Microsoft and Adobe Patch Tuesday, August 2025 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for August 2025
- Adobe Patches for August 2025
- Zero-day Vulnerability Patched in August Patch Tuesday Edition
- Critical Severity Vulnerabilities Patched in August Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities inVulnerability Management, Detection & Response (VMDR)
- Rapid Response withPatch Management (PM)
- Microsoft July 2025 Patch Tuesday Mitigations
- Qualys Monthly Webinar Series
It’s the second Tuesday of August, and Microsoft has rolled out its latest security updates. Microsoft’s August 2025 Patch Tuesday has arrived, bringing a fresh wave of security fixes to help organizations stay ahead of evolving threats. Here’s a quick breakdown of what you need to know.
Microsoft Patch Tuesday for August 2025
In this month’s Patch Tuesday, the August 2025 edition, Microsoft addressed 119 vulnerabilities. The updates include 13 critical and 91 important severity vulnerabilities. In this month’s updates, Microsoft has addressed one zero-day vulnerability that is being publicly disclosed.
Microsoft has addressed 10 vulnerabilities in Microsoft Edge (Chromium-based) in this month’s updates.
Microsoft Patch Tuesday, August edition includes updates for vulnerabilities in Microsoft Exchange Server, Microsoft Graphics Component, Remote Desktop Server, Windows Hyper-V, SQL Server, Windows NTFS, Windows NTLM, and more.
Microsoft has fixed several flaws in multiple software, including Spoofing, Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, and Remote Code Execution (RCE).
The August 2025 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 4 | Critical: 1 Important: 3 |
| Denial of Service Vulnerability | 4 | Important: 4 |
| Elevation of Privilege Vulnerability | 42 | Critical: 1 Important: 41 |
| Information Disclosure Vulnerability | 16 | Critical: 2 Important: 14 |
| Remote Code Execution Vulnerability | 34 | Critical: 9 Important: 25 |
Adobe Patches for August 2025
Adobe has released 13 security advisories to address 68 vulnerabilities in Adobe Commerce, Adobe Substance 3D Viewer, Adobe Animate, Adobe Illustrator, Adobe Photoshop, Adobe Substance 3D Modeler, Adobe Substance 3D Painter, Adobe Substance 3D Sampler, Adobe InDesign, Adobe InCopy, Adobe Substance 3D Stager, Adobe FrameMaker, and Adobe Dimension. 38 of these vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to privilege escalation, arbitrary file system read, application denial-of-service, and arbitrary code execution.
Zero-day Vulnerability Patched in August Patch Tuesday Edition
CVE-2025-53779: Windows Kerberos Elevation of Privilege Vulnerability
Kerberos is a robust network authentication protocol widely used in Windows environments, particularly within Active Directory (AD) domains. Its primary purpose is to verify the identity of users and services securely and efficiently, preventing unauthorized access and safeguarding sensitive data.
The path traversal vulnerability in Windows Kerberos may allow an authenticated attacker to elevate privileges over a network. Upon successful exploitation, an attacker could gain domain administrator privileges.
Critical Severity Vulnerabilities Patched in August Patch Tuesday Edition
CVE-2025-53781: Azure Virtual Machines Information Disclosure Vulnerability
Hyper-V is a virtualization technology developed by Microsoft that allows you to create and run multiple virtual machines (VMs) on a single physical computer. It acts as a hypervisor, providing a layer of abstraction between the hardware and the operating systems running in the VMs.
Upon successful exploitation, an attacker could disclose sensitive information.
CVE-2025-50176: DirectX Graphics Kernel Remote Code Execution Vulnerability
A type confusion vulnerability in the Graphics Kernel may allow an authenticated attacker to execute code locally. An authenticated attacker could trigger this vulnerability without admin or other elevated privileges.
CVE-2025-50177: Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability
Microsoft Message Queuing is a messaging infrastructure developed by Microsoft that enables applications to communicate asynchronously and reliably, even when they are not running on the same system or are temporarily offline.
Use-after-free vulnerability in Windows Message Queuing allows an unauthenticated attacker to achieve remote code execution. Successful exploitation of the vulnerability requires an attacker to win a race condition.
CVE-2025-53731 & CVE-2025-53740: Microsoft Office Remote Code Execution Vulnerability
A use-after-free vulnerability in Microsoft Office allows an unauthenticated attacker to achieve remote code execution.
CVE-2025-53733: Microsoft Word Remote Code Execution Vulnerability
Successful exploitation of the vulnerability may allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-53766: GDI+ Remote Code Execution Vulnerability
A heap-based buffer overflow vulnerability in Windows GDI+ may allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-53778: Windows NTLM Elevation of Privilege Vulnerability
NTLM (Windows NT LAN Manager) is an authentication protocol used in Windows networks to verify the identity of users and computers. It’s a challenge-response mechanism where a client proves its knowledge of a password to a server or domain controller.
An improper authentication flaw in Windows NTLM may allow an authenticated attacker to elevate privileges over a network. Upon successful exploitation, an attacker could gain SYSTEM privileges.
CVE-2025-53784: Microsoft Word Remote Code Execution Vulnerability
A use-after-free vulnerability in Microsoft Office Word may allow an unauthenticated attacker to achieve remote code execution.
CVE-2025-49707: Azure Virtual Machines Spoofing Vulnerability
An improper access control flaw in Azure Virtual Machines could allow an authenticated attacker to perform spoofing locally.
CVE-2025-48807: Windows Hyper-V Remote Code Execution Vulnerability
Improper restriction of the communication channel to intended endpoints in Windows Hyper-V could allow an authenticated attacker to achieve remote code execution.
CVE-2025-53793: Azure Stack Hub Information Disclosure Vulnerability
An improper authentication flaw in Azure Stack allows an unauthenticated attacker to disclose information over a network.
CVE-2025-50165: Windows Graphics Component Remote Code Execution Vulnerability
An untrusted pointer dereference flaw in the Microsoft Graphics Component may allow an unauthenticated attacker to achieve remote code execution.
Other Microsoft Vulnerability Highlights
- CVE-2025-53786 is an elevation of privilege vulnerability in Microsoft Exchange Server Hybrid Deployment. Successful exploitation of the vulnerability could allow an attacker to escalate privileges within the organization’s connected cloud environment.
- CVE-2025-49743 is an elevation of privilege vulnerability in Windows Graphics Component. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2025-50167 is an elevation of privilege vulnerability in Windows Hyper-V. Upon successful exploitation, an attacker could gain SYSTEM privileges.
- CVE-2025-50168 is an elevation of privilege vulnerability in Win32k. A type confusion flaw in Windows Win32K – ICOMP may allow an authorized attacker to gain SYSTEM privileges.
- CVE-2025-53132 is an elevation of privilege vulnerability in Win32k. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2025-53147 is an elevation of privilege vulnerability in the Windows Ancillary Function Driver for WinSock. A use-after-free flaw may allow an authenticated attacker to gain SYSTEM privileges.
- CVE-2025-53156 is an information disclosure vulnerability in the Windows Storage Port Driver. Successful exploitation of the vulnerability could allow the disclosure of certain kernel memory content.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Azure Virtual Machines, Microsoft Office SharePoint, Microsoft Edge for Android, Microsoft Dynamics 365 (on-premises), Windows Routing and Remote Access Service (RRAS), Windows Kernel, Windows Ancillary Function Driver for WinSock, Desktop Windows Manager, Windows File Explorer, Windows Push Notifications, Remote Access Point-to-Point Protocol (PPP) EAP-TLS, Windows Win32K – GRFX, Windows Distributed Transaction Coordinator, Windows Win32K – ICOMP, Windows SMB, Windows Cloud Files Mini Filter Driver, Windows DirectX, Windows Installer, Graphics Kernel, Windows Message Queuing, Windows Media, Windows PrintWorkflowUserSvc, Windows NT OS Kernel, Kernel Transaction Manager, Microsoft Brokering File System, Kernel Streaming WOW Thunk Service Driver, Storage Port Driver, Windows Local Security Authority Subsystem Service (LSASS), Windows Connected Devices Platform Service, Windows Remote Desktop Services, Azure File Sync, Microsoft Office Visio, Microsoft Office, Microsoft Office Word, Microsoft Office Excel, Microsoft Office PowerPoint, Azure Stack, Windows GDI+, Azure OpenAI, Windows Security App, Web Deploy, GitHub Copilot and Visual Studio, Microsoft 365 Copilot’s Business Chat, Windows Kerberos, Microsoft Teams, Windows Subsystem for Linux, Windows StateRepository API, Azure Portal, and Microsoft Edge (Chromium-based).
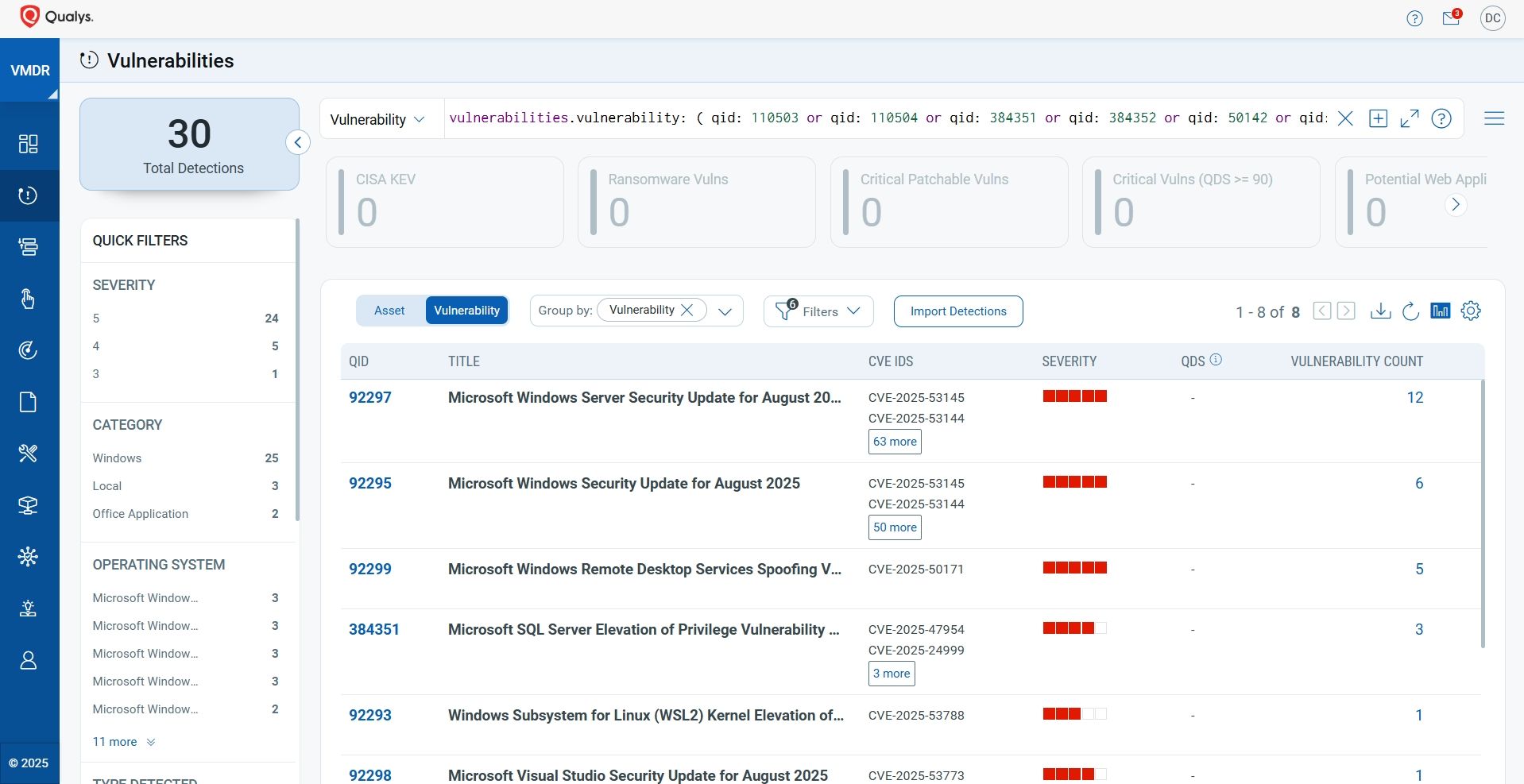
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 110503 or qid: 110504 or qid: 384351 or qid: 384352 or qid: 50142 or qid: 92292 or qid: 92293 or qid: 92295 or qid: 92296 or qid: 92297 or qid: 92298 or qid: 92299 )
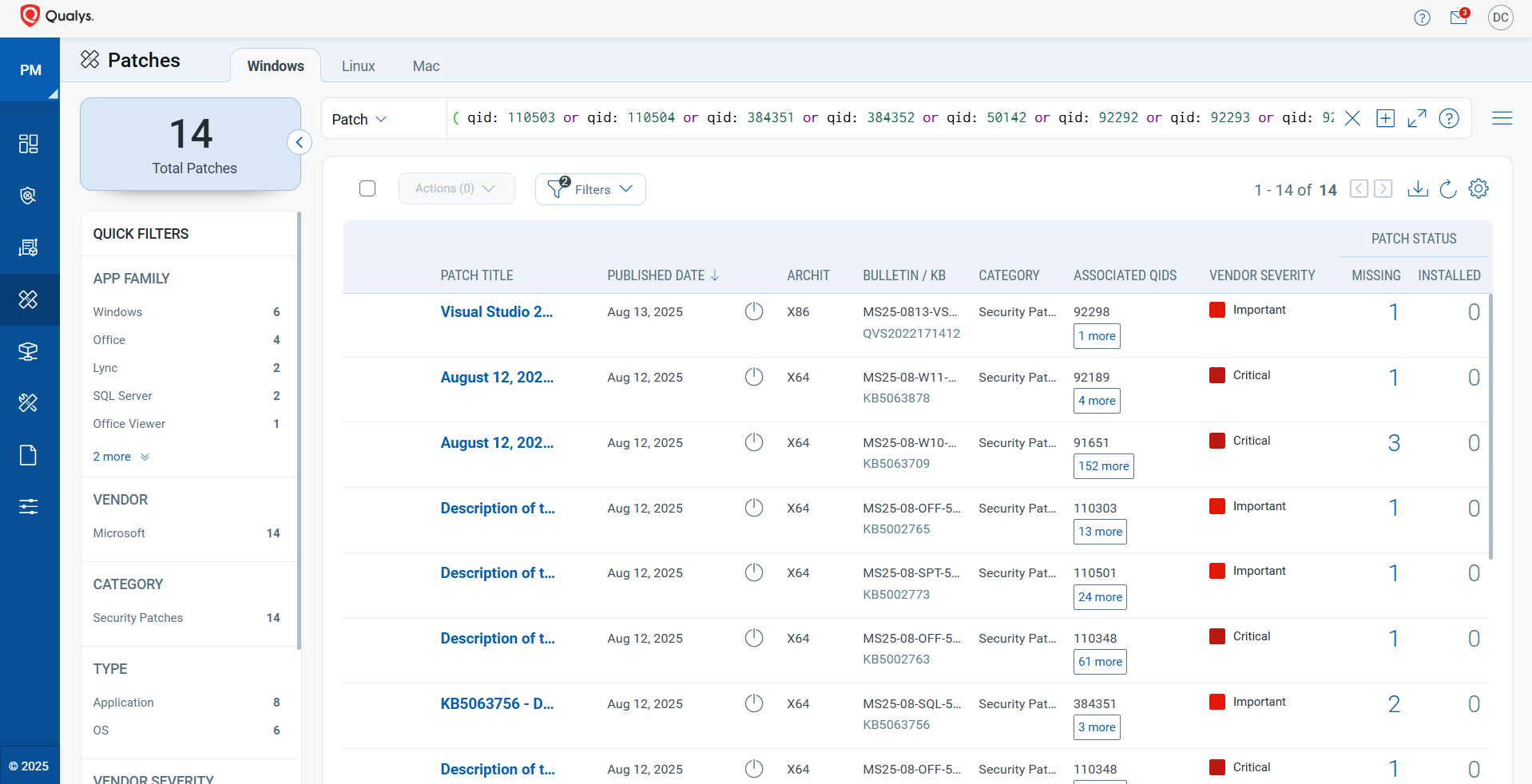
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select the respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 110503 or qid: 110504 or qid: 384351 or qid: 384352 or qid: 50142 or qid: 92292 or qid: 92293 or qid: 92295 or qid: 92296 or qid: 92297 or qid: 92298 or qid: 92299 )
Microsoft July 2025 Patch Tuesday Mitigations
As a first set of our mitigant signature set, we have Qualys-created mitigations for the following 18 vulnerabilities: CVE-2025-50161, CVE-2025-53132, CVE-2025-50168, CVE-2025-50162, CVE-2025-50163, CVE-2025-50164, CVE-2025-50160, CVE-2025-50156, CVE-2025-49757, CVE-2025-53720, CVE-2025-53719, CVE-2025-53138, CVE-2025-53153, CVE-2025-53148, CVE-2025-53722, CVE-2025-53778, CVE-2025-53144, CVE-2025-53145, CVE-2025-50177, CVE-2025-53143, CVE-2025-53142, CVE-2025-53149, CVE-2025-53786, CVE-2025-25005, CVE-2025-25006, CVE-2025-25007, CVE-2025-33051, CVE-2025-53133, CVE-2025-53725, CVE-2025-53726, and CVE-2025-50155.
For Microsoft Office vulnerabilities, where the Preview Pane is an attack vector, our mitigants modify configuration by modifying registry keys and, where applicable, Office policy files. These mitigations work for Microsoft Office applications such as MS Outlook, Word, Excel, PowerPoint, etc. Additionally, this mitigant set mitigates vulnerabilities that affect the Microsoft Brokering File System, Universal Plug and Play (UPnP) service, Visual Studio, Remote Desktop Client, and Windows Hyper-V.
Qualys TruRisk Mitigate product customers receive these scripts as part of the monthly Patch Tuesday signature set.
The next Patch Tuesday falls on September 9, and we will be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to ‘This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series
The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches