Risk Fact #4: Malware in your Cloud means Exploitation is underway

Qualys Blog Series – 2023 TotalCloud Security Insights by the Threat Research Unit
The 2023 TotalCloud Security Insights report from the Qualys Threat Research Unit (TRU) provides research insights, best practices, and detailed recommendations organized by five separate Risk Facts. The insights will enable organizations using cloud technologies to better understand these risks and how they can be better prepared to face those challenges in today’s threat landscape.
Read the previous blog in this series: External-Facing Vulnerabilities Cloud Security Research Risk Fact
Threats Known to Exploit High-Risk Assets
The data show that crypto mining and malware are the two most significant threats to cloud assets; both are designed to provide a foothold in your environment or facilitate lateral movement.
The critical damage caused by crypto mining is based on the wasted cost of compute cycles. Miners seek to use your cloud to create crypto coins and do not plan to deposit the coins in your account! An unmitigated crypto mining attack could cost your organization millions due to energy and cloud resource allocation fees. It also displaces your organization’s use of the resources it is paying for.
Not accounting for generic coin mining software such as XMRig, the top three malware categories in cloud infrastructures observed were AndroxGh0st/Legion RCE, Denonia, and SCARLETEEL. The data show the bulk of malware that will impact an insecure cloud asset is some variant of the crypto miner, many of which are generic and a few of which have received names — like Denonia.
Denonia
Denonia malware is an exciting use case as it is the first malware strain to specifically target AWS Lambda. There are no controls currently in the CIS Hardening Benchmark for AWS that cover Lambda specifically, outside of enabling IAM Access Analyzer, which examines permissions provided to Lambda functions.
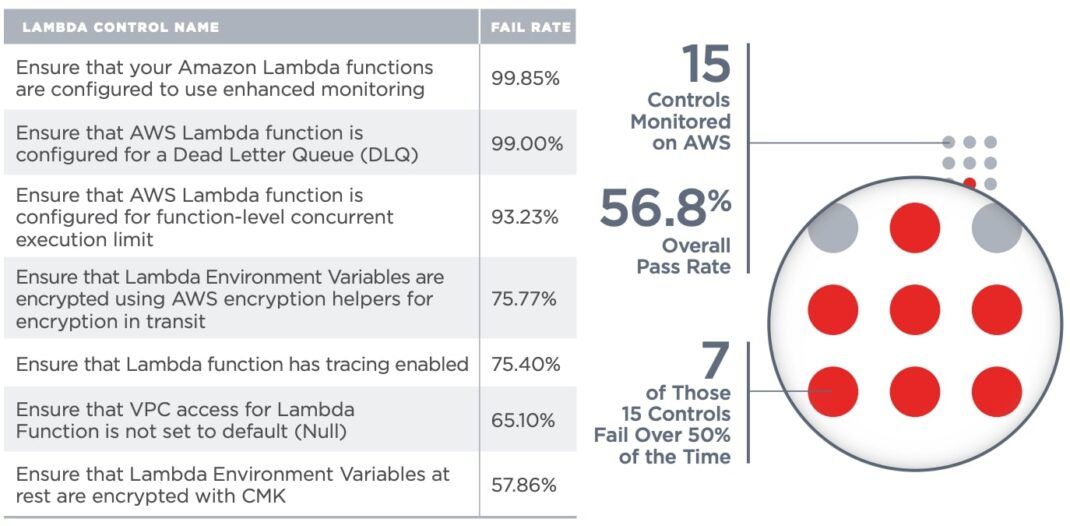
Looking at controls outside of CIS benchmarks, Lambda reflects the overall hardening stance for AWS, and the 15 monitored controls are passing at 56.8%.
Below, we look at seven of those controls that are failing more than 50% of the time.
Getting a Foothold — AndroxGh0st/Legion RCE, SCARLETEEL
In addition to crypto miners, the data show the use of AndroxGh0st and SCARLETEEL. AndroxGh0st works by targeting .env files to gain access to sensitive information such as high-permission credentials, allowing the attacker to move laterally through your organization.
SCARLETEEL specifically targets high-risk external-facing cloud assets to gather credentials and subsequently launch a credential-stuffing attack for lateral movement and exploitation of your cloud environment. Some attacks could eventually affect your on-premises assets.
SCARLETEEL also specifically targets Lambda functions to achieve its purpose.
AndroxGh0st/Legion RCE
The AndroxGh0st malware is written in Python and usually targets Simple Mail Transfer Protocol (SMTP) to enable spamming. AndroxGh0st specifically targets cloud environments — in particular, AWS secrets — and exploits vulnerabilities in web applications running in the cloud to maintain a foothold.
Just one vulnerability, CVE-2017-9841, in PHPUnit, has been associated explicitly with AndroxGh0st. However, after getting a foothold, the malware will programmatically attempt to maintain persistence in AWS by creating accounts and enabling permissions.
Leveraging Deep Learning AI to Detect Advanced Malware
Exploitation is where the adversaries’ public stories begin. When risk-reward is excellent enough, exploitation is a consequence. For defenders, the challenge is discovering and eradicating stealthy malware commonly found in Linux containers, which can evade detection for months. Legacy signature-based techniques simply cannot create and deploy signatures fast enough to prevent malware from infiltrating enterprise clouds.
A new approach is required using deep learning AI technology to quickly discover advanced malware in containers and complex network traffic flows. Deep learning is vital for enabling the sub-second detection of advanced zero-day malware, which refers to previously unknown and unseen malicious software that exploits vulnerabilities in cloud systems. Without this capability, high-risk cloud assets are ripe for exploitation.
Critical Insights from Risk Fact 4
Findings by the Threat Research Unit reveal a substantial risk of advanced malware in enterprise clouds. The most significant threats to cloud assets are crypto mining and malware, which provide a foothold in your environment or facilitate lateral movement. Detecting these threats quickly requires faster capabilities than legacy signature-based tools. A modern approach using deep learning AI can provide sub-second detection of advanced malware. Without this capability, cloud security has a substantial elevation of risk.
To learn more about the five cloud security Risk Facts and detailed recommendations, download your copy of Qualys 2023 TotalCloud Security Insights.
Read the next blog in this series: Keeping the pace of remediation at a cloud scale requires automation.
Get the full Qualys 2023 TotalCloud Security Insights and learn about all five Cloud Risk Facts now.
