Microsoft and Adobe Patch Tuesday, February 2024 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for February 2024
- Adobe Patches for February 2024
- Zero-day Vulnerabilities Patched in February Patch Tuesday Edition
- Other Critical Severity Vulnerabilities Patched in February Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response with Patch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- Qualys Monthly Webinar Series
The new Microsoft Patch Tuesday Edition for February 2024 is now live! We invite you to join us to review and discuss the details of these security updates and patches.
Microsoft Patch Tuesday for February 2024
Microsoft Patch Tuesday’s February 2024 edition addressed 79 vulnerabilities, including five critical and 66 important severity vulnerabilities. Microsoft has addressed two vulnerabilities known to be exploited in the wild in this batch of updates. Microsoft has also addressed six vulnerabilities in Microsoft Edge (Chromium-based). The vulnerabilities have been patched earlier this month.
Microsoft Patch Tuesday, February edition includes updates for vulnerabilities in Microsoft Office and Components, Microsoft Exchange Server, Azure File Sync, Azure Active Directory, SQL Server, Windows Kernel, DNS Server, Windows Internet Connection Sharing (ICS), and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The February 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 10 | Important: 10 |
| Denial of Service Vulnerability | 9 | Critical: 1 Important: 8 |
| Elevation of Privilege Vulnerability | 16 | Critical: 1 Important: 15 |
| Information Disclosure Vulnerability | 5 | Critical: 1 Important: 4 |
| Remote Code Execution Vulnerability | 31 | Critical: 2 Important: 29 |
| Security Feature Bypass Vulnerability | 3 | Important: 3 |
Adobe Patches for February 2024
Adobe has released five security advisories to address 29 vulnerabilities in Adobe Commerce, Substance 3D Painter, Adobe FrameMaker Publishing Server, Adobe Acrobat and Reader, and Substance 3D Designer. Out of 29, 15 vulnerabilities are given critical severity ratings. On successful exploitation, the vulnerabilities may lead to memory leaks, potential code execution, security feature bypass, and denial of service attacks.
Zero-day Vulnerabilities Patched in February Patch Tuesday Edition
CVE-2024-21351: Windows SmartScreen Security Feature Bypass Vulnerability
Windows SmartScreen is a security feature in Microsoft Windows operating systems that protects against malicious software and websites. SmartScreen is a background application that employs a cloud-based component to scan web pages you visit for security risks updated regularly.
To exploit the vulnerability, an authenticated attacker must send a specially crafted malicious file compromised by them. An attacker may exploit the vulnerability to bypass the SmartScreen user experience. The vulnerability could allow a malicious attacker to inject code into SmartScreen and potentially gain code execution, potentially leading to data exposure, lack of system availability, or both.
CISA has acknowledged the active exploitation of the vulnerability by adding this to its Known Exploited Vulnerabilities Catalog. CISA has requested users to patch it before March 5, 2024.
CVE-2024-21412: Internet Shortcut Files Security Feature Bypass Vulnerability
An internet shortcut file is a small file that contains a target URI or GUID to an object or the name of a target program file. Internet shortcuts are typically text files with the .URL extension.
An unauthenticated attacker may exploit the vulnerability by sending the targeted user a specially crafted file to bypass displayed security checks. However, the attacker would have no way to force a user to view the attacker-controlled content. Instead, the attacker must convince them to act by clicking the file link.
CISA has acknowledged the active exploitation of the vulnerability by adding this to its Known Exploited Vulnerabilities Catalog. CISA has requested users to patch it before March 5, 2024.
CVE-2024-21410: Microsoft Exchange Server Elevation of Privilege Vulnerability
Microsoft updated the advisory on Feb 14, 2024, mentioning the active exploitation of the vulnerability.
Microsoft Exchange Server is a platform that offers email, calendaring, contact, scheduling, and collaboration features. It runs exclusively on Windows Server operating systems and is designed to be accessed from mobile devices, desktops, and web-based systems.
An attacker could use an NTLM credentials-leaking type vulnerability to target an NTLM client, like Outlook. The compromised credentials can then be used to access the Exchange server as the victim’s client and act on the server on the victim’s behalf. Successful exploitation of the vulnerability may allow an attacker to relay a user’s leaked Net-NTLMv2 hash against a vulnerable Exchange Server and authenticate as the user.
CISA has acknowledged the active exploitation of the vulnerability by adding this to its Known Exploited Vulnerabilities Catalog. CISA has requested users to patch it before March 7, 2024.
Other Critical Severity Vulnerabilities Patched in February Patch Tuesday Edition
CVE-2024-21357: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
Pragmatic General Multicast (PGM), a.k.a. ‘reliable multicast,’ is a scalable receiver-reliable protocol. PGM allows receivers to detect loss, request retransmission of lost data, or notify an application of unrecoverable loss. PGM is best suited for applications that require duplicate-free multicast data delivery from multiple sources to multiple receivers.
This vulnerability can only be exploited on the systems connected to the same network segment as the attacker. The attack cannot be performed across multiple networks (for example, a WAN) and would be limited to systems on the same network switch or virtual network. An attacker must take additional actions before exploitation to prepare the target environment.
CVE-2024-21413: Microsoft Office Remote Code Execution Vulnerability
An attacker who exploits the vulnerability may bypass the Office Protected View and open it in editing instead of the protected mode. An attacker could gain high privileges, which include read, write, and delete functionality.
CVE-2024-20684: Windows Hyper-V Denial of Service Vulnerability
Windows Hyper-V allows hardware virtualization. IT professionals and software developers use virtualization to test software on multiple operating systems. Hyper-V enables working professionals to perform these tasks smoothly. With the help of Hyper-V, one can create virtual hard drives, virtual switches, and numerous different virtual devices, all of which can be added to virtual machines.
Successful exploitation of the vulnerability may allow a Hyper-V guest to affect the functionality of the Hyper-V host.
CVE-2024-21380: Microsoft Dynamics Business Central/NAV Information Disclosure Vulnerability
Dynamics NAV is an enterprise resource planning (ERP) app that helps businesses with finance, manufacturing, customer relationship management (CRM), supply chains, analytics, and electronic commerce. Small and medium-sized companies and local subsidiaries of large international groups use it.
An attacker must win a race condition to exploit the vulnerability. An authenticated attacker must convince a user to click on a specially crafted URL to be compromised by them. Successful exploitation of the vulnerability may allow an attacker to craft a payload enabling them to access sensitive user data, which could result in unauthorized access to the victim’s account or compromise of other confidential information.
Other Microsoft Vulnerability Highlights
- CVE-2024-21378 is a remote code execution vulnerability in Microsoft Outlook. To exploit the vulnerability, the attacker must be authenticated with LAN-access and have credentials for a valid Exchange user. An attacker may exploit the vulnerability by sending a malicious file and convincing the user to open it. On successful exploitation, an attacker could gain high privileges, which include read, write, and delete functionality.
- CVE-2024-21346 is an elevation of privilege vulnerability in Win32k. An attacker may exploit the vulnerability to gain SYSTEM privileges.
- CVE-2024-21379 is a remote code execution vulnerability in Microsoft Word. On successful exploitation, an attacker could gain high privileges, which include read, write, and delete functionality.
- CVE-2024-21345 is an elevation of privilege vulnerability in Windows Kernel. An authenticated attacker could run a specially crafted application and give them control of the targeted destination and source of the copy. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-21371 is an elevation of privilege vulnerability in Windows Kernel. An attacker must win a race condition to exploit the vulnerability. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-21338 is an elevation of privilege vulnerability in Windows Kernel. An attacker must first log on to the system to exploit this vulnerability. After that, an attacker could run a specially crafted application to exploit the vulnerability and take control of an affected system.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Azure DevOps, Microsoft Office, Azure Stack, Windows Hyper-V, Skype for Business, Trusted Compute Base, Microsoft Defender for Endpoint, Microsoft Dynamics, Azure Connected Machine Agent, Windows Win32K – ICOMP, Microsoft ActiveX, Microsoft WDAC OLE DB provider for SQL, Windows SmartScreen, Microsoft WDAC ODBC Driver, Windows Message Queuing, Windows LDAP – Lightweight Directory Access Protocol, Azure Site Recovery, Windows OLE, Microsoft Teams for Android, Microsoft Azure Kubernetes Service, Microsoft Windows DNS, Microsoft Office Outlook, Microsoft Office Word, Microsoft Office OneNote, .NET, Microsoft Edge (Chromium-based), Microsoft Windows, and Internet Shortcut Files.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
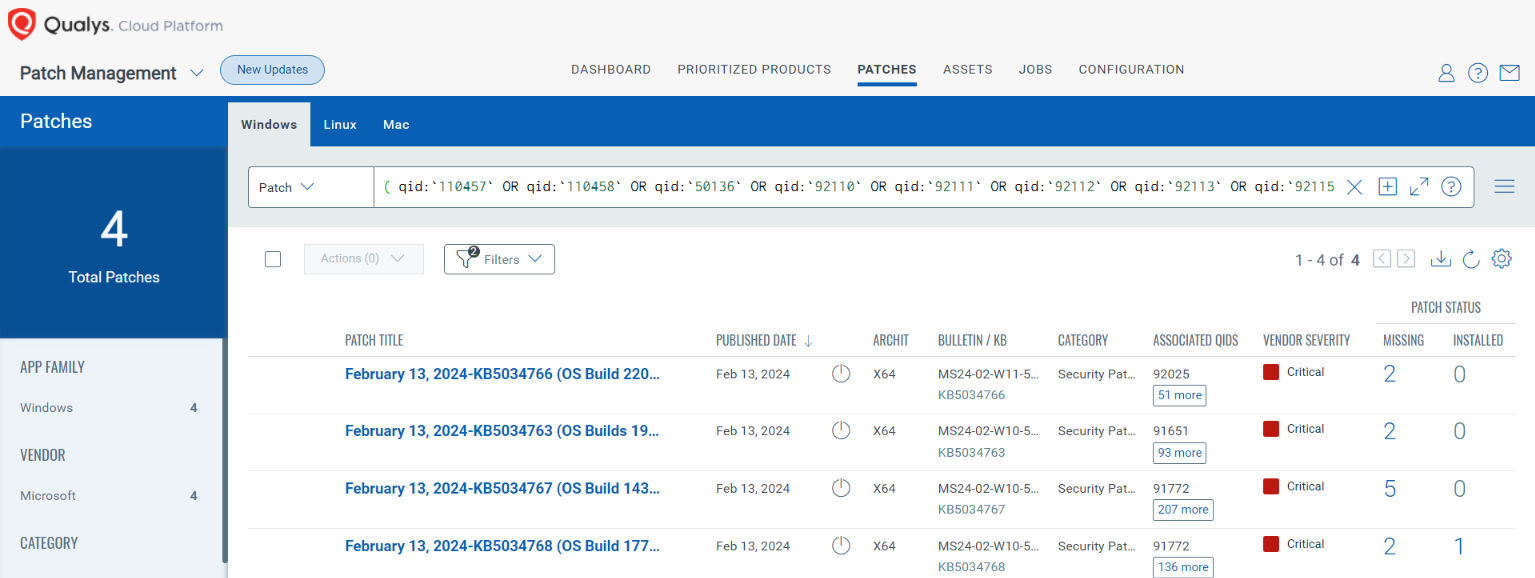
vulnerabilities.vulnerability: ( qid:`110457` OR qid:`110458` OR qid:`50136` OR qid:`92110` OR qid:`92111` OR qid:`92112` OR qid:`92113` OR qid:`92115` OR qid:`92116` )

Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`110457` OR qid:`110458` OR qid:`50136` OR qid:`92110` OR qid:`92111` OR qid:`92112` OR qid:`92113` OR qid:`92115` OR qid:`92116` )
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls, the risk of a vulnerability being exploited is reduced when the remediation (fix/patch) cannot be implemented immediately.
Qualys Policy Compliance team releases these exclusive controls based on vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, standard configuration, or general best practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is sometimes used temporarily to achieve a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been published to support the evaluation of the recommended workaround:
- 23810 Status of the ‘Extended Protection’ setting on the host (Without checking whether windows authentication is enabled)
- 27468 Status of the ‘Required SSL’ setting on the host
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [23810, 27468]

The next Patch Tuesday falls on March 12, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the ‘This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches