When Dependencies Turn Dangerous: Responding to the NPM Supply Chain Attack
On September 8, 2025, attackers compromised a set of 18 widely used npm packages—including chalk, debug, ansi-styles, and strip-ansi—collectively downloaded over 2.6 billion times per week.
Through a targeted phishing campaign against a maintainer, the attackers published malicious versions containing obfuscated JavaScript designed to intercept cryptocurrency transactions. Any organization pulling these versions into builds risked shipping tainted code into production environments.
The Impact: Scale, Reach, and Stealth
This incident highlights just how fragile the modern supply chain can be:
- Scale & reach: 2.6B weekly downloads meant thousands of downstream apps potentially bundled the malware.
- Foundational dependencies: The affected packages are utility libraries—often invisible, yet critical in front-end and back-end stacks.
- Stealthy payload: The injected code wrapped browser APIs, silently rewriting cryptocurrency wallet transactions before signing.
Compromised Packages and Versions
| # | Package | Malicious Version |
| 1 | ansi-regex | 6.2.1 |
| 2 | ansi-styles | 6.2.2 |
| 3 | backslash | 0.2.1 |
| 4 | chalk | 5.6.1 |
| 5 | chalk-template | 1.1.1 |
| 6 | color | 5.0.1 |
| 7 | color-convert | 3.1.1 |
| 8 | color-name | 2.0.1 |
| 9 | color-string | 2.1.1 |
| 10 | debug | 4.4.2 |
| 11 | has-ansi | 6.0.1 |
| 12 | is-arrayish | 0.3.3 |
| 13 | simple-swizzle | 0.2.3 |
| 14 | slice-ansi | 7.1.1 |
| 15 | strip-ansi | 7.1.1 |
| 16 | supports-color | 10.2.1 |
| 17 | supports-hyperlinks | 4.1.1 |
| 18 | wrap-ansi | 9.0.1 |
What Security Teams Should Do Immediately
Because supply chain attacks spread quickly, organizations must take fast, methodical steps to detect and contain impact:
- Check dependency manifests and registries
- Search package-lock.json, yarn.lock, or pnpm-lock.yaml for the exact compromised versions.
- Audit private registries and artifact mirrors to confirm whether tainted packages were cached or replicated.
- Purge poisoned caches
- Clear caches on developer machines, CI/CD servers, and artifact registries.
- Rebuild from known-safe sources to prevent reintroduction of the malicious versions.
- Blocklist the compromised versions
- Prevent reinstallation of these versions by pinning or overriding to safe releases.
- Update build pipelines to fail on detection of malicious versions.
- Scan built assets
- Review recent JavaScript bundles for injected obfuscated code.
- Add checksum or Subresource Integrity (SRI) validation for web assets served from CDNs.
- Hunt for suspicious runtime behavior
- Investigate any unusual outbound connections or API anomalies linked to the compromised code.
- Look for signs of exfiltration or wallet manipulation in logs and telemetry.
- Communicate quickly
- Notify impacted developers and teams.
- Track remediation status across environments (dev, staging, production).
These are baseline hygiene steps. They help ensure environments are clean and prevent re-poisoning from cached artifacts.
Why Hygiene Alone Falls Short
Even with disciplined processes, defenders face four challenges:
- Scale & complexity: With billions of downloads and deep transitive chains, manual checks are slow and error-prone.
- Context gap: Knowing a bad package exists doesn’t reveal whether it’s actually deployed in runtime.
- Runtime blind spots: Traditional software composition analysis (SCA) ends at manifests; it won’t catch if malicious code is actively reaching out to attacker infrastructure.
- Noise vs. signal: Treating all alerts equally delays response to what matters most.
How Qualys Strengthens Supply Chain Defense
This is where Qualys goes beyond hygiene into continuous, risk-aware protection:
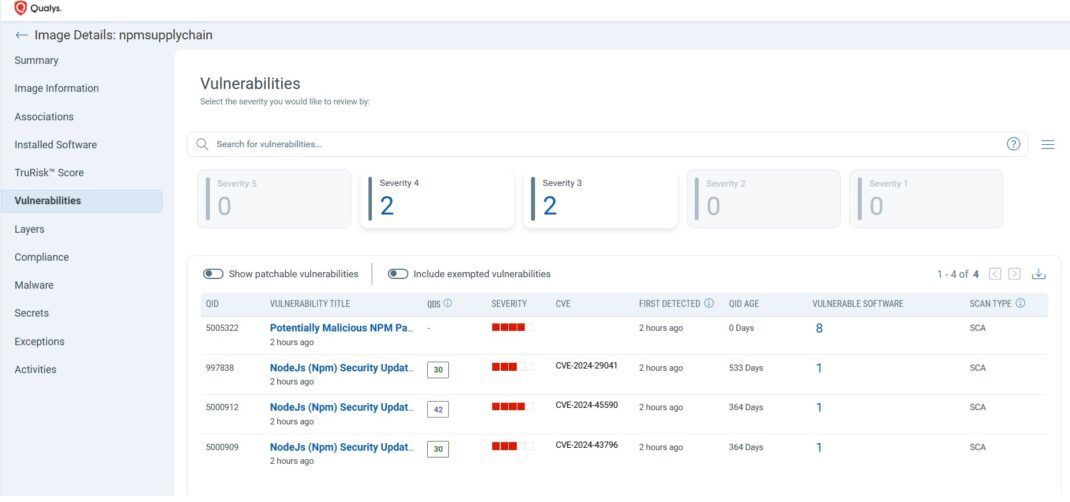
1. Node.js SCA with Runtime Correlation
- Identify compromised npm packages like chalk@5.6.1 or debug@4.4.2 across SBOMs, registries, and workloads.
- Correlate with runtime to answer: Where is this package actually deployed? Is it in a production container serving end-users?
2. TruRisk™ and QDS Scoring
- Prioritize compromised packages as critical through multi-dimensional scoring (exploitability, business impact, internet exposure).
- Qualys Detection Score (QDS) ensures these threats stand out instead of drowning in CVE noise.
3. Attack Path Context
- Map the blast radius: if debug@4.4.2 is in a front-end workload exposed to the internet and tied to privileged IAM roles, Qualys Attack Path shows how it could be exploited.
4. Cloud Detection & Response (CDR)
- Detect real-world malicious behavior:
- Outbound connections to attacker-controlled IPs.
- Exfiltration attempts of wallet or API data.
- Abnormal process or file drift flagged via eBPF sensors.
Example: From Detection to Containment
- Discovery: Qualys SCA flags ansi-styles@6.2.2 in a build pipeline.
- Prioritization: TruRisk marks it critical due to active exploitation.
- Correlation: Attack Path reveals it’s running in an internet-facing container tied to payment flows.
- Runtime Defense: CDR detects outbound wallet manipulation traffic.
- Response: Teams isolate the workload, clear caches, roll back to a safe version, and remediate across environments.
Final Takeaway
The npm compromise shows that supply chain attacks can leap from a single phishing email to billions of downloads in hours.
- Hygiene (lockfile checks, cache purges, blocklists) is essential, but not enough.
- Resilience requires continuous visibility, runtime-aware prioritization, and behavioral detection.
With Qualys SCA, TruRisk, Attack Path, and CDR, organizations gain the visibility and intelligence to not only spot tainted packages but stop them from becoming active compromises.
Because in today’s supply chain, it’s not just about knowing what’s inside your software—it’s about knowing what’s really at risk.
Sign up to try Qualys TotalCloud or get a complimentary custom review of your multi-cloud and container risk.