Curl 8.4.0 – Proactively Identifying Potential Vulnerable Assets
Table of Contents
- What is Curl and libcurl?
- What Are Curl Vulnerabilities CVE-2023-38545 & CVE-2023-38546?
- Vulnerable Versions
- What Should Organizations Do?
- How Can Qualys Help?
- Discover Vulnerable Instances Using Qualys VMDR
- DetectVulnerableVersionsoflibcurlUsingQualysCustomAssessmentandRemediation(CAR)
- Patch Vulnerable Systems Using Qualys Patch Management (PM)
- Qualys QID Coverage
- What vulnerabilities were remediated in curl 8.4.0?
- Conclusion
On Wednesday, October 4, 2023, the curl project maintainers announced pre-notification for curl version 8.4.0 to be released on October 11. This version will fix two new vulnerabilities with one high and one low-severity CVE. The prenotification stated that the high-severity issue is arguably the most critical security flaw identified in curl in recent history.
Details regarding the vulnerabilities and the new version will be disclosed around 06:00 UTC on October 11, 2023.
What is Curl and libcurl?
Curl is a versatile open-source command-line tool for transferring data with URL syntax, supporting many network protocols like SSL, TLS, HTTP, FTP, SMTP, and more. Developers and system administrators prevalently use it to interact with APIs, download files, and create automated workflows among various internet-based tasks.
On the other hand, libcurl serves as the powerhouse behind Curl, a free, client-side URL transfer library that supports the same wide range of protocols. It allows developers to add robust data transfer functionality to their applications, ensuring their software can communicate with servers for tasks like sending HTTP requests, managing cookies, and handling authentication. This makes it a vital tool for developing interconnected and web-aware applications.
What Are Curl Vulnerabilities CVE-2023-38545 & CVE-2023-38546?
Curl 8.4.0 is scheduled for release on October 11. It addresses two vulnerabilities, CVE-2023-38545 and CVE-2023-38546, with the former being of high severity and affecting both libcurl and the curl tool, while the latter is of low severity and impacts only libcurl. Specific details on the version range affected or further information about the vulnerabilities are not available pre-release to prevent aiding the identification of the problem areas. More comprehensive information, including details about the CVEs, will be published at 06:00 UTC on the release day. No, API or ABI changes are expected in the forthcoming release.
Vulnerable Versions
With specific version range details undisclosed to prevent pre-release problem identification, the vulnerabilities will be fixed in curl version 8.4.0. The forthcoming high-severity issue in libcurl demands cautious attention, though it might not affect all users. Updating the shared libcurl library is the anticipated universal fix across operating systems. Yet, according to the maintainer, a sizable number of rebuilds are expected, particularly in docker images and similar entities that incorporate their libcurl copies.
What Should Organizations Do?
Organizations should urgently inventory and scan all systems utilizing curl and libcurl, anticipating identifying potentially vulnerable versions once details are disclosed with the release of Curl 8.4.0 on October 11. Immediate update implementation upon release is essential to safeguard systems against these pressing vulnerabilities (CVE-2023-38545 and CVE-2023-38546).
How Can Qualys Help?
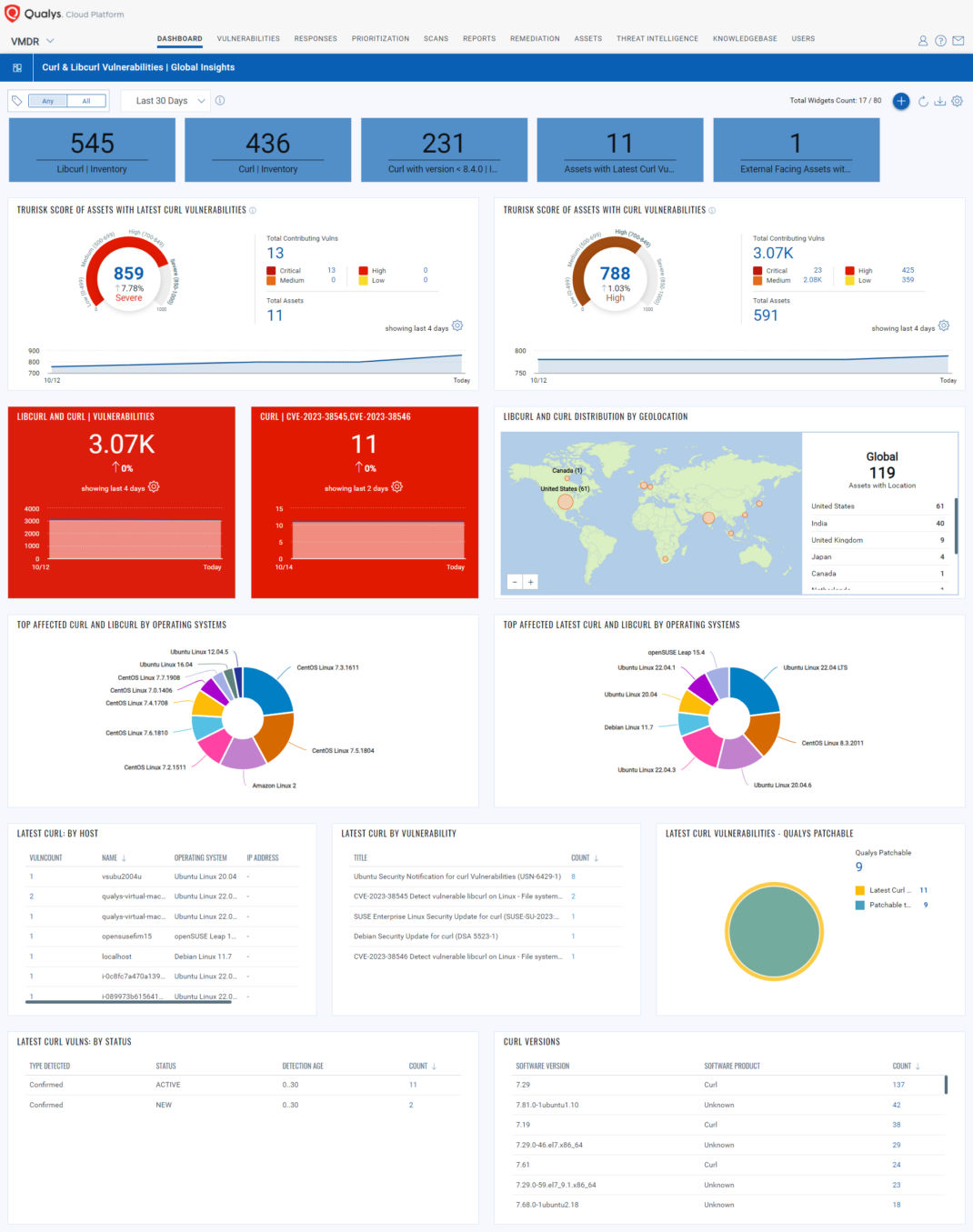
Using the Qualys Unified Dashboard, you can gain complete asset visibility for CVE-2023-38545 and CVE-2023-38546 vulnerabilities. Additionally, it provides asset counts for those with ‘curl/curlib.’ After identifying and prioritizing vulnerable assets among your remediation teams, Qualys Patch Management stands ready to help you swiftly mitigate these risks.
Explore the Curl & Libcurl Vulnerabilities | Global Insights dashboard, now available for download.
Inventory Curl and libcurl Using Qualys CSAM
Qualys CSAM makes it easy to identify assets containing curl/libcurl.
The following QQL query will identify assets with curl/libcurl installed:
Query: software: (name: 'libcurl' or name: 'curl')

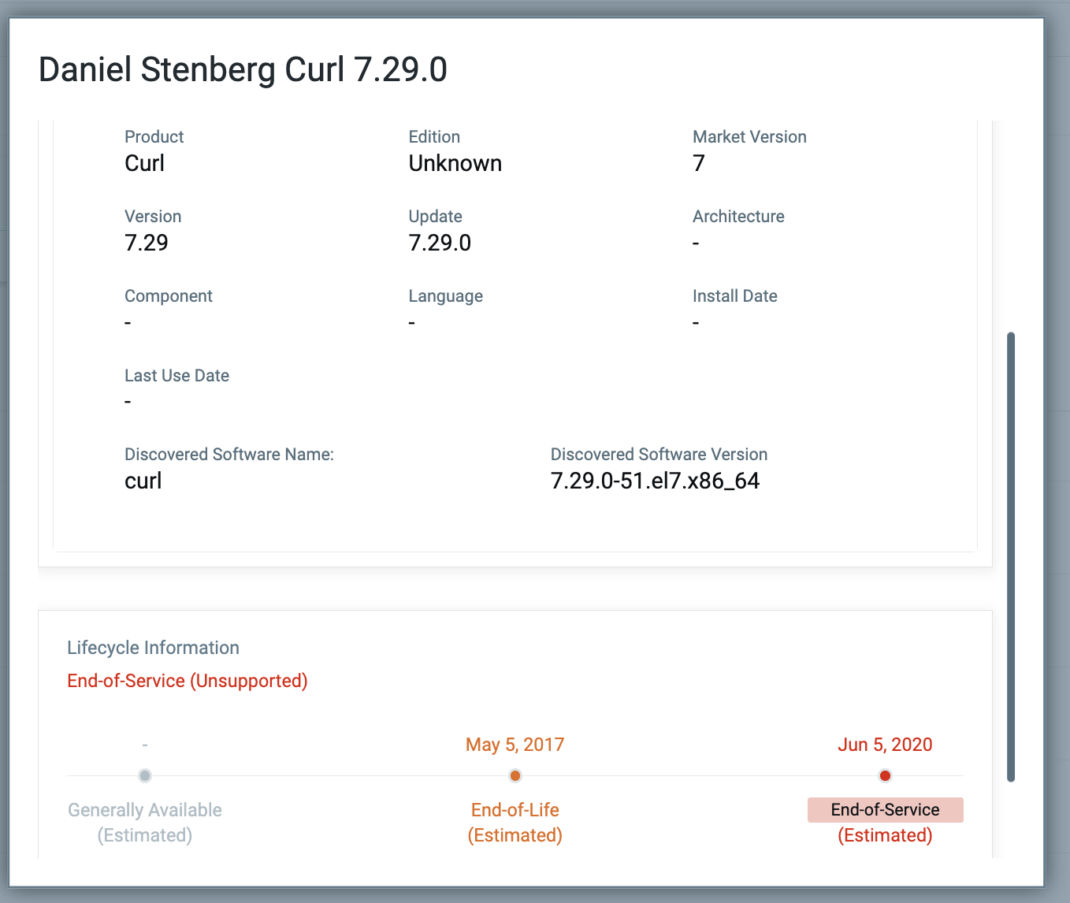
The QQL below assists in identifying assets with potentially vulnerable versions of curl/libcurl installed.
Query: software:(name:’curl’ and version < 8.4.0 )

Tag potentially vulnerable assets with CSAM
In addition to identifying the assets, Qualys also recommends that customers tag the assets with curl/libcurl installed.

Discover Vulnerable Instances Using Qualys VMDR
Once the vulnerability is disclosed, on October 11, each vendor will release backported patches for these vulnerabilities. The Qualys Threat Research Unit (TRU) closely tracking the vulnerability and will release QIDs to detect those backported versions.
Detect Vulnerable Versions of libcurl Using Qualys
Custom Assessment and Remediation (CAR)
The curl command-line tool offers multiple installation methods, from package managers like yum and apt in Linux distributions to direct downloads from the curl website. These downloads, often scripted within Unix shell scripts, make it challenging to locate installation paths and versions of both curl executables and their associated libraries.
Qualys Custom Assessment and Remediation (CAR) allows you to create Custom QID leveraging script from CAR Script Library to detect vulnerable versions of libcurl on your host. You only need to copy the script from Library and follow simple steps to create the custom QID.
Check out the detection script from CAR Script Library and create your own QID for this vulnerability.
Detection on Linux platform
CVE-2023-38545 Detect vulnerable libcurl on Linux – File system scan
This script scans the file system for vulnerable version of libcurl 7.69.0 to and including 8.3.0, for CVE-2023-38545 SOCKS5 heap buffer overflow

You can see the detections under VMDR.

and verify the Vulnerability Result under Vulnerability Details as part of the detection summary

CVE-2023-38546 Detect vulnerable libcurl on Linux – File system scan
This script scans the file system for vulnerable version of libcurl 7.9.1 to and including 8.3.0, for CVE-2023-38546 cookie injection with none file. Create your Custom QID leveraging library script and execute it across your Linux environment.

You can see the detections under VMDR.

Detection on Windows platform
Similarly, create custom QIDs for mentioned vulnerabilities on Windows platform.

Patch Vulnerable Systems Using Qualys Patch Management (PM)
Once all curl vulnerabilities are found in the environment, customers can use Qualys Patch Management to patch vulnerable applications.
As libcurl is a library used by many OSes and applications, it is safe to assume that in the near future, many of those applications will issue a patch to fix this libcurl vulnerability. Qualys Patch Management can patch those applications on Windows, Linux and MacOS.
Qualys Patch Management also offers a way to execute PowerShell scripts on Windows and shell scripts on Linux machines. It can be leveraged to quickly create mitigation steps.
Qualys QID Coverage
Qualys has released QIDs, available starting from version VULNSIGS-2.5.888-2 of the vulnsigs.
| QID | Title | Qualys Release Versions |
| 503379 | Alpine Linux Security Update for curl | VULNSIGS-2.5.888-2 |
| 6000245 | Debian Security Update for curl (DSA 5523-1) | VULNSIGS-2.5.888-2 |
| 691322 | Free Berkeley Software Distribution (FreeBSD) Security Update for curl (d6c19e8c-6806-11ee-9464-b42e991fc52e) | VULNSIGS-2.5.888-2 |
| 199825 | Ubuntu Security Notification for curl Vulnerabilities (USN-6429-1) | VULNSIGS-2.5.889-2 |
| 710772 | Gentoo Linux curl Multiple Vulnerabilities (GLSA 202310-12) | VULNSIGS-2.5.888-3 |
| 907390 | Common Base Linux Mariner (CBL-Mariner) Security Update for curl (31288-1) | VULNSIGS-2.5.894-2 |
| 941303 | AlmaLinux Security Update for curl (ALSA-2023:5763) | VULNSIGS-2.5.893-1 |
| 242183 | Red Hat Update for curl (RHSA-2023:5763) | VULNSIGS-2.5.893-1 |
| 356312 | Amazon Linux Security Advisory for curl : ALAS2-2023-2287 | VULNSIGS-2.5.891-1 |
| 356311 | Amazon Linux Security Advisory for curl : ALAS2023-2023-377 | VULNSIGS-2.5.891-1 |
| 284621 | Fedora Security Update for curl (FEDORA-2023-b855de5c0f) | VULNSIGS-2.5.891-1 |
| 242165 | Red Hat Update for curl (RHSA-2023:5700) | VULNSIGS-2.5.891-1 |
| 755071 | SUSE Enterprise Linux Security Update for curl (SUSE-SU-2023:4043-1) | VULNSIGS-2.5.889-2 |
| 755070 | SUSE Enterprise Linux Security Update for curl (SUSE-SU-2023:4044-1) | VULNSIGS-2.5.889-2 |
| 160994 | Oracle Enterprise Linux Security Update for curl (ELSA-2023-5763) | VULNSIGS-2.5.894-2 |
What vulnerabilities were remediated in curl 8.4.0?
On October 11, curl 8.4.0 was released. It contains fixes for two vulnerabilities:
| CVE | Description | Severity | Affected Scope |
|---|---|---|---|
| CVE-2023-38545 | SOCKS5 heap buffer overflow | High | libcurl and curl |
| CVE-2023-38546 | cookie injection with none file | Low | libcurl |
When will Qualys make patches available?
Qualys applications support various Linux and Unix distributions, which are in the process of releasing patches. Qualys has tested these vulnerabilities in the context of our implementations, finding them unexploitable to date. Products that embed libcurl will also need to update to the patched version. Projects using libcurl will be releasing updates soon and vulnerability remediation has been prioritized for near-term availability as early as mid-December.
Have these CVE’s been exploited in the wild?
Qualys Threat Research Unit (TRU) is not aware of any in-the-wild exploitation of either CVE-2023-38545 or CVE-2023-38546. While proof-of-concept do exist, use of it in testing of Qualys products produced a negative result of applicability.
How can organizations manage the upgrades to the Qualys Cloud Agent?
It is strongly recommended that organizations consider how they will manage upgrades to the Qualys Cloud Agent. To get the latest features, security, and performance enhancements, please refer to this information on how to enable automatic upgrades.
Conclusion
In light of the imminent release of curl 8.4.0 and the critical security flaws it aims to address, organizations must act swiftly to inventory, scan, and update all systems utilizing curl and libcurl. In particular, the gravity of the high-severity vulnerability mandates immediate and cautious attention to safeguarding interconnected and web-aware applications, ensuring the rich data transfer functionality curl and libcurl provide remain unimpaired and secure. The detailed insights into these vulnerabilities and the corrective measures will become pivotal following the clear disclosure slated for 06:00 UTC, October 11, 2023.