Microsoft and Adobe Patch Tuesday, October 2025 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for October 2025
- Adobe Patches for October 2025
- Zero-day Vulnerabilities Patched in October Patch Tuesday Edition
- Critical Severity Vulnerabilities Patched in October Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities inVulnerability Management, Detection & Response (VMDR)
- Rapid Response with TruRisk Eliminate
- Automating Risk Elimination and Accelerating Response: Meet Agent Sara
- EVALUATE Vendor-Suggested Mitigation withPolicy Audit
- Qualys Monthly Webinar Series
As cybersecurity threats evolve, Microsoft’s October 2025 Patch Tuesday delivers one of the most comprehensive security updates of the year. Here’s a quick breakdown of what you need to know.
Microsoft Patch Tuesday for October 2025
This month’s release addresses a staggering 193 vulnerabilities, including nine critical and 123 important-severity vulnerabilities.
In this month’s updates, Microsoft has addressed six zero-day vulnerabilities. Four of them are being publicly exploited, and two are publicly disclosed.
Microsoft has addressed 14 vulnerabilities in Microsoft Edge (Chromium-based) in this month’s updates.
This Patch Tuesday edition marks the end of an era, with the Windows 10 reaching the end of its support lifecycle. Microsoft has released the Windows 10 KB5066791 cumulative update, the final cumulative update for the operating system.
Microsoft Patch Tuesday, October edition, includes updates for vulnerabilities in Windows NTFS, Windows Cloud Files Mini Filter Driver, Windows NTLM, Windows Remote Desktop Protocol, Windows Remote Desktop Services, Windows Local Session Manager (LSM), and more.
From elevation of privilege flaws to remote code execution risks, this month’s patches are essential for organizations aiming to maintain a robust security posture.
The October 2025 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 10 | Important: 10 |
| Security Feature Bypass | 11 | Important: 11 |
| Denial of Service Vulnerability | 11 | Important: 11 |
| Elevation of Privilege Vulnerability | 81 | Critical: 3 Important: 78 |
| Information Disclosure Vulnerability | 28 | Important: 28 |
| Remote Code Execution Vulnerability | 31 | Critical: 5 Important: 26 |
Adobe Patches for October 2025
Adobe has released 12 security advisories to address 36 vulnerabilities in Adobe Connect, Adobe Commerce, Adobe Creative Cloud Desktop Application, Adobe Bridge, Adobe Animate, Adobe Experience Manager Screens, Substance 3D Viewer, Substance 3D Modeler, Adobe FrameMaker, Adobe Illustrator, Adobe Dimension, and Substance 3D Stager. 24 of these vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to privilege escalation, security feature bypass, and arbitrary code execution.
Zero-day Vulnerabilities Patched in October Patch Tuesday Edition
CVE-2025-24990: Windows Agere Modem Driver Elevation of Privilege Vulnerability
The Windows Agere Modem Driver is a software component that allows a computer to communicate with an Agere (or LSI) modem, often a dial-up or fax modem integrated into older computers.
The vulnerability exists in the third-party Agere Modem driver that ships natively with supported Windows operating systems. The driver has been removed in the October cumulative update. Successful exploitation of the vulnerability may allow an attacker to gain administrator privileges.
CISA added the vulnerability to its Known Exploited Vulnerabilities Catalog, urging users to patch it before November 4, 2025.
CVE-2025-59230: Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
Windows Remote Access Connection Manager (RASMan) is a core Windows service that manages dial-up and Virtual Private Network (VPN) connections, allowing your computer to connect to remote networks securely.
An improper access control flaw in Windows Remote Access Connection Manager may allow an authenticated attacker to elevate privileges locally. Upon successful exploitation of the vulnerability, an attacker could gain SYSTEM privileges.
CISA added the vulnerability to its Known Exploited Vulnerabilities Catalog, urging users to patch it before November 4, 2025.
CVE-2025-24052: Windows Agere Modem Driver Elevation of Privilege Vulnerability
The vulnerability exists in the third-party Agere Modem driver that ships natively with supported Windows operating systems. The driver has been removed in the October cumulative update. Successful exploitation of the vulnerability may allow an attacker to gain administrator privileges.
CVE-2025-2884: Cert CC: CVE-2025-2884 Out-of-Bounds read vulnerability in TCG TPM2.0 reference implementation
Microsoft mentioned in the advisory that “CVE-2025-2884 is regarding a vulnerability in the CG TPM2.0 Reference implementation’s CryptHmacSign helper function that is vulnerable to Out-of-Bounds read due to the lack of validation of the signature scheme with the signature key’s algorithm.
CERT/CC created this CVE on their behalf. The documented Windows updates incorporate CG TPM2.0 Reference implementation updates, which address this vulnerability.”
CVE-2025-47827: MITRE CVE-2025-47827: Secure Boot bypass in IGEL OS before 11
Microsoft describes, “In IGEL OS before 11, Secure Boot can be bypassed because the igel-flash-driver module improperly verifies a cryptographic signature. A crafted root filesystem can be mounted from an unverified SquashFS image.”
CVE-2025-0033: AMD CVE-2025-0033: RMP Corruption During SNP Initialization
The vulnerability exists in AMD EPYC processors using Secure Encrypted Virtualization – Secure Nested Paging (SEV-SNP). It involves a race condition during Reverse Map Table (RMP) initialization that could allow a malicious or compromised hypervisor to modify RMP entries before they are locked, potentially impacting the integrity of SEV-SNP guest memory. This vulnerability does not expose plaintext data or secrets and requires privileged control of the hypervisor to exploit.
Critical Severity Vulnerabilities Patched in October Patch Tuesday Edition
CVE-2025-59234: Microsoft Office Remote Code Execution Vulnerability
A use-after-free flaw in Microsoft Office could allow an unauthenticated attacker to execute code locally. An attacker must send the user a malicious file and convince the user to open it.
CVE-2025-49708: Windows Graphics Component Remote Code Execution Vulnerability
A use-after-free flaw in Microsoft Graphics Component could allow an authenticated attacker to execute code over a network. Upon successful exploitation of the vulnerability, an attacker could gain SYSTEM privileges.
CVE-2025-59291: Confidential Azure Container Instances Elevation of Privilege Vulnerability
External control of file name or path in Azure Compute Gallery could allow an authenticated attacker to elevate privileges locally. An attacker could trick the system into mounting a malicious file share to a sensitive location, leading to remote code execution.
CVE-2025-59292: Azure Compute Gallery Elevation of Privilege Vulnerability
Azure Compute Gallery is a service for centrally creating, managing, and sharing custom Virtual Machine (VM) images and other compute resources within and across organizations.
External control of the file name or path in Azure Compute Gallery could allow an authenticated attacker to elevate privileges locally. An attacker could trick the system into mounting a malicious file share to a sensitive location, leading to remote code execution.
CVE-2025-59227: Microsoft Office Remote Code Execution Vulnerability
A use-after-free flaw in Microsoft Office could allow an unauthenticated attacker to execute code locally.
CVE-2025-59287: Windows Server Update Service (WSUS) Remote Code Execution Vulnerability
Windows Server Update Service (WSUS) is a feature of Windows Server that allows IT administrators to manage the download and distribution of Microsoft product updates to computers on a local network.
An unauthenticated attacker can execute code over a network by deserializing untrusted data in the Windows Server Update Service. A remote, unauthenticated attacker could send a crafted event that triggers unsafe object deserialization in a legacy serialization mechanism, resulting in remote code execution.
Update (Oct 23, 2025): Microsoft released out-of-band security updates for CVE-2025-59287, a critical WSUS remote code execution bug caused by unsafe deserialization. Patches are available for Windows Server 2012, 2012 R2, 2016, 2019, 2022, 23H2 (Server Core), and 2025; This OOB update supersedes earlier October updates and requires a reboot after installation—prioritize WSUS servers immediately. Qualys is in the process of releasing a new QID.
CVE-2016-9535: MITRE CVE-2016-9535: LibTIFF Heap Buffer Overflow Vulnerability
tif_predict.h and tif_predict.c in libtiff 4.0.6 have assertions that can lead to assertion failures in debug mode, or buffer overflows in release mode, when dealing with unusual tile sizes like YCbCr with subsampling. Reported as MSVR 35105, aka “Predictor heap-buffer-overflow.
CVE-2025-59236: Microsoft Excel Remote Code Execution Vulnerability
A use-after-free flaw in Microsoft Office could allow an unauthenticated attacker to execute code locally.
CVE-2025-59246: Azure Entra ID Elevation of Privilege Vulnerability
Successful exploitation of the vulnerability may allow an attacker to elevate privileges.
Other Microsoft Vulnerability Highlights
- CVE-2025-48004 is an elevation of privilege vulnerability in the Microsoft Brokering File System. An attacker must win a race condition to exploit the vulnerability. Upon successful exploitation, an attacker could gain SYSTEM privileges.
- CVE-2025-55676 is an information disclosure vulnerability in the Windows USB Video Class System Driver. Successful exploitation of the vulnerability could allow the disclosure of certain memory addresses within kernel space.
- CVE-2025-55681 is an elevation of privilege vulnerability in Desktop Windows Manager. An out-of-bounds read flaw may allow an attacker to gain SYSTEM privileges.
- CVE-2025-58722 is an elevation of privilege vulnerability in Microsoft DWM Core Library. A heap-based buffer overflow in Windows DWM may allow an attacker to gain SYSTEM privileges.
- CVE-2025-59199 is an elevation of privilege vulnerability in the Software Protection Platform (SPP). The improper access control flaw may allow an unauthenticated attacker to elevate privileges locally.
- CVE-2025-55680 is an elevation of privilege vulnerability in the Windows Cloud Files Mini Filter Driver. Upon successful exploitation, an attacker could gain SYSTEM privileges.
- CVE-2025-55692 is an elevation of privilege vulnerability in the Windows Error Reporting Service. An attacker who successfully exploited this vulnerability could gain administrator privileges.
- CVE-2025-55693 is an elevation of privilege vulnerability in the Windows Kernel. An attacker must win a race condition to exploit the vulnerability. An attacker who successfully exploits the vulnerability could crash the system by exploiting the use-after-free vulnerability, even as a standard user.
- CVE-2025-55694 is an elevation of privilege vulnerability in the Windows Error Reporting Service. An attacker who exploits this vulnerability could gain administrator privileges.
- CVE-2025-59194 is an elevation of privilege vulnerability in the Windows Kernel. An attacker must win a race condition to exploit the vulnerability. Successful exploitation of the vulnerability may allow an authenticated attacker to elevate privileges locally.
- CVE-2025-59502 is a denial-of-service vulnerability in the Remote Procedure Call. An uncontrolled resource consumption flaw could allow an unauthenticated attacker to deny service over a network.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Agere Windows Modem Driver, Microsoft PowerShell, Windows Failover Cluster, Azure Connected Machine Agent, Microsoft Brokering File System, Virtual Secure Mode, Microsoft Graphics Component, Windows Kernel, Windows Device Association Broker service, Windows Digital Media, Windows Hello, Windows Virtualization-Based Security (VBS) Enclave, Xbox, Microsoft Exchange Server, Visual Studio, .NET, .NET, .NET Framework, Visual Studio, ASP.NET Core, Microsoft Configuration Manager, Azure Monitor, Windows Storage Management Provider, Connected Devices Platform Service (Cdpsvc), Windows Hyper-V, Windows BitLocker, Windows PrintWorkflowUserSvc, Windows NDIS, Windows USB Video Driver, Windows DirectX, Windows DWM, Windows Resilient File System (ReFS), Windows Error Reporting, Windows WLAN Auto Config Service, NtQueryInformation Token function (ntifs.h), Azure Local, Windows Routing and Remote Access Service (RRAS), Microsoft Windows, Windows Ancillary Function Driver for WinSock, Microsoft Windows Speech, Remote Desktop Client, Windows Cryptographic Services, Windows COM, Windows SMB Server, Windows Connected Devices Platform Service, Windows Bluetooth Service, Inbox COM Objects, Windows Remote Desktop, Windows File Explorer, Windows High Availability Services, Windows Core Shell, Microsoft Windows Search Component, Storport.sys Driver, Windows Management Services, Windows SSDP Service, Windows ETL Channel, Software Protection Platform (SPP), Data Sharing Service Client, Network Connection Status Indicator (NCSI), Windows StateRepository API, Windows Resilient File System (ReFS) Deduplication Service, Windows MapUrlToZone, Windows Push Notification Core, Azure Entra ID, Microsoft Office Word, Microsoft Office Excel, Microsoft Office Visio, Microsoft Office, Microsoft Office SharePoint, Windows Remote Access Connection Manager, Microsoft Office PowerPoint, Windows Health and Optimized Experiences Service, Azure PlayFab, JDBC Driver for SQL Server, Copilot, Windows DWM Core Library, Active Directory Federation Services, Microsoft Failover Cluster Virtual Driver, Redis Enterprise, Windows Authentication Methods, Windows SMB Client, XBox Gaming Services, Azure Monitor Agent, Windows Server Update Service, GitHub, Confidential Azure Container Instances, Windows Taskbar Live, Internet Explorer, Microsoft Defender for Linux, Windows Remote Procedure Call, AMD Restricted Memory Page, Microsoft Edge (Chromium-based), TCG TPM2.0, Windows Secure Boot, Microsoft Windows Codecs Library, and Games.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 110508 or qid: 110509 or qid: 385525 or qid: 385526 or qid: 385527 or qid: 50143 or qid: 92311 or qid: 92312 or qid: 92313 or qid: 92314 or qid: 92315 or qid: 92316 or qid: 92317 or qid: 92318 or qid: 92319 or qid: 92321 )

Rapid Response with TruRisk™ Eliminate
Patch to the Latest Version
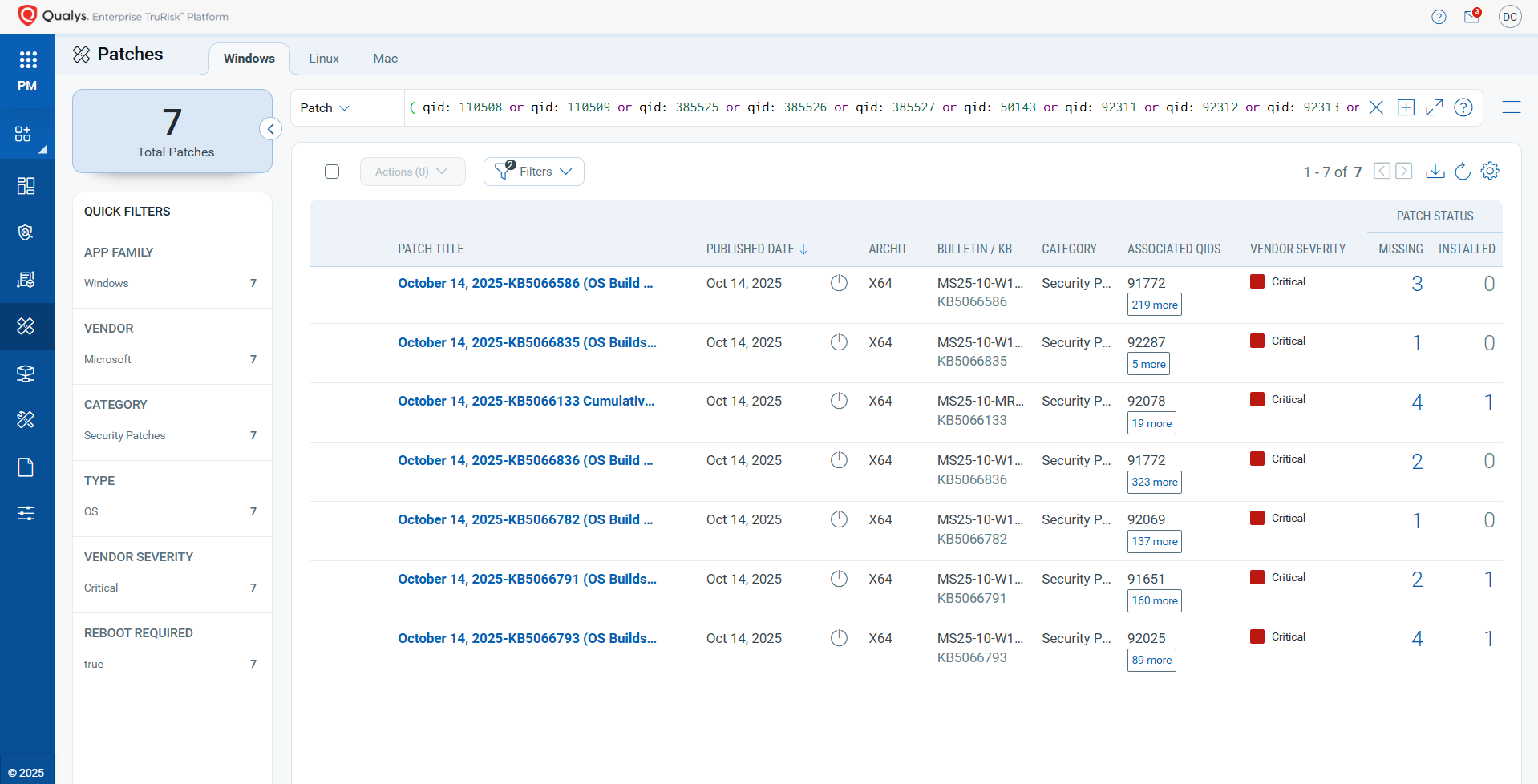
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 110508 or qid: 110509 or qid: 385525 or qid: 385526 or qid: 385527 or qid: 50143 or qid: 92311 or qid: 92312 or qid: 92313 or qid: 92314 or qid: 92315 or qid: 92316 or qid: 92317 or qid: 92318 or qid: 92319 or qid: 92321 )
Mitigation: Reducing Risk Until Remediation
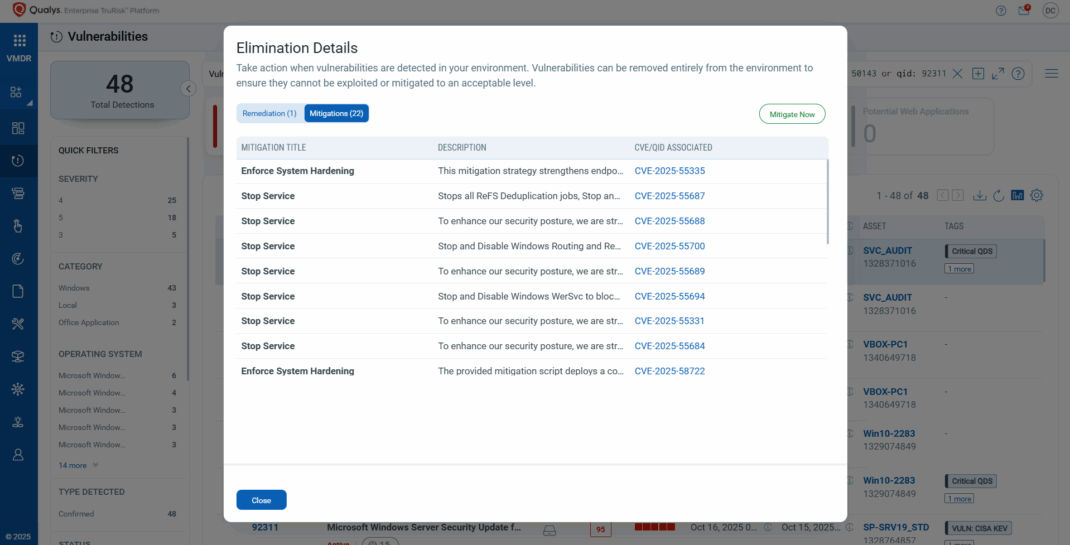
Not every team can patch immediately due to operational challenges. TruRisk™ Eliminate enables security teams to apply mitigation controls that immediately lower exposure and reduce the Qualys Detection Score (QDS).
As a first set of our mitigant signature set, we have Qualys-created mitigations for the following 61 vulnerabilities:
CVE-2025-55247, CVE-2025-55315, CVE-2025-58719, CVE-2025-59191, CVE-2025-55326, CVE-2025-59295, CVE-2025-59189, CVE-2025-48004, CVE-2025-11207, CVE-2025-11209, CVE-2025-11211, CVE-2025-11460, CVE-2025-11458, CVE-2025-11212, CVE-2025-11208, CVE-2025-11219, CVE-2025-11215, CVE-2025-11216, CVE-2025-11213, CVE-2025-11210, CVE-2025-11206, CVE-2025-11205, CVE-2025-59249, CVE-2025-53782, CVE-2025-59248, CVE-2025-49708, CVE-2025-59205, CVE-2025-59261, CVE-2025-59195, CVE-2025-59253, CVE-2025-59198, CVE-2025-59190, CVE-2025-58714, CVE-2025-59242, CVE-2025-58727, CVE-2025-55681, CVE-2025-58722, CVE-2025-59255, CVE-2025-59254, CVE-2025-55694, CVE-2025-55692, CVE-2025-55328, CVE-2025-55335, CVE-2025-59284, CVE-2025-55331, CVE-2025-55685, CVE-2025-55690, CVE-2025-55686, CVE-2025-55689, CVE-2025-55684, CVE-2025-55691, CVE-2025-55688, CVE-2025-59209, CVE-2025-59211, CVE-2025-55687, CVE-2025-59210, CVE-2025-59206, CVE-2025-58717, CVE-2025-55700, CVE-2025-59287, and CVE-2025-53717.
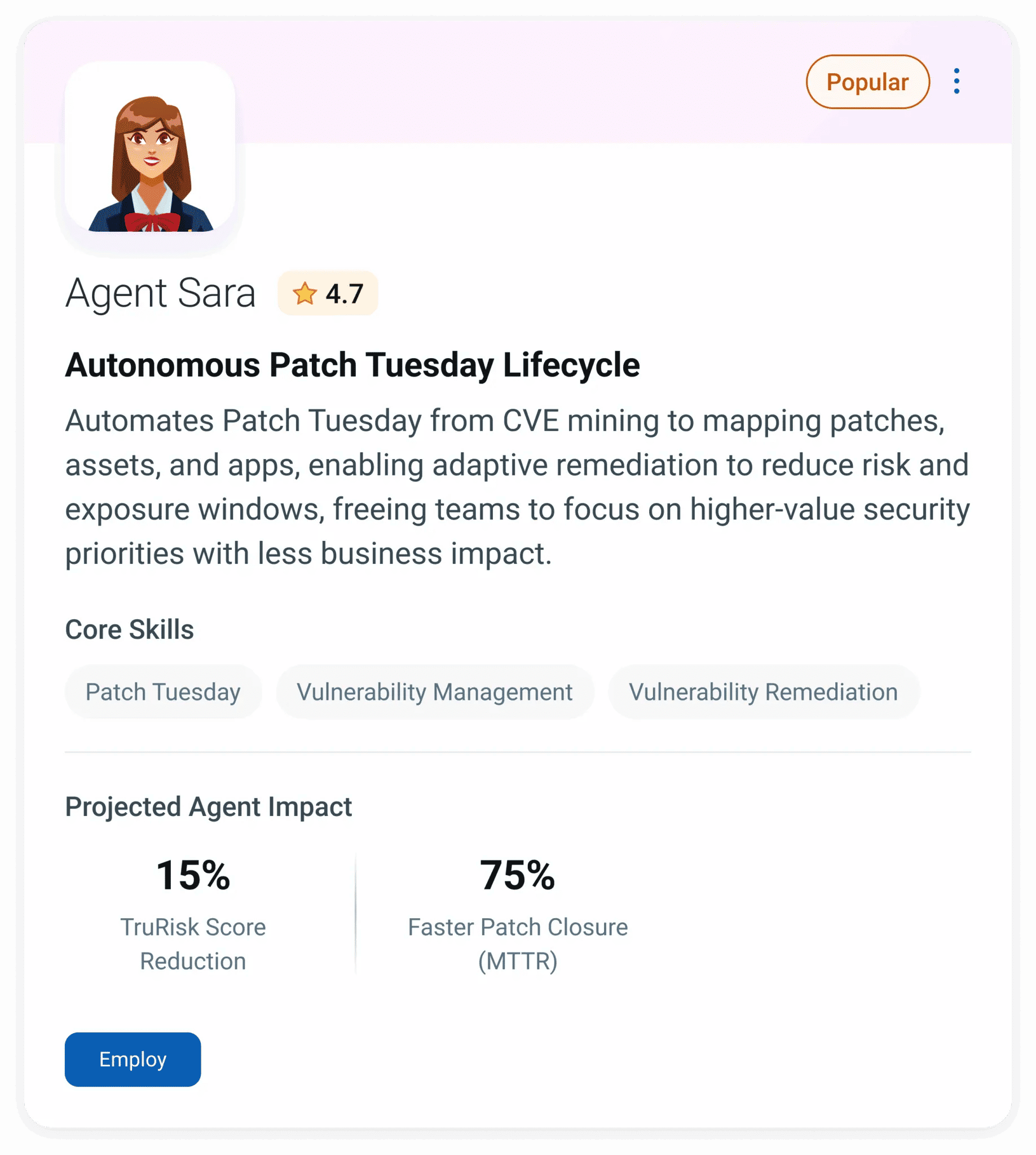
Automating Risk Elimination and Accelerating Response: Meet Agent Sara
To further accelerate your response, Qualys introduces Agent Sara, a powerful Agentic AI agent engineered to automate the entire Patch Tuesday risk elimination lifecycle. Agent Sara intelligently identifies, prioritizes, and remediates vulnerabilities, reducing manual effort and ultimately your current MTTR.
Discover more in our blog about how Agentic AI can transform your patching strategy.
EVALUATE Vendor-Suggested Mitigation with Policy Audit
With Qualys Policy Audit’s Out-of-the-Box Mitigation or Compensatory Controls, reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now; these security controls are not recommended by any industry standards, such as CIS, DISA-STIG.
Qualys Policy Audit team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best practice, existing in a default state, that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned.
The following Qualys Policy Audit Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2025-59282: Internet Information Services (IIS) Inbox COM Objects (Global Memory) Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 7.0 / 6.1
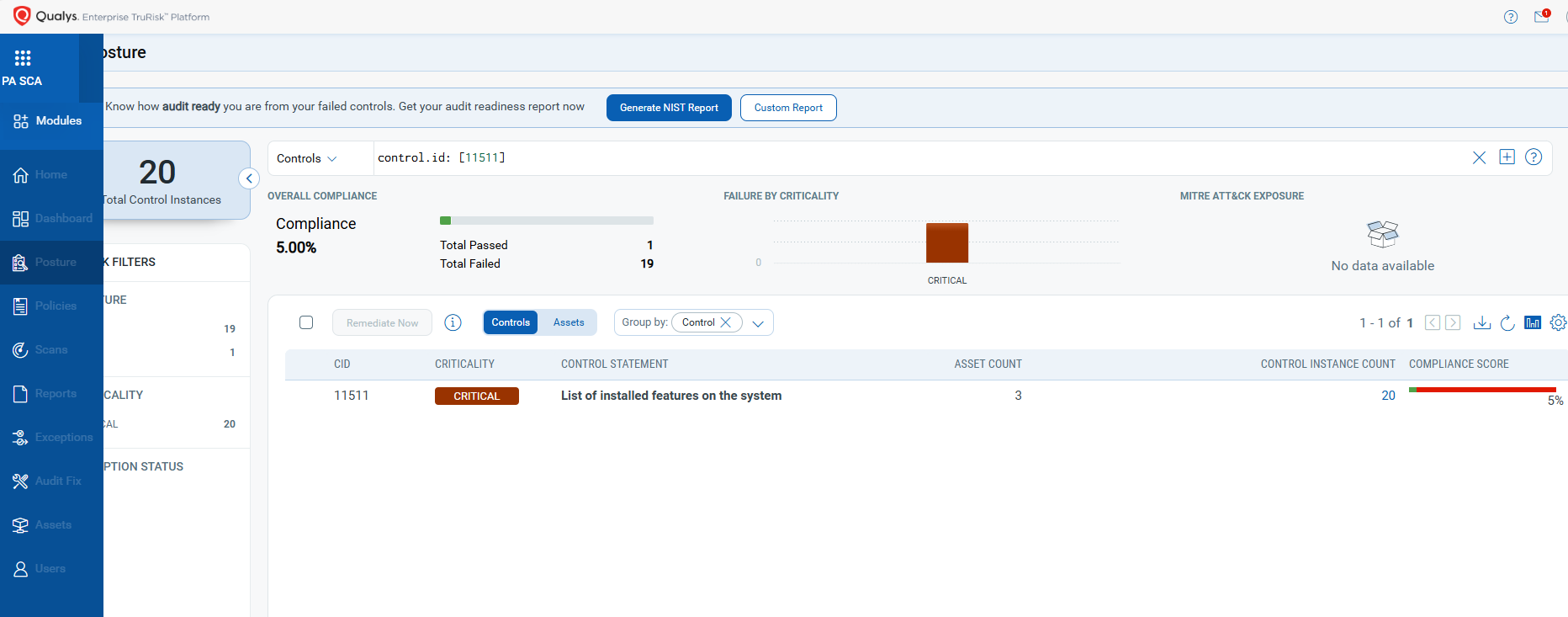
Policy Compliance Control IDs (CIDs):
- 11511 List of installed features on the system
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [11511]
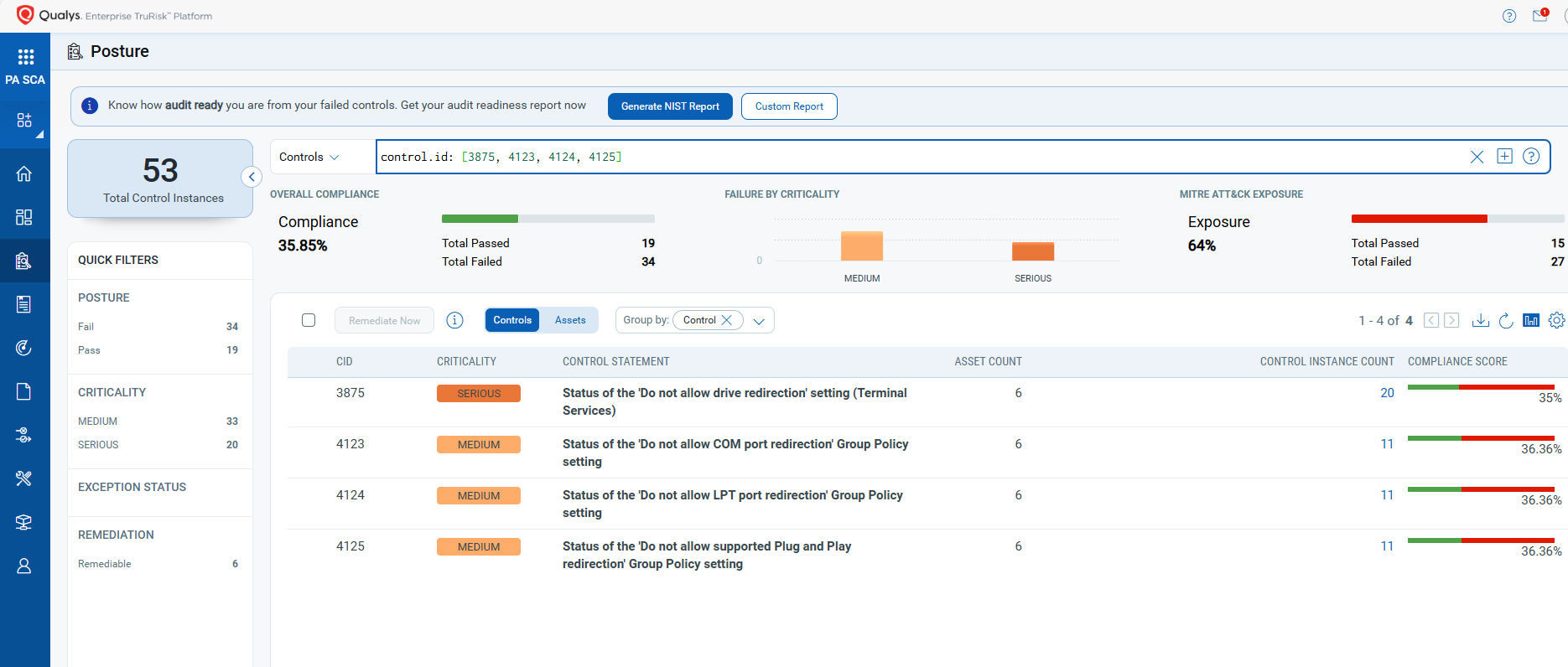
CVE-2025-58718: Remote Desktop Client Remote Code Execution Vulnerability
This vulnerability has a CVSS:3.1 8.8 / 7.7
Policy Compliance Control IDs (CIDs):
- 3875 Status of the ‘Do not allow drive redirection’ setting (Terminal Services)
- 4123 Status of the ‘Do not allow COM port redirection’ Group Policy setting
- 4124 Status of the ‘Do not allow LPT port redirection’ Group Policy setting
- 4125 Status of the ‘Do not allow supported Plug and Play redirection’ Group Policy setting
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [3875, 4123, 4124, 4125]
The next Patch Tuesday falls on November 11, and we will be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to ‘This Month in Vulnerabilities and Patch’s webinar.’
Qualys Monthly Webinar Series
The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are a part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches