Apache Struts CVE-2024-53677: File Upload Vulnerability, Impact, and Mitigation Strategies
Apache has announced a critical vulnerability affecting Apache Struts (CVE-2024-53677), a widely used Java-based web application framework. Struts is integral to many enterprise environments due to its robust architecture, extensive data validation capabilities, and seamless integration with other technologies. These qualities make Struts a preferred choice for large-scale, mission-critical applications, heightening the significance of newly discovered security risks.
Why Apache Struts (CVE-2024-5367) Poses a Serious Risk to Enterprises
The flaw lies in Struts’ file upload mechanism; affected versions include Struts 2.0.0 through 2.3.37 (End-of-life), Struts 2.5.0 through 2.5.33, and Struts 6.0.0 through 6.3.0.2. Attackers can manipulate file upload parameters to enable path traversal, allowing them to place malicious files into otherwise restricted directories. Under certain conditions, this can lead to remote code execution, enabling unauthorized actors to run arbitrary code, exfiltrate sensitive data, or compromise entire systems.
Apache Struts sits at the heart of many corporate IT stacks, driving public-facing portals, internal productivity applications, and critical business workflows. Its popularity in high-stakes contexts means that a vulnerability like CVE-2024-53677 could have far-reaching implications.
How To Remediate Apache Struts Exploit
Users are strongly advised to upgrade to Apache Struts 6.4.0 or later and migrate to the new file upload mechanism. To do so, you must migrate to the new file upload mechanism. While this transition is not backward compatible and may require rewriting specific actions and interceptors, it is necessary to ensure ongoing security and stability. Continuing to rely on legacy file upload methods leaves systems open to attack.
Qualys Solutions For Apache Struts
Detecting The Apache Struts Vulnerability
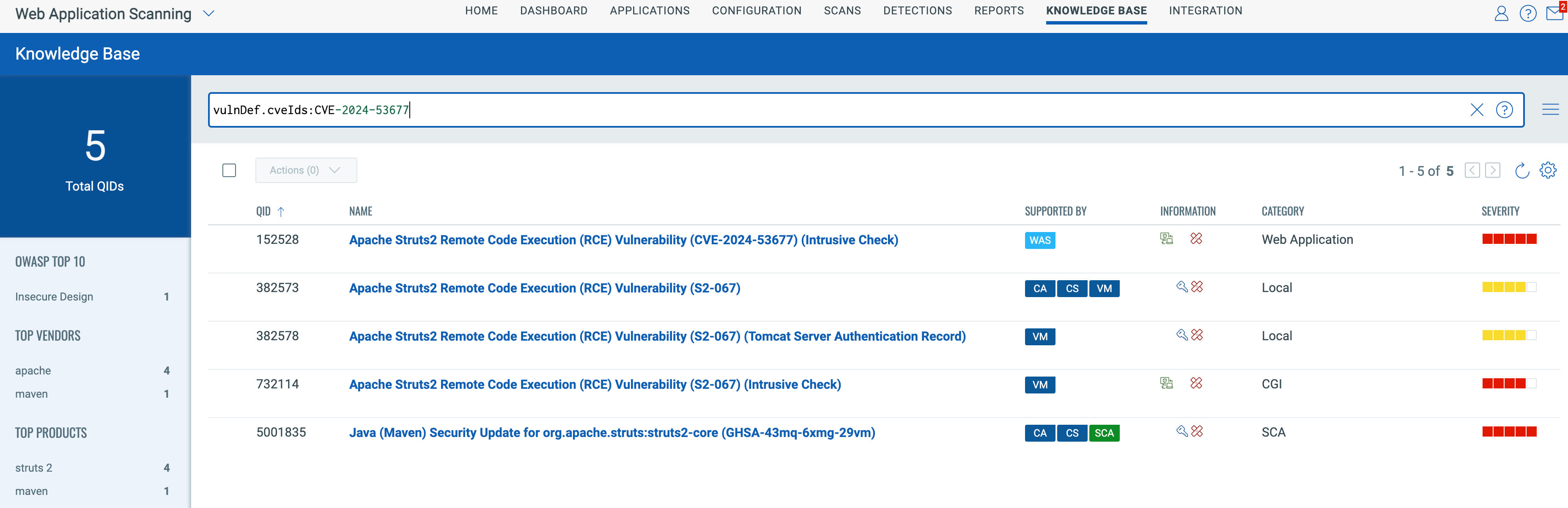
Qualys customers can use the following Qualys IDs (QIDs) to scan their environments, gain practical insights into this vulnerability’s potential impact, identify vulnerable assets, and guide effective remediation efforts.
| QID | Title |
| 382573 | Apache Struts2 Remote Code Execution (RCE) Vulnerability (S2-067) |
| 382578 | Apache Struts2 Remote Code Execution (RCE) Vulnerability (S2-067) (Tomcat Server Authentication Record) |
| 5001835 | Java (Maven) Security Update for org.apache.struts:struts2-core (GHSA-43mq-6xmg-29vm) |
Qualys has released the QIDs above, which are available starting from version VULNSIGS-2.6.213-2 of the vulnsigs.
Maximize Risk Reduction Using Qualys VMDR, TruRisk, and QQL
Qualys Vulnerability Management, Detection, and Response (VMDR) delivers comprehensive visibility into your environment’s vulnerabilities, enabling rapid response, prioritization, and effective risk mitigation. Integrating Qualys VMDR with Qualys Patch Management allows you to quickly remediate identified vulnerabilities, ensuring a more resilient and secure infrastructure.
Combine Qualys VMDR with TruRisk and the Qualys Query Language (QQL) to maximize the impact of your security strategy. Together, these tools streamline identifying and prioritizing vulnerable assets, helping you address threats more efficiently and safeguard your organization against emerging risks.
Use this QQL statement:
vulnerabilities.vulnerability.cveIds: CVE-2024-53677

Uncovering Hidden Risks with Software Composition Analysis (SCA)
Modern software is built on complex layers of dependencies, including numerous open-source frameworks and libraries. Software Composition Analysis (SCA) plays a critical role in continuously identifying, assessing, and managing vulnerabilities within these components, no matter where they reside. Unlike traditional scanning methods that often focus on familiar paths and may miss deeply nested or non-standard directories, SCA comprehensively crawls your entire file system. This holistic approach pinpoints vulnerabilities deep within your codebase, giving security and DevOps teams clear insights into package usage, helping them prioritize remediation efforts, and ultimately reducing the window of opportunity for potential attackers.
Deploying the Qualys Cloud Agent equips organizations with more sophisticated, in-depth detection capabilities. Leveraging its Software Composition Analysis (SwCA) feature, the agent identifies and reports on software components and vulnerabilities in third-party or open-source dependencies, delivering comprehensive insights into the security posture of various applications.
Use this QQL statement:
vulnerabilities.vulnerability.cveIds:CVE-2024-53677 and vulnerabilities.vulnerability.category:`SCA`


By adopting SwCA, organizations gain a holistic view of their software ecosystem, empowering them to address CVE-2024-53677 and other potential vulnerabilities effectively.
Qualys WAS For Apache Struts Vulnerability Detection
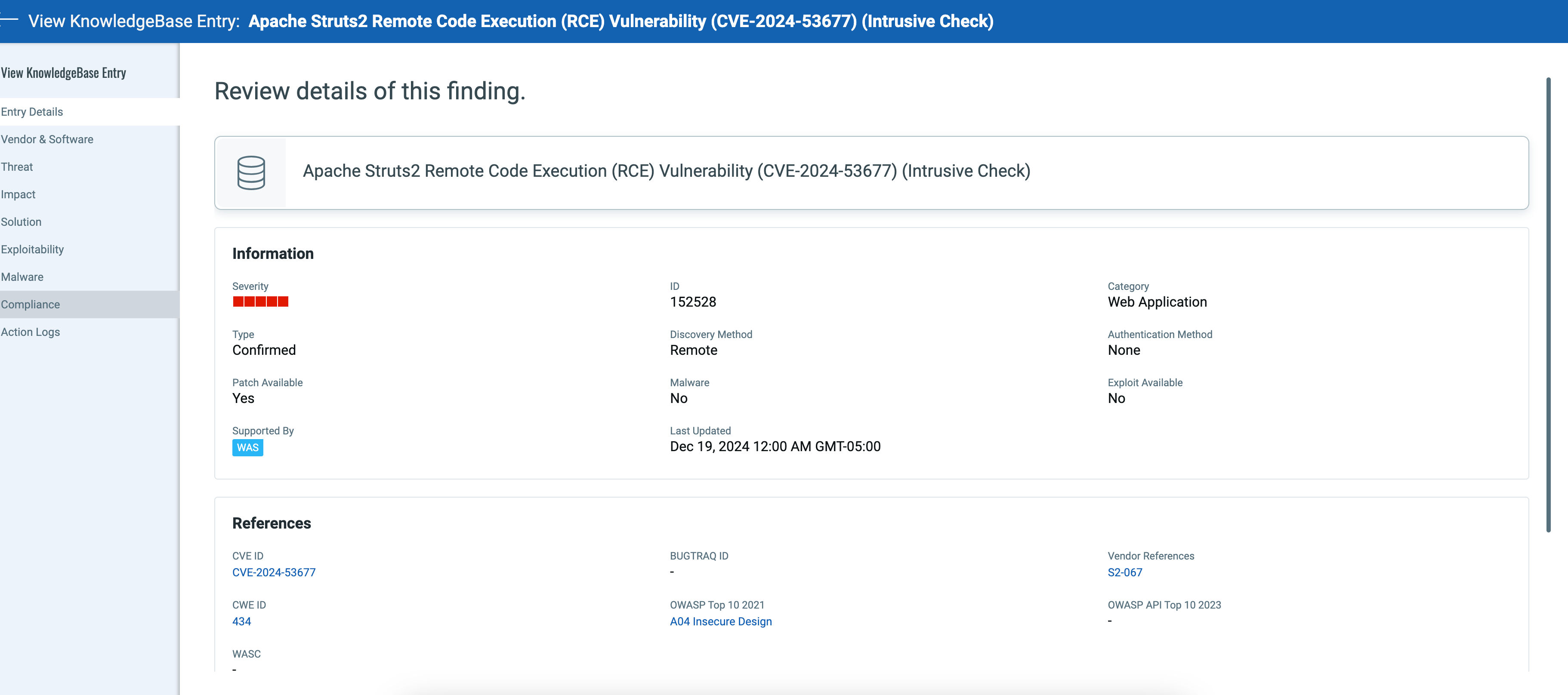
Launch WAS scan against your applications to detect the vulnerability. QID 152528 – Apache Struts2 Remote Code Execution (RCE) Vulnerability (CVE-2024-53677) will be reported if your application has the vulnerable instance of Apache Struts. You can get information regarding the vulnerability by querying the knowledge base.
Mitigate Risk with Qualys TruRisk Mitigate
Qualys TruRisk Mitigate helps you address critical Apache Struts vulnerabilities without the need to apply patches directly. This solution extends beyond traditional patch management, empowering you to effectively mitigate a broad range of vulnerabilities and reduce overall risk exposure.
In conclusion, CVE-2024-53677 poses a significant threat to businesses using Apache Struts, potentially enabling attackers to achieve remote code execution, compromise sensitive data, and undermine core business applications. Organizations must promptly update to Struts 6.4.0 or later to mitigate the risk and transition to the updated file upload mechanism. Coupled with proactive detection and remediation strategies—such as leveraging Qualys VMDR, Patch Management, Software Composition Analysis, and Qualys TruRisk Mitigate—organizations can effectively identify, prioritize, and resolve vulnerabilities, ensuring the security and resilience of their application environments.