Microsoft and Adobe Patch Tuesday, October 2024 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for October 2024
- Adobe Patches for October 2024
- Zero-day Vulnerabilities Patched in October Patch Tuesday Edition
- Critical Severity Vulnerabilities Patched in October Patch Tuesday Edition
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response with Patch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- Qualys Monthly Webinar Series
Microsoft has rolled out its October 2024 Patch Tuesday updates, offering vital security fixes for IT professionals to implement. With several critical vulnerabilities patched, this release highlights the ongoing need for regular maintenance and attention to security.
Microsoft Patch Tuesday for October 2024
Microsoft Patch’s Tuesday, October 2024 edition addressed 121 vulnerabilities, including three critical and 114 important severity vulnerabilities.
In this month’s updates, Microsoft has addressed two zero-day vulnerabilities known to be exploited in the wild. Microsoft also addressed three vulnerabilities that are publicly disclosed but not exploited in attacks.
Microsoft has addressed three vulnerabilities in Microsoft Edge (Chromium-based), which were patched earlier this month.
Microsoft Patch Tuesday, October edition includes updates for vulnerabilities in Microsoft Office and Components, Microsoft Management Console, Visual Studio, Windows Print Spooler Components, Windows Remote Desktop, Windows Remote Desktop Licensing Service, Windows Remote Desktop Services, .NET Framework, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Security Feature Bypass, and Remote Code Execution (RCE).
The October 2024 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 7 | Important: 7 |
| Denial of Service Vulnerability | 26 | Important: 26 |
| Elevation of Privilege Vulnerability | 28 | Important: 28 |
| Information Disclosure Vulnerability | 6 | Important: 6 |
| Remote Code Execution Vulnerability | 43 | Critical: 3 Important: 40 |
| Security Feature Bypass Vulnerability | 7 | Important: 7 |
Adobe Patches for October 2024
Adobe has released nine security advisories to address 52 vulnerabilities in Substance 3D Painter, Adobe Commerce, Adobe Dimension, Adobe Animate, Adobe Lightroom, Adobe InCopy, Substance 3D Stager, Adobe FrameMaker, and Adobe InDesign. 31 of these vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to arbitrary code execution and privilege escalation.
Zero-day Vulnerabilities Patched in October Patch Tuesday Edition
CVE-2024-43573: Windows MSHTML Platform Spoofing Vulnerability
Windows MSHTML is a browser engine that renders web pages frequently connected to Internet Explorer. Even though the Internet Explorer (IE) 11 desktop application has reached the end of support, MSHTML vulnerabilities are still relevant today and are being patched by Microsoft.
Microsoft has not shared any detailed information about the exploitation of this vulnerability. However, Microsoft mentioned in the advisory that exploitation of the vulnerability involves the MSHTML platform, previously used by Internet Explorer and Legacy Microsoft Edge, whose components are still installed in Windows.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before October 29, 2024.
CVE-2024-43572: Microsoft Management Console Remote Code Execution Vulnerability
Microsoft Management Console (MMC) is a tool that allows users and system administrators to configure, monitor, and manage Microsoft Windows systems. MMC provides a unified interface for managing, administering, and configuring systems.
Microsoft has not released any information about the vulnerability.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before October 29, 2024.
CVE-2024-6197: Open Source Curl Remote Code Execution Vulnerability
Microsoft states, “While the upstream advisory applies to curl, the command line tool, and libcurl as embedded in all software, Windows does not ship libcurl but only ships the curl command line. This vulnerability requires user interaction to select the server and to communicate with it.” Successful exploitation of the vulnerability requires a client to connect to a malicious server, which could allow the attacker to gain code execution on the client.
CVE-2024-20659: Windows Hyper-V Security Feature Bypass Vulnerability
Hyper-V is a virtualization technology in Windows that allows users to run multiple operating systems as virtual machines (VMs) on a physical host computer.
An attacker must first gain access to the restricted network before running an attack. Successful exploitation of the vulnerability may allow an attacker to compromise the hypervisor and kernel. This Hypervisor vulnerability relates to Virtual Machines within a Unified Extensible Firmware Interface (UEFI) host machine. An attacker may bypass the UEFI on some specific hardware, which could compromise the hypervisor and the secure kernel.
CVE-2024-43583: Winlogon Elevation of Privilege Vulnerability
Successful exploitation of the vulnerabilities may allow an attacker to gain SYSTEM privileges. Microsoft suggests enabling first-party IME to protect from this vulnerability.
Critical Severity Vulnerabilities Patched in October Patch Tuesday Edition
CVE-2024-43468: Microsoft Configuration Manager Remote Code Execution Vulnerability
Microsoft Configuration Manager (ConfigMgr) is a systems management software that helps IT professionals manage large groups of computers and servers. The software deploys operating systems to devices and manages hardware and software inventory.
An unauthenticated attacker may exploit this vulnerability by sending specially crafted requests to the target environment, which are processed unsafely. Successful exploitation of the vulnerability may allow the attacker to execute commands on the server and/or underlying database.
CVE-2024-43582: Remote Desktop Protocol Server Remote Code Execution Vulnerability
Remote DesktopProtocol (RDP) is a secure network communication protocol that allows users to access and control a computer remotely through a network connection. RDP is a technical standard for remote desktop software that is available for most Windows and Mac operating systems.
To exploit the vulnerability, an unauthenticated attacker must send malicious packets to a RPC host. Successful exploitation of the vulnerability may result in remote code execution on the server side with the same permissions as the RPC service.
CVE-2024-43488: Visual Studio Code extension for Arduino Remote Code Execution Vulnerability
The Visual Studio Code (VS Code) extension for Arduino allows users to develop, build, and deploy Arduino sketches in VS Code. The extension includes several features, such as syntax highlighting and IntelliSense, as well as automatic project scaffolding.
Missing authentication for critical functions in the Visual Studio Code extension for Arduino allows an unauthenticated attacker to perform remote code execution.
Other Microsoft Vulnerability Highlights
- CVE-2024-43502 is an elevation of privilege vulnerability in Windows Kernel. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
- CVE-2024-43581 and CVE-2024-43615 are remote code execution vulnerabilities in Microsoft OpenSSH for Windows. Successful exploitation of the vulnerability may allow an attacker to perform remote code execution on the target server.
- CVE-2024-43609 is a spoofing vulnerability in Microsoft Office. In a web-based attack scenario, an attacker may host a website or server containing a specially crafted file to exploit the vulnerability. An attacker would have to convince the user to click a link, typically through an enticement in an email or Instant Messenger message, and then convince the user to open the specially crafted file.
- CVE-2024-43509 and CVE-2024-43556 are elevation of privileges vulnerabilities in the Windows Graphics Component. Successful exploitation of the vulnerabilities may allow an attacker to gain SYSTEM privileges.
- CVE-2024-43560 is an elevation of privilege vulnerability in the Microsoft Windows Storage Port Driver. Successful exploitation of the vulnerabilities may allow an attacker to gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Hyper-V, Windows EFI Partition, Windows Kernel, OpenSSH for Windows, Azure Monitor, Windows Netlogon, Windows Kerberos, BranchCache, Azure Stack, Windows Routing and Remote Access Service (RRAS), .NET and Visual Studio, Microsoft Configuration Manager, Service Fabric, Power BI, .NET, Visual Studio Code, DeepSpeed, Windows Resilient File System (ReFS), Windows Common Log File System Driver, Microsoft Office SharePoint, Microsoft Office Excel, Microsoft Office Visio, Microsoft Graphics Component, Windows Standards-Based Storage Management Service, Windows BitLocker, Windows NTFS, Internet Small Computer Systems Interface (iSCSI), Windows Secure Kernel Mode, Microsoft ActiveX, Windows Telephony Server, Microsoft WDAC OLE DB provider for SQL, Windows Local Security Authority (LSA), Windows Mobile Broadband, RPC Endpoint Mapper Service, Remote Desktop Client, Windows Kernel-Mode Drivers, Microsoft Simple Certificate Enrollment Protocol, Windows Online Certificate Status Protocol (OCSP), Windows Cryptographic Services, Windows Secure Channel, Windows Storage, Windows Shell, Windows NT OS Kernel, Windows Storage Port Driver, Windows Network Address Translation (NAT), Windows Ancillary Function Driver for WinSock, Sudo for Windows, Windows MSHTML Platform, Microsoft Windows Speech, Microsoft Office, Winlogon, Windows Scripting, Code Integrity Guard, Visual C++ Redistributable Installer, Azure CLI, Outlook for Android, Microsoft Defender for Endpoint, Windows cURL Implementation, and Microsoft Edge (Chromium-based).
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
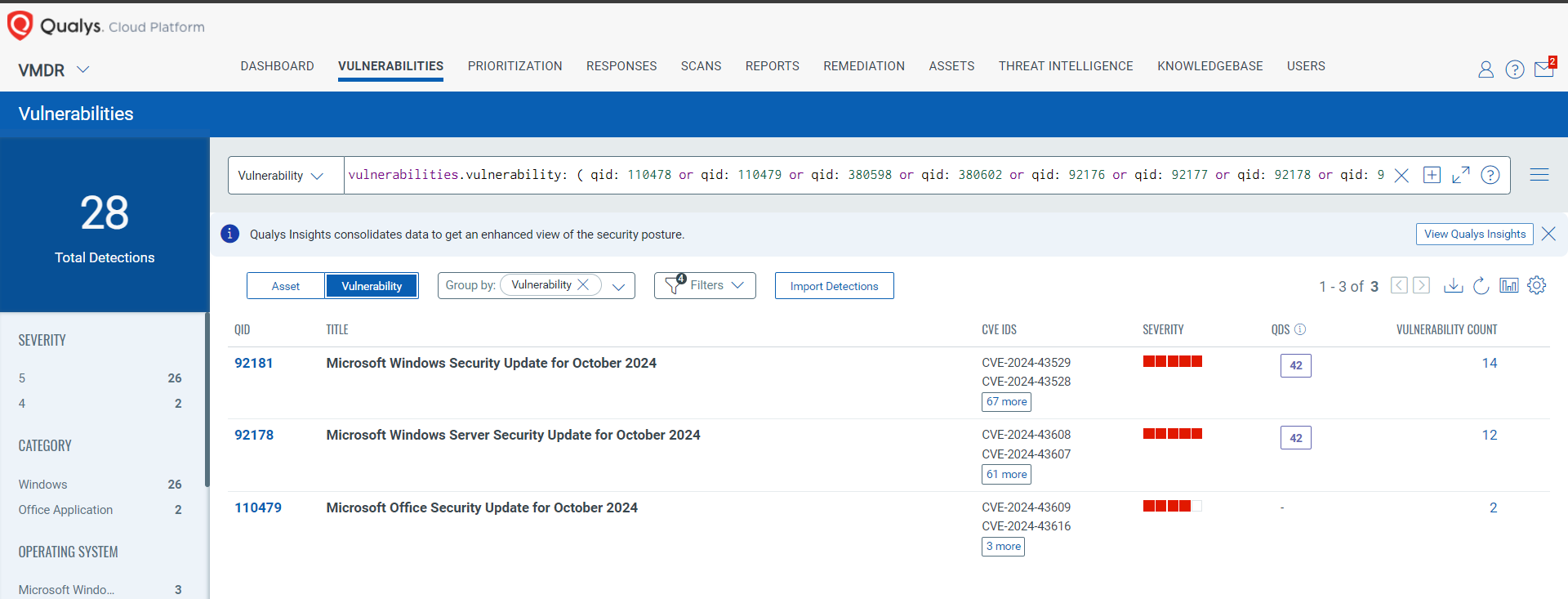
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 110478 or qid: 110479 or qid: 380598 or qid: 380602 or qid: 92176 or qid: 92177 or qid: 92178 or qid: 92179 or qid: 92180 or qid: 92181)
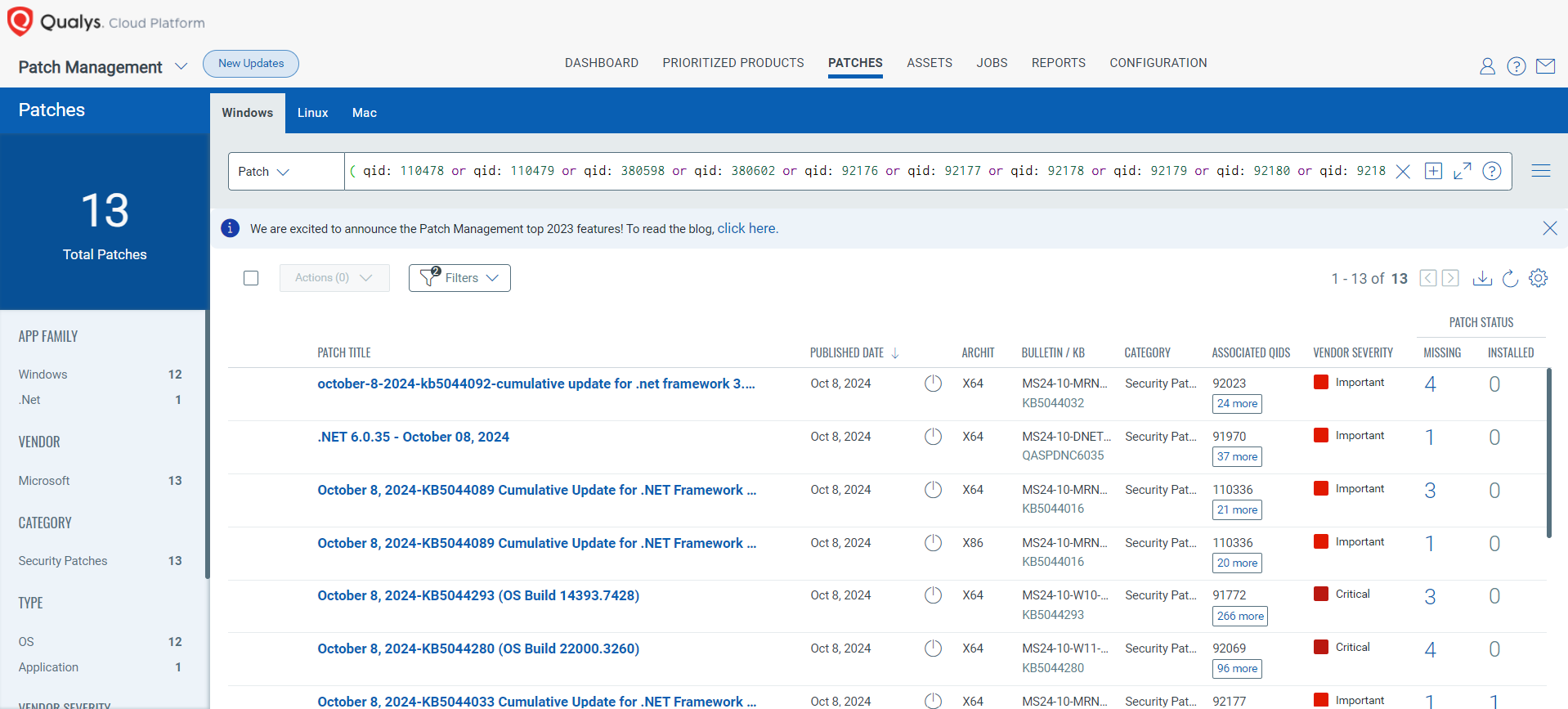
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 110478 or qid: 110479 or qid: 380598 or qid: 380602 or qid: 92176 or qid: 92177 or qid: 92178 or qid: 92179 or qid: 92180 or qid: 92181)
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now, these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2024-43533: Remote Desktop Client Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 8.8 / 7.7
Policy Compliance Control IDs (CIDs):
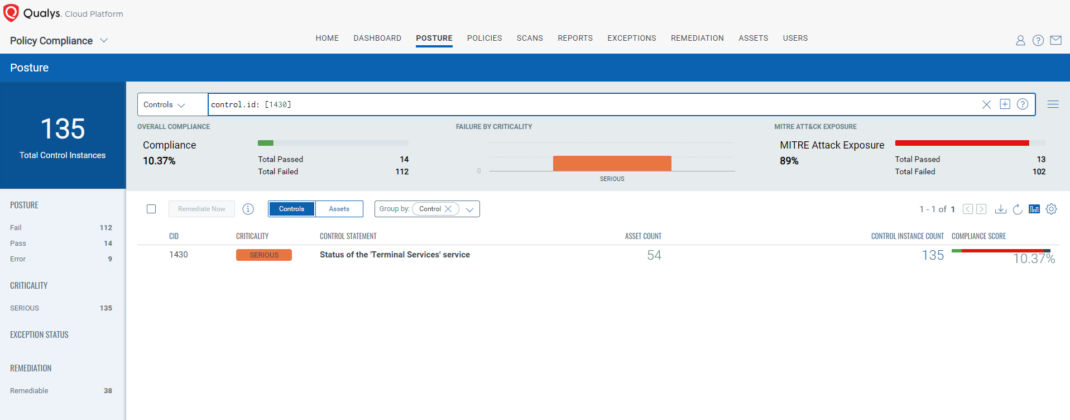
- 1430 Status of the ‘Terminal Services’ service
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [1430]
CVE-2024-43609: Microsoft Office Spoofing Vulnerability
This vulnerability has a CVSS:3.1 6.5 / 5.7
Policy Compliance Control IDs (CIDs):
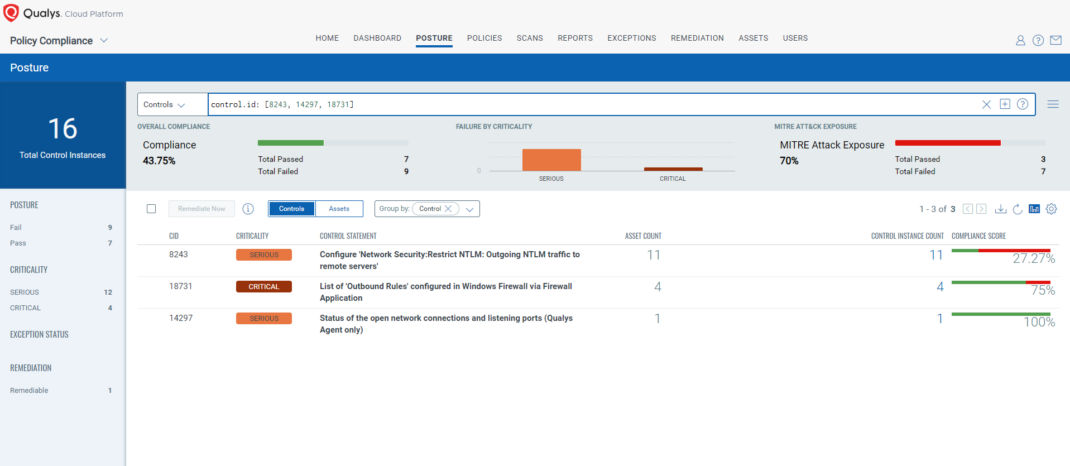
- 8243 Configure ‘Network Security:Restrict NTLM: Outgoing NTLM traffic to remote servers’
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
- 18731 List of ‘Outbound Rules’ configured in Windows Firewall via Firewall Application
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [8243, 14297, 18731]
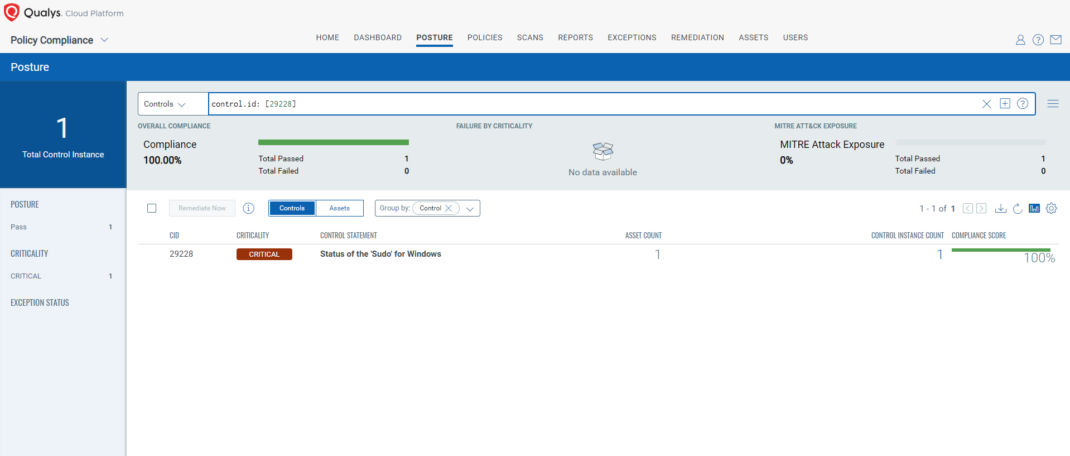
CVE-2024-43571: Sudo for Windows Spoofing Vulnerability
This vulnerability has a CVSS:3.1 5.6 / 4.9
Policy Compliance Control IDs (CIDs):
- 29228 Status of the ‘Sudo’ for Windows
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [29228]
The next Patch Tuesday falls on November 12, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to “This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series
The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
Thank you! May we also have the QQL too please?
The blog currently states that MS addressed “two” zero-days, but MS actually addressed five. The five are correctly listed under the zero-day section, but the summary above it says there are only two. Just a heads up on the typo :)
The blog currently states that MS addressed “two” zero-days, but MS actually addressed five. The five are correctly listed under the zero-day section, but the summary above it says there are only two. Just a heads up on the typo
wao great The October 2024 Patch Tuesday update from Microsoft and Adobe addresses multiple security vulnerabilities across various products. Microsoft released patches for critical vulnerabilities in Windows, Azure, Exchange Server, and other software, while Adobe focused on vulnerabilities in Acrobat, Reader, and other products. Users are strongly advised to update their systems to mitigate potential threats.