ToolShell Zero-day: Microsoft Rushes Emergency Patch for Actively Exploited SharePoint Vulnerabilities
On July 19, 2025, Microsoft issued an emergency out-of-band security update to address two zero-day vulnerabilities in Microsoft SharePoint Server: CVE-2025-53770 and CVE-2025-53771. These vulnerabilities are under active exploitation in the wild and demand immediate attention to protect your on-premises SharePoint environments.
CVE-2025-53770: Critical Remote Code Execution
The first of the two vulnerabilities, CVE-2025-53770, is a critical-severity vulnerability with a CVSS score of 9.8 out of 10. Successful exploitation could allow an unauthenticated attacker to execute arbitrary code on a vulnerable SharePoint server. This is due to an insecure deserialization of untrusted data.
The attacks leveraging this vulnerability have been dubbed “ToolShell” and can lead to a complete compromise of the targeted server, including access to sensitive data and the ability to install malicious web shells for persistent access.
Attackers can exfiltrate sensitive data, such as ASP.NET machine keys, which could enable further attacks, such as forging authentication tokens or persistent access.
Major authorities in both the U.S. and the U.K. have sounded the alarm: CISA has placed CVE-2025-53770 on its KEV list, and NHS England’s CSOC issued High-Severity Alert CC-4683 for active exploitation against Microsoft SharePoint Servers.
Why it matters
- A vulnerable SharePoint server becomes an immediate foothold for lateral movement and data theft.
- This vulnerability is actively weaponized and exploited in the wild, with exploitation confirmed by Microsoft and multiple research teams. Attackers can trigger the flaw remotely without authentication, user interaction, or elevated privileges, enabling rapid, full-system compromise.
- Exploitation in the wild activity means defenders have little to no lead time once a server is exposed.
CVE-2025-53771: Server Spoofing Vulnerability
Tracked as a medium-severity vulnerability with a CVSS score of 6.3, CVE-2025-53771 is a spoofing vulnerability. It arises from an improper limitation of a pathname to a restricted directory, also known as path traversal. While less critical than the RCE flaw, it plays a role in the overall attack chain, making its remediation crucial.
History of the Vulnerabilities
- CVE-2025-53770 (RCE, CVSS 9.8): A direct variant of CVE-2025-49706, Microsoft attempted to fix this vulnerability in the July 2025 Patch Tuesday roll-up. The original mitigation proved incomplete, leaving a new deserialization pathway that adversaries now exploit for unauthenticated remote code execution.
- CVE-2025-53771 (Spoofing, CVSS 6.3): A path-traversal–driven spoofing flaw that stems from improper restriction of file paths. Closely related to CVE-2025-49704 from the same July 2025 bulletin, it is less severe than the RCE issue but frequently chained with CVE-2025-53770 to facilitate lateral movement and persistence. Prompt remediation is, therefore, essential despite its medium rating.
Who is Affected?
These vulnerabilities impact on-premises installations of:
- Microsoft SharePoint Server Subscription Edition
- Microsoft SharePoint Server 2019
- Microsoft SharePoint Server 2016
- Microsoft SharePoint Server 2010 and 2013 (end‑of‑life and no longer supported, but still identified by Microsoft as affected)
Microsoft SharePoint Online (part of Microsoft 365) is not affected by these vulnerabilities.
Qualys QID Coverage
Qualys has released the QIDs in the table below for the above-mentioned vulnerabilities.
| CVE | QID | Title | Version |
| CVE-2025-53770/ CVE-2025-53771 | 110501 | Microsoft SharePoint Server Multiple Vulnerabilities | VULNSIGS-2.6.376-4 |
| CVE-2025-49706/ CVE-2025-49704 | 110498 | Microsoft SharePoint Server Security Update for July 2025 | VULNSIGS-2.6.366-4 |
Eliminating Risk of these Vulnerabilities with the Qualys Enterprise TruRiskTM Platform
Identify At-Risk SharePoint Servers with Qualys CSAM 3.0
Start by mapping every SharePoint instance that could be hit. With CyberSecurity Asset Management (CSAM) 3.0 and its External Attack Surface Management module, quickly surface:
- Internet-facing SharePoint servers running the vulnerable builds tied to CVE-2025-53770/CVE-2025-53771
- On-premises or cloud hosts still on End-of-Life (EOL) or End-of-Support (EOS) SharePoint versions
- Shadow or misconfigured instances that traditional inventories may have missed
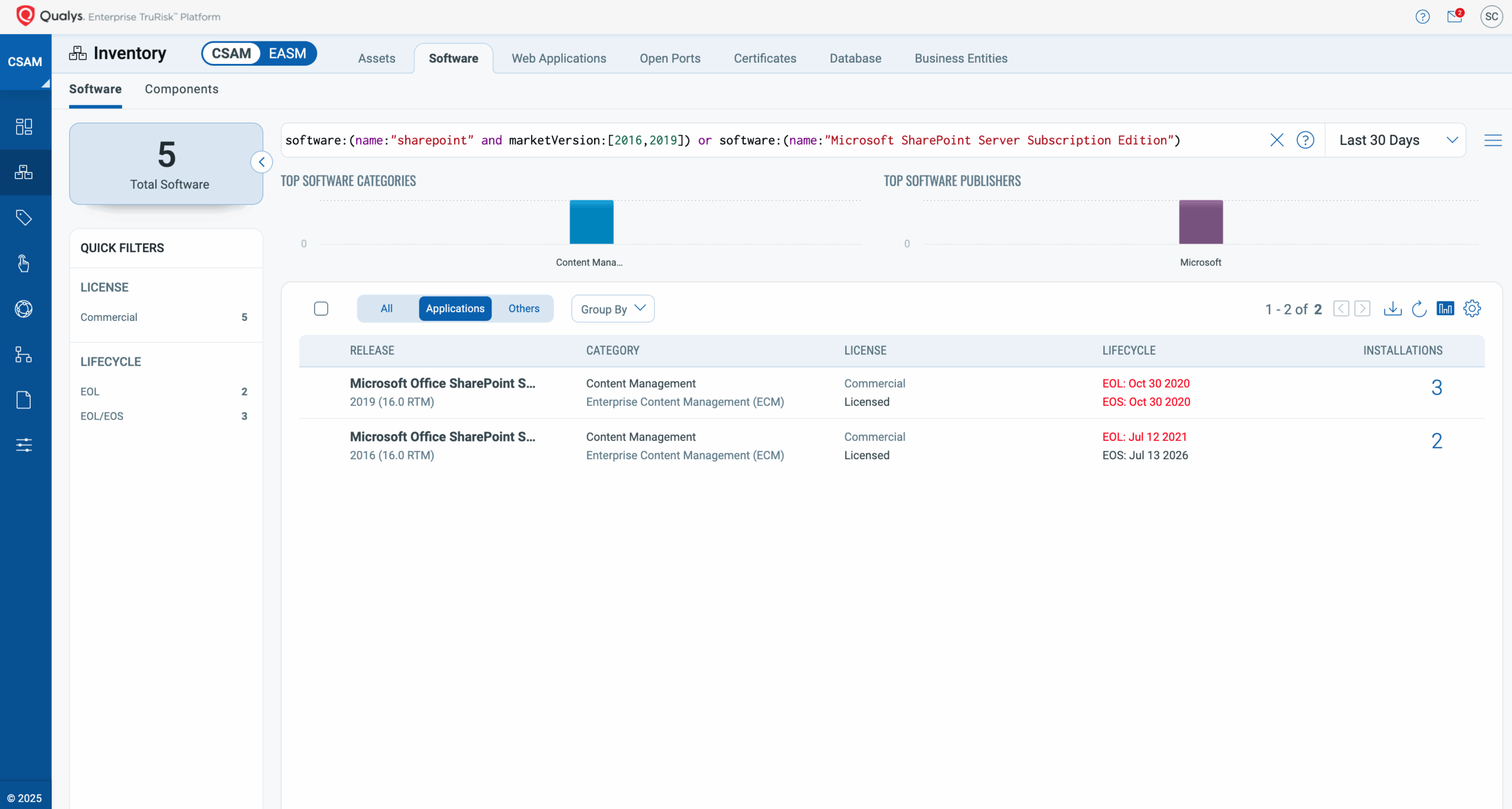
Identify every asset running SharePoint Server Subscription Edition 2019 or 2016 that is vulnerable to CVE-2025-53770/CVE-2025-53771:
software:(name:"sharepoint" and marketVersion:[2016,2019]) or software:(name:"Microsoft SharePoint Server Subscription Edition")
Strengthen Your Security Posture with Qualys VMDR
Qualys VMDR offers comprehensive coverage and visibility into vulnerabilities, empowering organizations to rapidly respond to, prioritize, and mitigate the associated risks. Additionally, Qualys customers can leverage Qualys Patch Management to remediate these vulnerabilities effectively.
Leverage the power of Qualys VMDR alongside TruRiskTM scoring and the Qualys Query Language (QQL) to efficiently identify and prioritize vulnerable assets, effectively addressing the vulnerabilities highlighted above.
Use this QQL statement:
(vulnerabilities.vulnerability.cveIds: CVE-2025-53770 or vulnerabilities.vulnerability.cveIds: CVE-2025-53771 or vulnerabilities.vulnerability.cveIds: CVE-2025-49706 or vulnerabilities.vulnerability.cveIds: CVE-2025-49704) and vulnerabilities.qualysMitigable:TRUE and vulnerabilities.qualysPatchable:TRUE

How Qualys TruRisk Eliminate Helps in Risk Reduction
TruRisk Eliminate™️ offers a comprehensive risk reduction solution designed to help security and IT teams to proactively address nearly 100% of CISA KEVs and ransomware vulnerabilities.
In the context of the SharePoint vulnerabilities, leverage Qualys TruRisk Eliminate to:
- Patch these vulnerabilities, or
- Apply out-of-the-box mitigations until a patch can be deployed
Because these vulnerabilities are Qualys patchable, you should immediately deploy the patches and fix them. Relevant patches were added to the Qualys patch catalog and are ready to be deployed by utilizing the Qualys agent.
In this case, due to the exploitability of the SharePoint vulnerabilities, customers must address these vulnerabilities quickly, especially on internet-facing SharePoint deployments.
Since it took time for Microsoft to release the relevant patches, customers could have used the Qualys provided mitigations to address the risk until the patch can be deployed.
The same researchers who researched and created the Microsoft SharePoint Server bypasses signature have proactively developed and thoroughly tested all mitigations, including the SharePoint ones, ensuring organizations can rapidly and effectively neutralize this new threat.
With 3 simple steps, you can reduce your risk:
Step 1 – In VMDR, list all the vulnerabilities
Use following query:
(vulnerabilities.vulnerability.cveIds: CVE-2025-53770 or vulnerabilities.vulnerability.cveIds: CVE-2025-53771 or vulnerabilities.vulnerability.cveIds: CVE-2025-49706 or vulnerabilities.vulnerability.cveIds: CVE-2025-49704)

Step 2 – View Risk Elimination
Select the vulnerabilities and use Actions > View Risk Eliminate.
This takes you to Eliminate Page which has Remediation (Patch) and Mitigation options available, for the most comprehensive risk reduction.
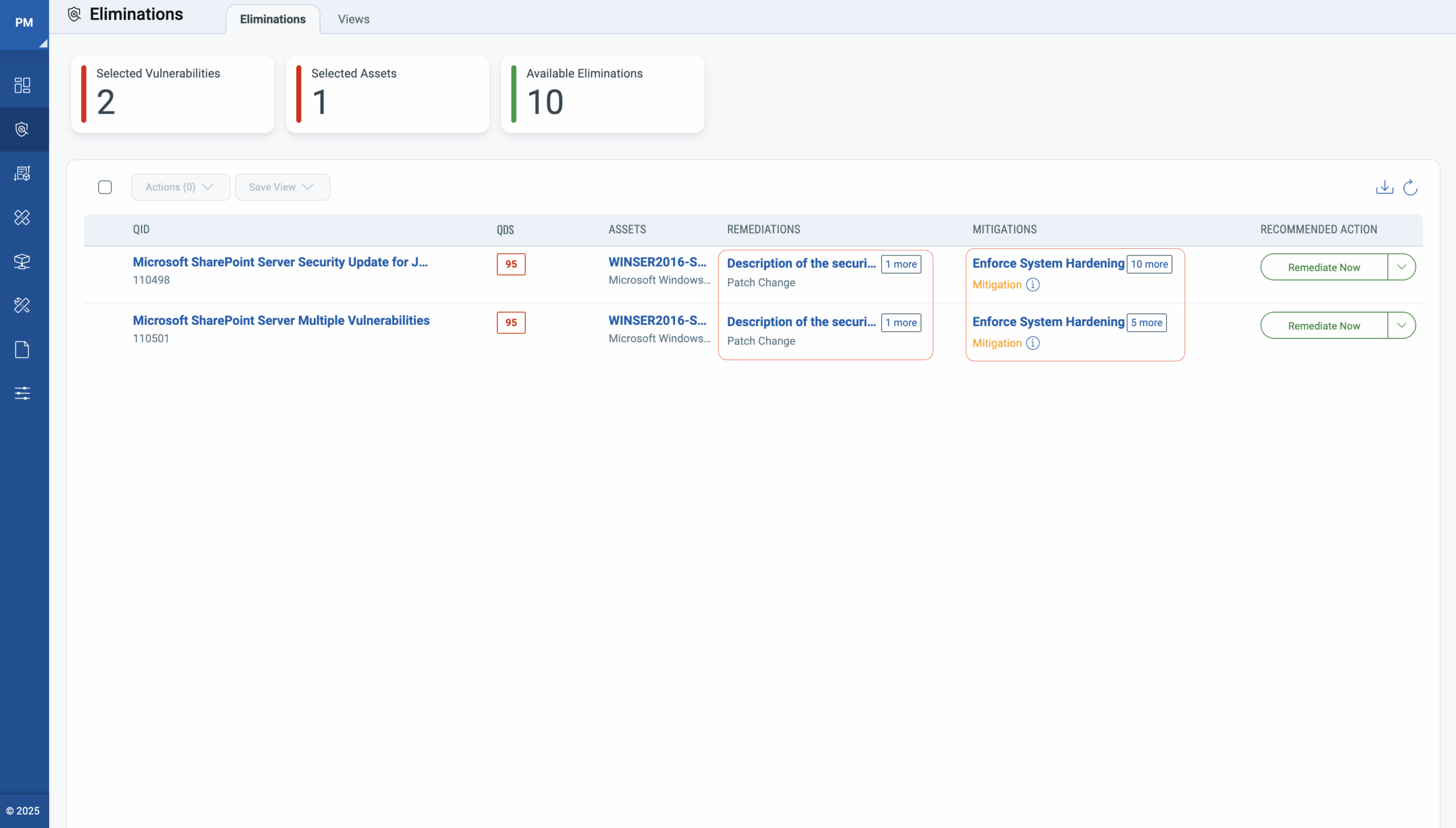

Step 3 – Create Remediation (Patch) or Mitigation Job
Remediation (Patch) will fix the vulnerability permanently.

Mitigation, on the other hand, is a temporary fix until a patch can be deployed. Mitigations are designed to reduce risk by making the vulnerability non-exploitable. Once applied successfully, you’ll see a visible reduction in the Qualys Detection Score (QDS).
For an in-depth technical blog post, visit our Threat Protect post on these vulnerabilities.