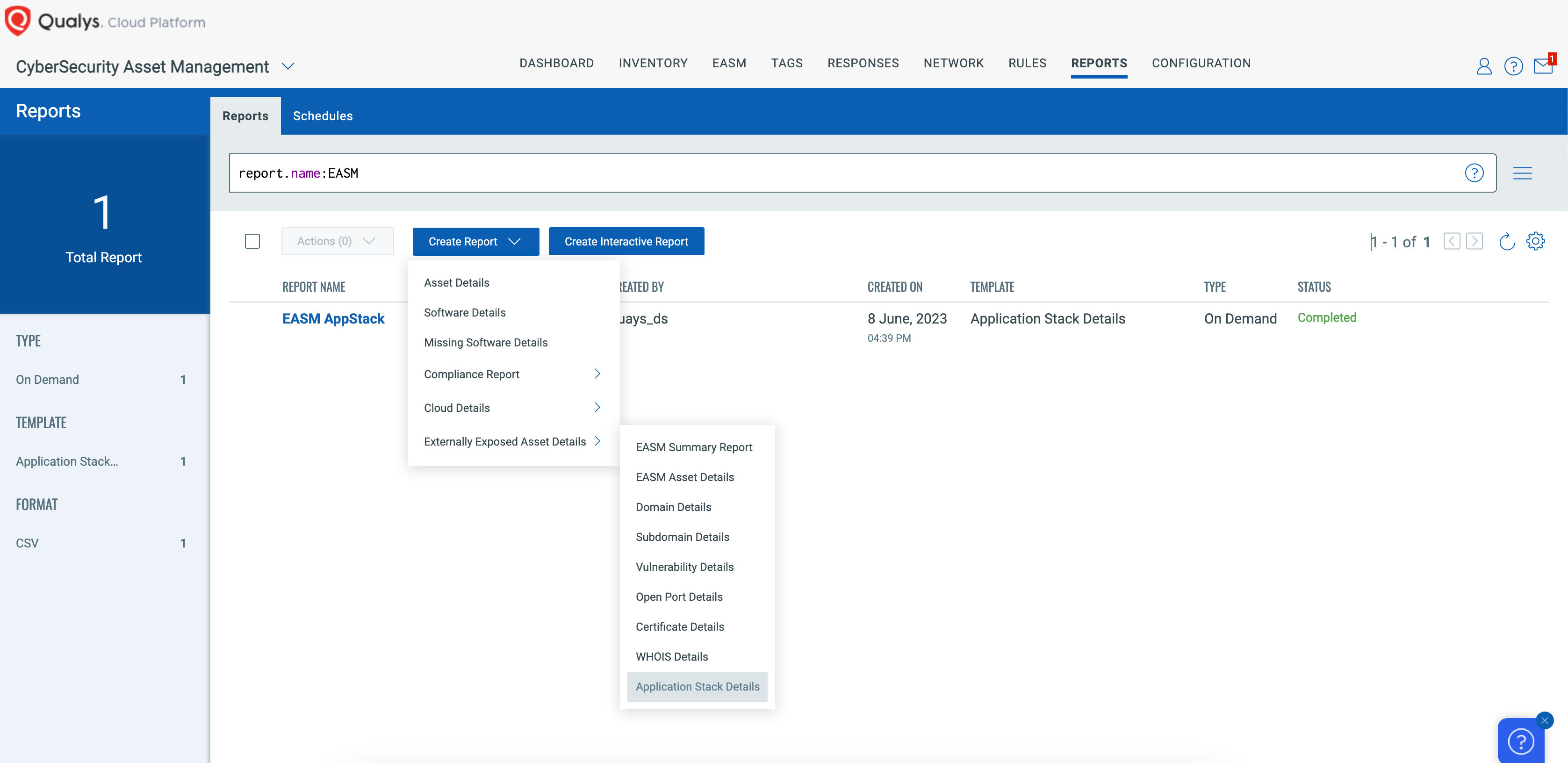
In the report, search or sort the report by the Application Name column to identify those externally exposed assets:
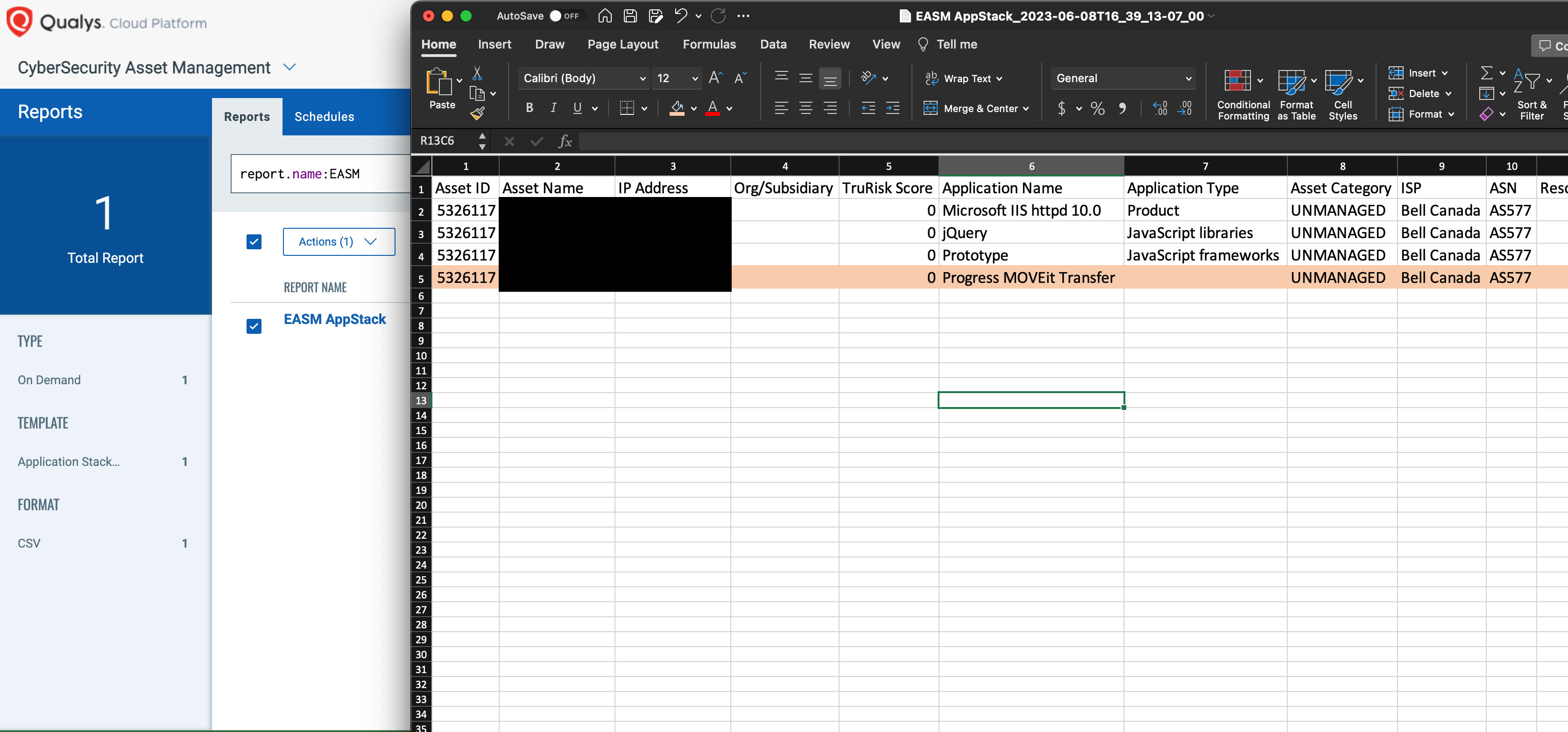
Detecting if an Instance is actually vulnerable requires more than just knowing the vendor and software. The ability to authenticate directly to the target or having an agent provides the highest fidelity detections possible. Using anonymous detections from the Qualys platform, we found 55% of these vulnerable instances have been remediated since the vulnerability was announced last Friday. Those which have been fixed were done so within 48 hours of first detection.
Vulnerability Analysis
This is a SQL Injection vulnerability in the web application that enables an unauthenticated remote attacker to gather information from the backend database, including the content stored within it. Once the attacker exploits the application, a webshell by the name of LEMURLOOT masquerades as a legitimate file (human.aspx) and is dropped on the target. The webshell enables the attackers to perform multiple actions, such as extracting Azure system settings, querying confidential data, creating users, running commands, or downloading files from the target.
Authentication and Database Connection
LEMURLOOT supports various parameters. Depending upon the parameter being used, specific actions are triggered.
At first, LEMURLOOT checks if an incoming HTTP request contains the header field X-siLock-Comment and a corresponding 36-character GUID-formatted value. The GUID value is used as a password. If this value does not pass the expected header field and value, it returns an HTTP 404 status code to clients.
If the correct password is passed through LEMURLOOT, it sends a header response X-siLock-Comment and value comment. This indicates that the connection is successful. LEMURLOOT connects itself to a SQL server from the execution host. It then processes data received from the connected client and parses expected commands from the HTTP header fields X-siLock-Step1, X-siLock-Step2, and X-siLock-Step3.
X-siLock-Step1 is the primary parameter used for access. X-siLock-Step2 specifies a directory, and X-siLock-Step3 specifies a filename.
When the X-siLock-Comment is set with the correct password string, the X-siLock-Step1 will define the actions that will be performed on the exploited system as follows:
- If the value of the header field X-siLock-Step1 is –1 – LEMURLOOT will return critical Azure Blob information, including Storage Account, Key, and Container IDs. It will also return a list of all files and folders stored in MOVEit, along with details of the file owners, file sizes, and institution names mentioned in the MOVEit Transfer system. An attacker may target specific files associated with specific users or organizations.
- If the X-siLock-Step1 header field value is –2 – LEMURLOOT will delete the new database admin user named “Health Check Service” admin user.
- If the value of header field X-siLock-Step1 is neither -1 nor –2 – LEMURLOOT will parse the values from header fields X-siLock-Step2 and X-siLock-Step3 and store them in fileid and folderid variables, respectively.
- If the values of fileid and folderid are not null – LEMURLOOT will retrieve the file from the local MOVEit Transfer system with these same values. gzip will compress the file and return it to the connected client.
- If the fileid and folderid variables are null – LEMURLOOT will download the file defined by X-siLock-Step2 and X-siLock-Step3. Without parameters, human2.aspx will create a new database admin user named “Health Check Service.”
Active Exploitation
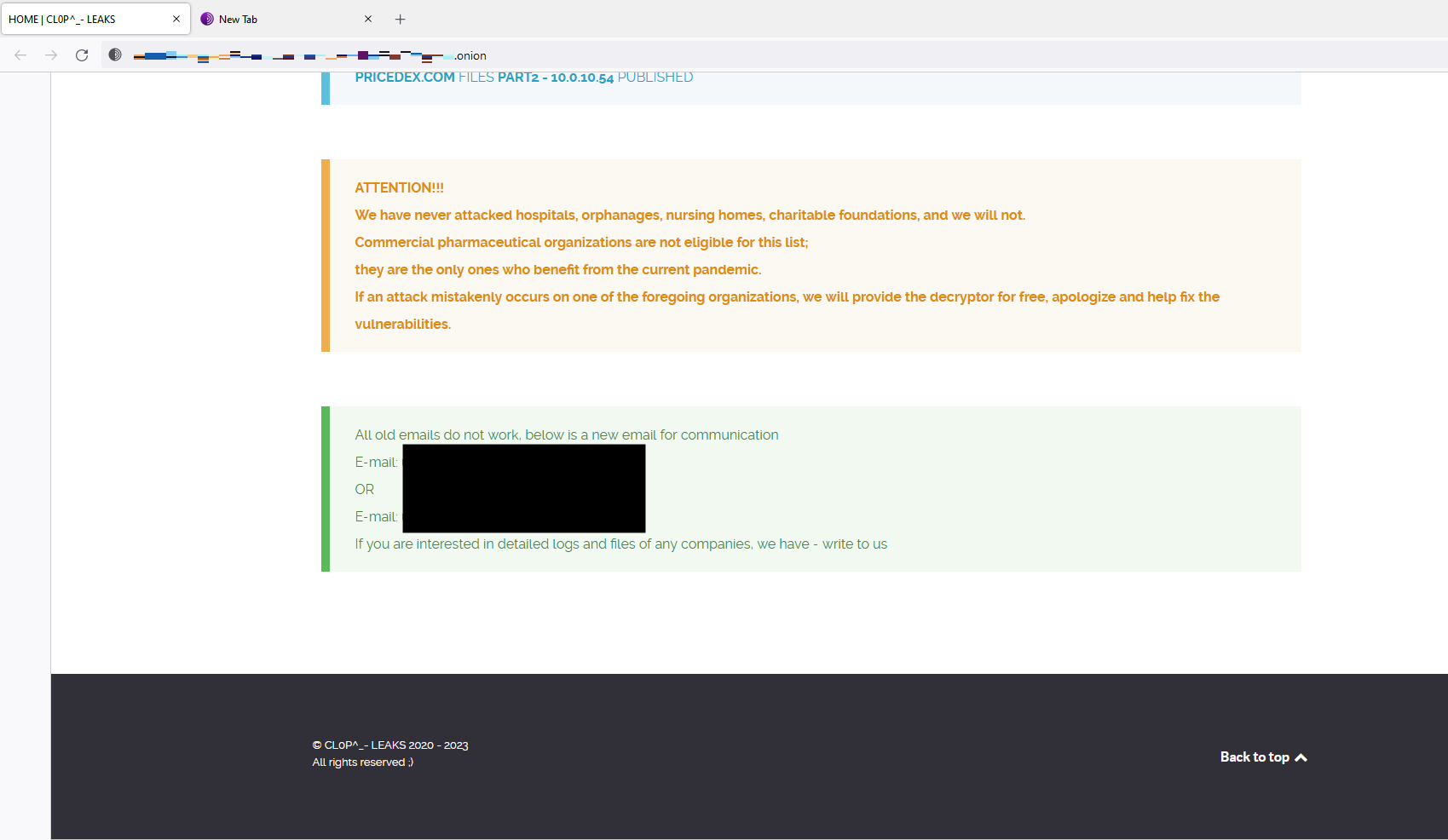
At this time, it is known that the cl0p ransomware gang is actively exploiting MOVEit. In an announcement on the cl0p TOR site, they are claiming to have exploited hundreds of organizations and provided an email to request validation if they have stolen any of your data. They are offering to provide a small sample size of data as confirmation that the data they have is valid, with a price for them to delete all of the data. The attackers will publish a list of victims on June 14th if they have not yet heard from them. Any organization which does not pay within 3 days, the attackers are threatening to release all information.
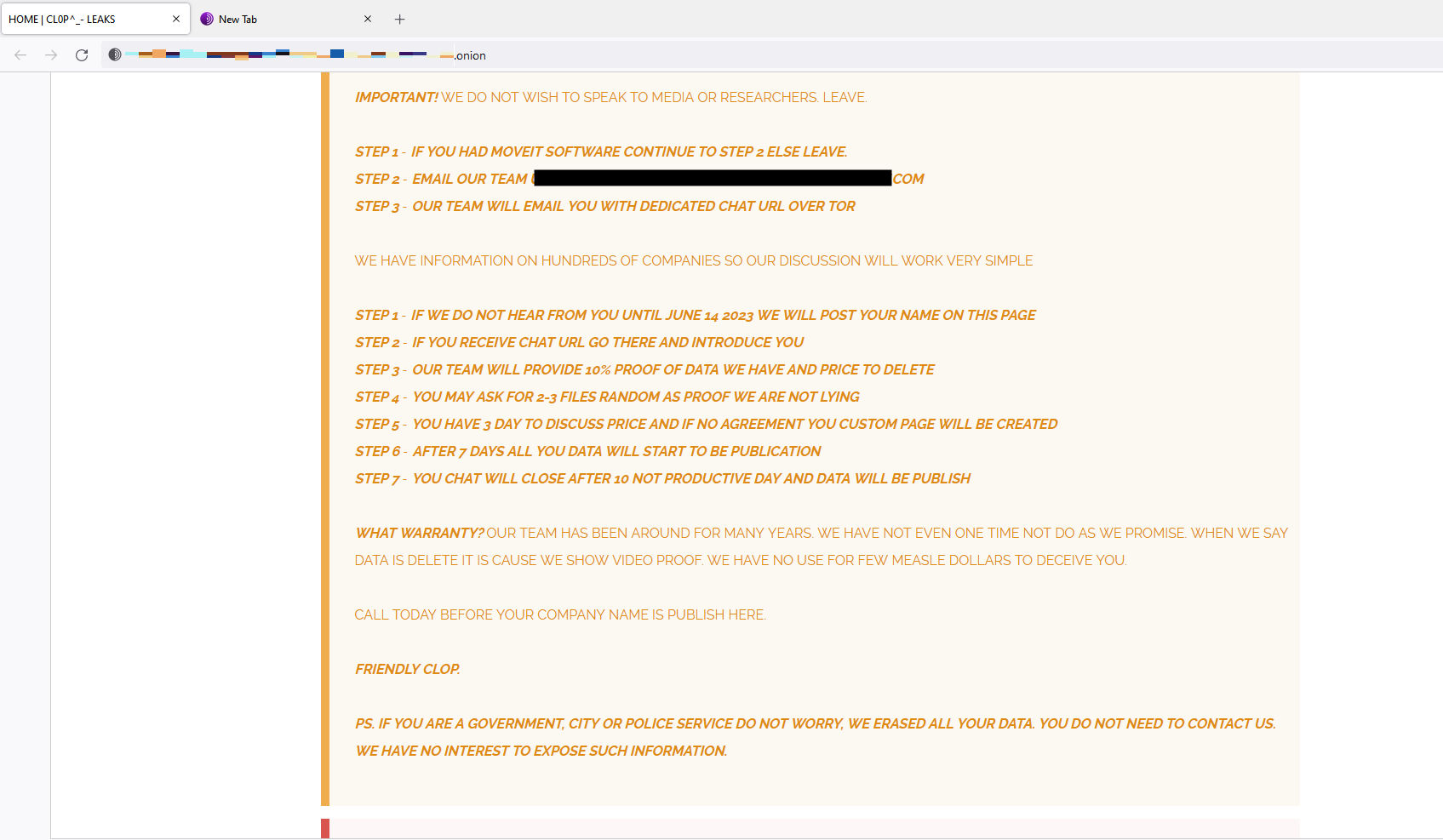
The attackers are claiming that all government, city, or police service organizations have already had their data deleted and will not be published. Cl0p has also claimed they do not attack hospitals, orphanages, nursing homes, or charitable foundations. If an organization is in this group, their data may also be eligible to be deleted free of charge.
Detecting the Vulnerability
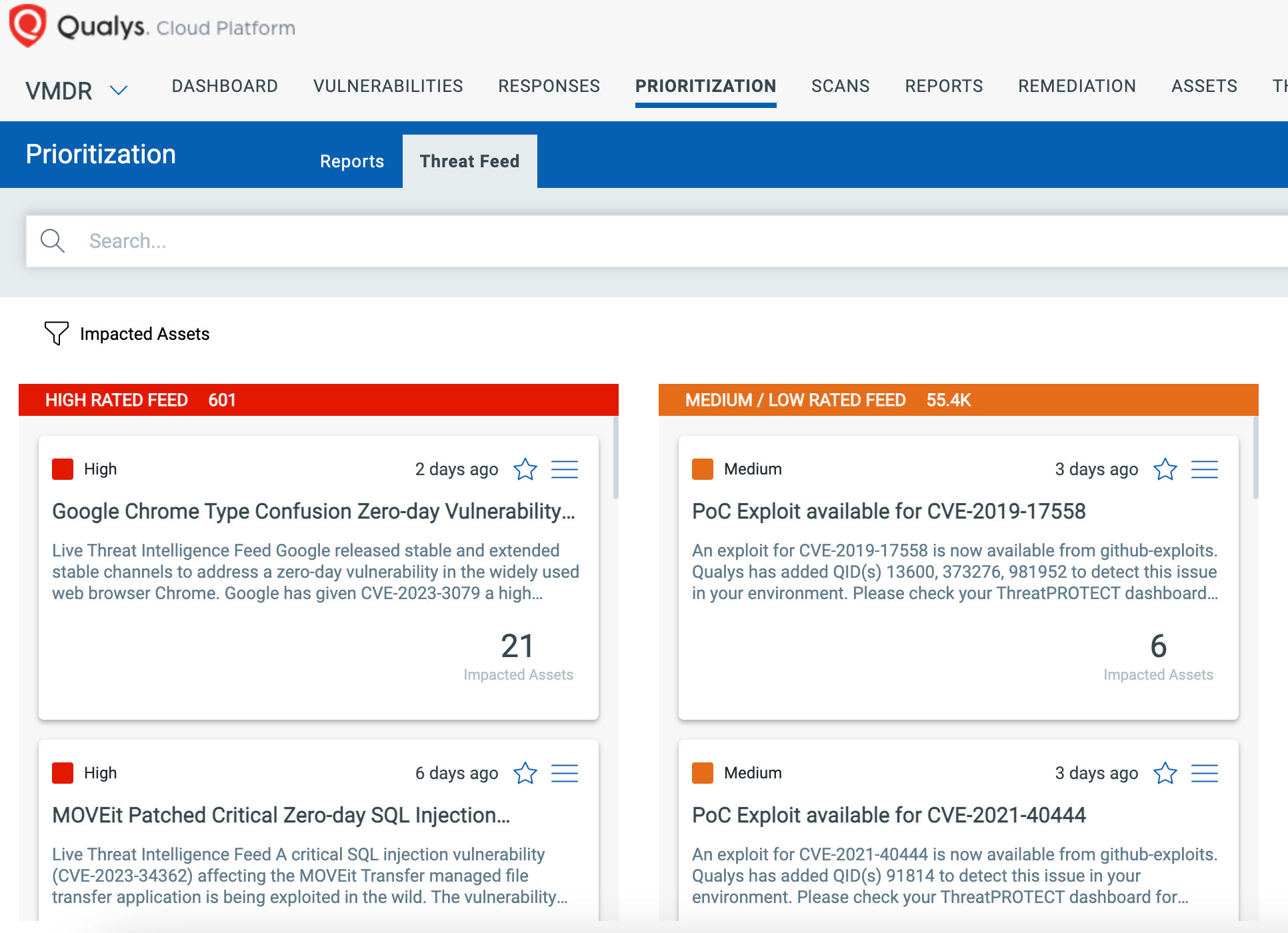
Qualys Threat Research Unit released QID 378543 which customers can scan their devices to detect vulnerable assets.

VMDR also enables you to stay on top of these threats proactively via the ‘live feed’ provided for threat prioritization. With ‘live feed’ updated for all emerging high and medium risks, you can clearly see the impacted hosts against threats. With this risk-based prioritization, you can quickly identify assets that are impacted by critical vulnerabilities like these and others as soon as they are announced.
Users of CyberSecurity Asset Management (CSAM) can quickly query their software inventory to discover instances of the Progress MOVEit Transfer product in their organization with the following QQL query:
software:(name:”Progress MOVEit Transfer”)
Remediating the Vulnerability
The MOVEit vulnerability was patched in the following release versions:
- MOVEit Transfer 2023.0.1
- MOVEit Transfer 2022.1.5
- MOVEit Transfer 2022.0.4
- MOVEit Transfer 2021.1.4
- MOVEit Transfer 2021.0.6
Users should follow the steps which are provided in the MOVEit Security Advisory in order to successfully provide remediation. These steps include the following:
- Disable all HTTP and HTTPS traffic to your MOVEit Transfer environment
- Search for IOCs, Delete, and Reset Account Credentials
- Apply the Patch
- Re-Enable all HTTP and HTTPS traffic to your MOVEit Transfer environment
- Verify all of the files have been successfully deleted, and no unauthorized accounts remain.
- Continuously monitor network, endpoints, and logs for IoCs (Indicators of Compromise) as listed in the advisory.
Leverage Qualys Custom Assessment and Remediation (CAR) To Mitigate Risk
Qualys CAR provides the mitigation utility for MoveIT CVE-2023-34362, as part our Script Library.
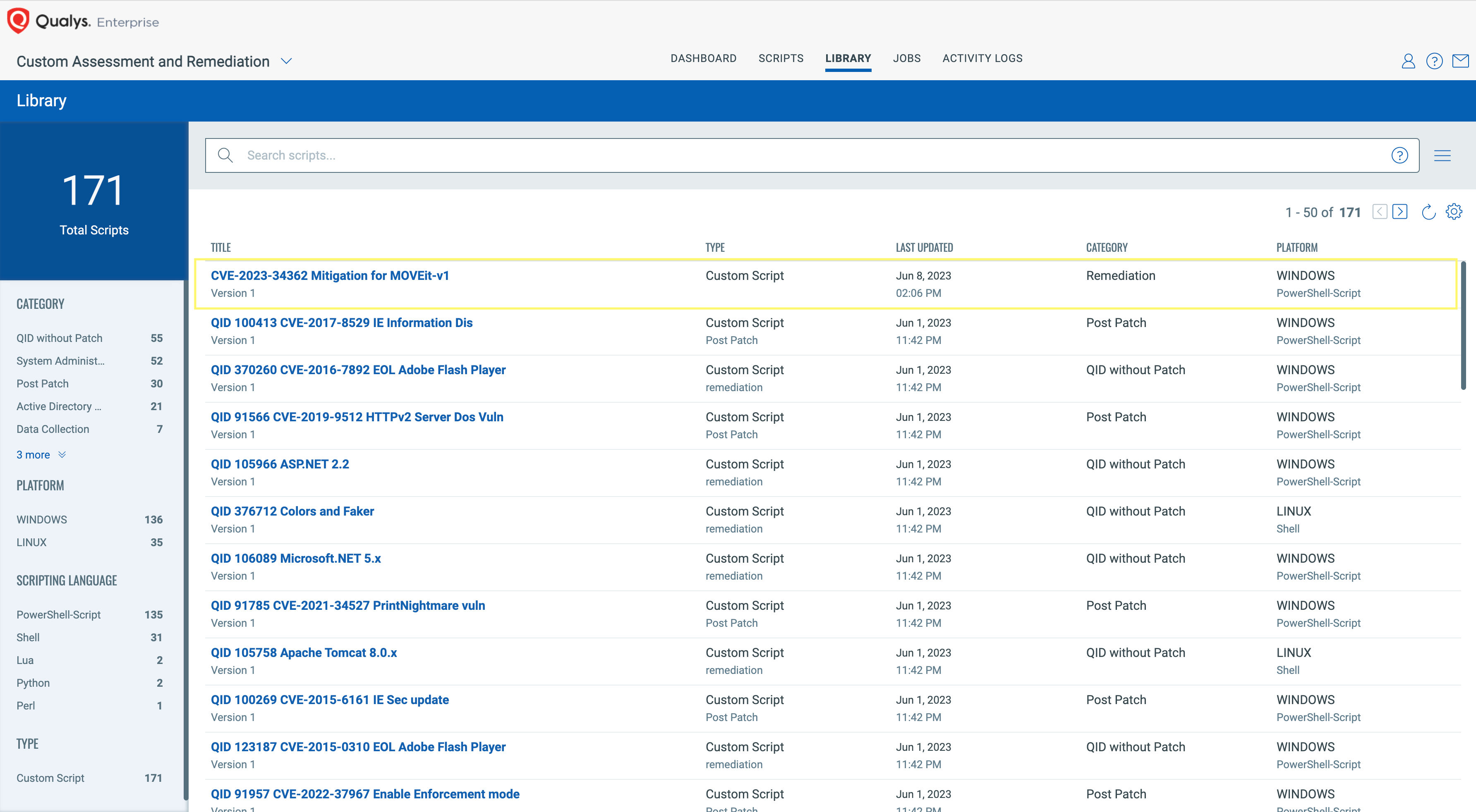
You can just import the script from Library, approve it and execute it on the hosts where Qualys Cloud Agent is deployed.
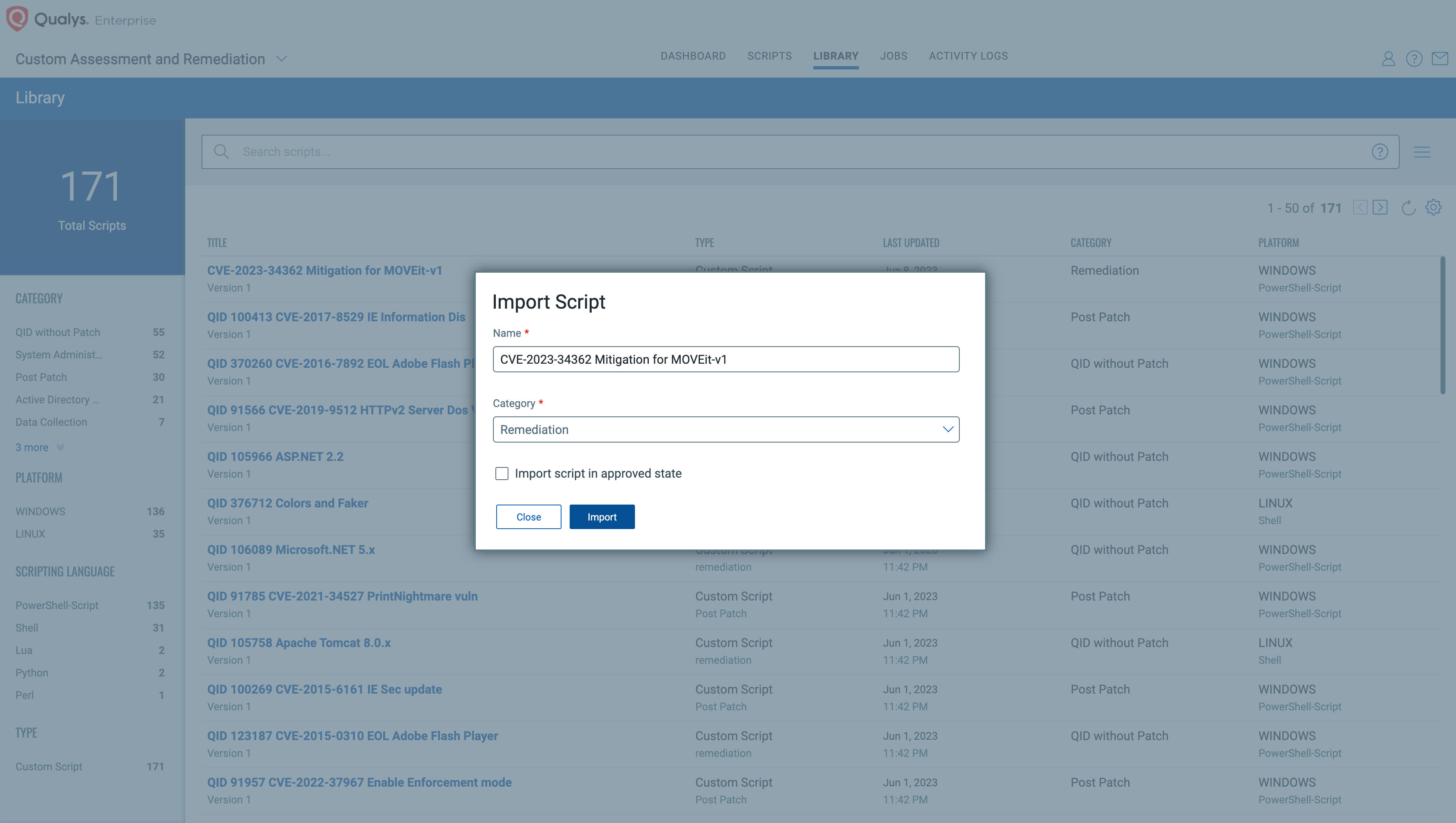
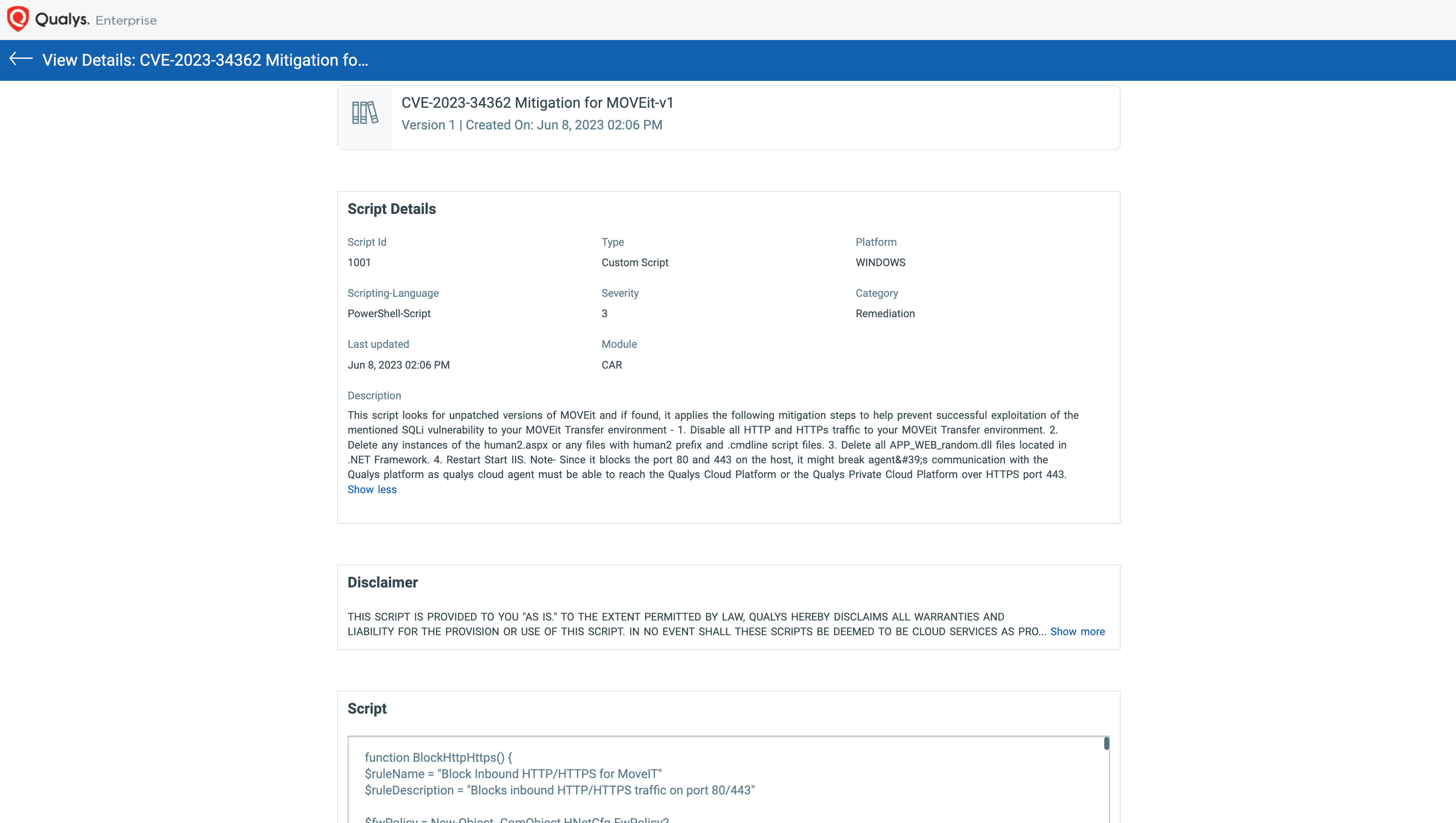
This script looks for unpatched versions of MOVEit and if found, it applies the following mitigation steps as per https://community.progress.com/s/article/MOVEit-Transfer-Critical-Vulnerability-31May2023 to help prevent successful exploitation of the mentioned SQLi vulnerability to your MOVEit Transfer environment.
Start a free trial or contact your TAM to enable CAR for your subscription today!
Detecting Exploitation
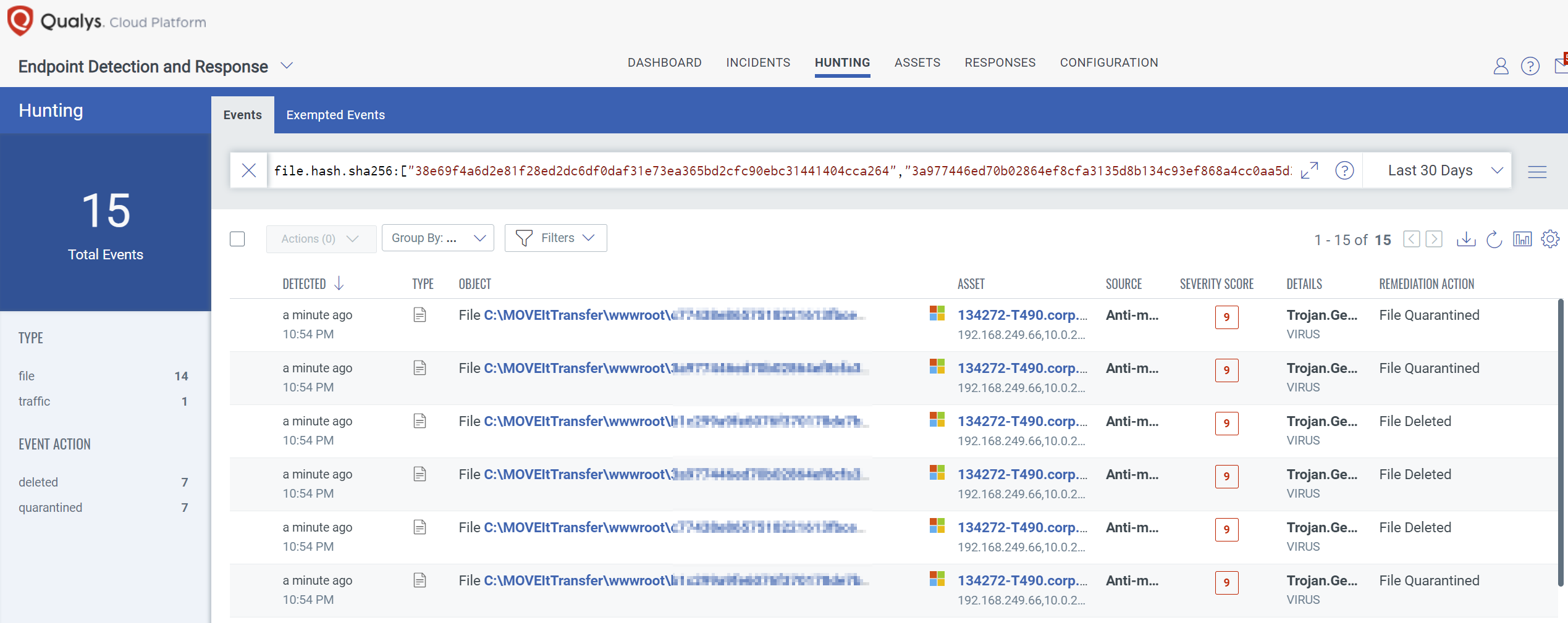
The post-exploitation activities have been documented and can be hunted for in environments which suspect they may have been compromised. Using a product such as Qualys Endpoint Detection and Response (EDR), users can search for the file hashes and file names outlined in the IOC document provided by the MOVEit Security Advisory. For example, a QQL below can find all of the hashes associated with the LEMURLOOT webshell:
file.hash.sha256:[“38e69f4a6d2e81f28ed2dc6df0daf31e73ea365bd2cfc90ebc31441404cca264″,”3a977446ed70b02864ef8cfa3135d8b134c93ef868a4cc0aa5d3c2a74545725b”,”b1c299a9fe6076f370178de7b808f36135df16c4e438ef6453a39565ff2ec272″,”c77438e8657518221613fbce451c664a75f05beea2184a3ae67f30ea71d34f37″,”702421bcee1785d93271d311f0203da34cc936317e299575b06503945a6ea1e0″,”387cee566aedbafa8c114ed1c6b98d8b9b65e9f178cf2f6ae2f5ac441082747a”,”4359aead416b1b2df8ad9e53c497806403a2253b7e13c03317fc08ad3b0b95bf”,”daaa102d82550f97642887514093c98ccd51735e025995c2cc14718330a856f4″,”6015fed13c5510bbb89b0a5302c8b95a5b811982ff6de9930725c4630ec4011d”,”9d1723777de67bc7e11678db800d2a32de3bcd6c40a629cd165e3f7bbace8ead”,”c56bcb513248885673645ff1df44d3661a75cfacdce485535da898aa9ba320d4″,”0ea05169d111415903a1098110c34cdbbd390c23016cd4e179dd9ef507104495″,”d49cf23d83b2743c573ba383bf6f3c28da41ac5f745cde41ef8cd1344528c195″,”5b566de1aa4b2f79f579cdac6283b33e98fdc8c1cfa6211a787f8156848d67ff”,”f0d85b65b9f6942c75271209138ab24a73da29a06bc6cc4faeddcb825058c09d”,”fe5f8388ccea7c548d587d1e2843921c038a9f4ddad3cb03f3aa8a45c29c6a2f”,”9e89d9f045664996067a05610ea2b0ad4f7f502f73d84321fb07861348fdc24a”,”ea433739fb708f5d25c937925e499c8d2228bf245653ee89a6f3d26a5fd00b7a”,”cf23ea0d63b4c4c348865cefd70c35727ea8c82ba86d56635e488d816e60ea45″,”2413b5d0750c23b07999ec33a5b4930be224b661aaf290a0118db803f31acbc5″,”348e435196dd795e1ec31169bd111c7ec964e5a6ab525a562b17f10de0ab031d”,”b9a0baf82feb08e42fa6ca53e9ec379e79fbe8362a7dac6150eb39c2d33d94ad”,”a1269294254e958e0e58fc0fe887ebbc4201d5c266557f09c3f37542bd6d53d7″,”48367d94ccb4411f15d7ef9c455c92125f3ad812f2363c4d2e949ce1b615429a”,”d477ec94e522b8d741f46b2c00291da05c72d21c359244ccb1c211c12b635899″,”3ab73ea9aebf271e5f3ed701286701d0be688bf7ad4fb276cb4fbe35c8af8409″]file.hash.sha256:[“38e69f4a6d2e81f28ed2dc6df0daf31e73ea365bd2cfc90ebc31441404cca264″,”3a977446ed70b02864ef8cfa3135d8b134c93ef868a4cc0aa5d3c2a74545725b”,”b1c299a9fe6076f370178de7b808f36135df16c4e438ef6453a39565ff2ec272″,”c77438e8657518221613fbce451c664a75f05beea2184a3ae67f30ea71d34f37″,”702421bcee1785d93271d311f0203da34cc936317e299575b06503945a6ea1e0″,”387cee566aedbafa8c114ed1c6b98d8b9b65e9f178cf2f6ae2f5ac441082747a”,”4359aead416b1b2df8ad9e53c497806403a2253b7e13c03317fc08ad3b0b95bf”,”daaa102d82550f97642887514093c98ccd51735e025995c2cc14718330a856f4″,”6015fed13c5510bbb89b0a5302c8b95a5b811982ff6de9930725c4630ec4011d”,”9d1723777de67bc7e11678db800d2a32de3bcd6c40a629cd165e3f7bbace8ead”,”c56bcb513248885673645ff1df44d3661a75cfacdce485535da898aa9ba320d4″,”0ea05169d111415903a1098110c34cdbbd390c23016cd4e179dd9ef507104495″,”d49cf23d83b2743c573ba383bf6f3c28da41ac5f745cde41ef8cd1344528c195″,”5b566de1aa4b2f79f579cdac6283b33e98fdc8c1cfa6211a787f8156848d67ff”,”f0d85b65b9f6942c75271209138ab24a73da29a06bc6cc4faeddcb825058c09d”,”fe5f8388ccea7c548d587d1e2843921c038a9f4ddad3cb03f3aa8a45c29c6a2f”,”9e89d9f045664996067a05610ea2b0ad4f7f502f73d84321fb07861348fdc24a”,”ea433739fb708f5d25c937925e499c8d2228bf245653ee89a6f3d26a5fd00b7a”,”cf23ea0d63b4c4c348865cefd70c35727ea8c82ba86d56635e488d816e60ea45″,”2413b5d0750c23b07999ec33a5b4930be224b661aaf290a0118db803f31acbc5″,”348e435196dd795e1ec31169bd111c7ec964e5a6ab525a562b17f10de0ab031d”,”b9a0baf82feb08e42fa6ca53e9ec379e79fbe8362a7dac6150eb39c2d33d94ad”,”a1269294254e958e0e58fc0fe887ebbc4201d5c266557f09c3f37542bd6d53d7″,”48367d94ccb4411f15d7ef9c455c92125f3ad812f2363c4d2e949ce1b615429a”,”d477ec94e522b8d741f46b2c00291da05c72d21c359244ccb1c211c12b635899″,”3ab73ea9aebf271e5f3ed701286701d0be688bf7ad4fb276cb4fbe35c8af8409″]
or
parent.name:”w3wp.exe” and process.arguments:”moveitdmz pool”
Discover Vulnerable Instances Using Qualys Web Application Scanning (WAS)
Qualys WAS QID Coverage
Qualys Web Application Security (WAS) can detect vulnerable versions of MOVEit with the following QID:
| QID | Title |
| 150691 | MOVEit Transfer SQL Injection Vulnerability (CVE-2023-34362) |
QID 150691 is a passive check that identifies vulnerable versions of MOVEit.
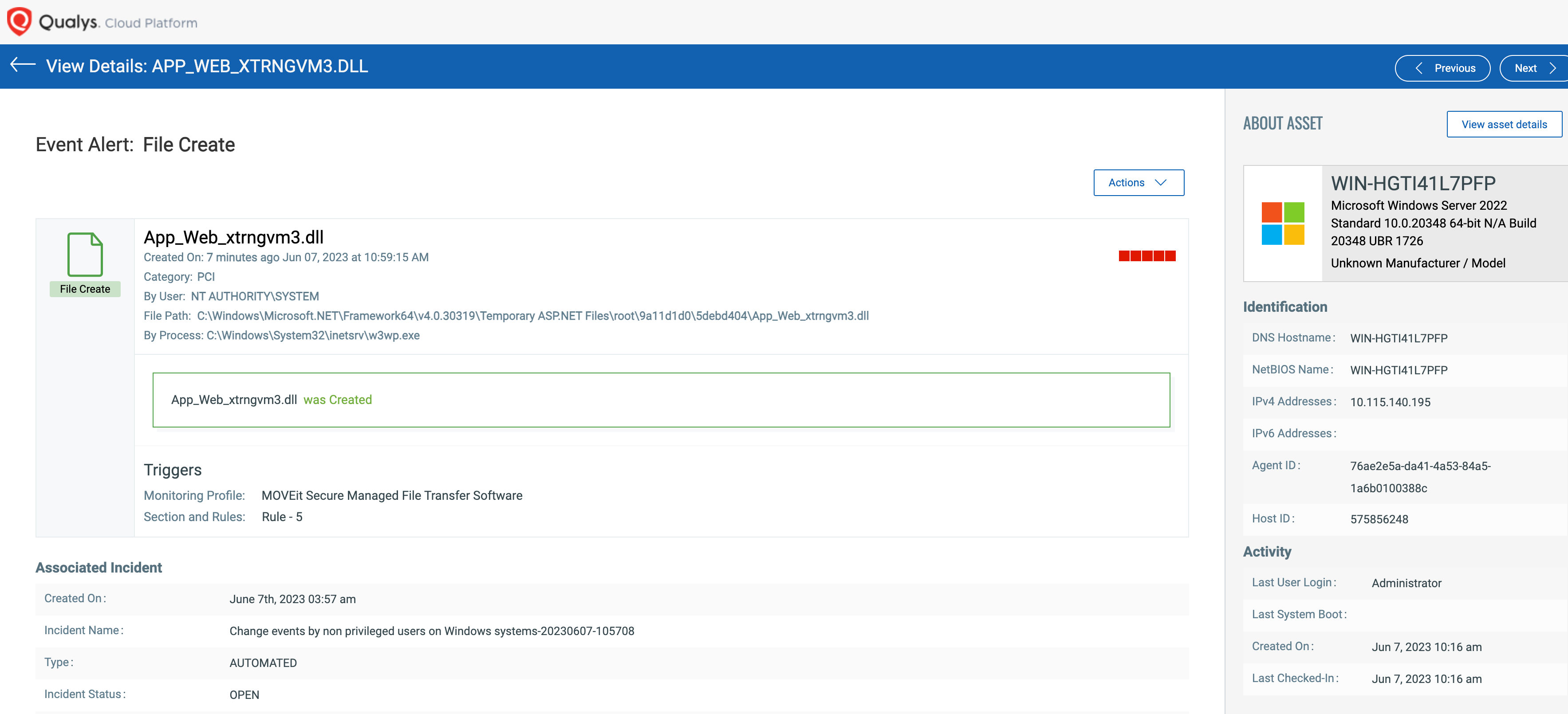
Detection via File Integrity Monitoring
Create a FIM profile that contains the key file paths of the MoveIt application, to be monitored for real-time detection. Once the hosts are assigned and monitoring starts, any activity under monitoring radar would be captured in real time with the ‘who-data’, i.e., the user and process responsible for the change.