Defense Lessons From the Black Basta Ransomware Playbook
Table of Contents
The cybersecurity world was rocked last week by a massive leak of Black Basta’s internal communications that emerged from the group’s chat logs. Triggered by internal conflicts and a retaliatory data dump following attacks on Russian banks, the exposed records offer a rare glimpse into Black Basta’s tactics, operations, and leadership.
We’ve analyzed these newly unveiled tactics, and in this blog, we equip security teams with clear, actionable insights. We aim to highlight the key lessons learned—like immediate patching, tighter access controls, and rapid incident response—and provide an urgent call to action. This practical guide aims to help organizations strengthen their defenses against evolving ransomware threats and mitigate potential damage.
Know Your Enemy’s Playbook
Understanding Black Basta’s attack tactics is critical for enterprises seeking to fortify their defenses. The Black Basta ransomware group leverages known vulnerabilities, misconfigurations, and insufficient security controls to breach systems. Their internal discussions reveal active targeting of exposed RDP servers, weak authentication mechanisms, and the deployment of malware droppers disguised as legitimate files.
Key attack vectors used by Black Basta include scanning for exposed RDP and VPN services—often relying on default VPN credentials or brute-forcing stolen credentials to gain initial access—and exploiting publicly known CVEs when systems remain unpatched. MSI and VBS-based malware droppers are frequently utilized to deliver malicious payloads, with Rundll32.exe leveraged to execute harmful DLLs. Credential harvesting and privilege escalation are also central to these tactics.
Patch Now: Top 20 CVEs Actively Exploited by Black Basta Ransomware Gangs
Black Basta Ransomware gangs are relentless, and leaked conversations reveal their playbook: a hit list of weaponized vulnerabilities they exploit against enterprise networks. For IT security professionals and practitioners, this isn’t just a list—it’s a call to action.
Below is a practical table featuring the Top 20 CVEs that demand immediate attention. These are the flaws ransomware crews are buzzing about, and your organization could be next if these aren’t patched yesterday. Qualys is proud to have coverage for all 62 CVEs mentioned in the leaked documents, the full list of CVEs mentioned can be found in Appendix A.
| # | Name | CVE | Product | QVS | QID |
|---|---|---|---|---|---|
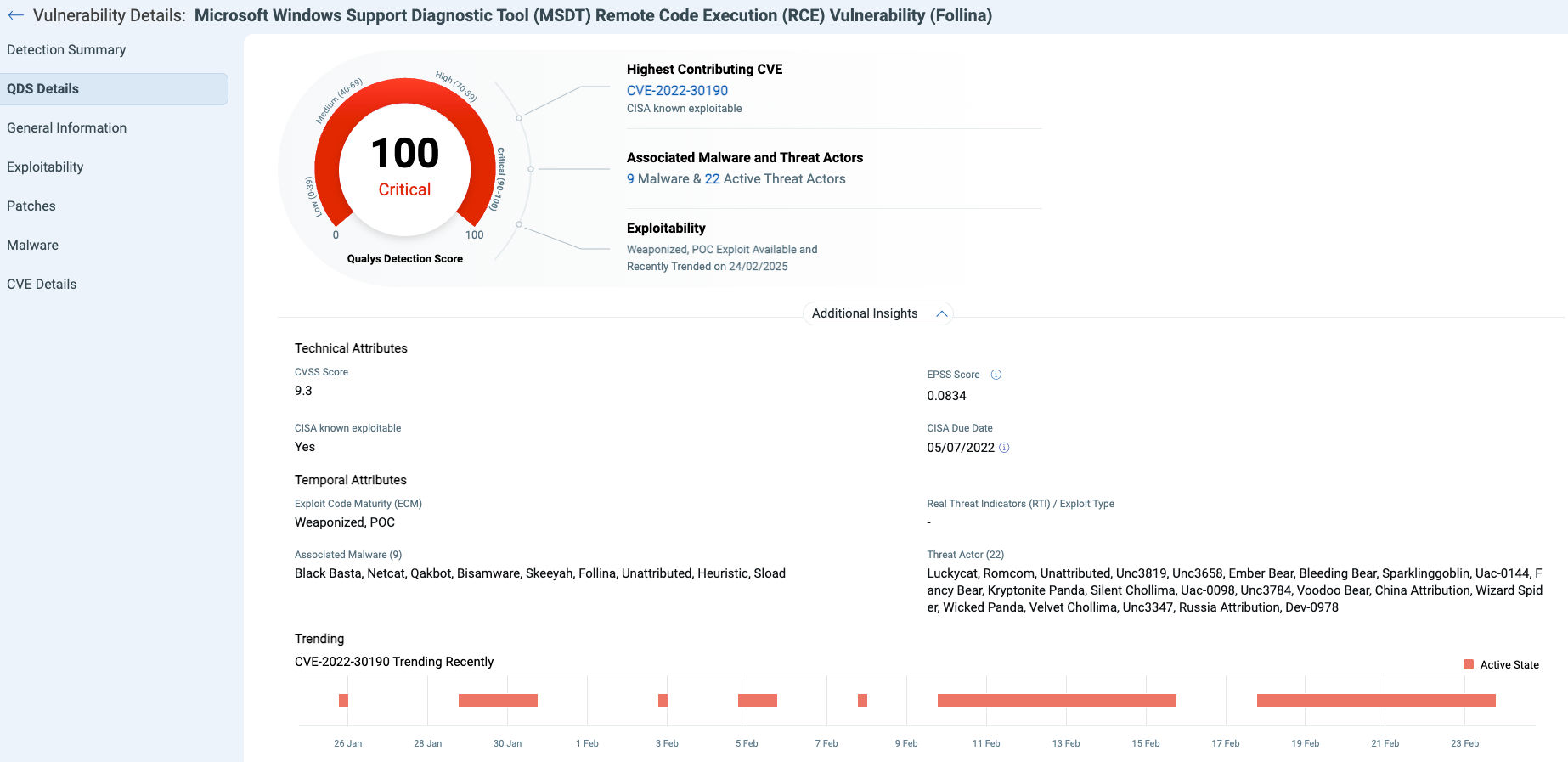
| 1 | Follina | CVE-2022-30190 | Microsoft Office | 100 | 91909 |
| 2 | Log4Shell | CVE-2021-44228 | Apache Log4j (Java apps) | 100 | 376157, 730297, 178935, etc |
| 3 | Spring4Shell | CVE-2022-22965 | Spring Framework (Java) | 100 | 376506, 984158, 376514, etc |
| 4 | F5 BIG-IP | CVE-2022-1388 | F5 BIG-IP load balancers | 100 | 376577, 730489 |
| 5 | Chrome Zero-Day | CVE-2022-0609 | Google Chrome | 95 | 376416, 690793, 179083, etc |
| 6 | Office | CVE-2017-11882 | Microsoft Office | 100 | 110308 |
| 7 | ProxyNotShell | CVE-2022-41082/41040 | Microsoft Exchange Server | 95 | 50122, 730621 |
| 8 | Zimbra | CVE-2022-27925/41352 | Zimbra Collaboration Suite | 100 | 376769, 378336 |
| 9 | Atlassian Confluence RCE | CVE-2022-26134 | Confluence Server | 100 | 730514, 376657 |
| 10 | Zyxel RCE | CVE-2022-30525 | Zyxel Firewalls | 96 | 730491 |
| 11 | FortiGate SSL VPN RCE | CVE-2024-21762 | Fortinet SSL VPN | 95 | 44170 |
| 12 | GlobalProtect RCE | CVE-2024-3400 | Palo Alto Networks PAN-OS | 100 | 731378, 731456, 731460 |
| 13 | Outlook | *CVE-2023-23397 | Microsoft Outlook | 92 | 110428 |
| 14 | Windows Sandbox Escape | *CVE-2023-28252 | Microsoft Windows | 95 | 92005, 92003 |
| 15 | Juniper SRX Firewall RCE | *CVE-2023-36844-47 | Juniper SRX firewalls | 95 | 44099 |
| 16 | Linux LPE | CVE-2024-1086 | Linux kernels | 95 | 755747, 755751, 755750 |
| 17 | ScreenConnect RCE | CVE-2024-1709 | ConnectWise ScreenConnect | 100 | 379390 |
| 18 | Ivanti SSL-VPN Pre-Auth RCE | *CVE-2024-21887/21893 | Ivanti Connect Secure | 100 | 731074 |
| 19 | FortiSIEM RCE | CVE-2024-23108/23109 | Fortinet FortiSIEM | 72 | 379902 |
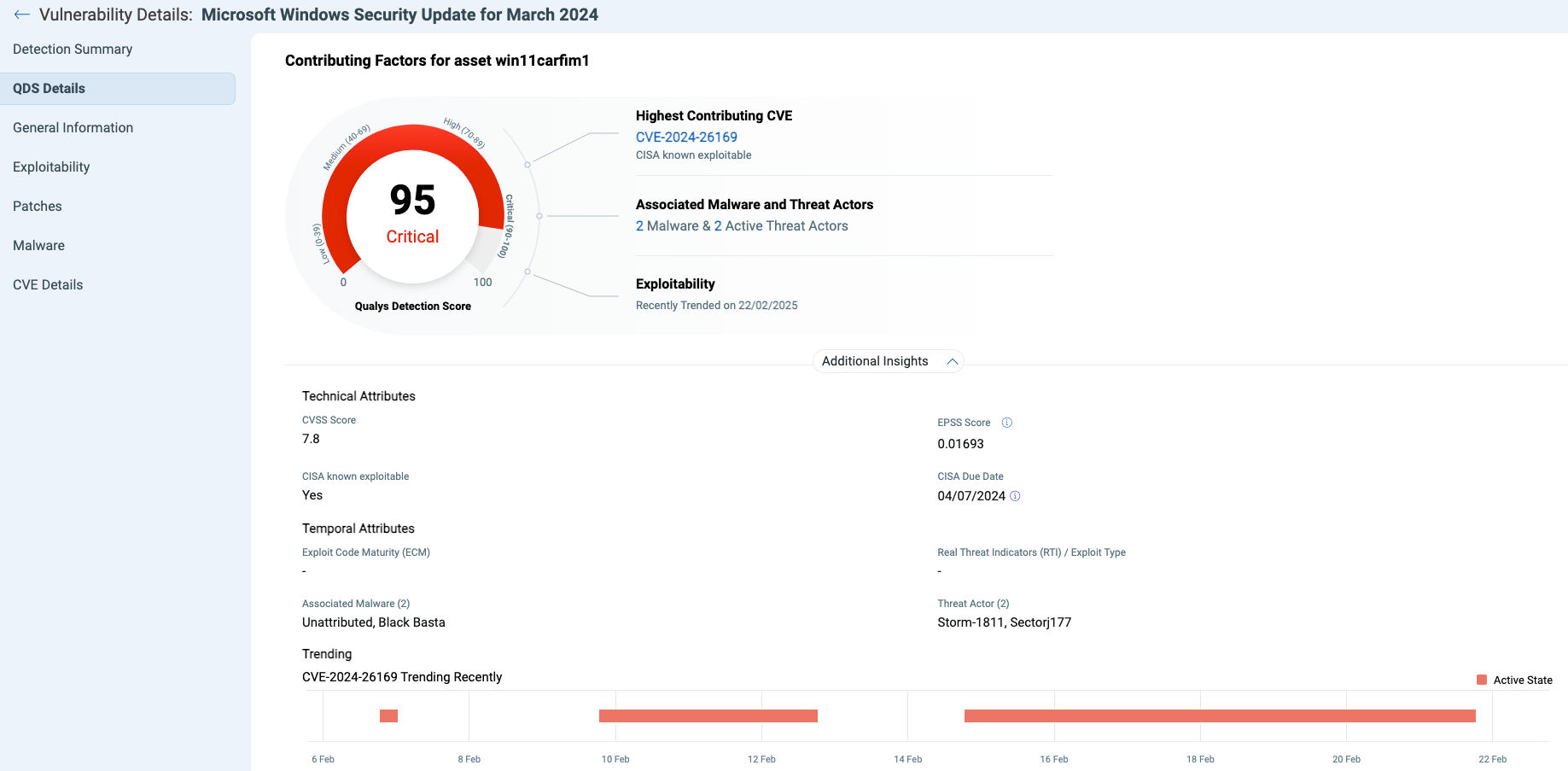
| 20 | Windows LPE | CVE-2024-26169 | Microsoft Windows | 95 | 92121 |
Note: CVEs marked with an asterisk (*) are not explicitly mentioned; however, based on their characteristics and the details discussed in the leaked data, they have been mapped to the corresponding CVEs.
Security teams must immediately patch the above-mentioned vulnerabilities that are actively exploited in ransomware campaigns.
Talk to Qualys Experts to see how you can implement this guidance today.
Most Wanted: Critical Misconfigurations to Fix Immediately
The table below highlights the top misconfigurations routinely exploited by Black Basta ransomware operators—real-world vulnerabilities integral to their attack workflow. Because attackers are actively scanning your perimeter for these weaknesses, treat them as “Patch Now” issues to stay one step ahead of ransomware threats.
| # | Misconfiguration | Product |
|---|---|---|
| 1 | SMBv1 Enabled on Legacy Systems | Windows Servers |
| 2 | Default Credentials | Servers, Routers, VPNs, IoT |
| 3 | Weak VPN Configurations | Cisco, Fortinet, GlobalProtect |
| 4 | Exposed RDP Without Filtering | Windows Servers |
| 5 | Public S3 Buckets | AWS S3 Storage |
| 6 | Open Jenkins Servers | CI/CD Pipelines |
| 7 | Unpatched Cisco ASA Firewalls | Cisco ASA Devices |
| 8 | Weak MSSQL Authentication | Microsoft SQL Servers |
| 9 | Citrix Netscaler Misconfigs | Citrix ADC/NetScaler |
| 10 | Shadow IT/Subdomains | Orphaned DNS Records |
The Initial Access Problem
Black Basta employs a layered approach involving credential theft, service exploitation (such as RDP brute force), social engineering, and persistence. They obtain credentials through phishing, supply chain compromises, dark web purchases, and by locating exposed services using tools like Shodan or Fofa (automated scanners), followed by brute-force attacks on accessible login portals (e.g., RDP). Internal communications confirm multiple tactics for establishing an initial foothold. This layered approach includes:
- Exploitation of Exposed Services & Misconfigurations: They aggressively search for internet-facing vulnerabilities, particularly in Jenkins CI/CD instances, VMware ESXi hosts, Citrix gateways, and VPNs with weak credentials.
- Abuse of Third-Party Services for Payload Hosting: To evade detection, they rely on legitimate file-sharing platforms like transfer.sh, temp.sh, and send.vis.ee for hosting malicious payloads, reducing the need for custom infrastructure.
- Data Exfiltration, Social Engineering, and Voice Phishing: Before deploying ransomware, they archive and extract entire file directories. Internal chats mention targeting legal and financial documents and using custom-built tool to automate data extraction. Beyond email phishing, Black Basta members impersonate IT support staff via phone calls, tricking employees into revealing credentials.
Attackers Move Fast
Ransomware groups are no longer taking their time once they breach an organization’s network. Recently leaked data from Black Basta shows they’re moving from initial access to network-wide compromise within hours—sometimes even minutes.
Ransomware operators are accelerating their attacks, leaving organizations with little time to respond. To prevent widespread damage, it’s critical to proactively detect known exploited vulnerabilities and minimize the attack surface. The longer you wait, the more likely attackers will exfiltrate data and lock down your environment. In many cases, automated scripts run post-exploitation tasks such as dumping credentials, disabling security tools, and deploying ransomware.
How Qualys Can Help
The recent leak of the Black Basta ransomware group’s internal chat logs has provided unprecedented insights into its operations, tools, and tactics. Qualys’ product suite aligns perfectly with the critical recommendations we’ve highlighted, offering a unified approach to cybersecurity.
See instances of the Black Basta’s top exploited vulnerabilities in your environment. Qualys VMDR users, download our custom dashboard today.
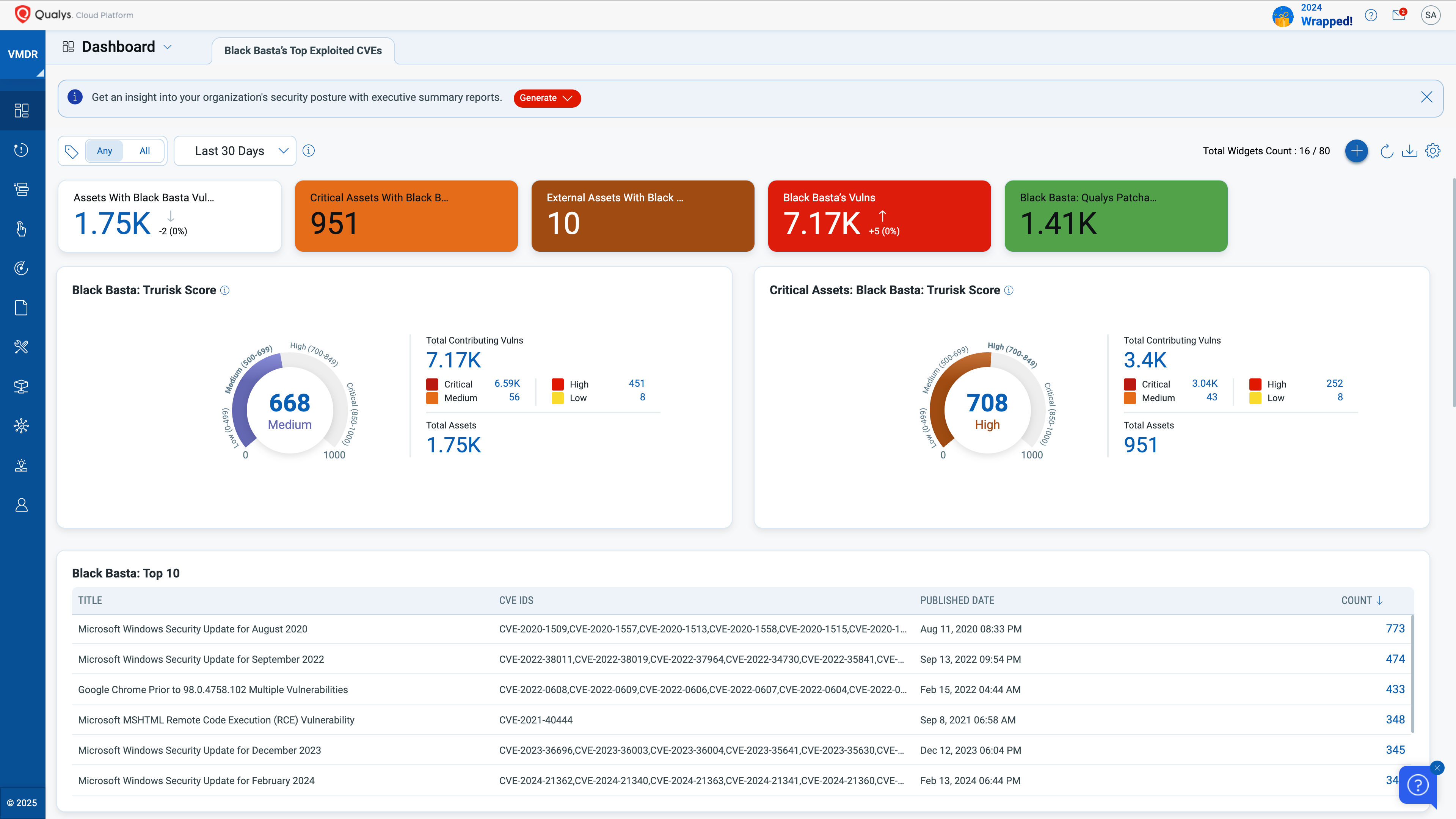
The CyberSecurity Asset Management (CSAM) solution provides complete visibility of assets, which is in line with the comprehensive asset discovery needed.
First find the scope of assets that need to be investigated. For example, to find all internet-facing assets with VPN or RDP software, use the following QQL: ” software:(name:”vpn” or name:”remote”) and tags.name:EASM ”
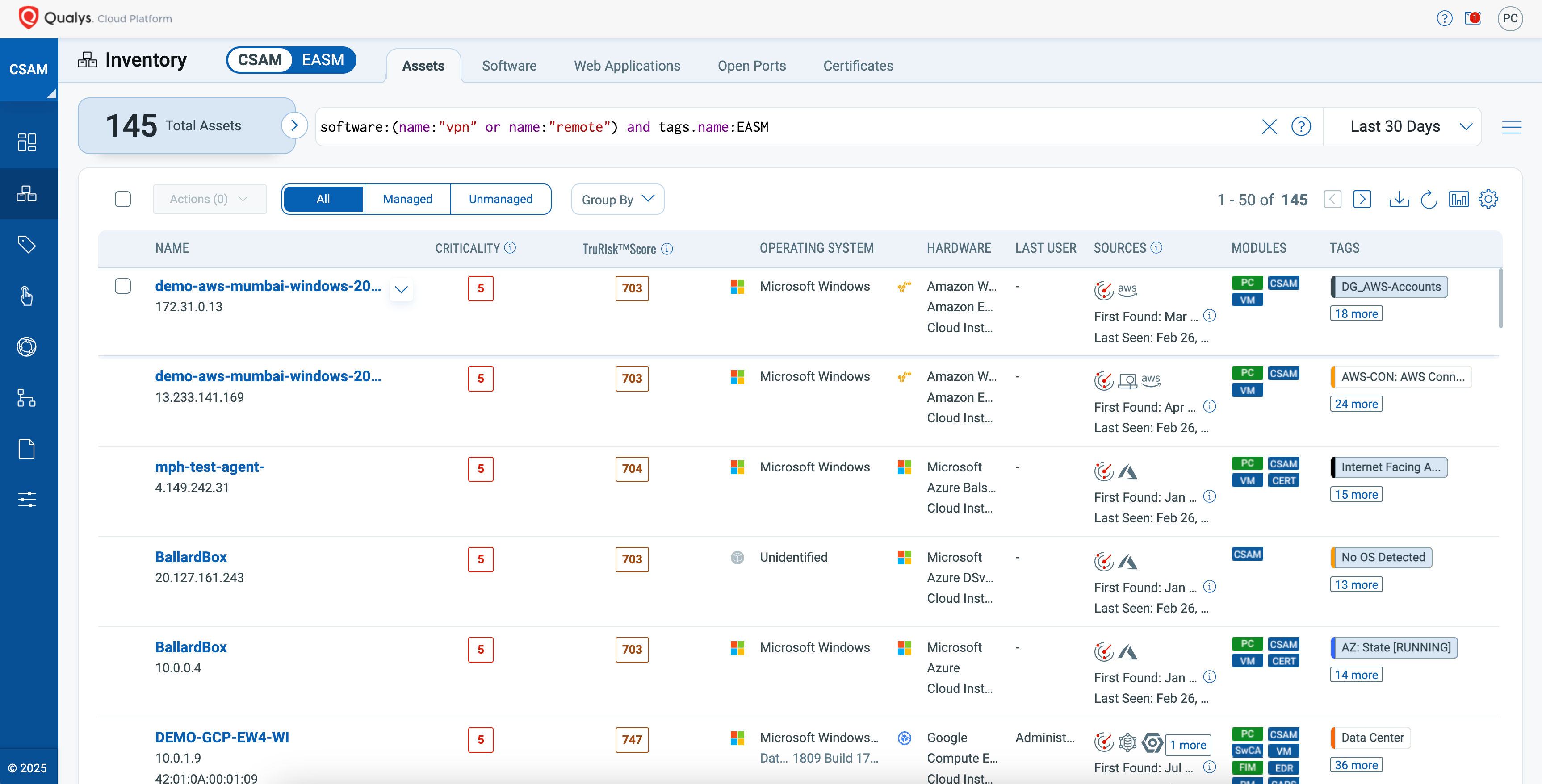
In addition, Qualys Patch Management delivers an advanced automated solution for timely software updates. Meanwhile, Qualys VMDR streamlines discovering, assessing, and prioritizing vulnerabilities. With its TruRisk scoring, the platform takes vulnerability management to the next level by incorporating risk-based prioritization, leading to more effective cybersecurity measures.
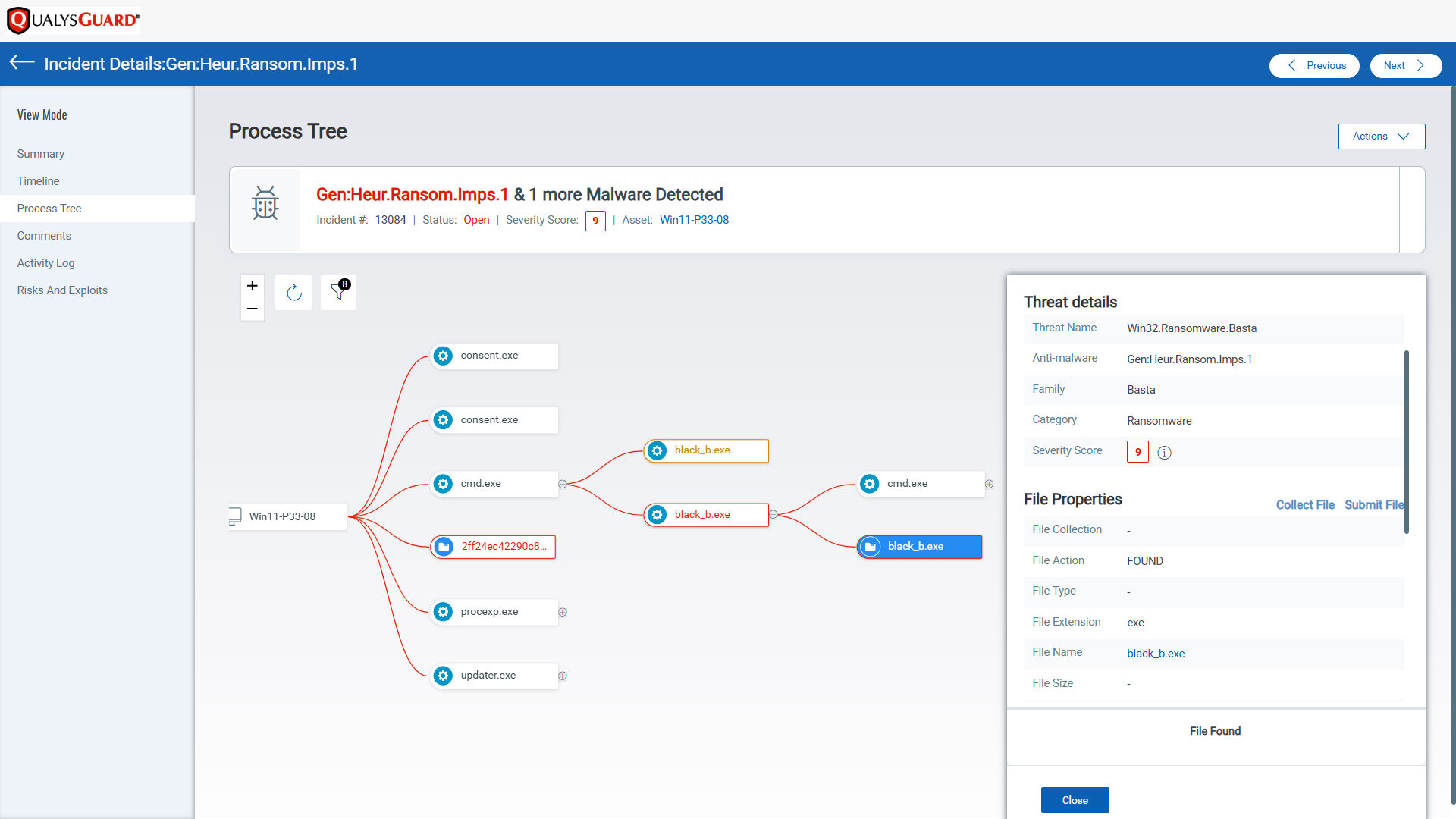
Our Endpoint Detection & Response solution is equipped to detect and mitigate the tactics, techniques, and procedures (TTPs) employed by Black Basta. This includes indicators of compromise (IOCs) and indicators of attack (IOAs) derived from the leaked logs, such as IP addresses, domains, and malware hashes used by the group.
Our dedicated threat research team actively analyzes emerging data, including the leaked Black Basta logs. This allows us to identify novel IOCs and adapt our detection mechanisms in real time. For instance, details from the logs about vulnerabilities exploited in Citrix, Ivanti, and Fortinet products have been integrated into our detection capabilities. Using our proprietary AI models, we continuously scan for credible and trending threat intelligence across the web. These models automatically craft detection logic for emerging threats like Black Basta’s operations.
Talk to Qualys Experts to see how you can implement this guidance today.
VMDR QQL for Black Basta
Qualys Query Language (QQL) is a powerful search tool within VMDR (Vulnerability Management, Detection, and Response) that helps security teams quickly identify and prioritize vulnerabilities. With QQL for Black Basta, you can instantly query your environment to detect assets exposed to ransomware-targeted CVEs, misconfigurations, and security gaps. This enables faster remediation and risk-based prioritization, helping organizations stay ahead of evolving threats like Black Basta.
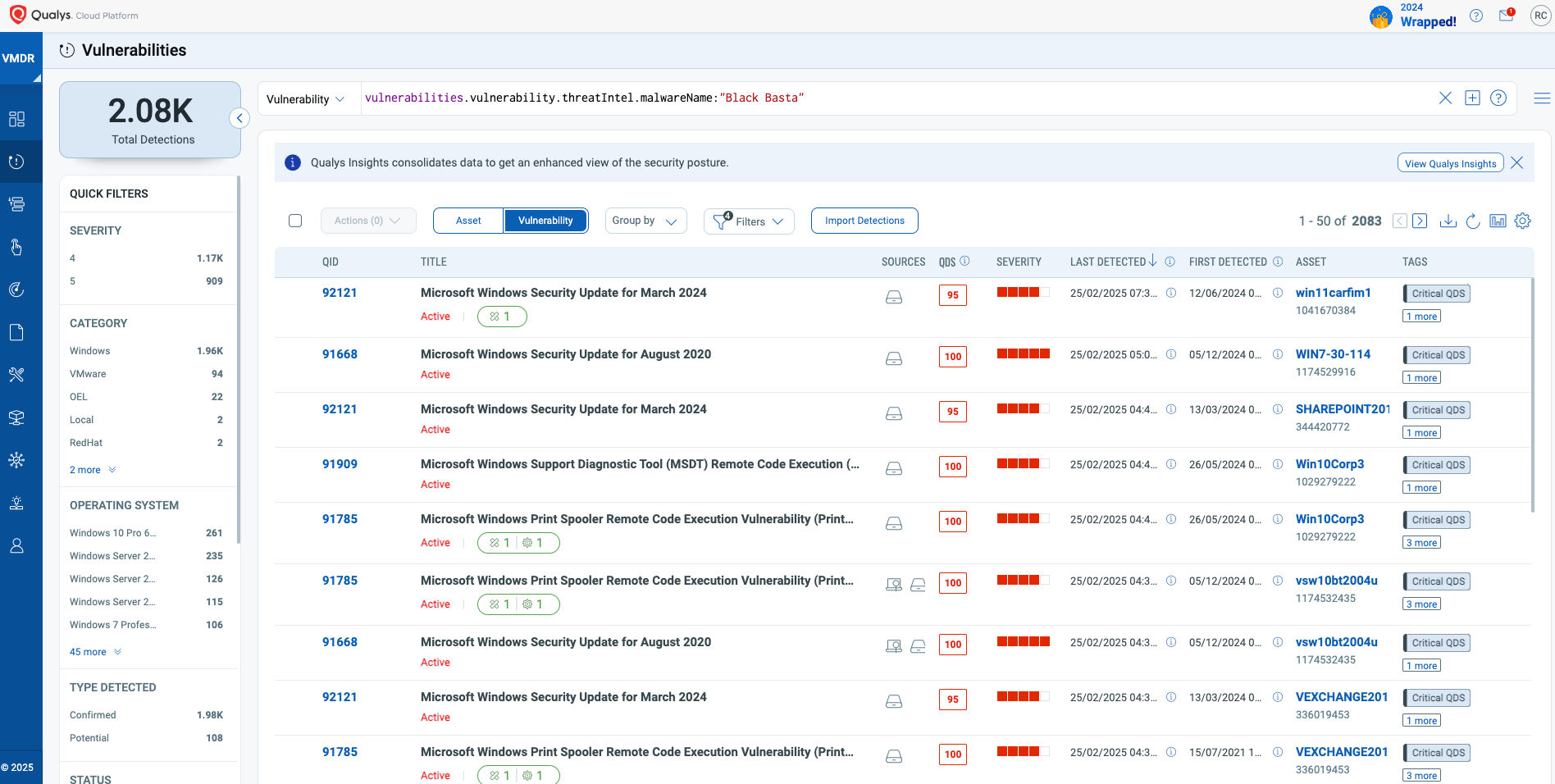
vulnerabilities.vulnerability.threatIntel.malwareName:"Black Basta"
Appendix A:
CVE-2017-11882, CVE-2021-26855, CVE-2021-28482, CVE-2021-40444, CVE-2021-42278, CVE-2021-42287, CVE-2021-42321, CVE-2021-44228, CVE-2022-0609, CVE-2022-1388, CVE-2022-22965, CVE-2022-26134, CVE-2022-27925, CVE-2022-30190, CVE-2022-30525, CVE-2022-37042, CVE-2022-37969, CVE-2022-41040, CVE-2022-41082, CVE-2022-41352, CVE-2023-20198, CVE-2023-21716, CVE-2023-22515, CVE-2023-29357, CVE-2023-35628, CVE-2023-36394, CVE-2023-36745, CVE-2023-36845, CVE-2023-36874, CVE-2023-36884, CVE-2023-38831, CVE-2023-42115, CVE-2023-42793, CVE-2023-4966, CVE-2023-6875, CVE-2023-7027, CVE-2023-7028, CVE-2024-1086, CVE-2024-1709, CVE-2024-21338, CVE-2024-21378, CVE-2024-21413, CVE-2024-21683, CVE-2024-21762, CVE-2024-23108, CVE-2024-23109, CVE-2024-23113, CVE-2024-23897, CVE-2024-24919, CVE-2024-25600, CVE-2024-26169, CVE-2024-27198, CVE-2024-3400, CVE-2017-5753, CVE-2017-5754, CVE-2020-1472, CVE-2023-23397, CVE-2023-3466, CVE-2023-3467, CVE-2023-3519, CVE-2023-36844, CVE-2024-1708