NotLockBit: A Deep Dive Into the New Ransomware Threat
Overview
NotLockBit is a new and emerging ransomware family that actively mimics the behavior and tactics of the well-known LockBit ransomware. It distinguishes itself by being one of the first fully functional ransomware strains to target macOS and Windows systems. Distributed as an x86_64 golang binary, NotLockBit showcases a high degree of sophistication while maintaining compatibility with both operating systems, highlighting its cross-platform capabilities.
Our analysis reveals that this new strain demonstrates advanced capabilities, including targeted file encryption, data exfiltration, and self-deletion mechanisms. These features, along with its ability to mimic existing ransomware families, make NotLockBit a significant and evolving threat in the ransomware landscape.
Technique Tactics & Procedures
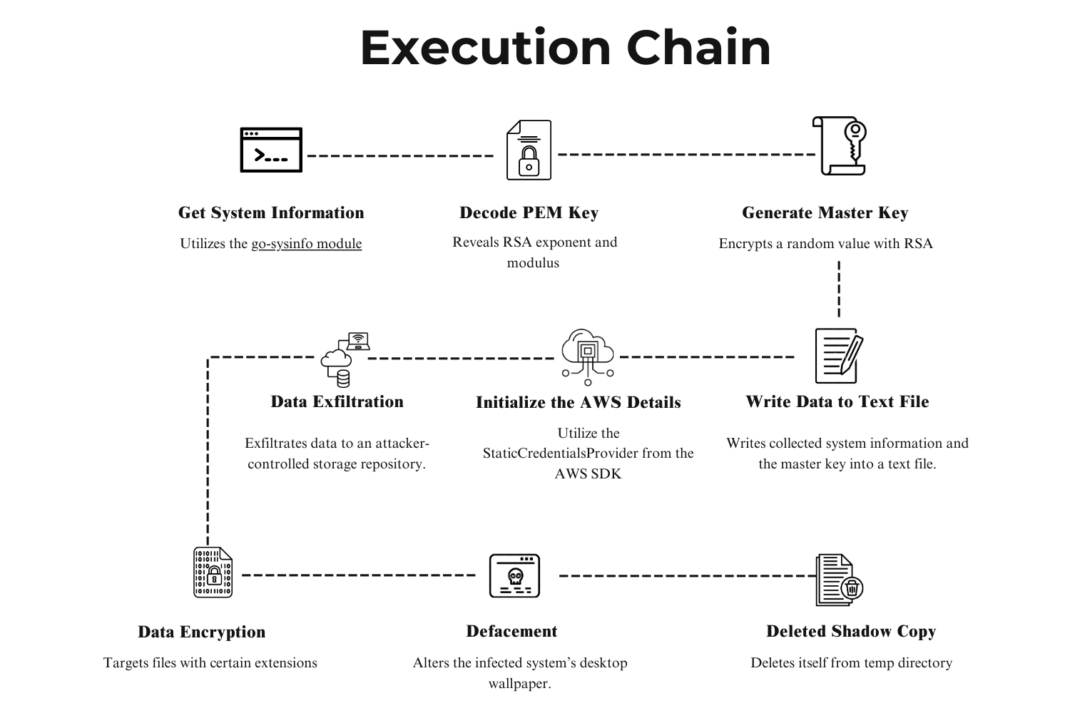
Sample Analysis
NotLockBit ransomware, like many modern ransomware strains, is written in the Go programming language. This choice of language provides several advantages for the malware author, such as fast development cycles, cross-platform compatibility, and robust performance.
This blog presents the analysis of the following samples, along with their corresponding hashes
- e02b3309c0b6a774a4d940369633e395b4c374dc3e6aaa64410cc33b0dcd67ac
- 14fe0071e76b23673569115042a961136ef057848ad44cf35d9f2ca86bd90d31
Initialization
The NotLockBit ransomware, when executed on a macOS target, performs a series of actions to gather critical system information. This is part of its initial reconnaissance phase, which allows the malware to adapt its behavior based on the target system’s specifics.
1. Get System Information:
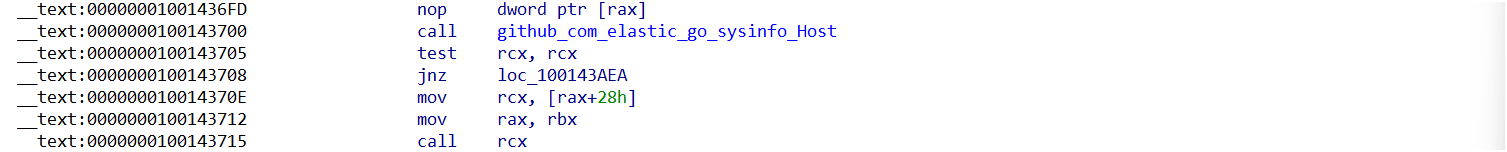
It utilizes the go-sysinfo module to gather system information. The module helps the ransomware collect detailed data about the host’s hardware, software, and network configuration.
2. Decode PEM File:
The public key is encoded using the Privacy Enhanced Mail (PEM) format, a widely used method for storing and transmitting cryptographic data in a Base64 format.
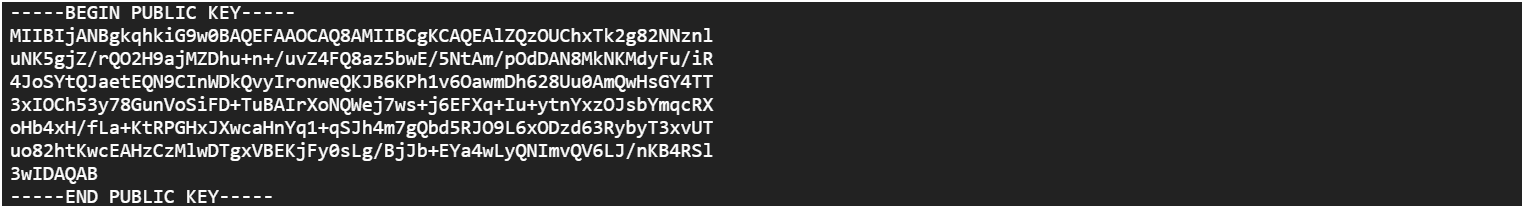
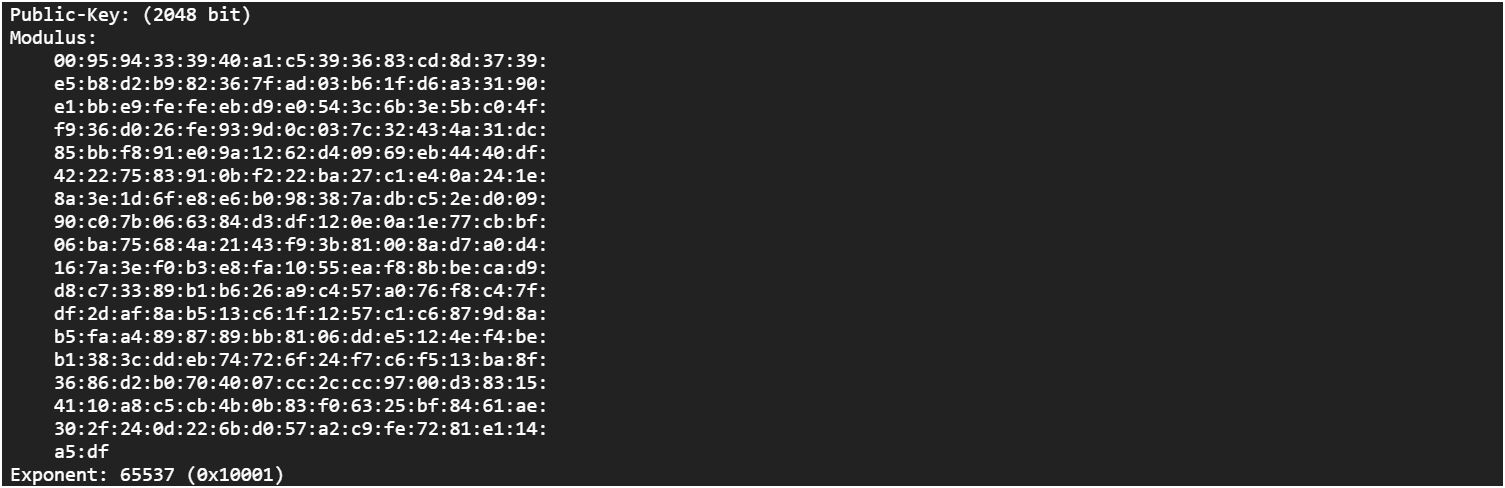
3. Generate and Encrypt Master Key:
The process begins by generating a random value, which serves as the foundation for encryption. This random value is then encrypted using the RSA details (exponent and modulus) extracted from the PEM file. The RSA encryption algorithm utilizes these components to securely encrypt the random value, ensuring that only the corresponding private key can decrypt it.
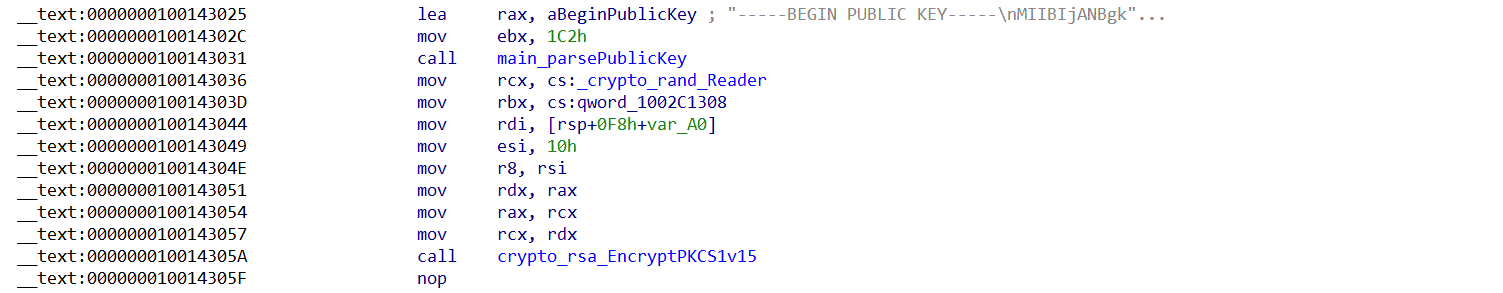
4. Write Collected Information to text file
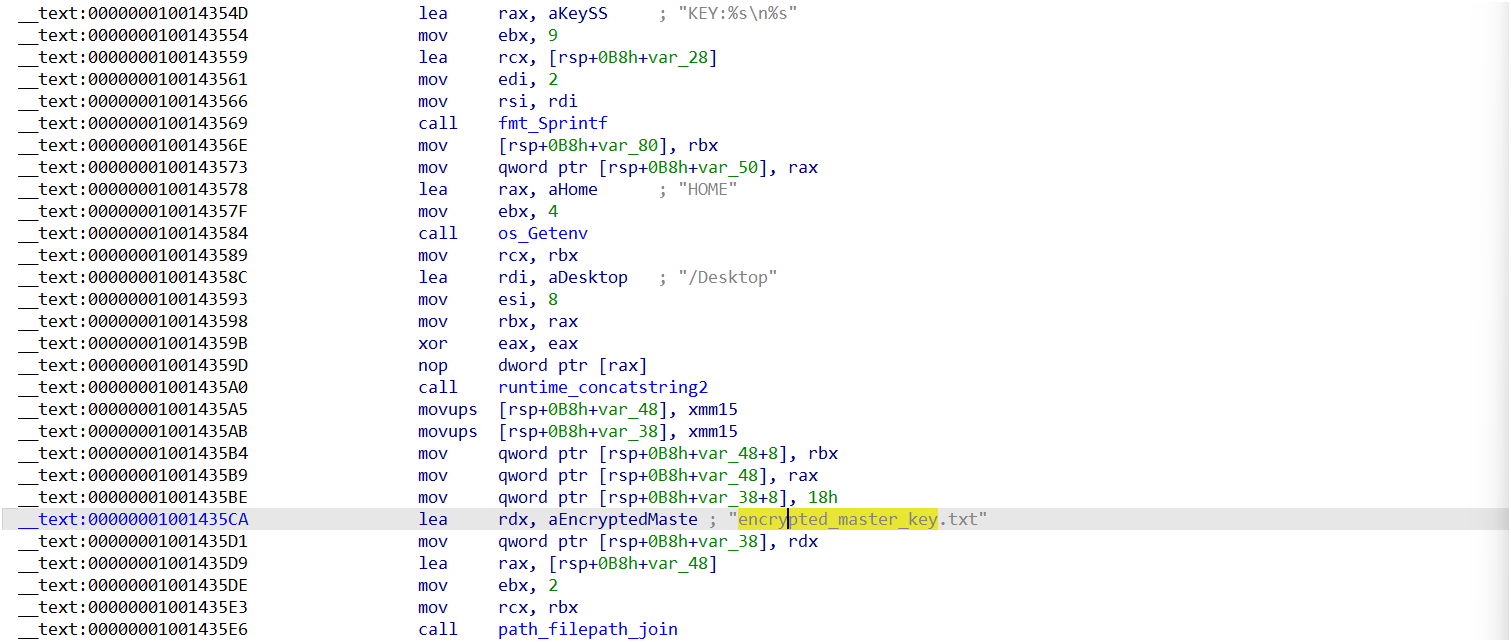
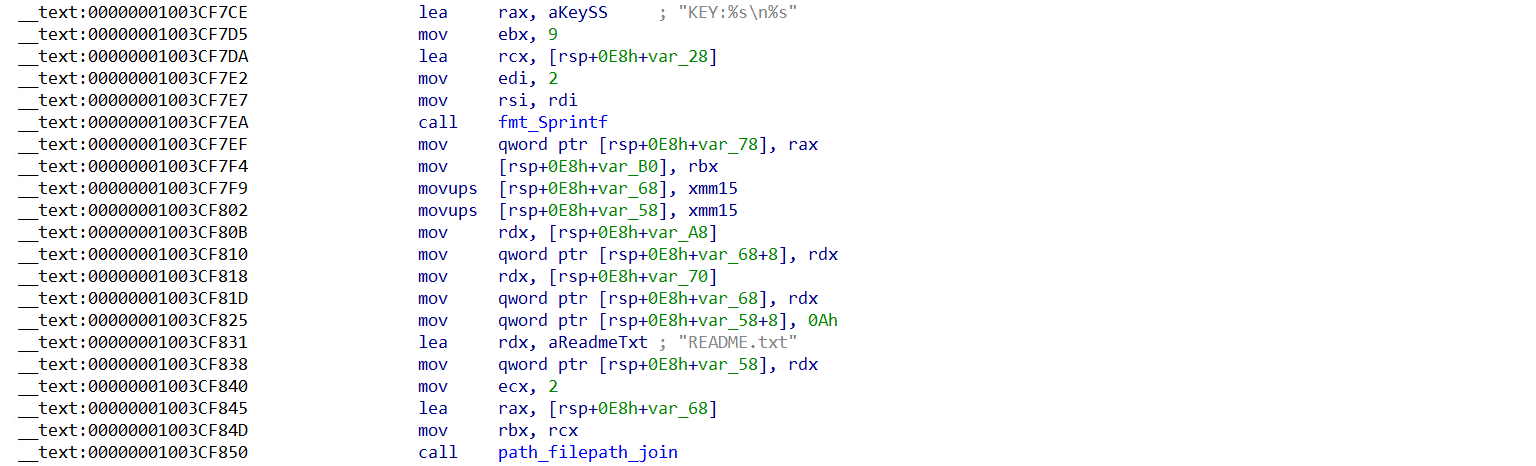
The behavior observed in one of the samples involves retrieving the HOME environment variable, appending /Desktop it, and then storing data in a file named “encrypted_master_key.txt” on the user’s desktop. In contrast, another sample stored data to a file named “Readme.txt”.
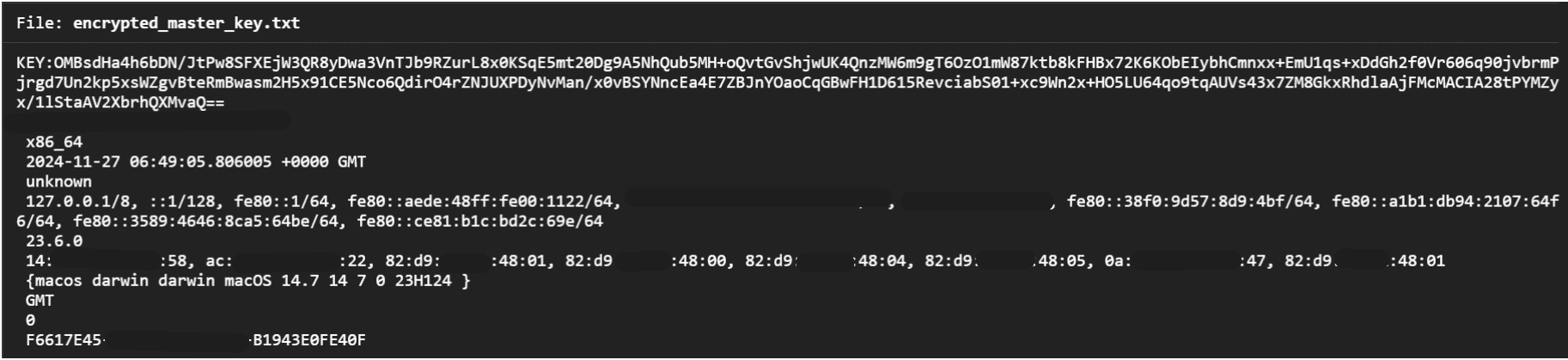
The text file encrypted_master_key.txt contains the following details.
| Encrypted Key | The master key, which has been encrypted using the RSA values decoded from the PEM file. |
| Machine Architecture | Information about the system’s architecture. |
| Timestamp | The exact time when the data was written or the encryption process occurred. |
| IP Information | Details about the machine’s network IP address or network configuration. |
| Machine Version Info | Information about the operating system and its version on the machine. |
| Machine UUID | The unique identifier was assigned to the machine for identification purposes. |
5. Load AWS Credentials
Utilize the StaticCredentialsProvider from the AWS SDK for Go v2 library to configure static credentials, which are defined by hard-coded values for AccessKeyID, SecretAccessKey, and AWS_REGION.
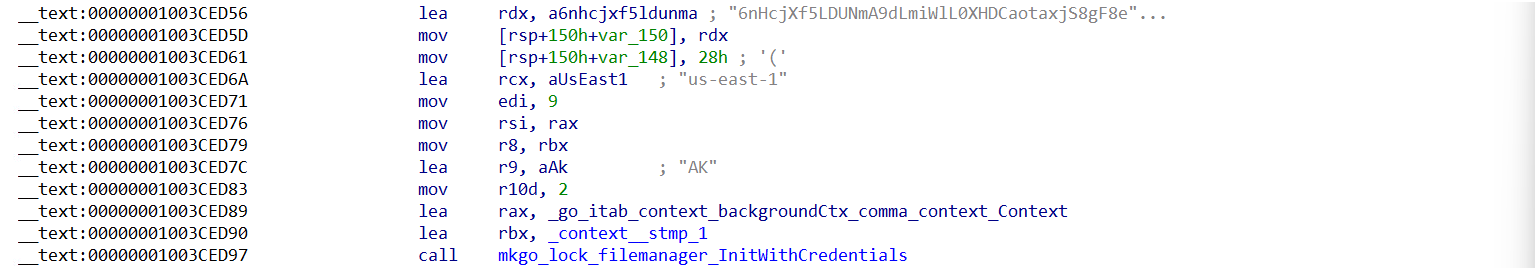
Data Exfiltration
Beyond merely encrypting files, NotLockBit engages in exfiltration by transferring the files to a storage repository under the attacker’s control. This repository is typically configured as an Amazon S3 bucket or another form of remote storage server. By implementing data exfiltration, the attackers ensure continuous access to the victim’s sensitive information, which might be subsequently leveraged for double extortion tactics, threatening to publicly disclose or sell the stolen data if the ransom is not paid.
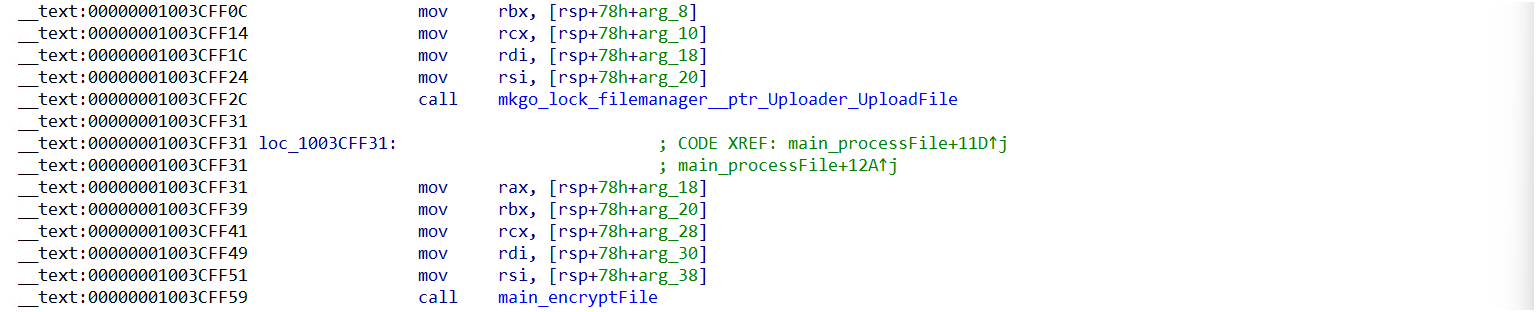
Data Encryption
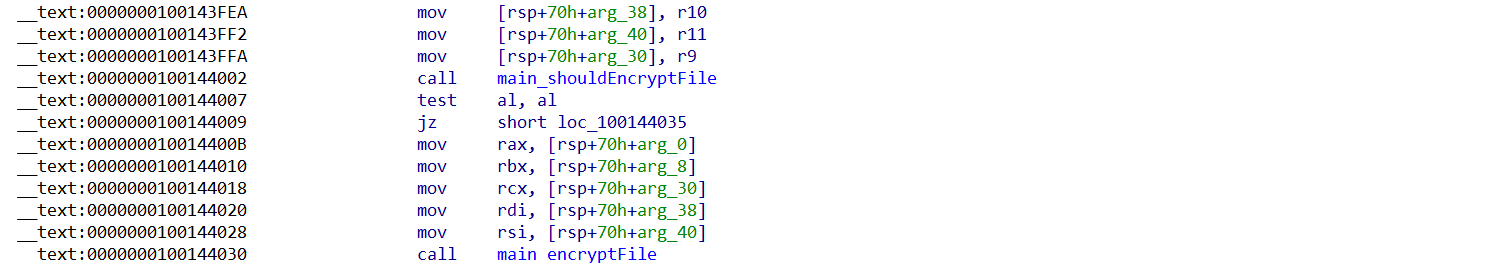
The ransomware scans the file system while deliberately skipping directories such as /proc/, /sys/, /dev/, /usr/, and /run/. It specifically targets files with certain extensions, focusing on personal and professional data as well as virtual machine files.
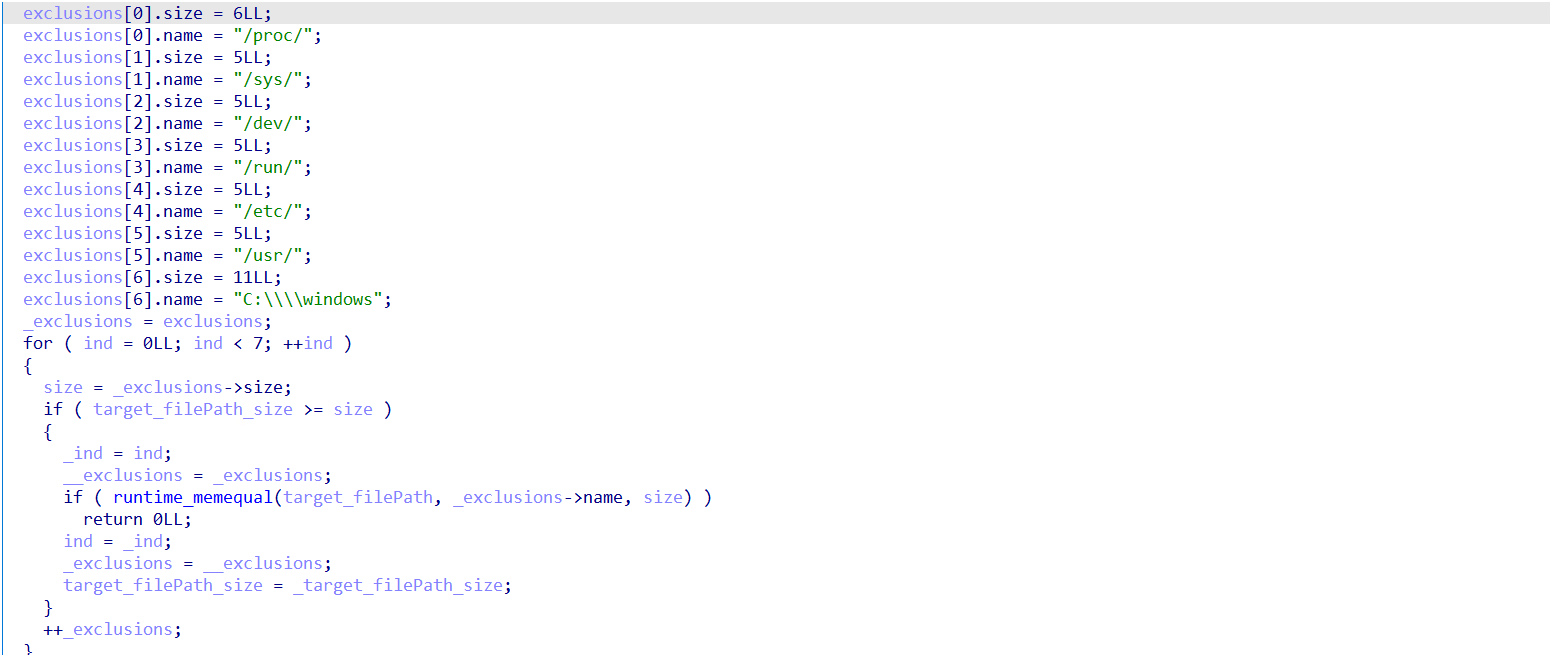
The ransomware is programmed to focus on specific file types by referencing a predefined list of extensions. These include common formats such as documents, image files, and other data types frequently used in personal or professional contexts.
Based on analyzed samples, the malware primarily targets user files and commonly used formats. Extensions such as .csv, .doc, .png, .jpg, .pdf, .txt, .vmdk, .vmsd, and .vbox are among those encrypted, as they often represent valuable or sensitive data typically found in personal or professional environments.
| .3ds | .asp | .avi | .bak | .bz2 | .cfg | .cpp | .csv | .ctl | .dbf |
| .doc | .dwg | .eml | .fdb | .frm | .hdd | .ibd | .iso | .jar | .jpg |
| .mdf | .mdb | .mpg | .msg | .myd | .myi | .nrg | .ora | .ost | .ova |
| .ovf | .php | .pmf | .png | .ppt | .pst | .pvi | .pyc | .rar | |
| .rtf | .sln | .sql | .tar | .txt | .tgz | .vbs | .vcb | .vdi | .vfd |
| .vmc | .vmx | .vsv | .xls | .xvd | .yml | .zip | .aspx | .avhd | .back |
| .conf | .disk | .djvu | .docx | .giff | .jpeg | .kdbx | .mpeg | .pptx | |
| .tiff | .vbox | .vmdk | .vmsd | .vsdx | . work | .xlsx | .yaml |
The ransomware employs AES to encrypt file contents and may use RSA to secure the encryption process.
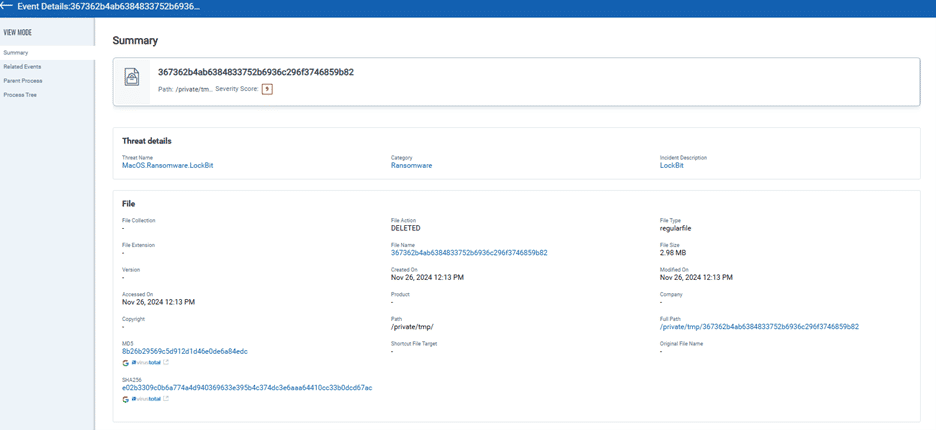
Unlike normal ransomware, the encrypted data is first written to a temporary file in /private/tmp/, which is then renamed to include the original file name, a unique identifier, and a .abcd extension, saving it in the original file’s directory.
Finally, the ransomware deletes the original file, ensuring that recovery is impossible without the decryption key.
Defacement
After completing the encryption process, NotLockBit actively alters the infected system’s desktop wallpaper. Utilizing the osascript command, it replaces the background with a custom LockBit ransom banner emphasizing the gravity of the threat.
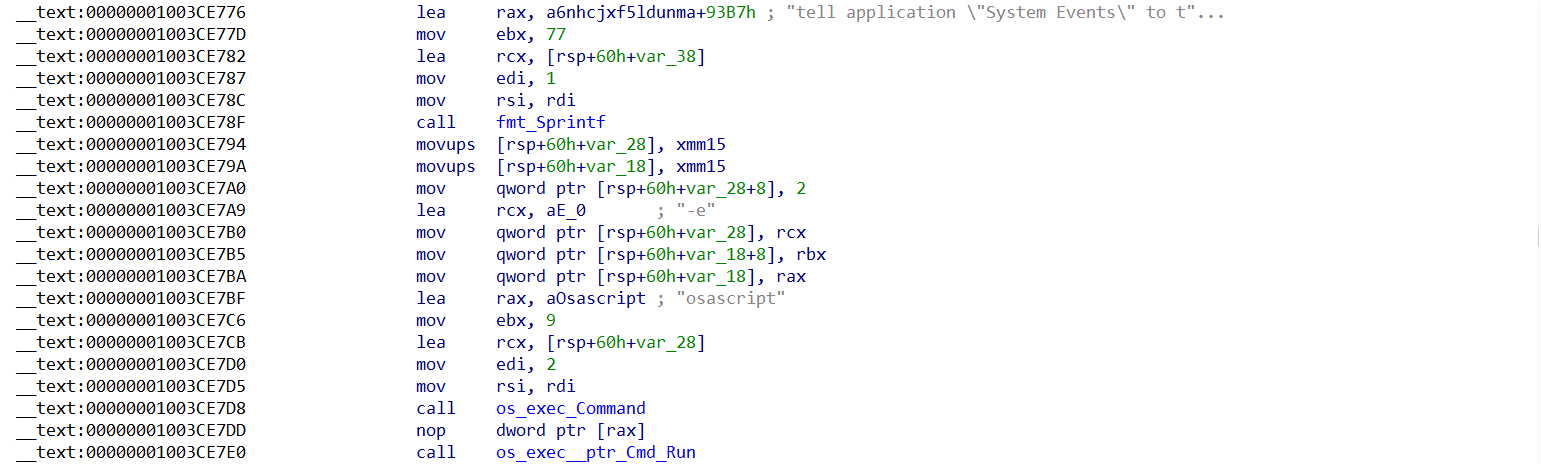
On macOS, the ransomware employs theosascript command to manipulate system settings, including changing the desktop wallpaper as part of its attack. The osascript command is a powerful tool for executing AppleScript code from the command line, allowing the ransomware to interact with system events. In this case, the ransomware uses the following script:
tell application “System Events” to tell every desktop to set picture to “%s”
This command instructs the System Events application to target every desktop instance on the system and set a new wallpaper image. The placeholder “%s” would be replaced with the path to the image the ransomware wants to display, which could be an image or a ransom note intended to inform the user of the attack. By altering the wallpaper, the ransomware increases its visibility to the victim, often as part of its psychological manipulation strategy.
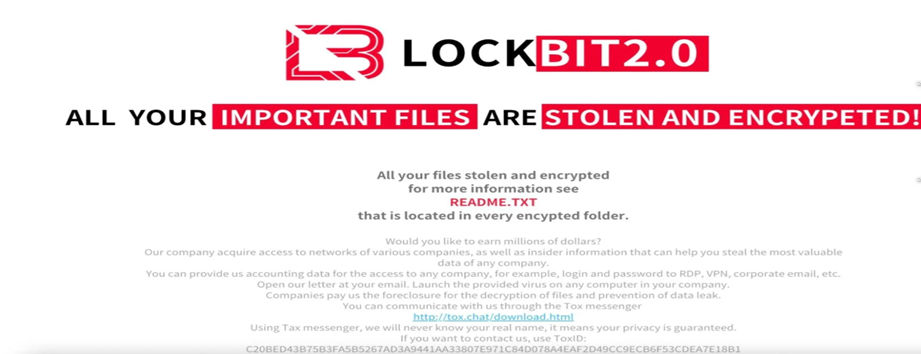
Self-Deletion
After the wallpaper is changed, the self-deletion activity is triggered and ultimately deletes the shadow copy.
Across analyzed samples, differences in binary data were observed: some samples retained visible function names, while others used obfuscated names, and a few were fully stripped. This variation highlights differing levels of obfuscation and compilation techniques across samples. In one of the samples, exfiltration was entirely omitted, leaving only encryption functionality, demonstrating a targeted and distinct approach.
Detections & Threat Hunting
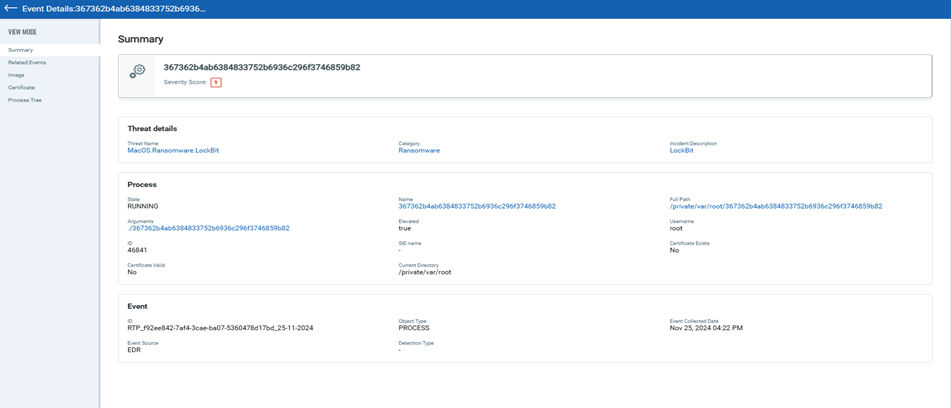
Qualys’s EDR & EPP offering provides comprehensive coverage against advanced threats. Notlockbit is detected and quarantined as soon as it is downloaded on the victim’s machine.
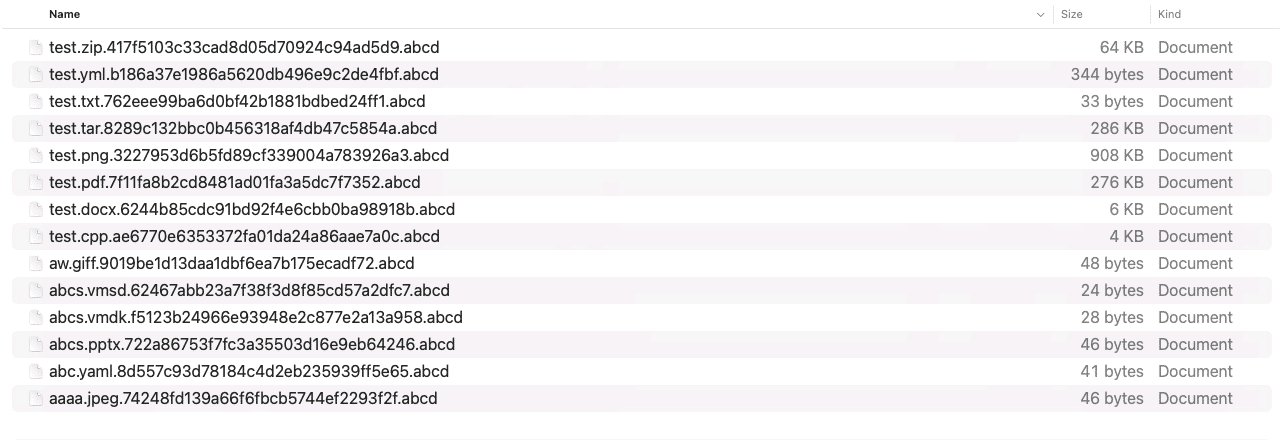
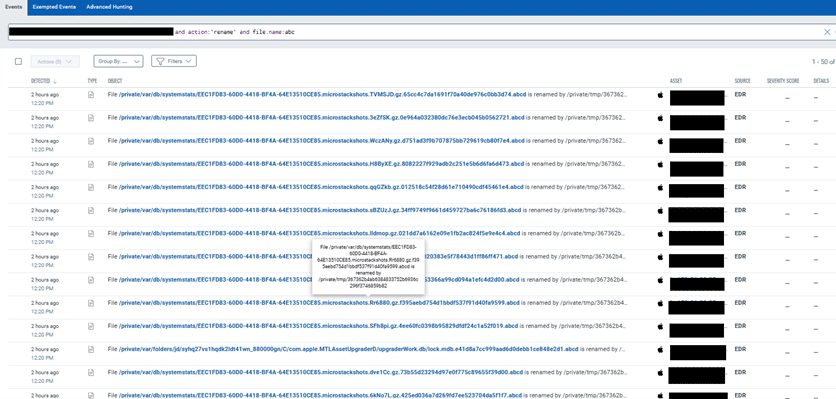
Following are the rename events generated for files encrypted with abcd extension.
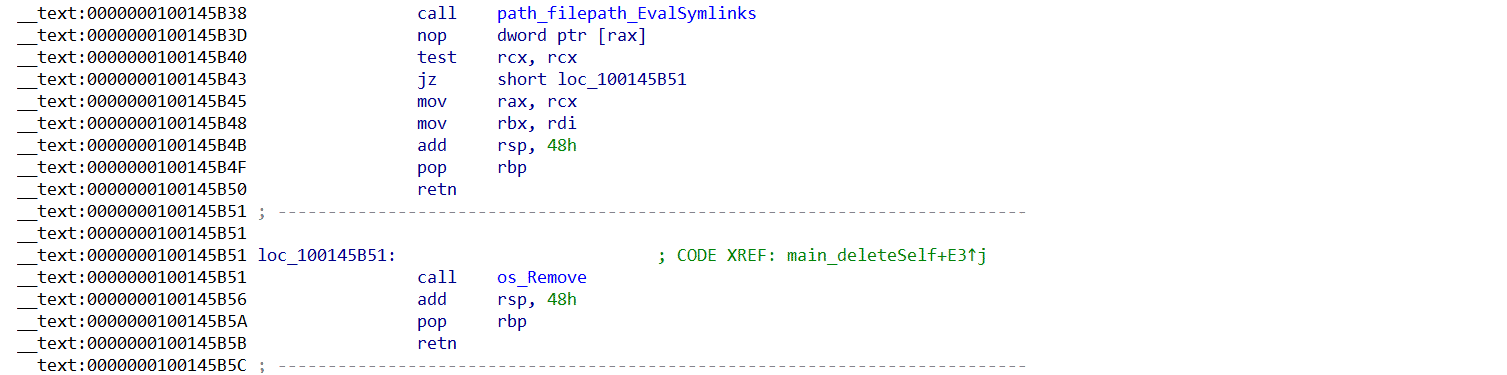
After completing its execution, the malware deletes itself through unlink activity. This is a self-removal mechanism designed to eliminate traces of its presence from the victim’s system.
Here are the Qualys Hunting queries that will allow you to investigate the threat.
| Description | Query |
| File created and detected by Threat intel | platform:mac and type:`file` and action:`created` and event.scoresource:Threat Intel |
| Files Dropped Activity | platform:mac and type:`file` and action:`created` and (file.name:encrypted_master_key.txt or file.name:readme.txt) and event.threatname:”Macos.Ransomware.Lockbit” |
| Unlink activity after execution | platform:mac and type:`file` and action:`deleted` and malware.category:ransomware |
| Files got renamed with abcd extension | platform:mac and type:`file` and file.extension:’abcd’ and action:`rename` |
| Osascript command used with specific arguments | platform:mac and process.name:osascript and process.arguments:-e and process.arguments:tell and process.arguments:application |
MITRE ATT&CK Techniques
| Operation | Techniques |
| Initial Access | Phishing (T1566) Exploit Public-Facing Applications (T1190) Drive-By Compromise (T1189) |
| Execution | Command and Scripting Interpreter (T1059) Automated System Information Discovery (T1083) |
| Persistence | Launch Daemons (T1543.003) Boot or Logon Autostart Execution: Login Items (T1547.015) |
| Privilege Escalation | Exploitation for Privilege Escalation (T1068) Sudo and Sudo Caching (T1548.003) |
| Defense Evasion | Obfuscated Files or Information (T1027) Timestomp (T1070.006) |
| Credential Access | Credential Dumping (T1003) |
| Exfiltration | Exfiltration Over C2 Channel (T1041) |
| Impact | Data Encrypted for Impact (T1486) |
Conclusion
The investigation into NotLockBit ransomware reveals an increasingly sophisticated threat that continues to evolve and maximize its impact. It employs a combination of targeted encryption strategies, deceptive methods like mimicking well-known ransomware families (e.g., LockBit), and self-deletion mechanisms to minimize forensic traces. Our analysis of its behavior demonstrated the use of AES-based encryption, strategic file targeting, and AWS S3 abuse for data exfiltration, highlighting its adaptability. These findings underscore the critical need for proactive endpoint detection, threat hunting, and incident response capabilities to combat such advanced ransomware campaigns effectively.
Indicators Of Compromise
| 14fe0071e76b23673569115042a961136ef057848ad44cf35d9f2ca86bd90d31 |
| 2e62c9850f331799f1e4893698295d0b069ab04529a6db1bfc4f193fe6aded2c |
| a28af0684456c26da769a2e0d29c5a726e86388901370ddf15bd3b355597d564 |
| aca17ec46730f5677d0d0a995b65504e97dce65da699fac1765db1933c97c7ec |
| e02b3309c0b6a774a4d940369633e395b4c374dc3e6aaa64410cc33b0dcd67ac |
Contributors
- Abhishek Barla, Threat Research Engineer, Qualys
Looks like pretty old technique the sample also is old, nothing novel i guess
If the AWS credentials are hardcoded and have been found during reverse engineering, isn’t it possible to use them in order to retrieve the master key and decrypt the files? Or is it used as a “one-way” upload to AWS? That part was unclear to me.