What Security Teams Need to Know as PHP and IoT Exploits Surge
Table of Contents
- PHP Servers Are the Top Target for Vulnerabilities and Misconfigurations
- PHP Exploitation Trends and Noteworthy CVEs
- The Dangers of Exposed Secrets and Credentials
- IOT Devices Remain a Weak Link in Security
- MVPower DVR Shell Unauthenticated Command Execution
- Cloud Vulnerabilities: CVE-2022-22947
- Threat Actors Exploit Cloud Resources for Reconnaissance
- 5 Best Practices to Reduce Exploitation Risk
- Building Resilience with Integrated Security
Attack automation is accelerating, widening the window between detection and response. Qualys TRU telemetry reveals how these attacks unfold and what defenders can do next.
The Qualys Threat Research Unit (TRU) has identified a sharp increase in attacks targeting PHP servers, IoT devices, and cloud gateways, primarily driven by botnets such as Mirai, Gafgyt, and Mozi. These automated campaigns exploit known CVE vulnerabilities and cloud misconfigurations to gain control over exposed systems and expand botnet networks.
With PHP powering more than 73% of websites and 82% of enterprises reporting incidents linked to cloud misconfigurations, the modern attack surface has never been broader. This blog explores the latest exploitation trends, highlights vulnerabilities and misconfigurations actively under attack, and outlines actionable steps security teams can take to strengthen defenses and minimize exposure.
PHP Servers Are the Top Target for Vulnerabilities and Misconfigurations
PHP remains a foundational component for websites and web applications, especially within popular content management systems (CMS) like WordPress. However, this ubiquity also creates a large and attractive attack surface. Many PHP deployments suffer from:
- Outdated versions and plugins
- Misconfigured file permissions
- Debugging components left enabled in production
- Insecure file storage
These gaps allow threat actors to launch remote code execution (RCE) attacks, exfiltrate data, or turn the server into a launchpad for malware. Left unaddressed, even a single misconfigured or outdated PHP instance can become the entry point for a large-scale compromise. For example, earlier this year hundreds of websites were compromised due to a zero-day vulnerability in the PHP-based Craft CMS.
PHP Exploitation Trends and Noteworthy CVEs
Attackers are constantly scanning for weaknesses in popular PHP frameworks and development tools. Here are a few examples of how critical vulnerabilities and insecure configurations continue to provide entry points for RCE and data compromise.
CVE-2022-47945: Remote Code Execution in ThinkPHP Framework
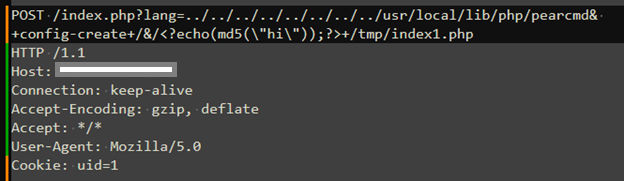
CVE-2022-47945 is a critical RCE vulnerability in ThinkPHP versions before 6.0.14, affecting applications with multi-language support enabled (lang_switch_on = true). The flaw lies in improper input sanitization of the lang parameter, which attackers exploit to perform Local File Inclusion (LFI) of sensitive internal scripts, such as:
/vendor/pear/pearcmd.php
/usr/local/lib/php/pearcmd
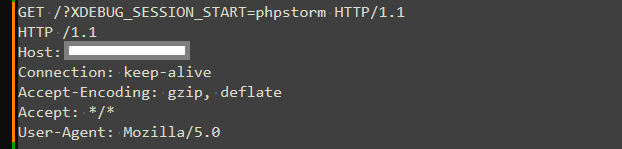
Remote Debugging using XDEBUG in PHPStorm
Qualys researchers have observed exploitation attempts where attackers use the ?XDEBUG_SESSION_START=phpstorm query string to initiate a remote debugging session with the XDebug plugin in combination with an integrated development environment (IDE), typically PHPStorm. If XDebug is unintentionally left active in production environments, attackers may use these sessions to gain insight into application behavior or extract sensitive data.
CVE-2021-3129: Remote Code Execution (RCE) Vulnerability in Laravel
CVE-2021-3129 is an RCE vulnerability that affects Laravel applications when the Ignition debugging package is exposed in production environments. Laravel Ignition exposes the route /_ignition/execute-solution in debug mode, which is used by developers to execute helper commands for fixing errors. If this feature is left enabled in production, it can be exploited by attackers to execute arbitrary code.
The following is one of the snippets from a network packet where attackers are trying to exploit CVE-2021-3129. Malicious command is base64 encoded in the subsequent HTTP request packet.
CVE-2017-9841: PHPUnit RCE
This long-standing vulnerability resides in PHPUnit, a widely used testing framework in PHP applications. The flaw stems from the presence of the vulnerable “eval-stdin.php” script in older PHPUnit versions, allowing unauthenticated attackers to execute arbitrary PHP code remotely. This vulnerability is often exploited in misconfigured production environments where development tools are unintentionally exposed to the internet.
HTTP Request URLs often seen in scanning include:
/api/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/app/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/apps/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/backup/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/blog/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/cms/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/crm/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/demo/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/laravel/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/lib/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/lib/phpunit/phpunit/Util/PHP/eval-stdin.php
/lib/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/panel/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/public/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/test/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/testing/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/tests/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/V2/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/vendor/phpunit/phpunit/LICENSE/eval-stdin.php
/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/vendor/phpunit/phpunit/Util/PHP/eval-stdin.php
/vendor/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/workspace/drupal/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/ws/ec/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/ws/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/www/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/yii/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
/zend/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
The Dangers of Exposed Secrets and Credentials
Insecurely stored secrets like credentials, API keys, and access tokens exposed to the internet are one of the most common and dangerous misconfigurations found on servers. Whether left behind during the transition from development to production or accidentally persisted in a deployment, secrets in plaintext files can lead to full compromise of cloud infrastructure. Attackers actively look for these plaintext files during initial recon andpost-exploitation.
The Qualys TRU has identified ongoing attempts by attackers to access sensitive Amazon Web Services (AWS) credential files on exposed or misconfigured Linux servers. Frequently targeted file paths include:
/.aws/credentials
/aws/credentials
/home/ec2-user/.aws/credentials
/credentials
/.aws/ecs-task-credentials
/.aws/ecs-task-credentials.json
/.aws/metadata/iam/security-credentials/
/.aws_creds.json
/.db_credentials
/.smtp-credentials
/.well-known/credentials.json
/admin/config?cmd=cat+/root/.aws/credentials
/api/aws/credentials
/api/v1/aws/credentials
/api/v1/credentials
/aws/credentials.json
/aws/ecs/task-credentials
/aws/ecs/task-credentials.json
/aws/iam/credentials.json
/aws/iam/ecs-task-credentials.json
/aws/iam/temp-creds.json
/aws/iam/temporary-credentials
/aws/metadata/iam/security-credentials
/aws/metadata/iam/security-credentials/
/aws/s3/credentials.bak
/aws/s3/credentials.json
/aws/s3/credentials.yml
/aws_credentials.txt
/aws_creds.js
/data/aws/credentials
/ecs/task-credentials
/ecs/task-credentials.json
/email/credentials.json
/hidden/.aws/credentials
/internal-api/aws/credentials
/internal-api/iam/credentials
/internal/aws/credentials
/k8s/eks/credentials
/latest/meta-data/iam/security-credentials/
/pms?module=logging&file_name=../../../../../../~/.aws/credentials&number_of_lines=10000
/private/aws_credentials.json
/public/.aws/credentials
/s3-credentials.bak
/s3-credentials.json
/s3/.aws/credentials
/s3/public/credentials
/tmp/.aws/credentials
/vendor/.aws/credentials
/vendor/aws/credentials
IOT Devices Remain a Weak Link in Security
Threat actors also continue to leverage insecure or legacy IoT devices. These systems often use outdated firmware, insecure protocols, and hardcoded credentials, creating a perfect storm for exploitation.
CVE-2024-3721: TBK DVR Command Injection
CVE-2024-3721 is a critical command injection vulnerability, stemming from insecure firmware logic, that affects TBK DVR-4104 and DVR-4216 devices and is actively exploited by Mirai-like botnets. The issue stems from unsanitized [mdb/mdc] parameters in HTTP requests, allowing unauthenticated command injection.
Here is a snippet from an exploitation attempt by an attacker:
Successful exploitation leads to the download and execution of the malicious script selftbk.sh file. This shell script acts as a dropper, downloading and executing a variant of the Mirai botnet malware, tailored for the target’s CPU architecture (e.g., ARM7). Once executed, the infected DVR becomes part of a botnet, capable of launching DDoS attacks, scanning for other vulnerable devices, and persisting within IoT infrastructure.
MVPower DVR Shell Unauthenticated Command Execution
Another recurring target is the MVPower TV-7104HE DVR, which contains a built-in backdoor that allows unauthenticated users to execute arbitrary system commands via an HTTP GET request. Though more of a misconfiguration than a vulnerability, we have observed it is actively targeted by Mirai variants. Following is a snippet from apacket capture where the Mirai Botnet is trying to execute a command on the remote system by exploiting this vulnerability.
Cloud Vulnerabilities: CVE-2022-22947
Cloud-native environments are also being targeted through exposed APIs and misconfigured services, with attackers quick to weaponize known flaws. One example is CVE-2022-22947, a critical RCE vulnerability in the Spring Cloud Gateway that allows unauthenticated attackers to execute arbitrary code via a maliciously crafted request to the /actuator/refresh endpoint.
Threat Actors Exploit Cloud Resources for Reconnaissance
Upon analyzing the source IPs involved in recent scanning activity, it was observed that a significant number of scans originated from cloud infrastructure providers. These include prominent services such as AWS, Google Cloud Platform (GCP), Microsoft Azure, Digital Ocean, and Akamai Cloud, among others.
This pattern aligns with how threat actors often abuse cloud resources, using cheap, temporary, or compromised computer instances to conduct reconnaissance and exploit attempts while masking their real origin. Large portions of this scanning activity appear to be tied to active vulnerability exploitation, such as attempts targeting PHP, ThinkPHP, DVR devices, Laravel, Spring Cloud Gateway servers, SSH brute-force attacks, misconfigurations, and secrets exposure.
According to the Qualys TRU research, the top autonomous system number (ASN) organizations by total number of scanning source IPs are:
| ASN Organization | Number of IP Addresses |
| GOOGLE-CLOUD-PLATFORM | 2373 |
| MICROSOFT-CORP-MSN-AS-BLOCK | 1725 |
| Akamai Connected Cloud | 1575 |
| DIGITALOCEAN-ASN | 1403 |
| HURRICANE | 943 |
| CHINA UNICOM China169 Backbone | 934 |
| Chinanet | 848 |
| AMAZON-02 | 666 |
| Alibaba US Technology Co., Ltd. | 589 |
| ONYPHE SAS | 550 |
| UCLOUD INFORMATION TECHNOLOGY HK LIMITED | 538 |
| CENSYS-ARIN-01 | 451 |
| Korea Telecom | 394 |
| AMAZON-AES | 387 |
| TOT Public Company Limited | 344 |
| Driftnet Ltd | 322 |
| CHEAPY-HOST | 189 |
This illustrates how easily attackers can operationalize scanning at scale, obscuring their origin by rapidly spinning up short-lived virtual machines (VMs) across providers like AWS and GCP before abandoning them and repeating the cycle. This tactic makes attribution difficult, as the traffic appears to come from trusted cloud infrastructure.
5 Best Practices to Reduce Exploitation Risk
Reducing the risks highlighted above requires a layered defense strategy that enhances visibility, limits exposure, and prioritizes remediation in the most critical areas of your environment.
Here are a few best practices that can help security teams stay ahead of these evolving threats:
- Ensure timely updates and patching: Regularly update all software dependencies, libraries, and frameworks. Monitor vendor advisory channels for new CVEs. For containerized environments, always rebuild images with the latest base and application versions.
- Remove development and debug tools in production: Many of the exploited vulnerabilities exist because dev-debug components are deployed in production. Always make sure that these components are disabled in production.
- Protect sensitive files and secrets: Do not store secrets in plaintext files; instead, use a managed store like AWS Secrets Manager or HashiCorp Vault. It’s also important to regularly audit servers and containers for hardcoded secrets.
- Harden network exposure: Allow only necessary IPs to access your cloud infrastructure. Restrict public access to debug ports, IoT device shells, and internal file paths.
- Secure cloud access and controls: Use security groups to tightly restrict port and IP access. Monitor cloud access logs for IAM misuse or secret scanning attempts.
Building Resilience with Integrated Security
Today’s threat actors don’t need to be highly sophisticated to be effective. With widely available exploit kits, botnet frameworks, and scanning tools, even entry-level attackers can cause significant damage.
By combining visibility, automation, and risk-based prioritization, the Qualys platform empowers organizations to:
- Maintain visibility into internet-facing assets (e.g., PHP servers and IoT devices)
- Detect and remediate misconfigurations in real time
- Eliminate known vulnerabilities before attackers weaponize them
- Protect cloud and on-premises infrastructure with continuous assessment
See what’s next in threat intelligence. Stay informed with new findings from the Qualys Threat Research.