Microsoft and Adobe Patch Tuesday, June 2025 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for June 2025
- Adobe Patches for June 2025
- Zero-day Vulnerabilities Patched in June Patch Tuesday Edition
- Critical Severity Vulnerabilities Patched in June Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities inVulnerability Management, Detection & Response (VMDR)
- Rapid Response withPatch Management (PM)
- Microsoft June 2025 Patch Tuesday Mitigations
- Qualys Monthly Webinar Series
Microsoft’s June 2025 Patch Tuesday has landed, addressing a new batch of critical and important vulnerabilities across Windows and enterprise products. Here’s a quick breakdown of what you need to know.
Microsoft Patch Tuesday for June 2025
In this month’s Patch Tuesday, June 2025 edition, Microsoft addressed 69 vulnerabilities. The updates include 10 critical and 57 important severity vulnerabilities. In this month’s updates, Microsoft has addressed one zero-day vulnerability being exploited in the wild and one being publicly disclosed.
Microsoft has addressed two vulnerabilities in Microsoft Edge (Chromium-based) in this month’s updates.
Microsoft Patch Tuesday, June edition includes updates for vulnerabilities in .NET and Visual Studio, Windows Common Log File System Driver, Windows Cryptographic Services, Windows DHCP Server, Windows KDC Proxy Service (KPSSVC), Windows DWM Core Library, Windows Local Security Authority Subsystem Service (LSASS), and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, and Remote Code Execution (RCE).
The June 2025 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 2 | Important: 2 |
| Denial of Service Vulnerability | 6 | Important: 6 |
| Elevation of Privilege Vulnerability | 13 | Critical: 1 Important: 12 |
| Information Disclosure Vulnerability | 17 | Important: 17 |
| Remote Code Execution Vulnerability | 25 | Critical: 8 Important: 17 |
| Security Feature Bypass Vulnerability | 3 | Important: 3 |
Adobe Patches for June 2025
Adobe has released seven security advisories to address 254 vulnerabilities in Adobe InCopy, Adobe Experience Manager, Adobe Commerce, Adobe InDesign, Adobe Substance 3D Sampler, Adobe Acrobat Reader, and Adobe Substance 3D Painter. 18 of these vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to privilege escalation, security feature bypass, and arbitrary code execution.
Zero-day Vulnerabilities Patched in June Patch Tuesday Edition
CVE-2025-33053: Web Distributed Authoring and Versioning (WEBDAV) Remote Code Execution Vulnerability
External control of file name or path flaws in WebDAV allows an unauthenticated attacker to execute code over a network. An attacker must convince a user to open a specially crafted file to execute remote code. Security researchers have confirmed that the APT group Stealth Falcon (aka FruityArmor) is abusing this zero-day vulnerability in WebDAV to deploy malware.
CISA added CVE-2025-33053 to its Known Exploited Vulnerabilities Catalog and urged users to patch it before July 1, 2025.
CVE-2025-33073: Windows SMB Client Elevation of Privilege Vulnerability
Improper access control flaw in Windows SMB may allow an authenticated attacker to elevate network privileges. Upon successful exploitation, an attacker could gain SYSTEM privileges.
Critical Severity Vulnerabilities Patched in June Patch Tuesday Edition
CVE-2025-29828: Windows Schannel Remote Code Execution Vulnerability
Schannel (Secure Channel) is a Security Support Provider (SSP) used by Windows to implement Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols.
Windows Cryptographic Services contains a missing memory release after an effective lifetime that may allow an unauthenticated attacker to execute code over a network. An attacker may exploit the vulnerability by maliciously using fragmented ClientHello messages to a target server that accepts Transport Layer Security (TLS) connections.
CVE-2025-32710: Windows Remote Desktop Services Remote Code Execution Vulnerability
Windows Remote Desktop Services (RDS), formerly Terminal Services, is a suite of Microsoft Windows Server features allowing users to access Windows applications and graphical desktops remotely.
Windows Remote Desktop Services contains a use-after-free flaw that may allow an unauthenticated attacker to execute code over a network. To exploit the vulnerability, an attacker must win a race condition.
CVE-2025-47162: Microsoft Office Remote Code Execution Vulnerability
Microsoft Office contains a heap-based buffer overflow flaw that could allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-47953 & CVE-2025-47164: Microsoft Office Remote Code Execution Vulnerability
Microsoft Office contains a use-after-free flaw that could allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-33071: Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability
The KDC Proxy Service (KPSSVC) in Windows is a service that allows clients to communicate with KDC servers (Key Distribution Centers) over HTTPS instead of TCP. It acts as a bridge, encapsulating Kerberos requests within HTTPS requests and relaying them to a Domain Controller.
Windows KDC Proxy Service (KPSSVC) contains a use-after-free flaw that may allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-47966: Power Automate Elevation of Privilege Vulnerability
Windows Power Automate is a desktop application within the broader Microsoft Power Platform that allows users to automate tasks on their Windows operating system.
Exposure of sensitive information to an unauthenticated actor in Power Automate may allow attackers to elevate network privileges.
CVE-2025-33070: Windows Netlogon Elevation of Privilege Vulnerability
Netlogon is a Remote Procedure Call (RPC) protocol and a service in Windows that facilitates authentication and communication between domain controllers and other devices within a domain.
The use of uninitialized resources in Windows Netlogon allows an unauthenticated attacker to elevate privileges over a network.
CVE-2025-47167: Microsoft Office Remote Code Execution Vulnerability
Microsoft Office contains a type confusion flaw that could allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-47172: Microsoft SharePoint Server Remote Code Execution Vulnerability
Improper neutralization of special elements used in an SQL command in Microsoft Office SharePoint may allow an authenticated attacker to achieve remote code execution.
Other Microsoft Vulnerability Highlights
- CVE-2025-32713 is an elevation of privilege vulnerability in the Windows Common Log File System Driver. Upon successful exploitation of the vulnerability, an attacker could gain SYSTEM privileges.
- CVE-2025-32714 is an elevation of privilege vulnerability in Windows Installer. Improper access control flaw may allow an attacker to gain SYSTEM privileges.
- CVE-2025-47962 is an elevation of privilege vulnerability in Windows SDK. Improper access control flaw may allow an attacker to gain SYSTEM privileges.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Storage Management Provider, Windows Remote Desktop Services, Windows Win32K – GRFX, Windows Installer, Remote Desktop Client, Windows Media, Windows SMB, Windows Recovery Driver, Windows Storage Port Driver, WebDAV, Microsoft Local Security Authority Server (lsasrv), Windows Local Security Authority (LSA), Windows Routing and Remote Access Service (RRAS), Windows Kernel, Windows Standards-Based Storage Management Service, App Control for Business (WDAC), Windows Netlogon, Windows Shell, Microsoft Office, Microsoft Office SharePoint, Microsoft Office Excel, Microsoft Office Word, Microsoft Office Outlook, Microsoft Office PowerPoint, Windows Remote Access Connection Manager, Windows Security App, Visual Studio, Windows SDK, Power Automate, Microsoft AutoUpdate (MAU), Windows Hello, Nuance Digital Engagement Platform, Windows Secure Boot, and Microsoft Edge (Chromium-based).
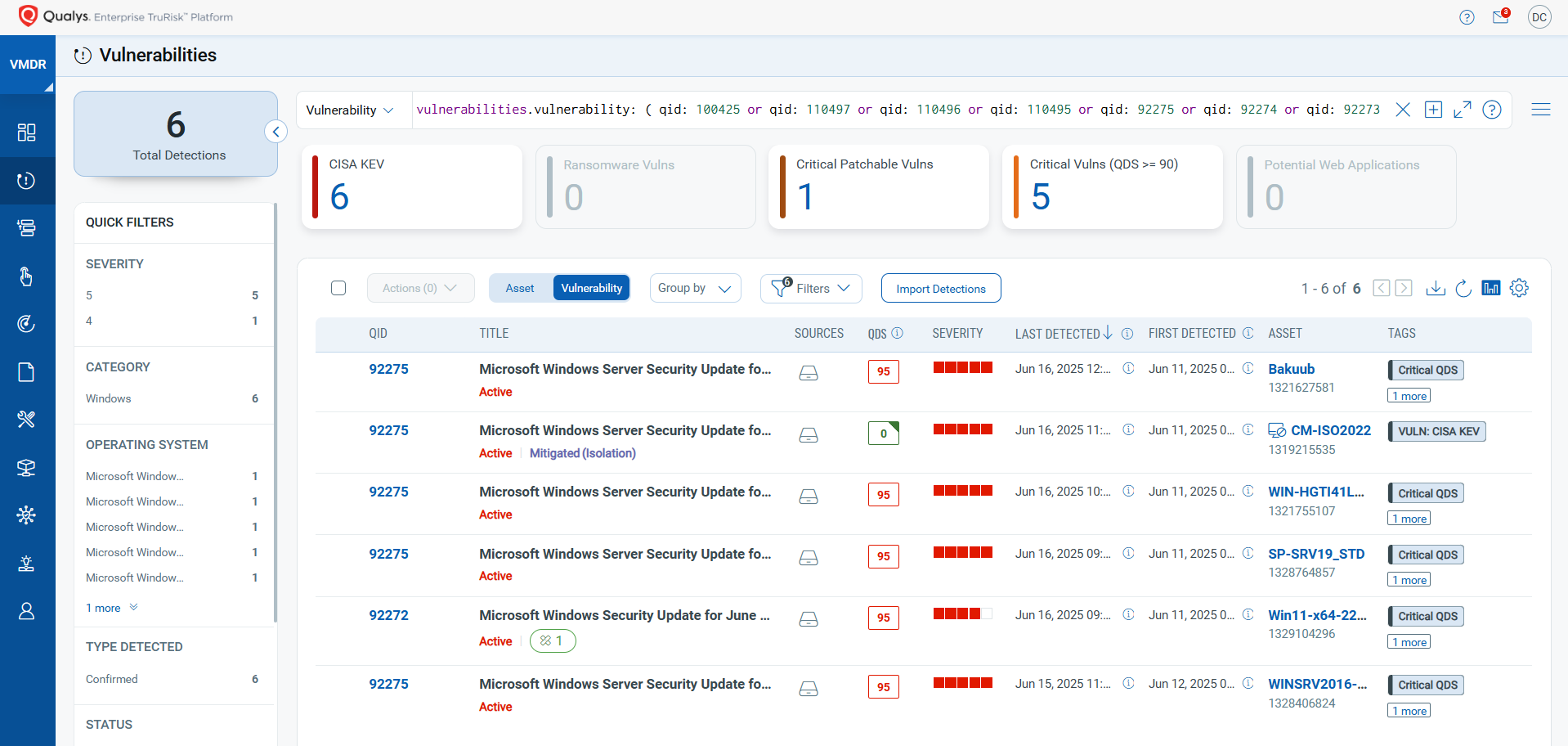
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 100425 or qid: 110497 or qid: 110496 or qid: 110495 or qid: 92275 or qid: 92274 or qid: 92273 or qid: 92272 or qid: 92270 or qid: 383342 or qid: 383341 )
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select the respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 100425 or qid: 110497 or qid: 110496 or qid: 110495 or qid: 92275 or qid: 92274 or qid: 92273 or qid: 92272 or qid: 92270 or qid: 383342 or qid: 383341 )

Microsoft June 2025 Patch Tuesday Mitigations
We have Qualys-created mitigations for the following vulnerabilities: CVE-2025-33064, CVE-2025-33066, CVE-2025-47162, CVE-2025-47953, CVE-2025-47164, CVE-2025-47167, CVE-2025-47171, and CVE-2025-33053.
For Microsoft Office vulnerabilities, where the Preview Pane is an attack vector, we automate their configuration by modifying registry keys and, where applicable, Office policy files. These mitigations work for MS Outlook, Word, Excel, PowerPoint, etc. Another release of this mitigation set involves disabling and executing Windows shortcuts (.lnk) files by modifying specific Registry settings.
Qualys TruRisk Mitigate product customers receive these scripts as part of the Patch Tuesday signature set.
The next Patch Tuesday falls on July 8, and we will be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to ‘This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series
The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
However, it appears that for the second month running, mitigation and the relevant QIDs are missing from the VMDR Knowledgebase.