Microsoft and Adobe Patch Tuesday, July 2023 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for July 2023
- Adobe Patches for July 2023
- Zero-day Vulnerabilities Patched in July Patch Tuesday Edition
- Other Critical Severity Vulnerabilities Patched in July Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response with Patch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
- Qualys Monthly Webinar Series
Microsoft has released July’s edition of Patch Tuesday! This installment of security updates addressed 132 security vulnerabilities in various products, features, and roles.
Microsoft Patch Tuesday for July 2023
This month’s Patch Tuesday edition has fixed six zero-day vulnerabilities known to be exploited in the wild. Nine of these 132 vulnerabilities are rated as critical and 122 as important. Microsoft has not addressed any vulnerabilities related to Microsoft Edge (Chromium-based) in this month’s Patch Tuesday Edition. This month’s security updates included one Defense-in-depth update (ADV230001) and one for the Trend Micro EFI Modules (ADV230002).
CISA has added four zero-day vulnerabilities (CVE-2023-32046, CVE-2023-32049, CVE-2023-35311, and CVE-2023-36874) to its Known Exploited Vulnerabilities Catalog and requested users to patch it before August 1, 2023.
Microsoft Patch Tuesday, July edition includes updates for vulnerabilities in Microsoft Office and Components, Windows Layer-2 Bridge Network Driver, Windows Local Security Authority (LSA), Windows Media, Windows Message Queuing, Windows MSHTML Platform, Windows Netlogon, Win32K, Microsoft Power Apps, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The July 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 7 | Important: 7 |
| Denial of Service Vulnerability | 22 | Important: 22 |
| Elevation of Privilege Vulnerability | 33 | Important: 33 |
| Information Disclosure Vulnerability | 19 | Important: 19 |
| Remote Code Execution Vulnerability | 37 | Critical: 8 Important: 29 |
| Security Feature Bypass Vulnerability | 13 | Critical: 1 Important: 12 |
Adobe Patches for July 2023
Adobe has released two security advisories in this month’s updates. The advisories addressed 15 vulnerabilities in Adobe InDesign and Adobe ColdFusion. Out of 15 vulnerabilities, only three are rated as critical. The critical severity vulnerabilities could lead to arbitrary code execution and security feature bypass.
Zero-day Vulnerabilities Patched in July Patch Tuesday Edition
CVE-2023-32046: Windows MSHTML Platform Elevation of Privilege Vulnerability
Windows MSHTML is a browser engine that renders web pages frequently connected to Internet Explorer. Even though the Internet Explorer (IE) 11 desktop application has reached the end of support, MSHTML vulnerabilities are still relevant today and are being patched by Microsoft.
The vulnerability can be exploited in both email and web-based attack scenarios.
- In an email attack scenario, an attacker must send the specially crafted file to the users and convince them to open it.
- In a web-based attack scenario, an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) containing a specially crafted file to exploit the vulnerability.
CVE-2023-36874: Windows Error Reporting Service Elevation of Privilege Vulnerability
Windows Error Reporting is an event-based feedback infrastructure designed to collect information on the issues that Windows detects. The service reports the information to Microsoft and provides users with available solutions.
To exploit the vulnerability, an attacker must have local access to the targeted machine, and the user must have permission to create folders and performance traces on the device, with restricted privileges that regular users have by default. On successful exploitation, an attacker could gain administrator privileges.
CVE-2023-35311: Microsoft Outlook Security Feature Bypass Vulnerability
An attacker must send a specially crafted URL to exploit this vulnerability. An attacker could bypass the Microsoft Outlook Security Notice prompt on successful exploitation.
CVE-2023-32049: Windows SmartScreen Security Feature Bypass Vulnerability
An attacker must make the users click on a specially crafted URL to exploit the vulnerability. An attacker could bypass the Open File – Security Warning prompt on successful exploitation.
CVE-2023-36884: Office and Windows HTML Remote Code Execution Vulnerability
Microsoft is aware of the exploitation attempts of the vulnerability by using specially-crafted Microsoft Office documents. An attacker may craft a Microsoft Office document to perform remote code execution on the target system.
In the blog, Microsoft mentioned that the attacks were targeted against defense and government entities in Europe and North America. Russia-based cybercriminal group Storm-0978 has exploited the vulnerability to deliver a backdoor similar to RomCom.
Microsoft has not released any patch to address the vulnerability as of now. There is mitigation available for the vulnerability.
ADV230001: Guidance on Microsoft Signed Drivers Being Used Maliciously
Microsoft Windows Hardware Developer Program certified drivers were used to exploit developer program accounts in post-exploitation activity. Microsoft has confirmed that no Microsoft account has been exploited in the attacks.
Sophos, Trend Micro, and Cisco have reported the exploitation activities to Microsoft. In the exploitation attempts, the attackers had administrator permissions on the exploited systems before using the drivers. Further research found that multiple Microsoft Partner Centre (MPC) developer accounts were involved in uploading harmful drivers to get a Microsoft signature. In response to the attacks, Microsoft immediately suspended all the developer accounts involved in the attacks.
Other Critical Severity Vulnerabilities Patched in July Patch Tuesday Edition
CVE-2023-35315: Windows Layer-2 Bridge Network Driver Remote Code Execution Vulnerability
An unauthenticated attacker must send specially crafted file operation requests to a Windows Server configured as a Layer-2 Bridge to exploit the vulnerability. An attacker must gain access to the restricted network before running an attack. Successful exploitation of the vulnerability will lead to remote code execution on the target system.
CVE-2023-35352: Windows Remote Desktop Security Feature Bypass Vulnerability
Windows Remote Desktop helps to connect Windows, Android, or iOS devices to a Windows 10 PC from afar.
Successful exploitation of the vulnerability would allow an attacker to bypass certificate or private key authentication when establishing a remote desktop protocol session. A remote attacker may exploit this vulnerability in a low-complexity attack.
CVE-2023-35365, CVE-2023-35366, and CVE-2023-35367: Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability
Routing and Remote Access service (RRAS) is an open platform for networking and routing that provides dial-up or VPN connections for remote users or site-to-site connectivity. It provides routing services to organizations via secure VPN connections via the Internet, local area networks (LAN), wide area networks (WAN), or both.
To exploit this vulnerability, an attacker must send specially crafted packets to a server configured with the Routing and Remote Access Service running.
CVE-2023-33157: Microsoft SharePoint Remote Code Execution Vulnerability
Microsoft SharePoint is a web-based document management and collaboration platform that strengthens teamwork. The application helps in sharing files, data, news, and resources.
An attacker must be authenticated to the target site as at least a Site Member and have Manage List permissions to exploit this vulnerability. On successful exploitation, an attacker may perform a remote attack to gain access to the victim’s information and the ability to alter data. An attacker may also cause downtime for the targeted environment by exploiting the vulnerability.
CVE-2023-33160: Microsoft SharePoint Server Remote Code Execution Vulnerability
To exploit this vulnerability, an attacker must be authenticated to the target site as the Site Member at the least. On successful exploitation, an attacker may perform a remote attack to get access to the victim’s information and the ability to alter data. An attacker may also cause downtime for the targeted environment by exploiting the vulnerability.
An attacker could use deserialization of unsafe data input vulnerability to exploit the vulnerable APIs. To exploit the vulnerability, a user must use a vulnerable API on an affected version of SharePoint with specially crafted input, potentially leading to remote code execution on the SharePoint Server.
CVE-2023-32057: Microsoft Message Queuing Remote Code Execution Vulnerability
Message Queuing (MSMQ) is a protocol developed by Microsoft to ensure reliable communication between Windows computers across different networks, even when a host is temporarily not connected (by maintaining a message queue of undelivered messages).
An attacker must send a malicious MSMQ packet to an MSMQ server to exploit this vulnerability. On successful exploitation, an attacker may perform remote code execution on the server side.
CVE-2023-35297: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
Pragmatic General Multicast (PGM) is a multicast computer network transport protocol appropriate for multi-receiver file transfer applications. PGM provides a reliable sequence of packets to multiple recipients simultaneously.
An attack can be performed only on the systems connected to the same network segment as the attacker. The attack cannot be performed across multiple networks (for example, a WAN).
Other Microsoft Vulnerability Highlights
- CVE-2023-21526 is an information disclosure vulnerability in Windows Netlogon. The vulnerability can be exploited in a man-in-the-middle (MITM) attack. To read or manipulate network communications, the attacker must insert themself into the logical network channel that connects the target with the requested resource. A successful exploit may lead to interception and potential modification of traffic between client and server systems.
- CVE-2023-33134 is a remote code execution vulnerability in the Microsoft SharePoint Server. An attacker must have the “Use Remote Interfaces” and “Add and Customize Pages” permissions to exploit this vulnerability on a Policy Center site. In a network-based attack, an attacker must be authenticated to a SharePoint Online tenant associated with a hybrid deployment to tamper with data. The vulnerability is exploited when this altered data is synchronized to the on-premises server. On the on-premises server, the attacker’s code will be executed in the context of the SharePoint timer service.
- CVE-2023-35312 is an elevation of privilege vulnerability in Microsoft VOLSNAP.SYS. Successful exploitation of the vulnerability would allow an attacker to gain ADMINISTRATOR privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, .NET and Visual Studio, ASP.NET and .NET, Azure Active Directory, Azure DevOps, Microsoft Azure Kubernetes Service, Microsoft Dynamics, Microsoft Graphics Component, Microsoft Media-Wiki Extensions, Microsoft Printer Drivers, Microsoft Windows Codecs Library, Mono Authenticode, Paint 3D, DNS Server, Service Fabric, Visual Studio Code, Windows Active Directory Certificate Services, Windows Active Template Library, Windows Admin Center, Windows App Store, Windows Authentication Methods, Windows CDP User Components, Windows Certificates, Windows Clip Service, Windows Cloud Files Mini Filter Driver, Windows Cluster Server, Windows CNG Key Isolation Service, Windows Common Log File System Driver, Windows Connected User Experiences and Telemetry, Windows CryptoAPI, Windows Cryptographic Services, Windows Defender, Windows Failover Cluster, Windows Geolocation Service, Windows HTTP.sys, Windows Image Acquisition, Windows Installer, Windows Kernel, Windows Layer 2 Tunneling Protocol, Windows Network Load Balancing, Windows NT OS Kernel, Windows ODBC Driver, Windows OLE, Windows Online Certificate Status Protocol (OCSP) SnapIn, Windows Partition Management Driver, Windows Peer Name Resolution Protocol, Windows PGM, Windows Print Spooler Components, Windows Remote Desktop, Windows Remote Procedure Call, Windows Routing and Remote Access Service (RRAS), Windows Server Update Service, Windows SmartScreen, Windows SPNEGO Extended Negotiation, Windows Transaction Manager, Windows Update Orchestrator Service, Windows VOLSNAP.SYS, Windows Volume Shadow Copy, and Windows Win32K.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
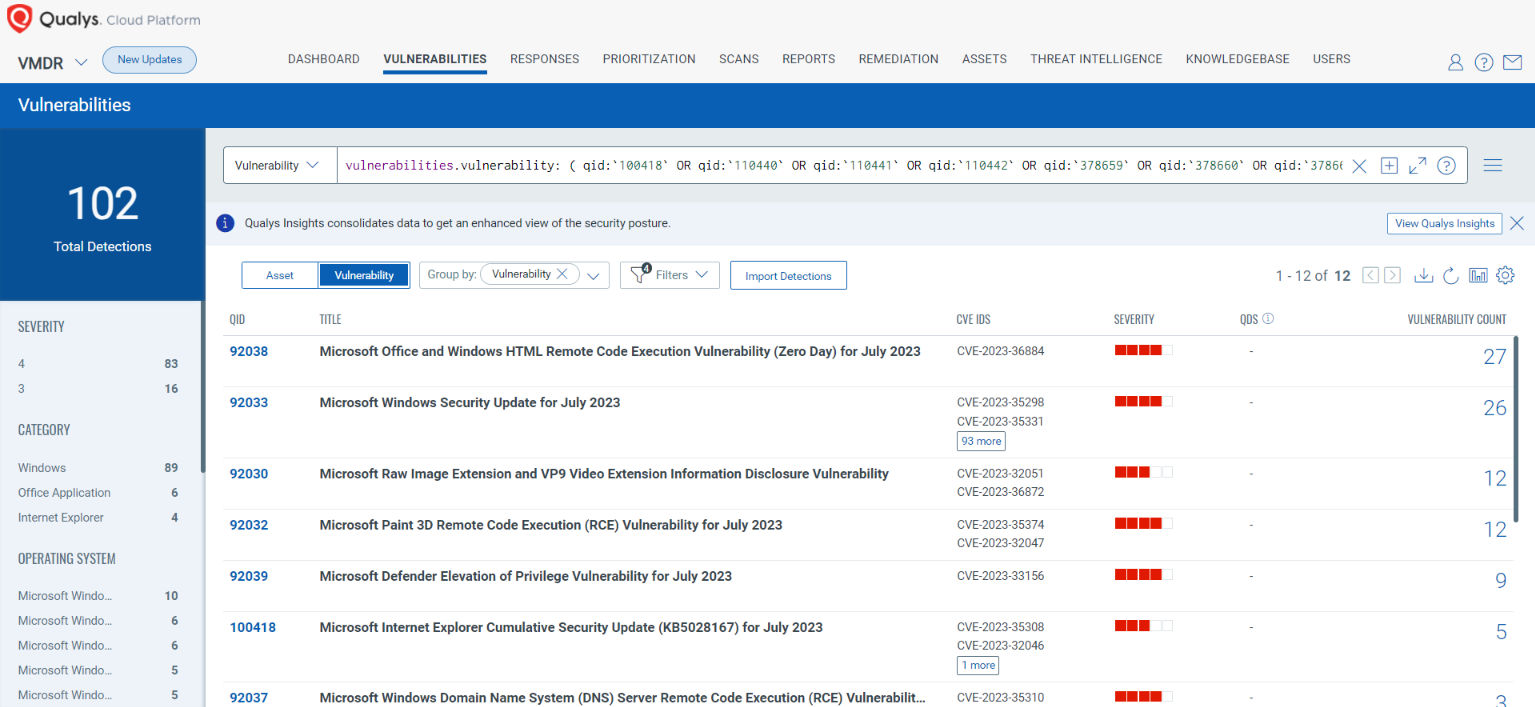
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`100418` OR qid:`110440` OR qid:`110441` OR qid:`110442` OR qid:`378659` OR qid:`378660` OR qid:`378661` OR qid:`92030` OR qid:`92031` OR qid:`92032` OR qid:`92033` OR qid:`92033` OR qid:`92034` OR qid:`92035` OR qid:`92036` OR qid:`92037` OR qid:`92038` OR qid:`92039` OR qid:`92040` )
Rapid Response with Patch Management (PM)
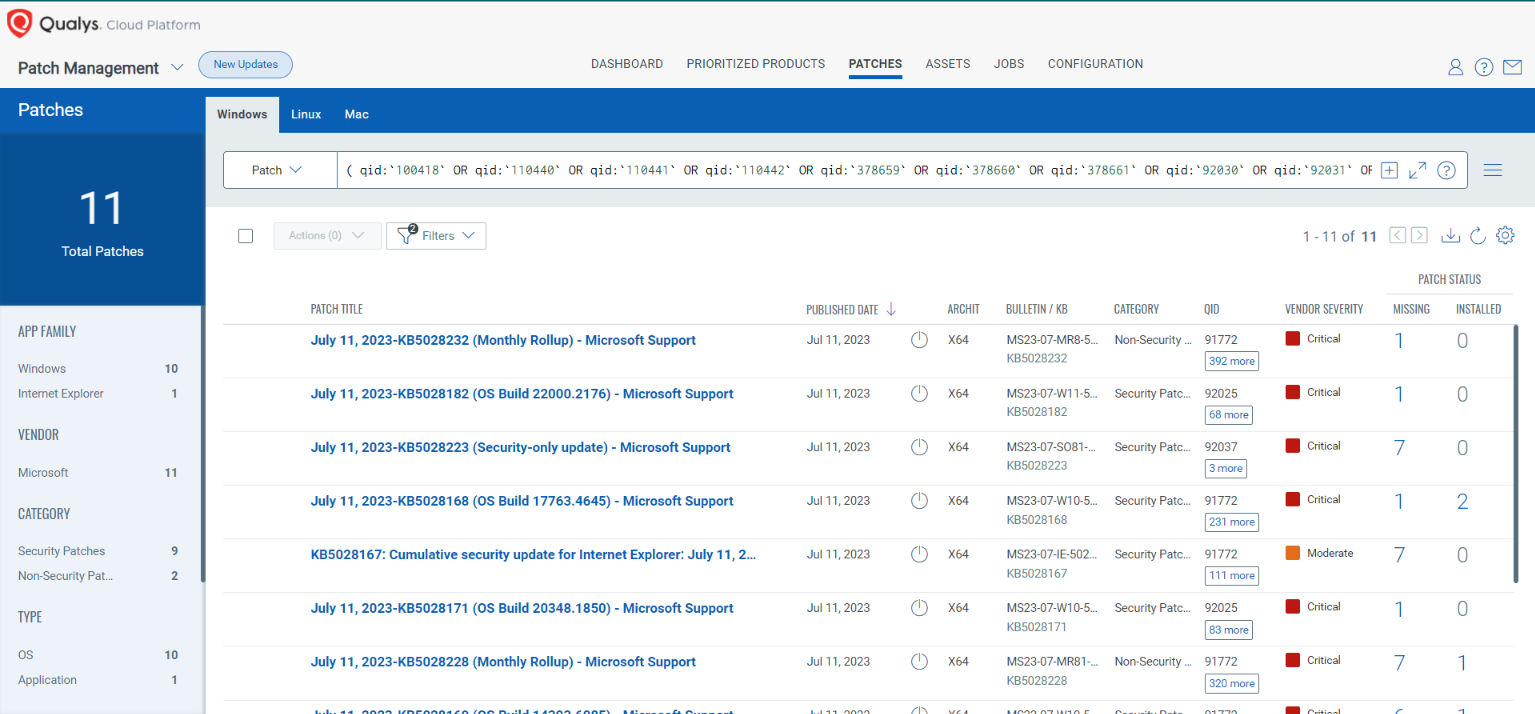
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`100418` OR qid:`110440` OR qid:`110441` OR qid:`110442` OR qid:`378659` OR qid:`378660` OR qid:`378661` OR qid:`92030` OR qid:`92031` OR qid:`92032` OR qid:`92033` OR qid:`92033` OR qid:`92034` OR qid:`92035` OR qid:`92036` OR qid:`92037` OR qid:`92038` OR qid:`92039` OR qid:`92040` )
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of vendor-suggested mitigation or workaround.
Mitigation refers to a setting, standard configuration, or general best-practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is sometimes used temporarily for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
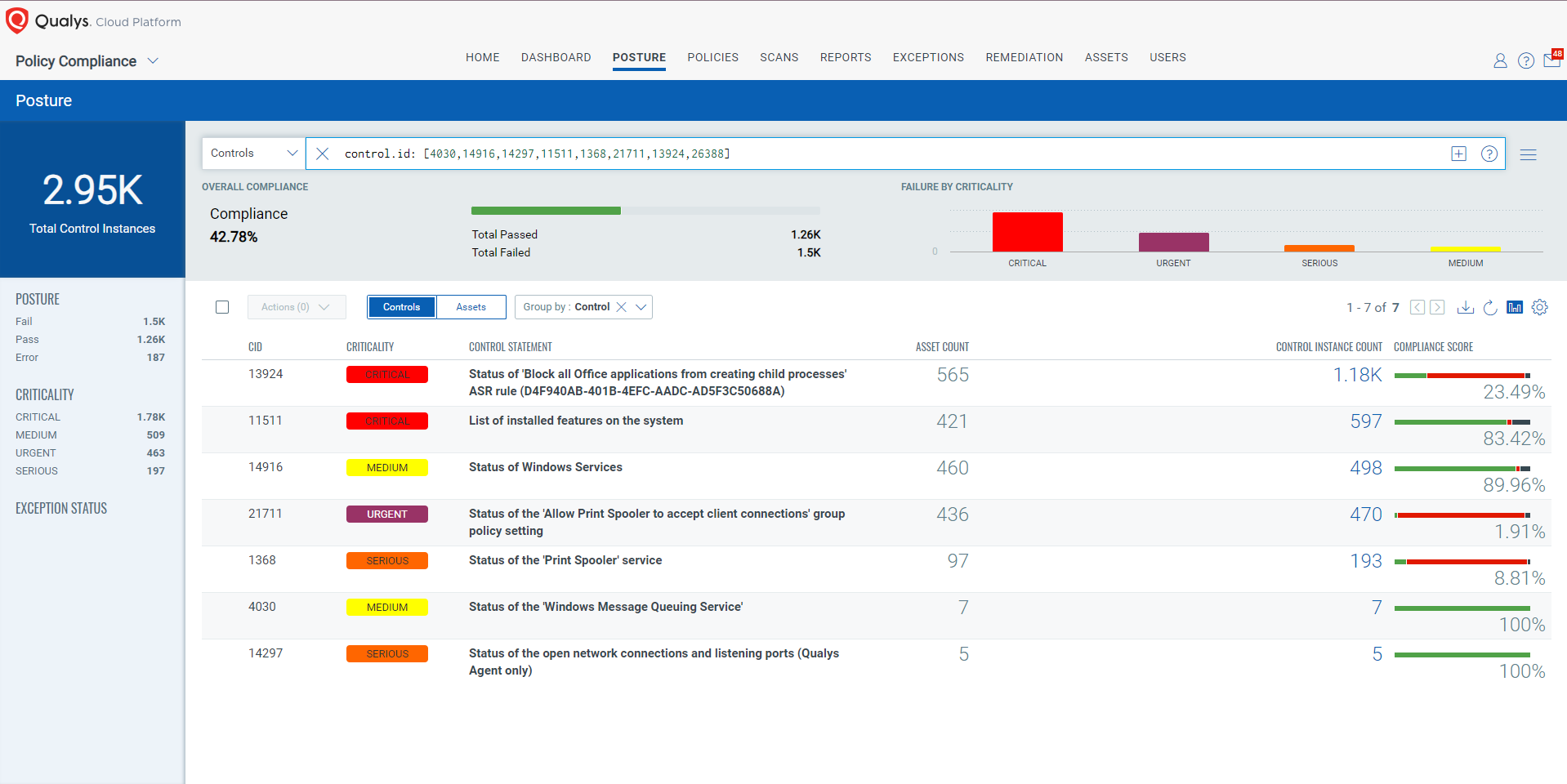
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-35365 and CVE-2023-35366: Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 11511 List of installed features on the system
CVE-2023-32057: Microsoft Message Queuing Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 4030 Status of the ‘Windows Message Queuing Service’
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
CVE-2023-35302: Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 8.8 / 7.7
Policy Compliance Control IDs (CIDs):
- 1368 Status of the ‘Print Spooler’ service
- 21711 Status of the ‘Allow Print Spooler to accept client connections’ group policy setting
CVE-2023-36884: Office and Windows HTML Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 8.3 / 8.1
Policy Compliance Control IDs (CIDs):
- 13924 Status of ‘Block all Office applications from creating child processes’ ASR rule (D4F940AB-401B-4EFC-AADC-AD5F3C50688A)
- 26388 Status of the ‘FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION’ setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [4030,14916,14297,11511,1368,21711,13924,26388]
EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
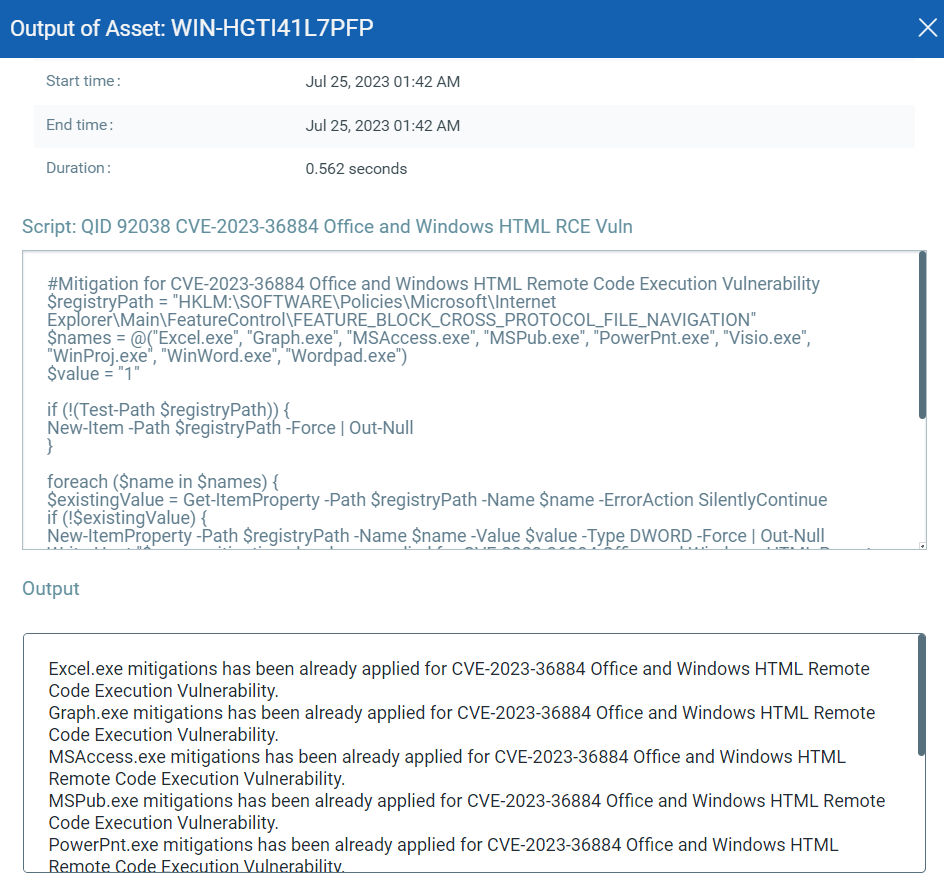
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
CVE-2023-36884: Office and Windows HTML Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.3/10.
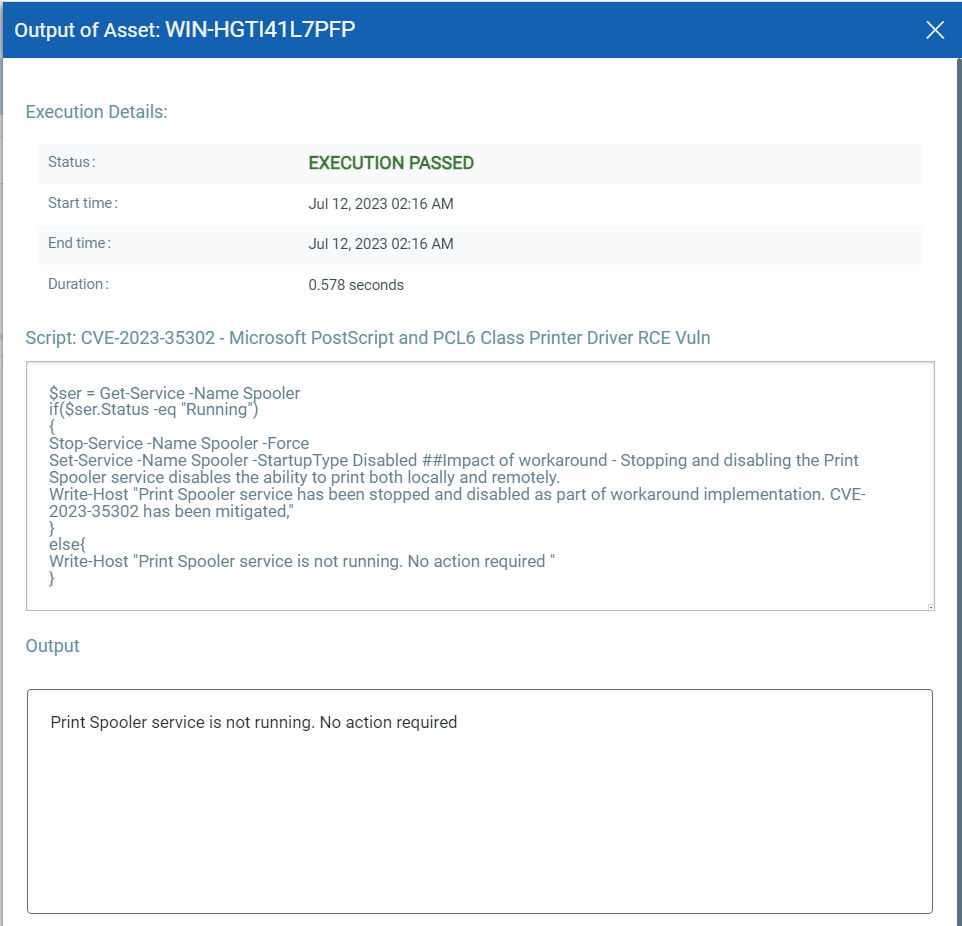
CVE-2023-35302: Microsoft PostScript and PCL6 Class Printer Driver Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
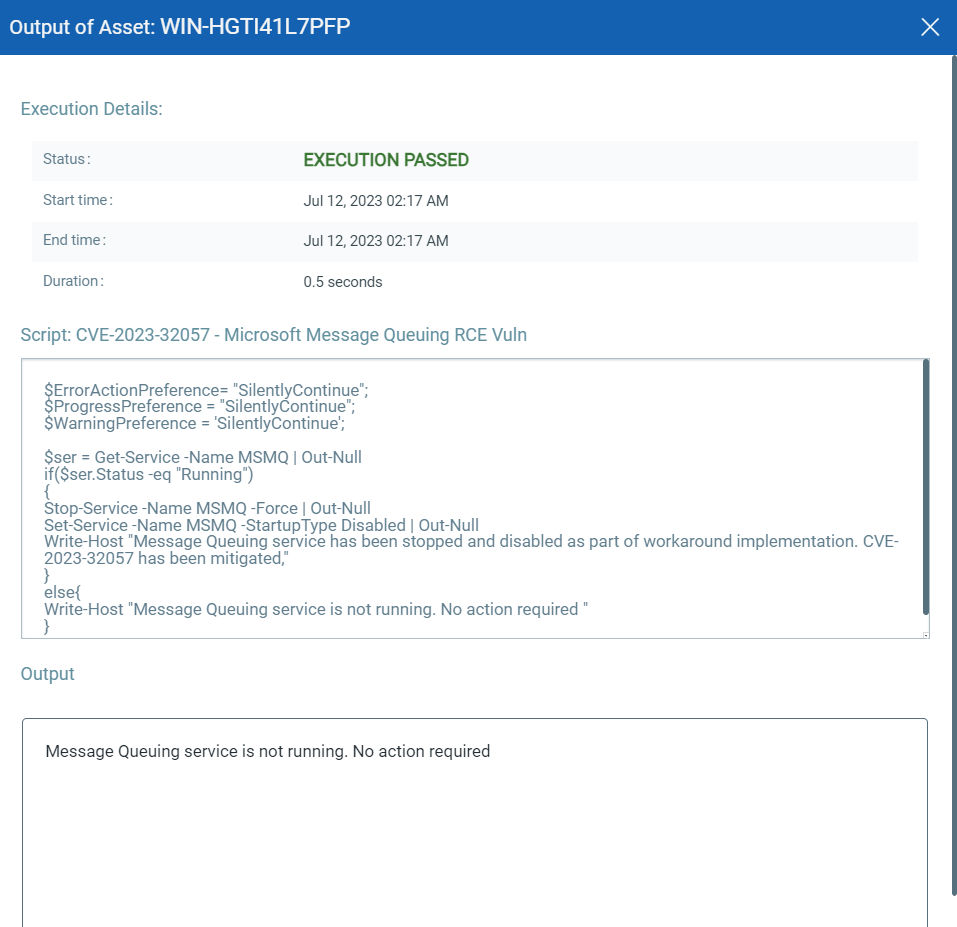
CVE-2023-32057: Microsoft Message Queuing Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
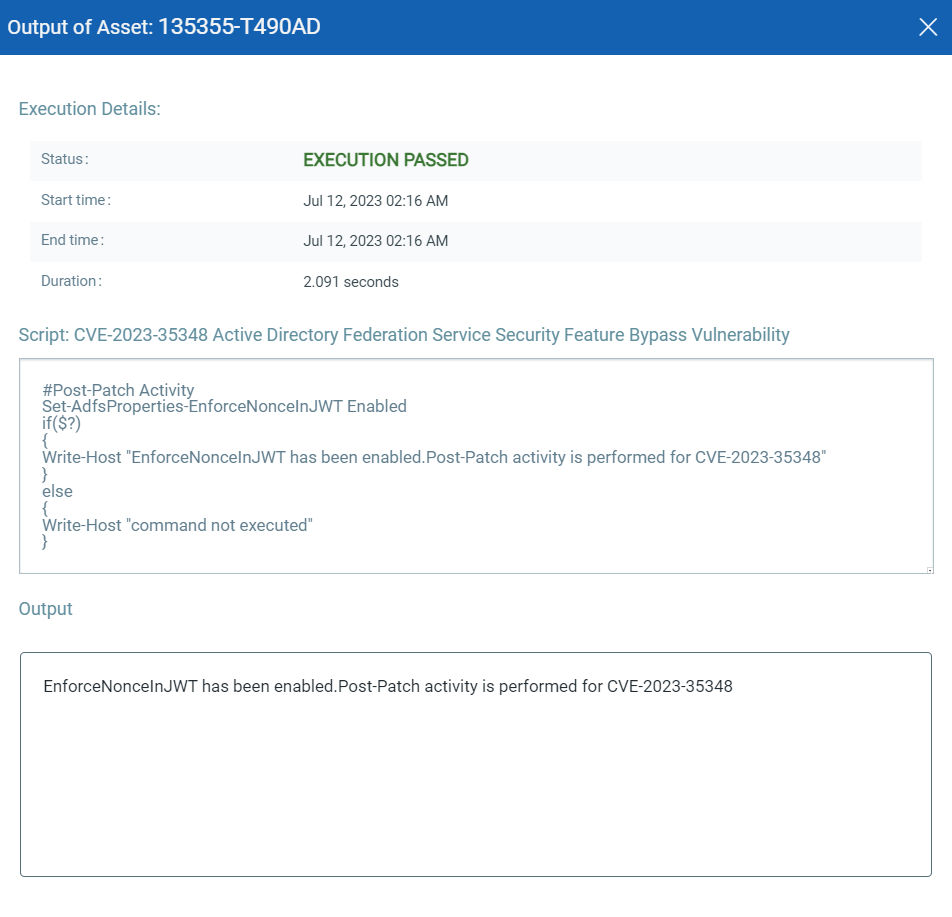
CVE-2023-35348: Active Directory Federation Service Security Feature Bypass Vulnerability
Note: This is Post Patch Activity
This vulnerability has a CVSSv3.1 score of 8.8/10.
The next Patch Tuesday will be on August 8, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the ‘This Month in Vulnerabilities and Patches webinar.’
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches