Securing Cloud Environments Against Potential Extortion Threats

Introduction
With the growing reliance on cloud infrastructure, organizations must be vigilant against potential extortion threats targeting misconfigurations and weak access controls. Unfortunately, extortion threats are a huge problem. According to the Verizon 2024 Data Breach Investigations Report (DBIR), “Roughly one-third of all breaches involved Ransomware or some other Extortion technique.” Hypothetically, an attack could leverage exposed files and credentials to infiltrate cloud environments, escalate privileges, and potentially exfiltrate sensitive data.
This blog will walk through how such an attack might occur, outline the MITRE ATT&CK tactics and techniques relevant to this scenario, and highlight critical best practices for securing cloud environments.
How an Extortion Attack Could Unfold
Extortion threats are characterized by the fact that the attacker is looking to use the exfiltrated data to extort money.
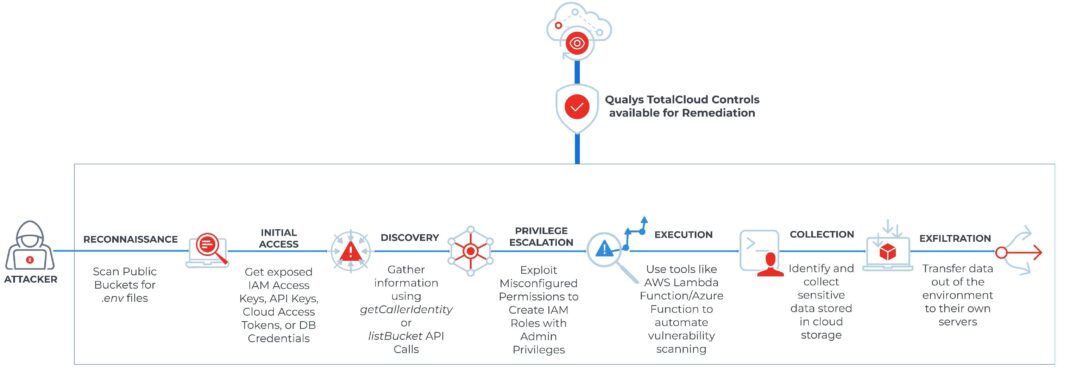
Here is how one could happen: Consider a scenario where attackers employ automated tools to scan for publicly exposed environment files (e.g., .env). These files often contain cloud access keys, database credentials, and API tokens that could enable attackers to compromise cloud environments and abuse access rights.
Attackers could leverage various MITRE ATT&CK tactics and techniques to achieve their objectives, creating a persistent foothold and escalating their privileges.
MITRE ATT&CK Framework: Key Tactics and Techniques
- Initial Access (T1078 – Valid Accounts): The attacker might gain access using compromised credentials found in exposed .env files or misconfigured public permissions.
- Discovery (T1580 – Cloud Infrastructure Discovery): After gaining access, attackers could use API calls like GetCallerIdentity or ListBuckets to gather information about the cloud environment’s structure and resources.
- Privilege Escalation (T1548 – Abuse Elevation Control Mechanism): If initial credentials are insufficient for their goals, attackers may exploit misconfigured permissions to create new roles with escalated privileges, allowing broader access within the cloud infrastructure.
- Persistence (T1136 – Create Account): Attackers may create long-lasting credentials or new accounts to establish persistence within the environment, allowing them to retain access for future malicious activities.
- Execution (T1072 – Software Deployment Tools): Using compromised permissions, attackers could deploy malicious functions, such as AWS Lambda functions, to automate scanning for additional vulnerabilities across other domains.
- Collection (T1530 – Data from Cloud Storage): Once they identify and access sensitive cloud resources, attackers could download files from cloud storage, exfiltrating sensitive data for ransom or further exploitation.
- Exfiltration (T1048 – Exfiltration Over Alternative Protocol): Attackers could transfer stolen data out of the environment using API calls or other tools, then leave ransom notes to demand payment in exchange for not leaking or selling the data.
The Role of Automation in Scaling Attacks
Automation would allow attackers to execute these tactics and techniques at scale, targeting hundreds or thousands of potential victims without manual intervention. Cloud-native tools and functions, like AWS Lambda, could automate scans across regions and domains, dramatically increasing the campaign’s reach.
Impact of a Potential Attack
An attack of this nature could have severe repercussions for organizations, including:
- Data Loss and Compliance Violations: Sensitive data exfiltration could lead to legal and regulatory consequences.
- Ransom Demands: Attackers might leave ransom notes, demanding payment to prevent the public release of stolen data.
- Credential Abuse: Exposed credentials could enable attackers to launch further phishing or malicious campaigns, amplifying the damage.
Key Security Measures to Mitigate Extortion Threats
To guard against potential extortion attacks, organizations should implement the following security practices:
1. Secure Environment Files: Protect files containing environment variables (.env) and other sensitive configurations by restricting access controls and avoiding public exposure.
Qualys Control IDs:
Control ID – 45: S3 Bucket Access Control List Grant Access to Everyone or Authenticated Users.
Control ID – 46: S3 Bucket Policy Grant Access to Everyone.
2. Rotate and Limit Credential Lifespan: Use temporary credentials that automatically expire to limit the impact if they are compromised. Regularly rotate credentials to reduce the risk of unauthorized access.
Qualys Control IDs:
Control ID – 2: Ensure console credentials unused for 45 days or greater are disabled.
Control ID – 4: Ensure access key1 is rotated every 90 days or less.
Control ID – 5: Ensure access key2 is rotated every 90 days or less.
Control ID – 14: Ensure no root user account access key exists.
3. Follow Least Privilege Principles: Ensure that IAM roles, users, and policies have only the minimum permissions required, reducing the risk of privilege escalation by attackers.
Qualys Control IDs:
Control ID – 17: Ensure IAM policies are attached only to groups or roles.
Control ID – 18: Eliminate use of the root user for administrative and daily tasks.
Control ID – 50: Ensure IAM policies that allow full *:* administrative privileges are not attached.
Control ID – 400: Ensure an IAM User does not have access to the console.
Control ID – 417: Ensure IAM policies that allow full administrative privileges are not created.
4. Monitor for Anomalies: Implement threat detection tools that alert security teams to unusual activity, such as unexpected API calls or data access attempts. Solutions like AWS GuardDuty or third-party monitoring tools can help detect these activities.
Qualys Control IDs:
Control ID – 19: Ensure CloudTrail is enabled in all regions.
Control ID – 387: Ensure GuardDuty is enabled to specific org/region.
5. Automate Response Actions: Use automated response mechanisms to disable compromised accounts, rotate exposed credentials, and restrict access to sensitive resources immediately when suspicious activity is detected.
For automating response actions, Qualys’ CDR tool helps detect known and unknown threats in real time with deep learning AI.
The Auto Remediation capability within Qualys TotalCloud allows detected security issues and misconfigurations in cloud environments to be fixed automatically. This provides a “one-click” remediation option to rapidly address vulnerabilities and compliance concerns without manual intervention, often through pre-defined workflows and integrations with cloud provider APIs.
Conclusion
By understanding the potential tactics and techniques used in cloud extortion campaigns, organizations can better defend against them. Following best practices, such as securing sensitive configuration files, applying least privilege access, and automating incident response, can significantly reduce the risk of falling victim to extortion and similar cloud-based attacks.
Ongoing vigilance and proactive measures are essential to protect cloud environments against evolving threats. Integrating these security practices will enhance your resilience to extortion and other cloud security risks.
Contributor
- Rahul Pareek, Security Analyst, Cloud, Qualys