regreSSHion: Remote Unauthenticated Code Execution Vulnerability in OpenSSH server
Last updated on: August 1, 2024
Table of Contents
- About OpenSSH: Securing Enterprise Communications and Infrastructure
- Affected OpenSSH versions:
- Potential Impact of regreSSHion
- Immediate Steps to Mitigate Risk
- Technical Details
- Qualys QID Coverage
- Discover Vulnerable Assets Using Qualys CyberSecurity Asset Management (CSAM)
- Enhance Your Security Posture with Qualys Vulnerability Management, Detection, and Response (VMDR)
- Gain exposure visibility and remediation tracking with the regreSSHion Unified Dashboard
- Automatically Patch regreSSHion vulnerability With Qualys Patch Management
- Detect and remediate CVE-2024-6387 with Qualys TotalCloud Container Security
- Qualys Products and Customer Responsibilities
- Frequently Asked Questions (FAQs)

The Qualys Threat Research Unit (TRU) has discovered a Remote Unauthenticated Code Execution (RCE) vulnerability in OpenSSH’s server (sshd) in glibc-based Linux systems. CVE assigned to this vulnerability is CVE-2024-6387.
The vulnerability, which is a signal handler race condition in OpenSSH’s server (sshd), allows unauthenticated remote code execution (RCE) as root on glibc-based Linux systems; that presents a significant security risk. This race condition affects sshd in its default configuration.
Based on searches using Censys and Shodan, we have identified over 14 million potentially vulnerable OpenSSH server instances exposed to the Internet. Anonymized data from Qualys CSAM 3.0 with External Attack Surface Management data reveals that approximately 700,000 external internet-facing instances are vulnerable. This accounts for 31% of all internet-facing instances with OpenSSH in our global customer base. Interestingly, over 0.14% of vulnerable internet-facing instances with OpenSSH service have an End-Of-Life/End-Of-Support version of OpenSSH running.
In our security analysis, we identified that this vulnerability is a regression of the previously patched vulnerability CVE-2006-5051, which was reported in 2006. A regression in this context means that a flaw, once fixed, has reappeared in a subsequent software release, typically due to changes or updates that inadvertently reintroduce the issue. This incident highlights the crucial role of thorough regression testing to prevent the reintroduction of known vulnerabilities into the environment. This regression was introduced in October 2020 (OpenSSH 8.5p1).
Qualys has developed a working exploit for the regreSSHion vulnerability. As part of the disclosure process, we successfully demonstrated the exploit to the OpenSSH team to assist with their understanding and remediation efforts. We do not release our exploits, as we must allow time for patches to be applied. However, even though the exploit is complex, we believe that other independent researchers will be able to replicate our results.
About OpenSSH: Securing Enterprise Communications and Infrastructure
OpenSSH (Open Secure Shell) is a suite of secure networking utilities based on the Secure Shell (SSH) protocol, which is vital for secure communication over unsecured networks. It provides robust encryption to ensure privacy and secure file transfers, making it an essential tool for remote server management and secure data communication. Known for its extensive security and authentication features, OpenSSH supports various encryption technologies and is standard on multiple Unix-like systems, including macOS and Linux.
OpenSSH’s implementation serves as a critical tool for secure communication. Its enterprise value lies in its scalability and the ability to enforce robust access controls and secure automated processes across various environments. This includes everything from automated backups and batch processing to complex DevOps practices, which involve the secure handling of sensitive data across multiple systems and locations. Its continued development and widespread adoption highlight its importance in maintaining the confidentiality and integrity of network communications worldwide.
OpenSSH stands as a benchmark in software security, exemplifying a robust defense-in-depth approach. Despite the recent vulnerability, its overall track record remains exceptionally strong, serving as both a model and an inspiration in the field.
Affected OpenSSH versions:
- OpenSSH versions earlier than 4.4p1 are vulnerable to this signal handler race condition unless they are patched for CVE-2006-5051 and CVE-2008-4109.
- Versions from 4.4p1 up to, but not including, 8.5p1 are not vulnerable due to a transformative patch for CVE-2006-5051, which made a previously unsafe function secure.
- The vulnerability resurfaces in versions from 8.5p1 up to, but not including, 9.8p1 due to the accidental removal of a critical component in a function.
OpenBSD systems are unaffected by this bug, as OpenBSD developed a secure mechanism in 2001 that prevents this vulnerability.
Potential Impact of regreSSHion
This vulnerability, if exploited, could lead to full system compromise where an attacker can execute arbitrary code with the highest privileges, resulting in a complete system takeover, installation of malware, data manipulation, and the creation of backdoors for persistent access. It could facilitate network propagation, allowing attackers to use a compromised system as a foothold to traverse and exploit other vulnerable systems within the organization.
Moreover, gaining root access would enable attackers to bypass critical security mechanisms such as firewalls, intrusion detection systems, and logging mechanisms, further obscuring their activities. This could also result in significant data breaches and leakage, giving attackers access to all data stored on the system, including sensitive or proprietary information that could be stolen or publicly disclosed.
This vulnerability is challenging to exploit due to its remote race condition nature, requiring multiple attempts for a successful attack. This can cause memory corruption and necessitate overcoming Address Space Layout Randomization (ASLR). Advancements in deep learning may significantly increase the exploitation rate, potentially providing attackers with a substantial advantage in leveraging such security flaws.
Immediate Steps to Mitigate Risk
Addressing the regreSSHion vulnerability in OpenSSH, which enables remote code execution on Linux systems, demands a focused and layered security approach. Here are concise steps and strategic recommendations for enterprises to safeguard against this significant threat:
- Patch Management: Quickly apply available patches for OpenSSH and prioritize ongoing update processes.
- Enhanced Access Control: Limit SSH access through network-based controls to minimize the attack risks.
- Network Segmentation and Intrusion Detection: Divide networks to restrict unauthorized access and lateral movements within critical environments and deploy systems to monitor and alert on unusual activities indicative of exploitation attempts.
- Custom Assessment and Remediation: Quickly execute mitigation script on required assets. To find out more, check out the FAQ section ‘Are there any mitigations for this vulnerability?’
Technical Details
You can find the technical details of this vulnerability at:
https://www.qualys.com/2024/07/01/cve-2024-6387/regresshion.txt
Qualys QID Coverage
Qualys is releasing the QIDs in the table below as they become available, starting with vulnsigs version VULNSIGS-2.6.83-4 and in Linux Cloud Agent manifest version LX_MANIFEST-2.6.83.4-5
| QID | Title | Affected OS/Technology |
| 513833 | Alpine Linux 3.20 Security Update for openssh (regreSSHion) | Alpine Linux |
| 513832 | Alpine Linux 3.19 Security Update for openssh (regreSSHion) | Alpine Linux |
| 513831 | Alpine Linux 3.18 Security Update for openssh (regreSSHion) | Alpine Linux |
| 513830 | Alpine Linux 3.17 Security Update for openssh (regreSSHion) | Alpine Linux |
| 285635 | Fedora Security Update for openssh (FEDORA-2024-213f33544e) (regreSSHion) | Fedora Security |
| 756591 | SUSE Enterprise Linux Security Update for openssh (SUSE-SU-2024:2275-1) (regreSSHion) | SUSE Enterprise |
| 357791 | Amazon Linux Security Advisory for openssh : ALAS2023-2024-649 (regreSSHion) | Amazon Linux |
| 710942 | Gentoo Linux OpenSSH Remote Code Execution Vulnerability (GLSA 202407-09) (regreSSHion) | Gentoo Linux |
| 6081987 | VMware Photon OS Security Update for openssh (PHSA-2024-4.0-0642) (regreSSHion) | VMware Photon |
| 6081986 | VMware Photon OS Security Update for openssh (PHSA-2024-5.0-0307) (regreSSHion) | VMware Photon |
| 6122971 | Google Container OS-Optimized OS 101 Security Update for net-misc/openssh (CVE-2024-6387) (regreSSHion) | Google Container OS |
| 6122969 | Google Container OS-Optimized OS 105 Security Update for net-misc/openssh (CVE-2024-6387) (regreSSHion) | Google Container OS |
| 6122965 | Google Container OS-Optimized OS 109 Security Update for net-misc/openssh (CVE-2024-6387) (regreSSHion) | Google Container OS |
| 6122961 | Google Container OS-Optimized OS 113 Security Update for net-misc/openssh (CVE-2024-6387) (regreSSHion) | Google Container OS |
| 161766 | Oracle Enterprise Linux Security Update for openssh (ELSA-2024-12468) (regreSSHion) | Oracle Enterprise |
| 691562 | Free Berkeley Software Distribution (FreeBSD) Security Update for openssh (f1a00122-3797-11ef-b611-84a93843eb75) (regreSSHion) | Free Berkeley |
| 200455 | Debian/Ubuntu Notification for OpenSSH Vulnerability (USN-6859-1) (regreSSHion) | Debian/Ubuntu |
| 6007430 | Debian 11 Security Update for openssh (CVE-2024-6387) (regreSSHion) | Debian 11 Security |
| 6007429 | Debian/Ubuntu Update for openssh (DSA 5724-1) (regreSSHion) | Debian/Ubuntu |
| 42046 | OpenSSH Remote Unauthenticated Code Execution Vulnerability (regreSSHion) | OS agnostic |
| Upcoming QID(s) | ||
| QID | Title | Affected OS/Technology |
| 243964 | Red Hat Update for openssh (RHSA-2024:4312) | Red Hat |
It is recommended that Qualys customers use OS-specific QIDs to scan for backported packages on supported Linux distributions.
Please check the Qualys Vulnerability Knowledgebase for the full list of coverage for this vulnerability.
Discover Vulnerable Assets Using Qualys CyberSecurity Asset Management (CSAM)
The initial and crucial step in managing this critical vulnerability and mitigating associated risks involves pinpointing all assets susceptible to this specific issue. Use CSAM 3.0 with External Attack Surface Management to identify your organization’s internet-facing instances that have vulnerable versions of OpenSSH or are at their End of Life (EOL) or End of Support (EOS).
Free Trial
Identify internet-facing instances with vulnerable versions of OpenSSH
In the following example, we aim to identify all assets running the OpenSSH:
software:(name:"openssh" and version<4.4 and lifecycle.stage: `EOL/EOS`) or software:(name:"openssh" and version<9.8 and version>=8.5 and lifecycle.stage: `EOL/EOS`)
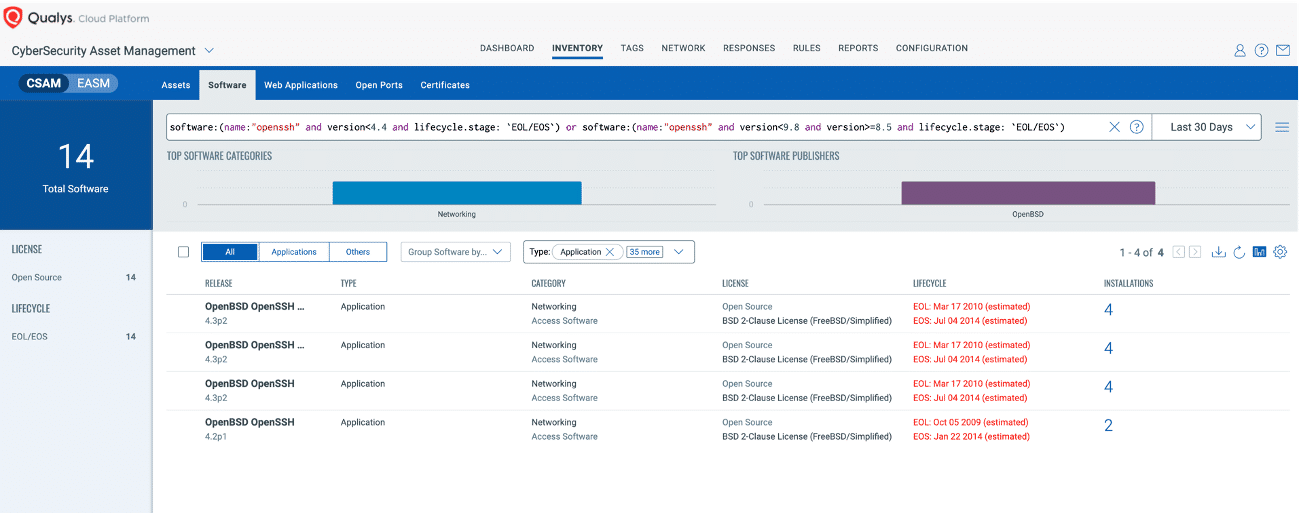
software:(name:"openssh" and version<4.4) or software:(name:"openssh" and version<9.8 and version>=8.5)
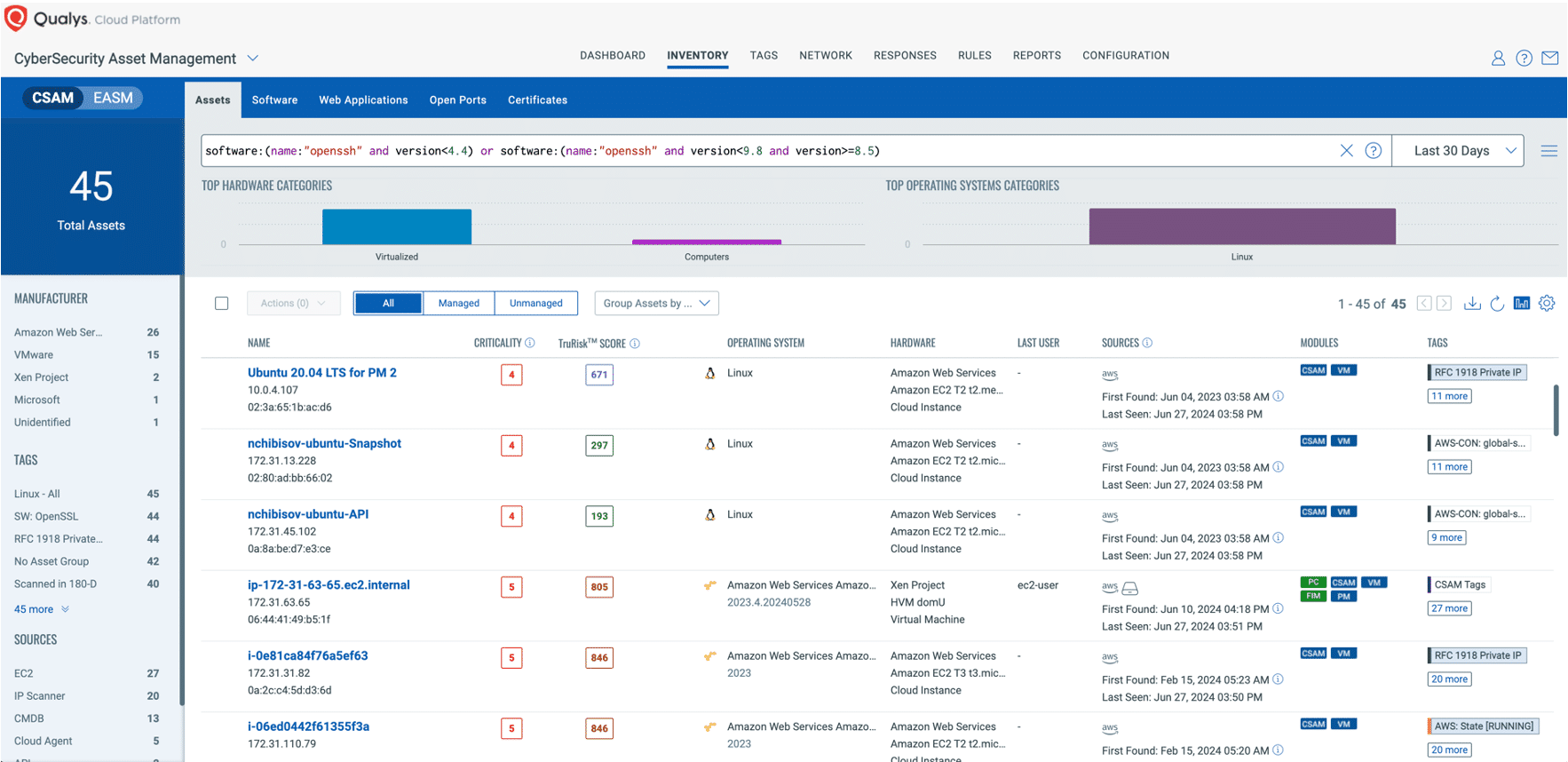
Enhance Your Security Posture with Qualys Vulnerability Management, Detection, and Response (VMDR)
Qualys VMDR offers comprehensive coverage and visibility into vulnerabilities, empowering organizations to rapidly respond to, prioritize, and mitigate the associated risks. Additionally, Qualys customers can leverage Qualys Patch Management to remediate these vulnerabilities effectively.
Leverage the power of Qualys VMDR alongside TruRisk and the Qualys Query Language (QQL) to efficiently identify and prioritize vulnerable assets, effectively addressing the vulnerabilities highlighted above.
Free Trial
Try Qualys VMDR at no cost for 30 days
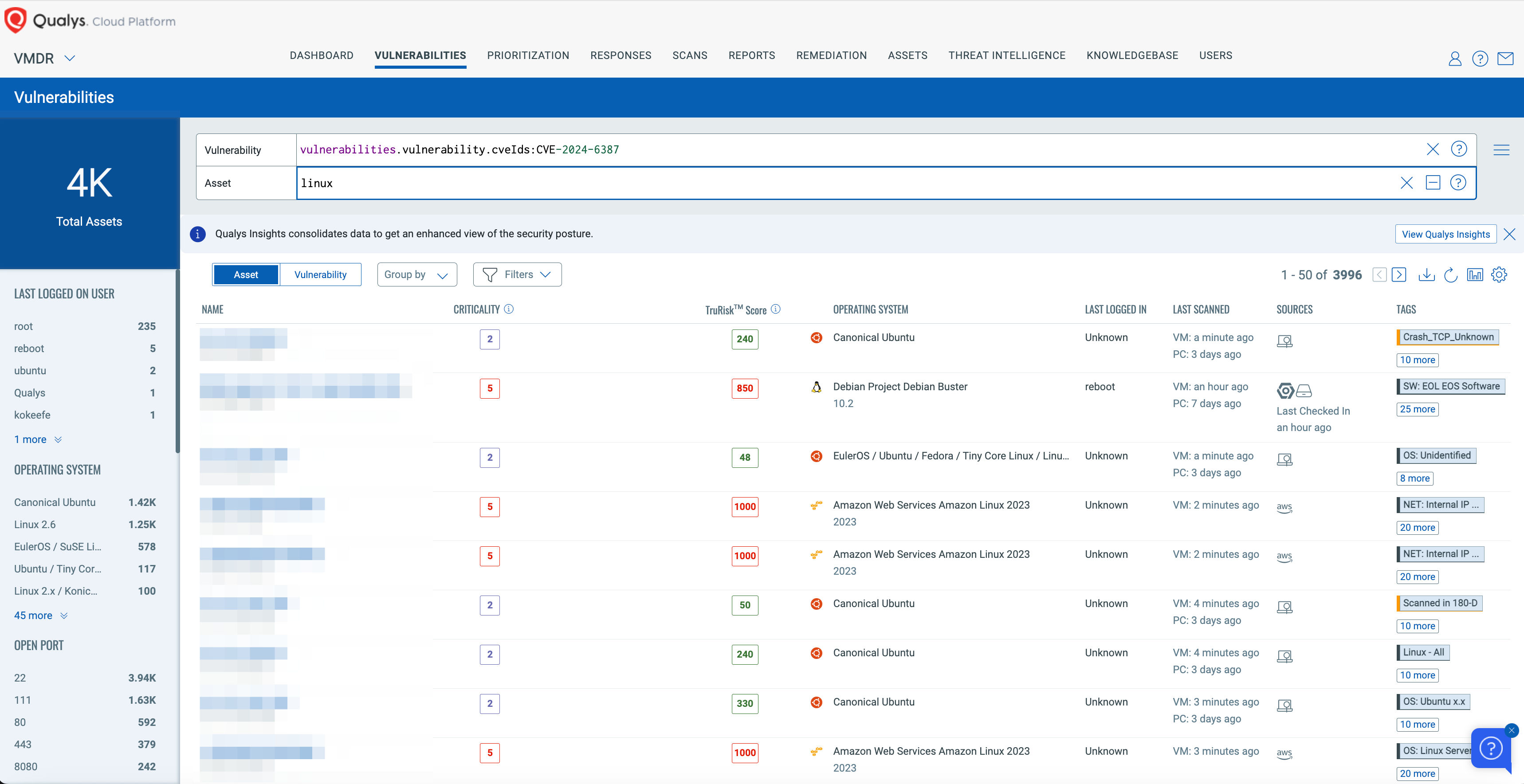
Use this QQL statement:
vulnerabilities.vulnerability.cveIds:CVE-2024-6387
Gain exposure visibility and remediation tracking with the “regreSSHion” Unified Dashboard
With the Qualys Unified Dashboard, you can track the vulnerability exposure within your organization and view your impacted hosts, their status, distribution across environments, and overall management in real time, allowing you to see your mean time to remediation (MTTR).
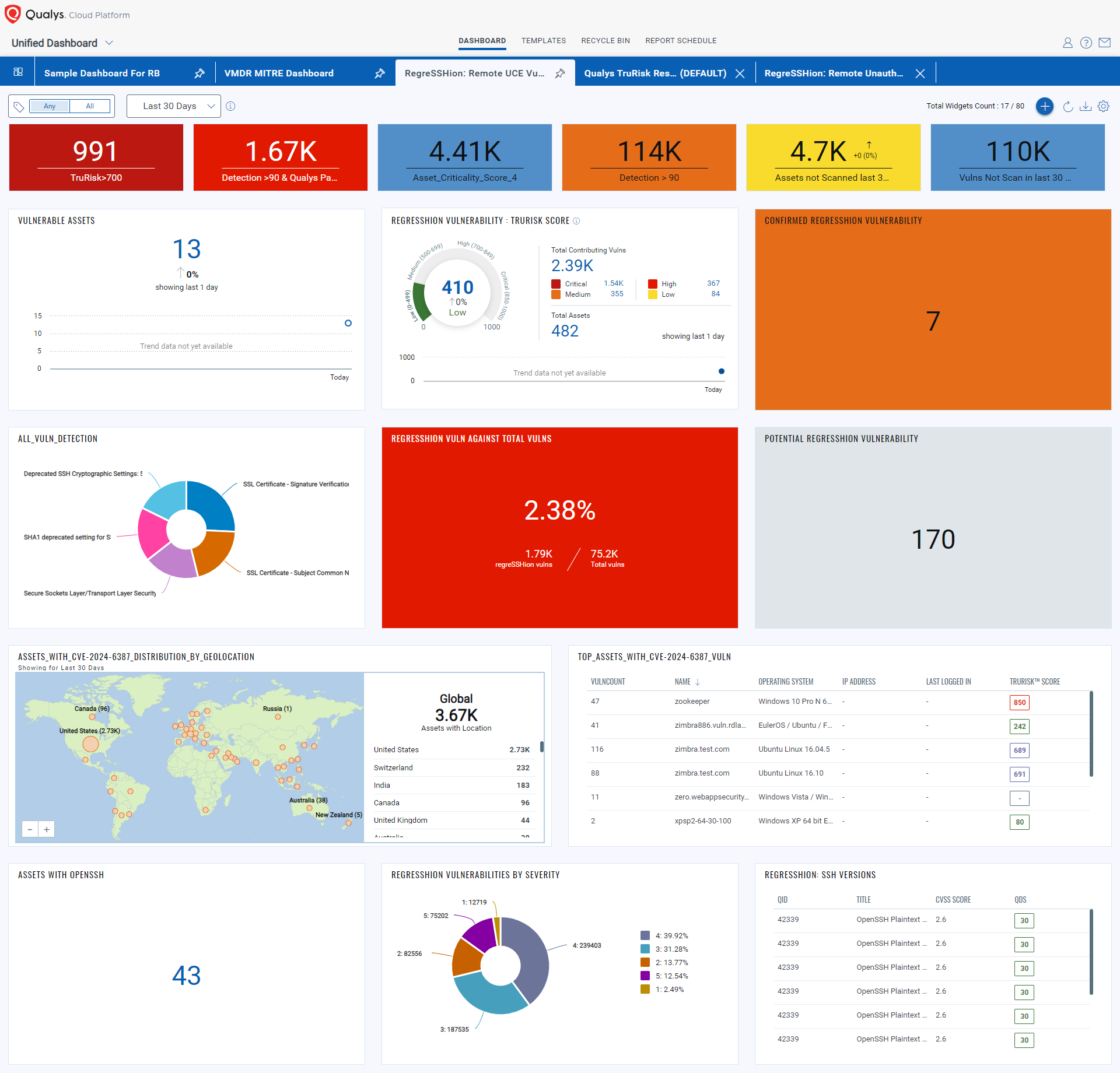
To make it easier for customers to track and manage regreSSHion vulnerability in their subscriptions, we have created the Manage regreSSHion dashboard, which you can download and import into your subscription.
Automatically Patch “regreSSHion” vulnerability With Qualys Patch Management
We expect vendors to release patches for this vulnerability shortly. Qualys Patch Management can automatically deploy those patches to vulnerable assets, when available.
Customers can use the “patch now” button found to the right of the vulnerability to add regreSSHion to a patch job. Once patches are released, Qualys will find the relevant patches for this vulnerability and automatically add those patches to a patch job. This will allow customers to deploy those patches to vulnerable devices, all from the Qualys Cloud Platform.
Free Trial
Qualys Patch Management No-Cost 45-Day Trial
Detect and remediate CVE-2024-6387 with Qualys TotalCloud Container Security
Qualys TotalCloud Container Security offers comprehensive coverage and visibility into vulnerabilities across all your container environments, including managed Kubernetes and on-premises Kubernetes. This empowers organizations to rapidly respond to, prioritize, and mitigate associated risks effectively.
Leverage the power of Qualys TotalCloud Container Security and the Qualys Query Language (QQL) to efficiently identify and prioritize vulnerable assets, ensuring prompt and effective remediation of the vulnerabilities highlighted by CVE-2024-6387.
Use this QQL statement:
state:`RUNNING` and vulnerabilities.cveids:CVE-2024-6387
Qualys Products and Customer Responsibilities
Qualys is cutting the release cycle short for certain products that are deployed on customer premises. At least one of those products depends on a supplier that will publish a fix release shortly. We intend to release fixes for this Severity HIGH CVE in the coming days to ensure that customers are safe from regreSSHion. Once builds have cleared Quality Assurance, we will provide updates to help customers patch.
Frequently Asked Questions (FAQs)
Will the Qualys Research Team publish exploit code or include proof-of-concept code for this vulnerability?
No, as part of our commitment to responsible disclosure and maintaining high-security standards, we will not publish exploit codes. Given the complexity of this vulnerability, it is crucial to allow organizations to apply patches effectively without the immediate pressure of public exploits.
Are there any mitigations for this vulnerability?
If sshd can’t be updated or recompiled, set LoginGraceTime to 0 in the config file. This exposes sshd to a denial of service by using up all MaxStartups connections, but it prevents the remote code execution risk.
Using the following Qualys Policy Compliance (PC) Control, you can evaluate whether the suggested mitigation has been applied to the affected assets.

To execute this evaluation, enable your free trial of Policy Compliance – https://www.qualys.com/forms/policy-compliance/
Using Qualys Custom Assessment and Remediation (CAR), you can easily apply this mitigation across affected assets in one go. Just follow these easy steps:
1. Go to CAR Library, look for Zero Day Utilities, and import the mitigation script.
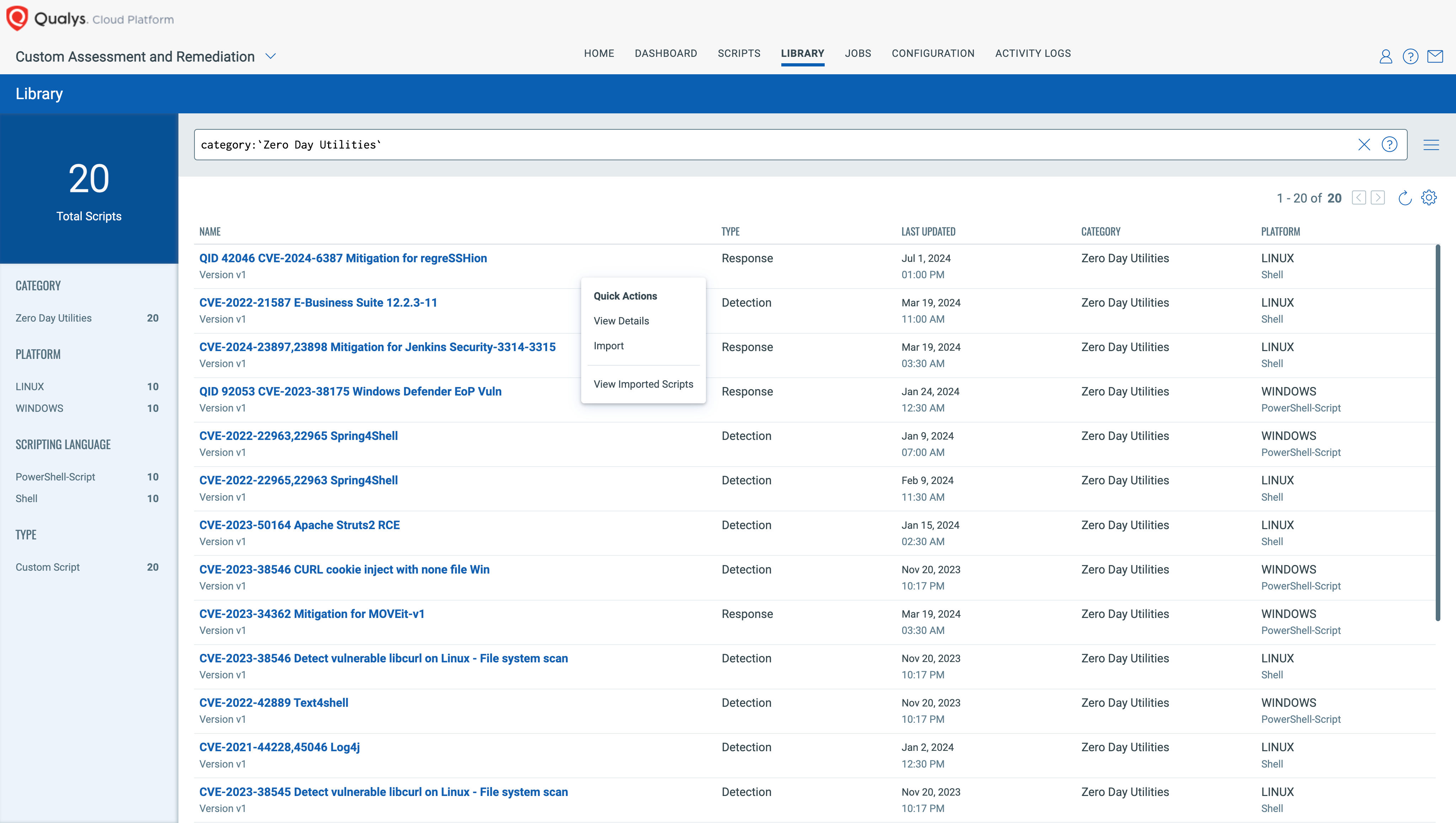
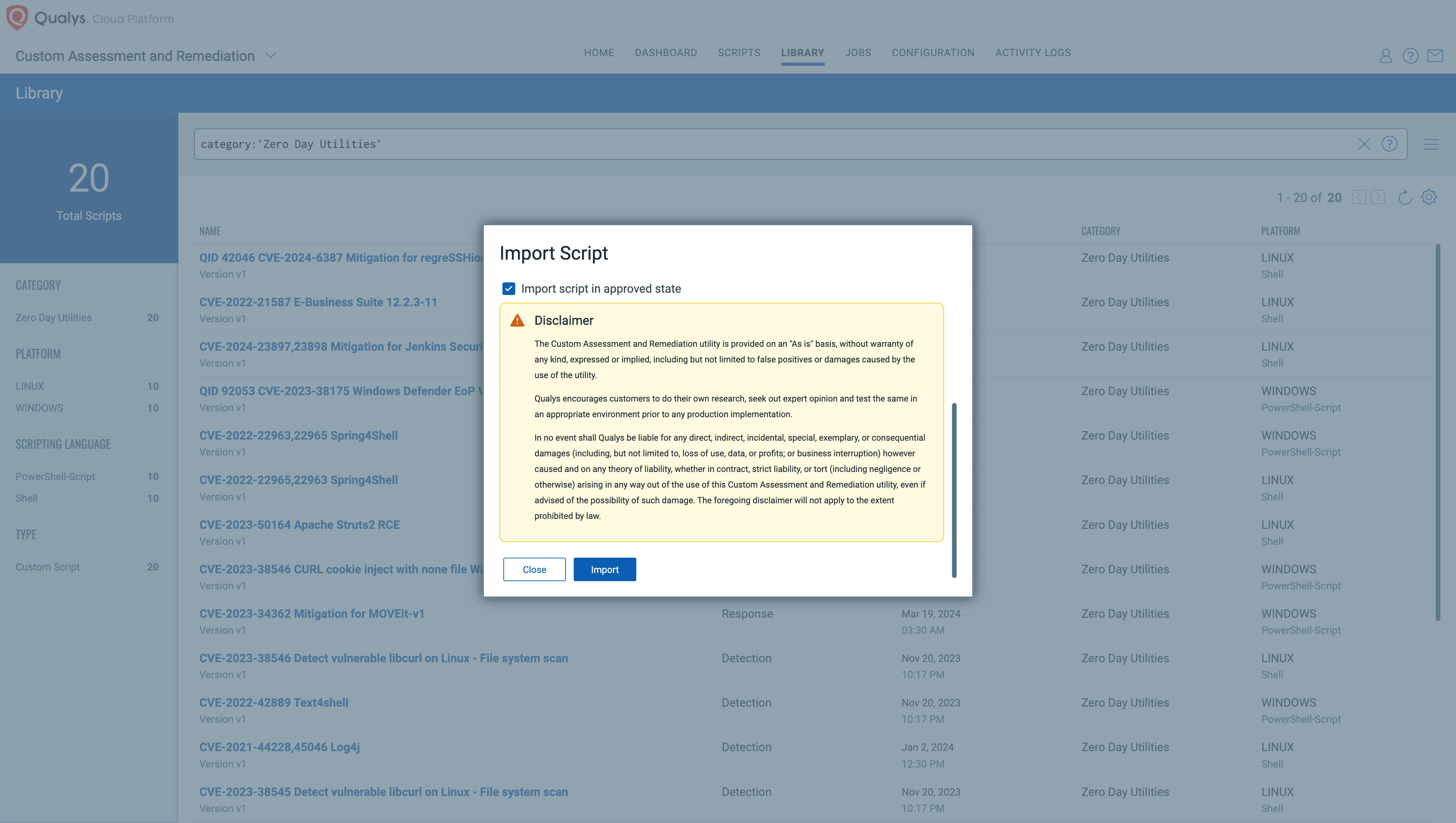
2. You can approve while importing or later on.
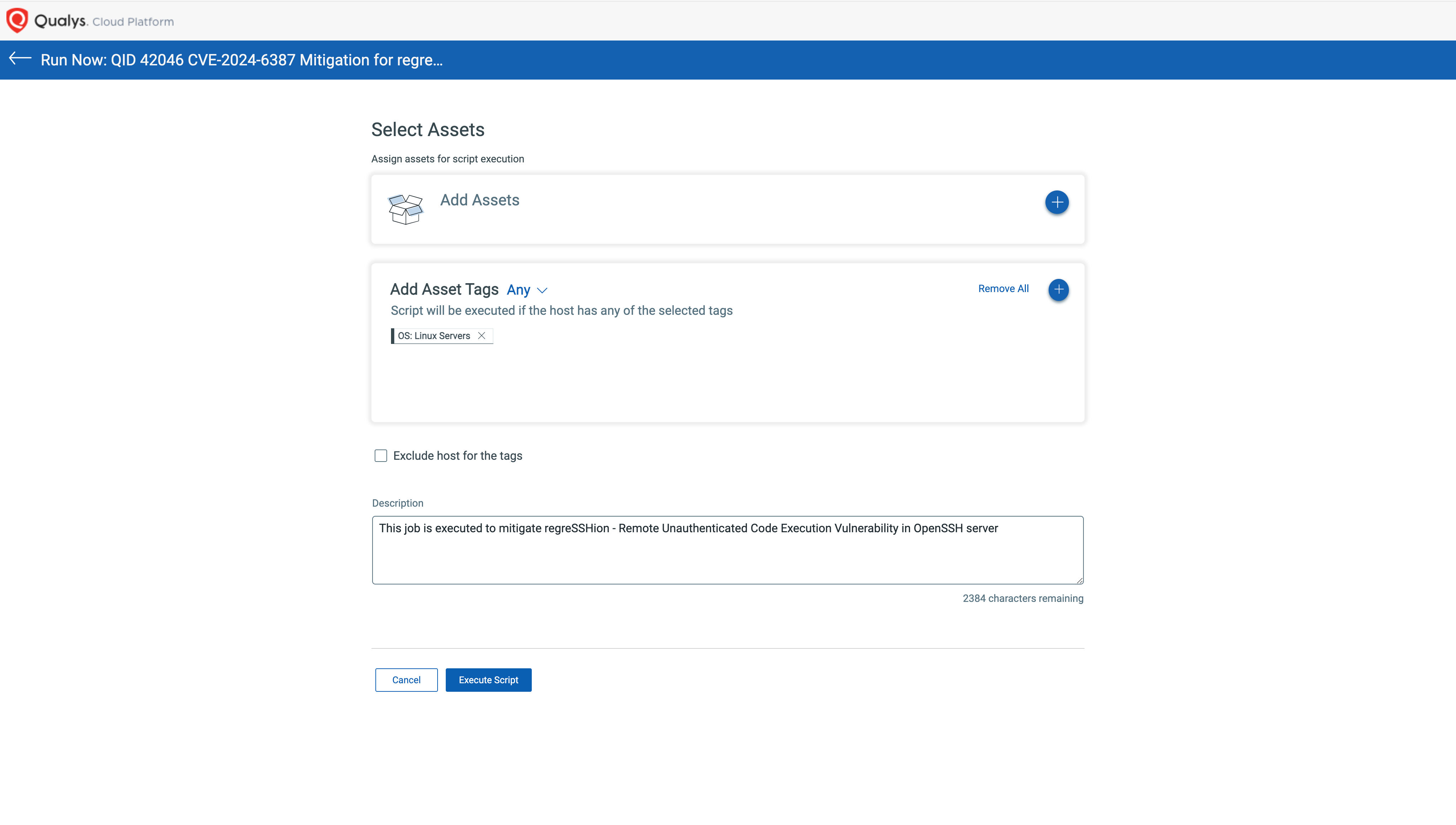
3. Execute it across required assets/asset tags.
To execute this mitigation, enable your free trial of CAR – https://www.qualys.com/forms/custom-assessment-remediation/
Is this vulnerability remotely exploitable?
Yes, this vulnerability can be exploited remotely and allows unauthenticated remote code execution (RCE) as root, posing a significant security risk.
Why is the vulnerability named “regreSSHion”?
This is a pun/reference to this being a regression bug affecting OpenSSH.
Should organizations patch these vulnerabilities urgently?
Yes, we would encourage organizations to patch this vulnerability urgently, especially on their internet-facing assets.
How will the new security fix be implemented for different versions?
This fix is part of a major update, making it challenging to backport. Consequently, users will have two update options: upgrading to the latest version released on Monday, July 1st (9.8p1) or applying a fix to older versions as outlined in the advisory, which is the approach most vendors will take.
Does this vulnerability affect macOS or Windows?
Per Microsoft Security Update Guide and our research team’s discussion with Microsoft, we have concluded that Windows installations are not vulnerable.
The regreSSHion vulnerability is applicable macOS platforms; however, its exploitability on these platforms remains uncertain. Further analysis is required to determine the specific impact.
How can users identify exploitation attempts of this vulnerability?
Exploitation attempts for this vulnerability can be identified by seeing many many lines of “Timeout before authentication” in the logs.
What is the exposure to Qualys infrastructure?
The Qualys security team has taken immediate steps to protect our corporate infrastructure and products from any impact regarding the exploitation of this vulnerability. At this time, we have not experienced any negative impacts or detected any exploitation attempts. In addition, the Qualys security team has implemented enhanced monitoring and response plans to detect and respond to future exploit attempts. Emergency patching procedures have been initiated to fully remediate the vulnerability. To further help the broader security community, we are sharing our detection logic (see FAQ: “How to identify exploitation attempts of this vulnerability?”) to help customers respond should attacks occur before patching and mitigation efforts are completed.
How can users identify systems vulnerable to the OpenSSH regreSSHion vulnerability?
Users can determine if their systems are vulnerable by verifying the version of the OpenSSH server installed. Systems running affected versions should be considered at risk and prioritized for updates.
Under what circumstances might QID 42046 fail to report accurately?
Accurate detection with QID 42046 requires root privileges, as the command used only runs with root access.
Why is a QID categorized as a confirmed or potential vulnerability?
A QID is reported as confirmed in authenticated scan results because these scans can access detailed information that verifies the vulnerability more reliably. On the other hand, remote unauthenticated scans categorize a QID as potential because they primarily depend on the information presented by the OpenSSH service banner. This banner might display a partial version of details, leading to less definitive conclusions about the presence of a vulnerability.
When will the Qualys Detection Score (QDS) be updated?
As the vulnerability begins to trend across various threat intelligence sources, our QDS will utilize these intelligent feeds for dynamic updates. We expect its effectiveness to reach a score of 90 or above.
Has the threat feed been updated to include the regreSSHion vulnerability?
Yes, the Qualys threat feed is updated when emerging threats are tracked and reported from the dark web and other sources. The update activates as soon as a vulnerability trends across various threat intelligence platforms.
No record found for this QID or CVE in Qualys KB. Great job on reporting however the data set is not published.
“Immediate Steps to Mitigate Risk” there’s a config-based mitigation, this section is just marketing nonsense and it’s irresponsible of you to hide the actual immediate mitigation in the “technical details”
This website helped me to learn about Remote Unauthenticated Code Execution Vulnerability in the OpenSSH server. It made it easy to work on the OpenSSH server.
What should be done for the windows servers marked with active for CVE-2024-6387?
The 9.8 patch exists for windows also?