Microsoft and Adobe Patch Tuesday, June 2023 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for June 2023
- Adobe Patches for June 2023
- Other Critical Severity Vulnerabilities Patched in June Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response with Patch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
- Qualys Monthly Webinar Series
Microsoft has released June’s edition of Patch Tuesday! This installment of security updates addressed 94 security vulnerabilities in various products, features, and roles.
Microsoft Patch Tuesday for June 2023
No zero-day vulnerabilities known to be exploited in the wild have been fixed in this month’s Patch Tuesday edition. Six of these 94 vulnerabilities are rated as critical and 70 as important. This month’s security updates covered 17 Microsoft Edge (Chromium-based) vulnerabilities patched earlier this month.
Microsoft Patch Tuesday, June edition includes updates for vulnerabilities in Microsoft Office and Components, Microsoft Exchange Server, Win32K, Windows TPM Device Driver, Windows Remote Procedure Call Runtime, Windows PGM, Microsoft Printer Drivers, Windows Hello, Windows Kernel, DNS Server, Windows SMB, Windows Server Service, Microsoft Power Apps, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The June 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 10 | Important: 9 |
| Denial of Service Vulnerability | 10 | Critical: 1 Important: 9 |
| Elevation of Privilege Vulnerability | 17 | Critical: 1 Important: 15 |
| Information Disclosure Vulnerability | 5 | Important: 5 |
| Remote Code Execution Vulnerability | 32 | Critical: 4 Important: 24 |
| Security Feature Bypass Vulnerability | 3 | Important: 4 |
| Microsoft Edge (Chromium-based) | 17 |
Adobe Patches for June 2023
Adobe has released only Four security advisories for June. The advisories addressed 18 critical and important vulnerabilities in Adobe Experience Manager, Adobe Commerce, Adobe Animate, and Substance 3D Designer. Four of the 18 vulnerabilities are rated as critical. Successful exploitation of the vulnerabilities could lead to arbitrary code execution and security feature bypass.
Other Critical Severity Vulnerabilities Patched in June Patch Tuesday Edition
CVE-2023-29357: Microsoft SharePoint Server Elevation of Privilege Vulnerability
Microsoft SharePoint is a web-based document management and collaboration platform that helps share files, data, news, and resources. The application transforms business processes by providing simple sharing and seamless collaboration.
An attacker with access to spoofed JWT authentication tokens may exploit this vulnerability to execute a network attack. A successful network attack will bypass authentication and allow an attacker to gain access as an authenticated user. On successful exploitation of the vulnerability, an attacker would gain administrator privileges.
CVE-2023-24897: .NET, .NET Framework, and Visual Studio Remote Code Execution Vulnerability
To exploit this vulnerability, an attacker must convince a user to download and open a specially crafted file from a website through social engineering. The malicious link will lead to a local attack on their computer and allow an attacker to perform remote code execution.
CVE-2023-32013: Windows Hyper-V Denial of Service Vulnerability
Windows Hyper-V is a piece of software that allows hardware virtualization. IT professionals and software developers use virtualization to test software on multiple operating systems. Hyper-V enables working professionals to perform these tasks smoothly. With the help of Hyper-V, one can create virtual hard drives, virtual switches, and numerous different virtual devices, all of which can be added to virtual machines.
To exploit this vulnerability, an attacker must prepare the target environment to improve exploit reliability. A network attacker with low privileges may exploit this vulnerability in a low-complexity attack to cause a denial of service (DoS) situation.
CVE-2023-29363, CVE-2023-32014, and CVE-2023-32015: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
Pragmatic General Multicast (PGM), a.k.a. ‘reliable multicast,’ is a scalable receiver-reliable protocol. PGM allows receivers to detect loss, request retransmission of lost data, or notify an application of unrecoverable loss. PGM is best suited for applications that require duplicate-free multicast data delivery from multiple sources to multiple receivers.
Windows message queuing service must be running in a PGM Server environment to exploit the vulnerability. When the service is running, an attacker may send a specially crafted file over the network to achieve remote code execution. The Windows message queuing service is a Windows component that needs to be enabled for a system to be exploitable by this vulnerability. This feature can be added with the help of the Control Panel.
Other Microsoft Vulnerability Highlights
- CVE-2023-28310 exists in Exchange Server that may allow an authenticated attacker to perform remote code execution on the affected system with the help of a PowerShell remoting session. An attacker must be connected to the same internet as the Exchange server to exploit the vulnerability.
- CVE-2023-29358 and CVE-2023-29359 affect the Microsoft Windows graphics device interface (GDI) that allows applications to use graphics and formatted texts on video displays and printers. An attacker could gain SYSTEM privileges on successful exploitation of the vulnerabilities.
- CVE-2023-29360 is an elevation of privilege vulnerability that affects the Windows Trusted Platform Module (TPM) Device Driver. On successful exploitation of the vulnerability, an attacker could gain SYSTEM privileges.
- CVE-2023-29361 is an elevation of privilege vulnerability that affects Windows Cloud Files Mini Filter Driver. To exploit this vulnerability, an attacker must win a race condition. An attacker who exploits this vulnerability could gain SYSTEM privileges on the affected system.
- CVE-2023-29371 exists in the Microsoft Windows graphics device interface (GDI). The vulnerability may allow an attacker to gain SYSTEM privileges on successful exploitation.
- CVE-2023-32031 is a remote code execution vulnerability that affects Microsoft Exchange Server. An authenticated attacker may use the vulnerability to trigger malicious code in the context of the server’s account through a network call.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Azure DevOps, .NET and Visual Studio, Microsoft Dynamics, Windows CryptoAPI, .NET Framework, .NET Core, NuGet Client, Microsoft Edge (Chromium-based), Windows NTFS, Windows Group Policy, Remote Desktop Client, SysInternals, Windows DHCP Server, Microsoft Office SharePoint, Windows GDI, Windows Cloud Files Mini Filter Driver Windows Authentication Methods, Microsoft Windows Codecs Library, Windows Geolocation Service, Windows OLE, Windows Filtering, Microsoft WDAC OLE DB provider for SQL, Windows ODBC Driver, Windows Resilient File System (ReFS), Windows Collaborative Translation Framework, Windows Bus Filter Driver, Windows iSCSI, Windows Container Manager Service, Windows Hyper-V, and Windows Installer.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
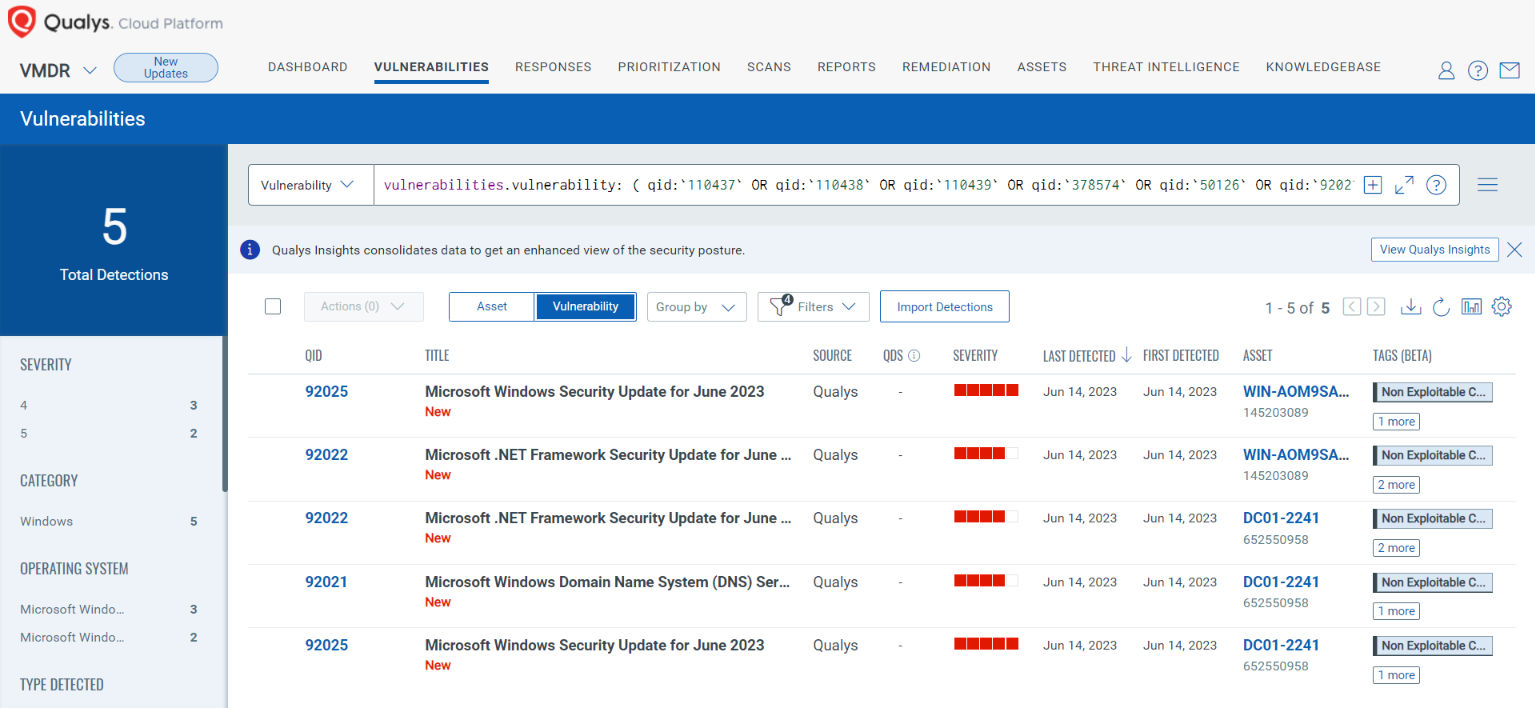
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110437` OR qid:`110438` OR qid:`110439` OR qid:`378574` OR qid:`50126` OR qid:`92021` OR qid:`92022` OR qid:`92023` OR qid:`92024` OR qid:`92025` OR qid:`92027`)
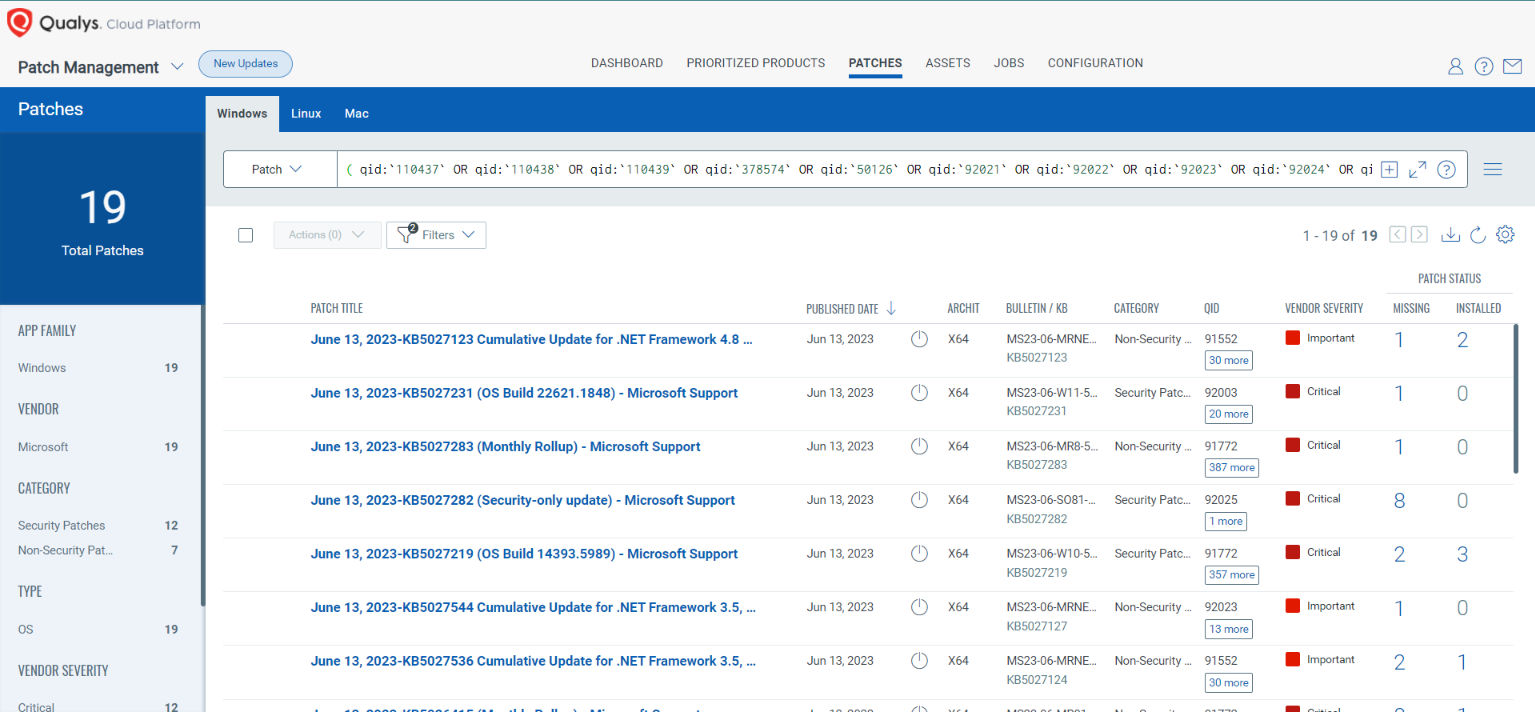
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110437` OR qid:`110438` OR qid:`110439` OR qid:`378574` OR qid:`50126` OR qid:`92021` OR qid:`92022` OR qid:`92023` OR qid:`92024` OR qid:`92025` OR qid:`92027`)
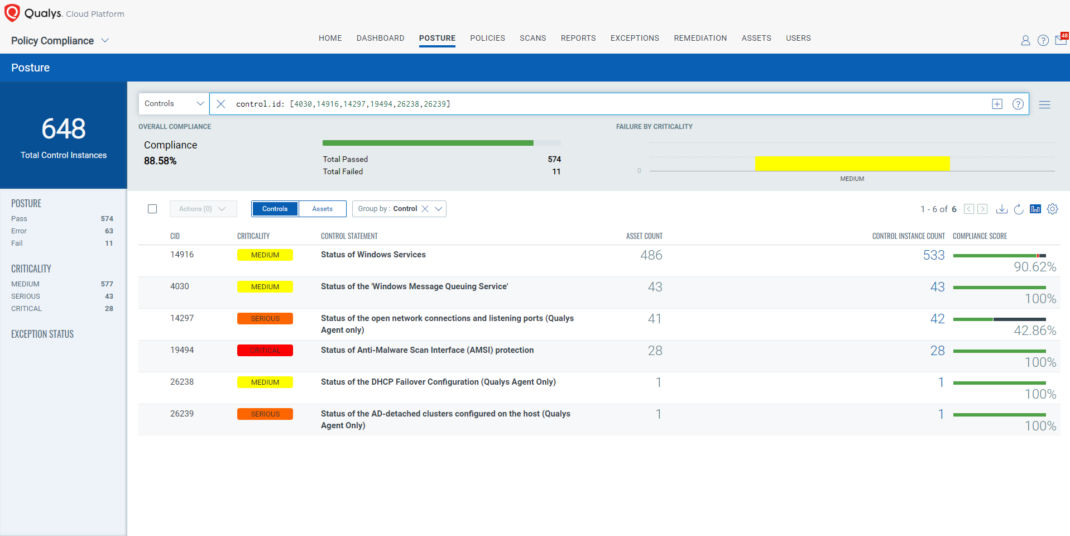
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of vendor-suggested mitigation or workaround.
Mitigation refers to a setting, standard configuration, or general best practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is sometimes used temporarily for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-29357: Microsoft SharePoint Server Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
19494 Status of Anti-Malware Scan Interface (AMSI) protection
CVE-2023-32015, CVE-2023-32014, and CVE-2023-29363: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
4030 `Status of the ‘Windows Message Queuing Service’
14916 Status of Windows Services
14297 Status of the open network connections and listening ports (Qualys Agent only)
CVE-2023-29355: DHCP Server Service Information Disclosure Vulnerability
This vulnerability has a CVSSv3.1 5.3 / 4.6
Policy Compliance Control IDs (CIDs):
26238 Status of the DHCP Failover Configuration
CVE-2023-32022: Windows Server Service Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 7.6 / 6.6
Policy Compliance Control IDs (CIDs):
26239 Status of the AD-detached clusters configured on the host (Qualys Agent Only)
CVE-2023-32021: Windows SMB Witness Service Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 7.1 / 6.2
Policy Compliance Control IDs (CIDs):
26239 Status of the AD-detached clusters configured on the host (Qualys Agent Only)
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [4030,14916,14297,19494,26238,26239]
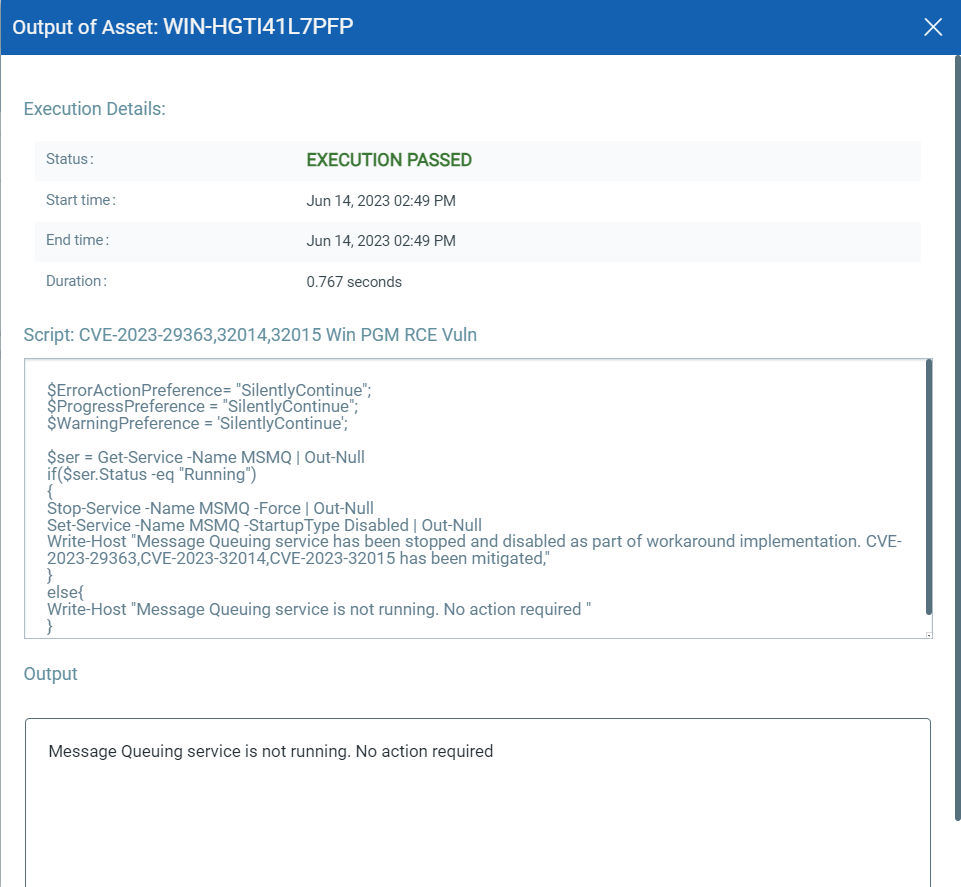
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
CVE-2023-29363, CVE-2023-32014, CVE-2023-32015 Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
The next Patch Tuesday falls on July 11, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the ‘This Month in Vulnerabilities and Patches webinar.’
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.