Microsoft and Adobe Patch Tuesday, March 2025 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for March 2025
- Adobe Patches for March 2025
- Zero-day Vulnerabilities Patched in March Patch Tuesday Edition
- Critical Severity Vulnerabilities Patched in March Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities inVulnerability Management, Detection & Response (VMDR)
- Rapid Response withPatch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- Risk Reduction via TruRisk Eliminate
- Qualys Monthly Webinar Series
March 2025 Patch Tuesday is here, and Microsoft has rolled out critical security updates that address multiple vulnerabilities across its product suite. Here’s a quick breakdown of what you need to know.
Microsoft Patch Tuesday for March 2025
Microsoft Patch’s Tuesday, March 2025 edition addressed 67 vulnerabilities, including six critical and 51 important severity vulnerabilities. In this month’s updates, Microsoft has addressed seven zero-day vulnerabilities, six of which have been actively exploited in attacks and one publicly disclosed.
Microsoft has addressed 10 vulnerabilities in Microsoft Edge (Chromium-based) in this month’s updates.
Microsoft Patch Tuesday, March edition includes updates for vulnerabilities in Microsoft Streaming Service, Windows Hyper-V, Microsoft Windows, DNS Server, Visual Studio, Windows Routing and Remote Access Service (RRAS), Windows NTLM, Windows Common Log File System Driver, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, and Remote Code Execution (RCE).
The March 2025 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 3 | Important: 3 |
| Denial of Service Vulnerability | 1 | Important: 1 |
| Elevation of Privilege Vulnerability | 23 | Important: 23 |
| Information Disclosure Vulnerability | 4 | Important: 4 |
| Remote Code Execution Vulnerability | 23 | Critical: 6 Important: 17 |
| Security Feature Bypass | 3 | Important: 3 |
Adobe Patches for March 2025
Adobe has released seven security advisories to address 38 vulnerabilities in Adobe Acrobat Reader, Substance 3D Sampler, Adobe Illustrator, Substance 3D Painter, Adobe InDesign, Substance 3D Modeler, and Substance 3D Designer. 28 of these vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to memory leak and arbitrary code execution.
Zero-day Vulnerabilities Patched in March Patch Tuesday Edition
CVE-2025-24983: Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability
The Windows Win32 Kernel Subsystem is a core component within the Windows operating system that bridges standard Windows applications (using the Win32 API) and the underlying Windows kernel.
The use after free vulnerability in Windows Win32 Kernel Subsystem may allow an authorized attacker to elevate privileges locally. An attacker may exploit the vulnerability to gain SYSTEM privileges.
CISA added the CVE-2025-24983 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before April 1, 2025.
CVE-2025-24984: Windows NTFS Information Disclosure Vulnerability
Windows NTFS (New Technology File System) is a file system that stores and organizes files on Windows operating systems. It’s the default file system for Windows NT 3.1 and later versions. NTFS offers encryption, file and folder permissions, and disk quotas.
An attacker may exploit the vulnerability to potentially read portions of heap memory. An attacker must have physical access to the target computer to plug in a malicious USB drive.
CISA added the CVE-2025-24984 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before April 1, 2025.
CVE-2025-24985: Windows Fast FAT File System Driver Remote Code Execution Vulnerability
A Windows Fast FAT File System Driver is a software component within the Windows operating system that manages file operations on a storage device formatted with the Fast FAT file system.
The integer overflow or wraparound flaw in Windows Fast FAT Driver may allow an unauthorized attacker to execute code. An attacker may trick a local user on a vulnerable system into mounting a specially crafted VHD to trigger the vulnerability.
CISA added the CVE-2025-24985 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before April 1, 2025.
CVE-2025-24991: Windows NTFS Information Disclosure Vulnerability
Inserting sensitive information into a log file in Windows NTFS may allow an authorized attacker to disclose information locally. An attacker may exploit the vulnerability to read portions of heap memory potentially.
CISA added the CVE-2025-24991 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before April 1, 2025.
CVE-2025-24993: Windows NTFS Remote Code Execution Vulnerability
The heap-based buffer overflow vulnerability in Windows NTFS may allow an authorized attacker to execute code locally. An attacker may trick a local user on a vulnerable system into mounting a specially crafted VHD to trigger the vulnerability.
CISA added the CVE-2025-24993 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before April 1, 2025.
CVE-2025-26630: Microsoft Access Remote Code Execution Vulnerability
Microsoft Access is a database management system (DBMS) that helps users create and manage databases. The system uses Visual Basic for Applications to automate business processes.
The use after free flaw in Microsoft Office Access allows an unauthorized attacker to execute code locally. An attacker must trick a user into running a malicious file to successfully exploit the vulnerability.
CVE-2025-26633: Microsoft Management Console Security Feature Bypass Vulnerability
Improper neutralization flaw in Microsoft Management Console may allow an unauthorized attacker to bypass a security feature.
CISA added the CVE-2025-26633 to its Known Exploited Vulnerabilities Catalog and requested users to patch it before April 1, 2025.
Critical Severity Vulnerabilities Patched in March Patch Tuesday Edition
CVE-2025-24035 & CVE-2025-24045: Windows Remote Desktop Services Remote Code Execution Vulnerability
Windows Remote Desktop Services (RDS) is a Microsoft feature that allows users to remotely access and use Windows applications and desktops from various devices over a network connection.
The sensitive data storage in improperly locked memory flaw in Windows Remote Desktop Services allows an unauthorized attacker to execute code over a network. An attacker must win a race condition to exploit the vulnerability.
CVE-2025-24057: Microsoft Office Remote Code Execution Vulnerability
The heap-based buffer overflow flaw in Microsoft Office may allow an unauthorized attacker to execute code remotely.
CVE-2025-24064: Windows Domain Name Service Remote Code Execution Vulnerability
Windows Domain Name Service is the implementation of the Domain Name System (DNS) within the Windows operating system. The service allows users to access websites and network devices using easy-to-remember domain names instead of complex IP addresses.
The use after free flaw in the DNS Server may allow an unauthorized attacker to execute code over a network. An attacker must win a race condition to exploit the vulnerability.
CVE-2025-24084: Windows Subsystem for Linux (WSL2) Kernel Remote Code Execution Vulnerability
The untrusted pointer dereference in Windows Subsystem for Linux may allow an unauthorized attacker to execute code locally.
CVE-2025-26645: Remote Desktop Client Remote Code Execution Vulnerability
Relative path traversal in Remote Desktop Client allows an unauthorized attacker to execute code over a network.
Other Microsoft Vulnerability Highlights
- CVE-2025-24044 is an elevation of privilege vulnerability in the Windows Win32 Kernel Subsystem. Upon successful exploitation of the vulnerability, an attacker could gain SYSTEM privileges.
- CVE-2025-21180 is a remote code execution vulnerability in the Windows exFAT File System. This heap-based buffer overflow flaw in Windows exFAT File System could allow an unauthorized attacker to execute code.
- CVE-2025-24995 is an elevation of privilege vulnerability in Kernel Streaming WOW Thunk Service Driver. Upon successful exploitation of the vulnerability, an attacker could gain SYSTEM privileges.
- CVE-2025-21247 is a security feature bypass vulnerability in MapUrlToZone. The improper resolution of path equivalence flaw could allow an unauthorized attacker to bypass a security feature over a network.
- CVE-2025-24061 is a security feature bypass vulnerability in Windows Mark of the Web. An attacker may exploit the vulnerability to bypass the SmartScreen user experience.
- CVE-2025-24066 & CVE-2025-24067 are the elevation of privilege vulnerabilities in the Kernel Streaming Service Driver. The use after free flaw in Microsoft Streaming Service could allow an authorized attacker to gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows exFAT File System, Azure Agent Installer, Windows MapUrlToZone, Windows Remote Desktop Services, .NET, Windows Win32 Kernel Subsystem, Azure CLI, Windows USB Video Driver, Windows Telephony Server, Microsoft Office, Windows Mark of the Web (MOTW), DNS Server, Windows Kernel-Mode Drivers, ASP.NET Core & Visual Studio, Windows File Explorer, Microsoft Local Security Authority Server (lsasrv), Microsoft Office Excel, Windows Cross Device Service, Microsoft Office Word, Windows Subsystem for Linux, Windows NTFS, Windows Fast FAT Driver, Azure PromptFlow, Kernel Streaming WOW Thunk Service Driver, Windows Kernel Memory, Visual Studio, Microsoft Windows, Azure Arc, Microsoft Office Access, Visual Studio Code, Microsoft Management Console, Microsoft Edge (Chromium-based), and Remote Desktop Client.
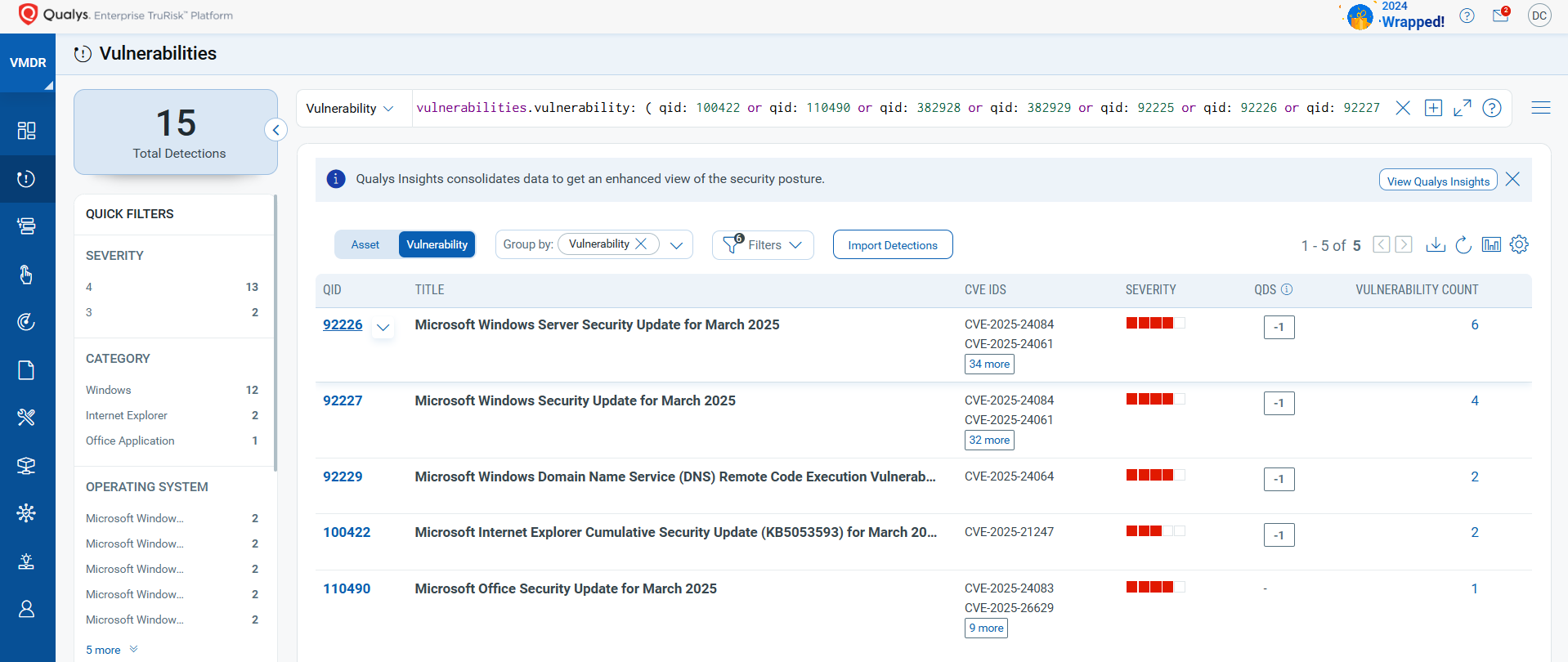
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 100422 or qid: 110490 or qid: 382928 or qid: 382929 or qid: 92225 or qid: 92226 or qid: 92227 or qid: 92228 or qid: 92229 or qid: 92230 or qid: 92232 )
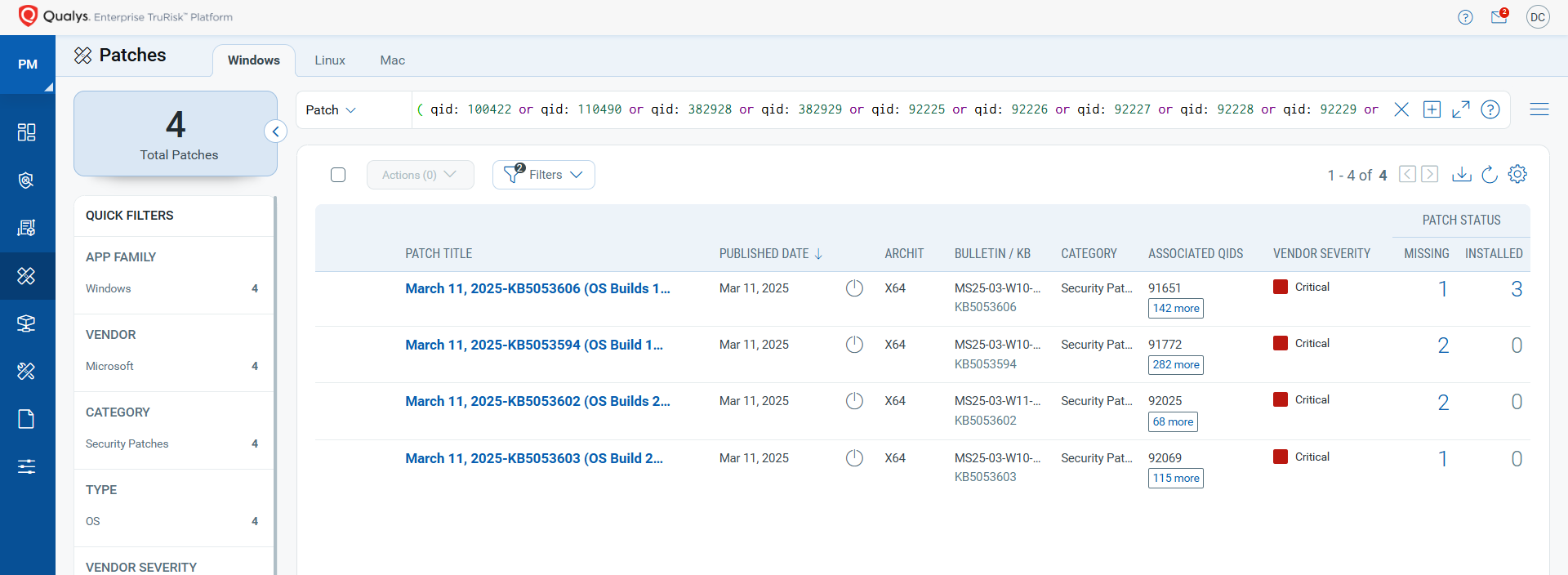
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 100422 or qid: 110490 or qid: 382928 or qid: 382929 or qid: 92225 or qid: 92226 or qid: 92227 or qid: 92228 or qid: 92229 or qid: 92230 or qid: 92232 )
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/Patch) cannot be done now. These security controls are not recommended by industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
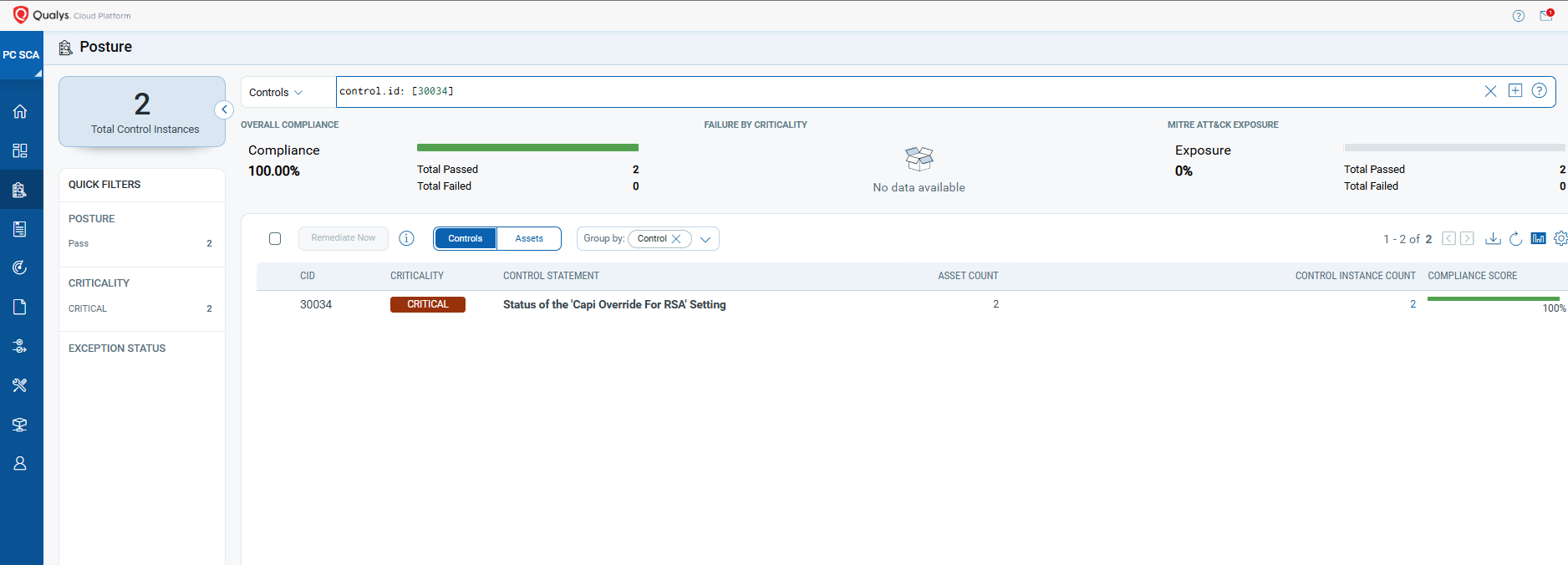
The following Qualys Policy Compliance Control IDs (CIDs), and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2024-30098: Windows Cryptographic Services Security Feature Bypass Vulnerability
This vulnerability has a CVSS: 3.1 7.5 / 6.5
Policy Compliance Control IDs (CIDs):
• 30034 Status of the ‘Capi Override For RSA’ Setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [30034]
Risk Reduction via TruRisk Eliminate
With Qualys TruRisk Eliminate customers can install innovative patchless mitigation strategies for the following vulnerabilities. Some of these do not require a system reboot and can be used as a stop-gap while your systems are being patched for these vulnerabilities. More information about Qualys TruRisk Eliminate can be found here – https://www.qualys.com/apps/trurisk-eliminate/
- CVE-2025-24045 – Windows Remote Desktop Services Remote Code Execution Vulnerability
- CVE-2025-24035 – Windows Remote Desktop Services Remote Code Execution Vulnerability
- CVE-2025-24084 – Windows Subsystem for Linux (WSL2) Kernel Remote Code Execution Vulnerability
- CVE-2025-24055 – Windows USB Video Class System Driver Information Disclosure Vulnerability
- CVE-2025-24988 – Windows USB Video Class System Driver Elevation of Privilege Vulnerability
- CVE-2025-24054 – NTLM Hash Disclosure Spoofing Vulnerability
- CVE-2025-24996 – NTLM Hash Disclosure Spoofing Vulnerability
- CVE-2025-24045 – Windows Remote Desktop Services Remote Code Execution Vulnerability
- CVE-2025-24056 – Windows Telephony Service Remote Code Execution Vulnerability
- CVE-2025-24987 – Windows USB Video Class System Driver Elevation of Privilege Vulnerability
For some of the CVEs mentioned above, we mitigate risks by disabling RemoteAccess, TapiSrv services. Additional mitigation strategies that involving NTLM hashes and non-essential device derives are also enabled to provide optimal protection against the above mentioned vulnerabilities.
The next Patch Tuesday falls on April 8, and we will be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to ‘This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series
The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches