A Strategic Response to the F5 BIG-IP Nation-State Breach 2025
In mid-October 2025, the cybersecurity landscape was dealt a severe blow. F5 disclosed a long-term, sophisticated breach by a nation-state threat actor. This incident exposed critical F5 BIG-IP vulnerabilities and triggered heightened scrutiny across enterprise edge infrastructure.
This was not a typical vulnerability disclosure. The attackers exfiltrated a strategic critical pair of assets: portions of BIG-IP source code, and internal details of undisclosed (unpatched) vulnerabilities.
CISA’s KEV Inclusion Underscores the Severity of the F5 BIG-IP Breach
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) immediately labeled this event as an “imminent threat.” The breach was swiftly added to the CISA Known Exploited Vulnerabilities (KEV) list, indicating the highest level of urgency. The reason is simple: The adversary now possesses a technical advantage, allowing them to analyze the source code and weaponize unpatched flaws far faster than any defender can reverse-engineer a patch.
For enterprise vulnerability management and risk management teams, this incident is a code-red scenario. It demands a response that goes far beyond a standard patch cycle.
Security and risk practitioners must now execute a comprehensive, multi-phased response. The details below will guide your organization through this process:
- Inventory All F5 Assets (Immediately): You cannot protect what you don’t know you have. Initiate an exhaustive inventory of all F5 instances, including physical appliances, Virtual Editions (VEs), and cloud-native deployments.
- Execute an Aggressive Patching Strategy (Now): F5 released a massive quarterly patch bundle (K000156572) with 44 new CVEs (27 High, 16 Medium, and 1 Low CVEs). This release was likely accelerated to close the exact windows of opportunity the stolen data revealed. All critical, internet-facing devices must be patched immediately, followed by all other in-scope devices.
- Harden the Management Plane (Top Priority): The most dangerous misconfiguration is an internet-facing management interface. Any BIG-IP management plane (TMUI or SSH) accessible from the public internet must be disconnected or firewalled off immediately.
Patching and mitigating known flaws is just the beginning. A deeper investigation is required, starting with a comprehensive configuration audit. Teams must validate settings using tools like F5’s iHealth, and ensure critical controls, such as “port lockdown,” are enforced on self-IPs. Concurrently, organizations must assume compromise and launch a proactive threat hunt, such as identifying malicious outbound connections from the BIG-IP to internal servers, anomalous admin accounts, and unauthorized configuration changes.
The Risk-Velocity Mismatch: F5 Patching Decelerates as Attacker Insight Accelerates
At the Qualys Threat Research Unit, we analyzed vulnerability data for six critical, weaponized CVEs related to F5 Big-IP. These include the most impactful F5 KEV vulnerabilities now treated as confirmed exploit risk. We looked into their vulnerability lifecycle events across enterprise environments, drawing on data from tens of thousands of detections. What our data showed was a chronic, concerning problem: organizations are getting slower at patching these critical F5 appliances.
This creates a significant risk-velocity mismatch. The long-known F5 BIG-IP vulnerabilities that remained unpatched became amplified by the adversary’s time-to-weaponize advantage. The attacker’s time-to-weaponize has shrunk from months (for a typical public CVE) to hours or days (using stolen source code). Our data shows that the industry’s response velocity is lagging significantly behind this new threat velocity. This unpatched population of devices represents a persistent and exploitable attack surface. Adversaries are aware that these assets are difficult to patch and can now leverage their knowledge from the stolen data to target them more effectively.
The new 44-CVE bundle (K000156572) is not a routine patch cycle; it’s an urgent containment effort. Because this bundle was released to close the exact windows of opportunity revealed by the stolen data, all 44 of these CVEs must be treated with the same urgency as actively known flaws. These are the vulnerabilities that the adversary already has deep insight into.
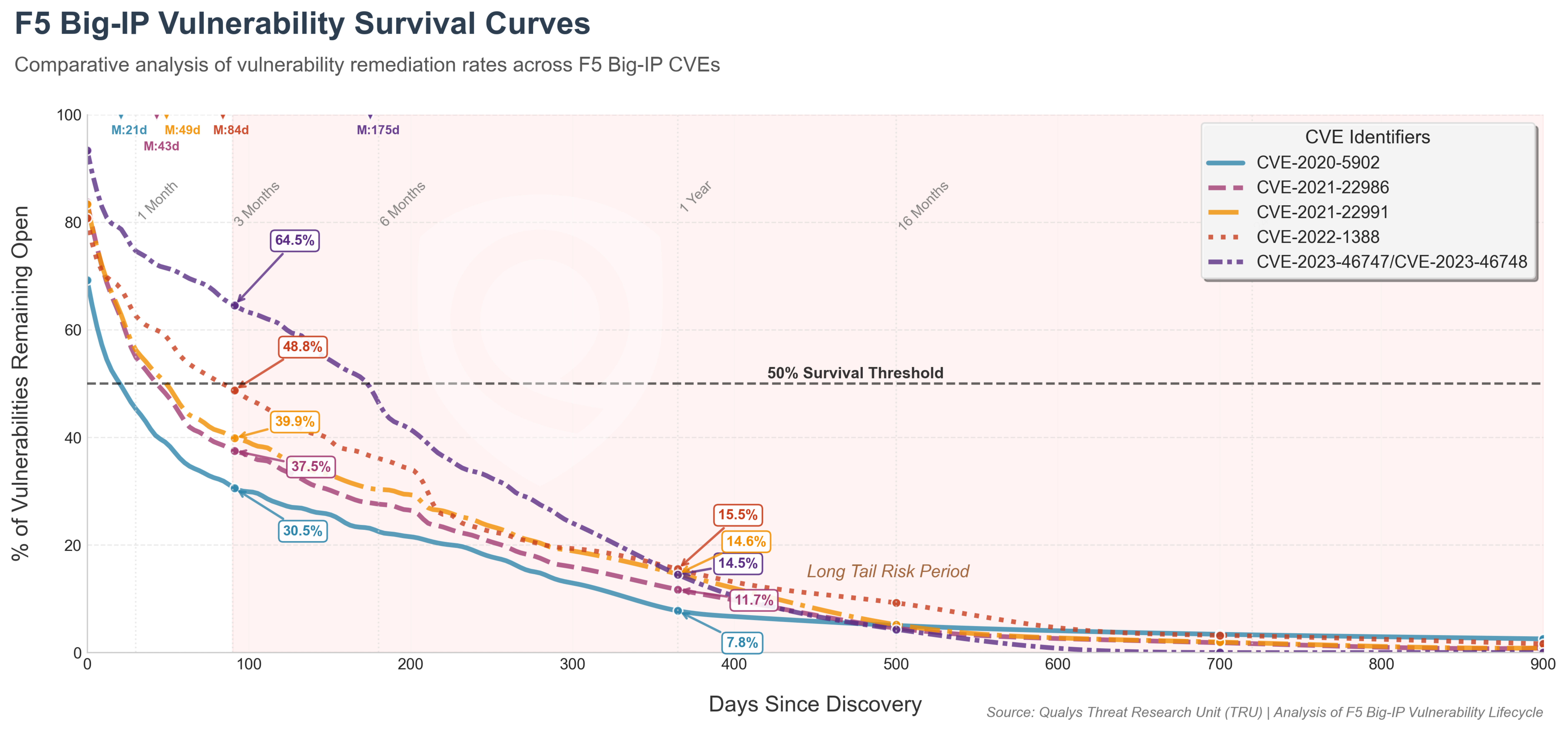
Analyzing remediation history back to 2020 is essential for two critical insights. First, CVE-2020-5902 establishes our ‘best-case’ patching baseline (a 21-day median), which is necessary to prove the subsequent trend. More importantly, these vulnerabilities define the ‘long-tail risk.’ Any asset still unpatched against these old, known flaws represents the most severe risk—these are the proven, neglected, and hard to patch devices that attackers, now armed with stolen source code, will target with precision.
Our data shows a consistent deceleration in patching speed for these critical and weaponized vulnerabilities over the past five years. The median survival time (the time it takes for 50% of organizations to patch), marked by the triangle indicators at the chart’s top, has increased from 21 days (CVE-2020-5902) to 175 days (CVE-2023-46748).
This trend appears to be specific to F5 Big-IP, a critical network-edge appliance, rather than a general market-wide issue. This suggests that patching these particular devices is becoming increasingly complex, possibly due to operational complexity, concerns about service disruption, and challenges in asset visibility.
We are also seeing a substantial and growing long-tail risk period. Looking at the 12-month (365-day) mark, 7.8% to 15.5% of these vulnerable instances remain unpatched. It’s highly recommended to triage by mitigation if patching is not an immediate option. As a viable action, execute compensating controls, like hardening the management plane, before attempting to patch. To that end, the Qualys Threat Research Unit is actively monitoring the remediation of the new 44-CVE bundle. Stay tuned, as we will release our initial survival curve analysis for this latest patch cycle in the coming weeks to share the most current data on these patch rates.
This represents a persistent population of devices that are challenging to remediate and require a different strategy beyond simple scanning and reporting. That is precisely the problem the Risk Operations Center (ROC) is designed to solve. The ROC isn’t another tool to find more vulnerabilities; it’s an engine to provide the context and risk-based prioritization to finally escape this chaos.
How Qualys Helps You Discover F5 Assets and Detect Related Vulnerabilities
Discover F5 Assets Using Qualys CyberSecurity Asset Management (CSAM)
The first step in addressing this critical vulnerability is to gain complete visibility into all F5 vulnerabilities across your infrastructure. Using Qualys CyberSecurity Asset Management (CSAM) 3.0, integrated with External Attack Surface Management (EASM), organizations can automatically discover every exposed F5 instance.
CSAM not only identifies where these assets reside but also highlights end-of-life (EoL) or end-of-support (EoS) versions, ensuring security teams can prioritize the highest-risk systems for remediation. By combining CSAM’s real-time asset discovery with Qualys Vulnerability Management, Detection, and Response (VMDR), you can quickly detect, assess, and mitigate F5-related vulnerabilities before they can be exploited.
Free Trial
Identify internet-facing instances with vulnerable versions of F5 Big-IP
In the following example, we aim to identify all F5 BIG-IP assets:
operatingSystem:"F5 BIG-IP" and hardware.manufacturer:`F5`
In the following example, we aim to identify assets with OS version greater than 12:
operatingSystem.version>12 and operatingSystem.publisher:`F5`

Enhance Your Security Posture with Qualys Vulnerability Management, Detection, and Response (VMDR)
Qualys VMDR offers comprehensive coverage and visibility into vulnerabilities, empowering organizations to rapidly respond to, prioritize, and mitigate the associated risks.
Qualys has released detections for the CVEs published by F5. All QIDs require authenticated remote scanning. For more details about the vulnerable versions, please refer to our threatprotect post.
Leverage the power of Qualys VMDR alongside TruRisk and the Qualys Query Language (QQL) to efficiently identify and prioritize vulnerable assets, effectively addressing the vulnerabilities highlighted above.
Query for all CVEs, use this QQL statement:
vulnerabilities.vulnerability.cveIds:[CVE-2025-58474, CVE-2025-55036, CVE-2025-61938, CVE-2025-41430, CVE-2025-53474, CVE-2025-59268, CVE-2025-59269, CVE-2025-47148, CVE-2025-59478, CVE-2025-60016, CVE-2025-58153, CVE-2025-48008, CVE-2025-55669, CVE-2025-46706, CVE-2025-59781, CVE-2025-58424, CVE-2025-54479, CVE-2025-53856, CVE-2025-61951, CVE-2025-61935, CVE-2025-58071, CVE-2025-53868, CVE-2025-54858, CVE-2025-58096, CVE-2025-53521, CVE-2025-61958, CVE-2025-61933, CVE-2025-54854, CVE-2025-61960, CVE-2025-59481, CVE-2025-61974, CVE-2025-59483, CVE-2025-54755, CVE-2025-61990]
Alternatively, you can query for all associated QIDs:
vulnerabilities.vulnerability.qid:[385574, 385571, 385573, 385572, 385544, 385543, 385560, 385562, 385556, 385567, 385548, 385561, 385540, 385547, 385566, 385555, 385541, 385568, 385559, 385550, 385553, 385552, 385563, 385557, 385564, 385542, 385558, 385554, 385545, 385565, 385551, 385569, 385549, 385546]

Strengthen Configuration Security with Qualys Policy Audit
In incidents like the October 2025 F5 BIG-IP breach, configuration assurance plays a pivotal role in reducing risk exposure. Qualys Policy Audit helps organizations continuously validate that critical infrastructure, including F5 BIG-IP systems, is securely configured and aligned with officially recommended mitigations and workarounds by F5.
The platform provides dedicated configuration controls (CIDs) to assess compliance posture across a wide range of technologies, including those affected by the latest F5 vulnerabilities. These controls perform technically feasible checks mapped to relevant CVEs, verifying that configurations adhere to secure baselines and compensatory settings defined in official vendor guidance.
Within the Qualys Posture view, security teams can easily:
- Evaluate compliance against configuration benchmarks
- Identify and prioritize misconfigurations associated with high-risk CVEs
- Track remediation progress and confirm that applied fixes remain effective over time
Policies such as “Compensatory Controls for October 2025 F5 BIG-IP Exploited Vulnerabilities” illustrate how Qualys enables organizations to operationalize mitigation guidance through measurable controls.
The following table provides an example of CVE-to-Control (CID) mappings that support compliance validation for affected systems:
| CVE ID | Control |
| CVE-2025-60016 | 31220 |
| CVE-2025-48008 | 31224, 31225, 31226 |
| CVE-2025-59781 | 31224, 31225, 31226 |
| CVE-2025-41430 | 31224, 31225, 31226 |
| CVE-2025-55669 | 31224, 31225, 31226 |
| CVE-2025-61951 | 31221, 31224, 31225, 31226 |
| CVE-2025-54479 | 31224, 31225, 31226 |
| CVE-2025-59478 | 31224, 31225, 31226 |
| CVE-2025-54858 | 31224, 31225, 31226 |
| CVE-2025-53856 | 31224, 31225, 31226 |
| CVE-2025-61974 | 31224, 31225, 31226 |
| CVE-2025-58071 | 31224, 31225, 31226 |
| CVE-2025-53521 | 31224, 31225, 31226 |
| CVE-2025-61960 | 31224, 31225, 31226 |
| CVE-2025-54854 | 31224, 31225, 31226 |
| CVE-2025-53474 | 31224, 31225, 31226 |
| CVE-2025-58096 | 31222 |
| CVE-2025-61935 | 31224, 31225, 31226 |
| CVE-2025-59481 | 18835, 13903, 14251,31224, 31225, 31226 |
| CVE-2025-61958 | 18835, 14251 |
| CVE-2025-47148 | 31224, 31225, 31226 |
| CVE-2025-59269 | 13903, 14251 |
| CVE-2025-58153 | 22392 |
| CVE-2025-59268 | 18835, 13903, 14251 |
| CVE-2025-58424 | 31223 |
Users can view compliance results by navigating to the Posture tab within Qualys Policy Audit and applying a query such as:
policy.name:"Compensatory Controls for October 2025 F5 BIG-IP Exploited Vulnerabilities"
This helps teams maintain visibility across critical assets, ensuring configurations remain resilient against exploitation and aligned with evolving security best practices.
Conclusion
The F5 BIG-IP breach is a stark reminder that in our interconnected ecosystem, your security is inextricably linked to the security of your critical suppliers. This incident is a clear and present danger that demands a response far beyond a typical patch cycle.
An effective defense requires a holistic program, which is impossible without a foundation of strong asset management, threat intelligence, and risk-based prioritization. This foundation is what guides a focused response, enabling immediate tactical remediation to patch, harden, and decommission your most critical assets first, followed by thorough configuration audits and proactive threat hunting to address hidden risks.
Get started with Qualys solutions today.