Microsoft and Adobe Patch Tuesday, February 2026 Security Update Review
Table of Contents
- Microsoft Patch Tuesday forFebruary2026
- Adobe Patches for February 2026
- Zero-day Vulnerabilities Patched inFebruaryPatch Tuesday Edition
- Critical Severity Vulnerabilities Patched inFebruaryPatch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities inVulnerability Management, Detection & Response (VMDR)
- Rapid Response with TruRisk Eliminate
- Qualys Monthly Webinar Series
Microsoft’s February 2026 Patch Tuesday focuses on closing security gaps that attackers could exploit, reinforcing the importance of timely patching in enterprise environments. Here’s a quick breakdown of what you need to know.
Microsoft Patch Tuesday for February 2026
This month’s release addresses 61 vulnerabilities, including five critical and 52 important-severity vulnerabilities.
In this month’s updates, Microsoft has addressed six zero-day vulnerabilities that have been exploited in the wild.
Microsoft addressed one vulnerability in Microsoft Edge (Chromium-based) that was patched earlier this month.
Microsoft Patch Tuesday, February edition, includes updates for vulnerabilities in Microsoft Exchange Server, Microsoft Graphics Component, Windows NTLM, Windows Remote Access Connection Manager, Windows Remote Desktop, and more.
From elevation of privilege flaws to remote code execution risks, this month’s patches are essential for organizations aiming to maintain a robust security posture.
The February 2026 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
| Spoofing Vulnerability | 7 | Important: 6 |
| Denial of Service Vulnerability | 3 | Important: 3 |
| Elevation of Privilege Vulnerability | 25 | Critical: 3 Important: 22 |
| Information Disclosure Vulnerability | 6 | Critical: 2 Important: 4 |
| Remote Code Execution Vulnerability | 12 | Important: 12 |
| Security Feature Bypass Vulnerability | 5 | Important: 5 |
Adobe Patches for February 2026
Adobe has released nine security advisories to address 44 vulnerabilities in Adobe Audition, Adobe After Effects, Adobe InDesign Desktop, Adobe Substance 3D Designer, Adobe Substance 3D Stager, Adobe Bridge, Adobe Substance 3D Modeler, Adobe Lightroom Classic, and Adobe DNG SDK. 27 of these vulnerabilities are given critical severity ratings. Successful exploitation of these vulnerabilities may lead to arbitrary code execution.
Zero-day Vulnerabilities Patched in February Patch Tuesday Edition
CVE-2026-21519: Desktop Windows Manager Elevation of Privilege Vulnerability
Desktop Window Manager is a system service in Windows (Vista and later) that enables visual effects such as transparency, window animations, and live taskbar thumbnails via GPU hardware acceleration.
A type confusion flaw in the Desktop Window Manager may allow an authenticated attacker to elevate privileges locally. Successful exploitation of the vulnerability may allow an attacker to gain SYSTEM privileges.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before March 3, 2026.
CVE-2026-21533: Windows Remote Desktop Services Elevation of Privilege Vulnerability
Windows Remote Desktop Services (RDS) is a Microsoft Windows Server technology that allows users to securely access virtualized desktops, applications, and resources from any device, anywhere.
An improper privilege management flaw in Windows Remote Desktop could allow an authenticated attacker to elevate privileges locally. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before March 3, 2026.
CVE-2026-21510: Windows Shell Security Feature Bypass Vulnerability
The Windows Shell is the primary interface for users to interact with the Windows operating system, encompassing visible elements like the Desktop, Taskbar, and Start Menu.
A failure in the Windows Shell protection mechanism may allow an unauthenticated attacker to bypass a network security feature. An attacker must convince a user to open a malicious link or shortcut file to exploit the vulnerability.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before March 3, 2026.
CVE-2026-21514: Microsoft Word Security Feature Bypass Vulnerability
An attacker must send a user a malicious Office file and convince them to open it to exploit the vulnerability.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before March 3, 2026.
CVE-2026-21525: Windows Remote Access Connection Manager Denial of Service Vulnerability
Windows Remote Access Connection Manager is a core Windows service that manages dial-up and Virtual Private Network connections, allowing user computers to securely connect to remote networks, corporate resources, or other devices.
A null pointer dereference in Windows Remote Access Connection Manager could allow an unauthenticated attacker to deny service locally.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before March 3, 2026.
CVE-2026-21513: MSHTML Framework Security Feature Bypass Vulnerability
The MSHTML Framework (also known as Trident) is a proprietary browser engine developed by Microsoft. It is a software component that renders web pages and other HTML content within applications running on Microsoft Windows.
A failure in the MSHTML Framework protection mechanism could allow an unauthenticated attacker to bypass a security feature over a network.
CISA acknowledged the active exploitation of the vulnerability by adding it to its Known Exploited Vulnerabilities Catalog. CISA urges users to patch the vulnerability before March 3, 2026.

Critical Severity Vulnerabilities Patched in February Patch Tuesday Edition
CVE-2026-24300: Azure Front Door Elevation of Privilege Vulnerability
Microsoft mentioned in the advisory, “This vulnerability has already been fully mitigated by Microsoft. There is no action for users of this service to take. The purpose of this CVE is to provide further transparency.”
CVE-2026-21522: Microsoft ACI Confidential Containers Elevation of Privilege Vulnerability
A command injection flaw in Azure Compute Gallery allows an authorized attacker to elevate privileges locally. Upon successful exploitation, an attacker could execute arbitrary commands within the affected ACI container’s context, thereby running code with the same privileges as the compromised container.
CVE-2026-23655: Microsoft ACI Confidential Containers Information Disclosure Vulnerability
Upon successful exploitation of the vulnerability, an attacker could disclose the secret tokens and keys.
CVE-2026-24302: Azure Arc Elevation of Privilege Vulnerability
As per the Microsoft advisory, “This vulnerability has already been fully mitigated by Microsoft. There is no action for users of this service to take. The purpose of this CVE is to provide further transparency.”
CVE-2026-21532: Azure Function Information Disclosure Vulnerability
As per the Microsoft advisory, “This vulnerability has already been fully mitigated by Microsoft. There is no action for users of this service to take. The purpose of this CVE is to provide further transparency.”

Other Microsoft Vulnerability Highlights
- CVE-2026-21511 is a spoofing vulnerability in Microsoft Outlook. Deserialization of untrusted data in Microsoft Office Outlook may allow an unauthenticated attacker to perform network spoofing.
- CVE-2026-21253 is an elevation of privilege vulnerability in the Mailslot File System. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.
- CVE-2026-21241 is an elevation of privilege vulnerability in the Windows Ancillary Function Driver for WinSock. Successful exploitation of the vulnerability may allow an authenticated attacker to gain SYSTEM privileges.
- CVE-2026-21238 is an elevation of privilege vulnerability in the Windows Ancillary Function Driver for WinSock. Successful exploitation of the vulnerability may allow an authenticated attacker to gain SYSTEM privileges.
- CVE-2026-21231 is an elevation of privilege vulnerability in the Windows Kernel. An attacker who successfully exploited this vulnerability could gain SYSTEM privileges.

Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions affected, including, but not limited to, Windows Win32K – GRFX, Microsoft Edge for Android, Windows Notepad App, Windows GDI+, .NET and Visual Studio, Windows Kernel, Azure Local, Power BI, Windows HTTP.sys, Windows Connected Devices Platform Service, Windows Ancillary Function Driver for WinSock, Windows Subsystem for Linux, Windows LDAP – Lightweight Directory Access Protocol, Role: Windows Hyper-V, Windows Cluster Client Failover, Mailslot File System, GitHub Copilot and Visual Studio, Microsoft Office Excel, Microsoft Office Word, Windows Storage, Windows Shell, Microsoft Office Outlook, Azure DevOps Server, Internet Explorer, Github Copilot, Windows App for Mac, .NET, Desktop Window Manager, Azure Compute Gallery, Azure IoT SDK, Azure HDInsights, Azure SDK, Azure Function, Microsoft Defender for Linux, Azure Front Door (AFD), Azure Arc, and Microsoft Edge (Chromium-based).
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
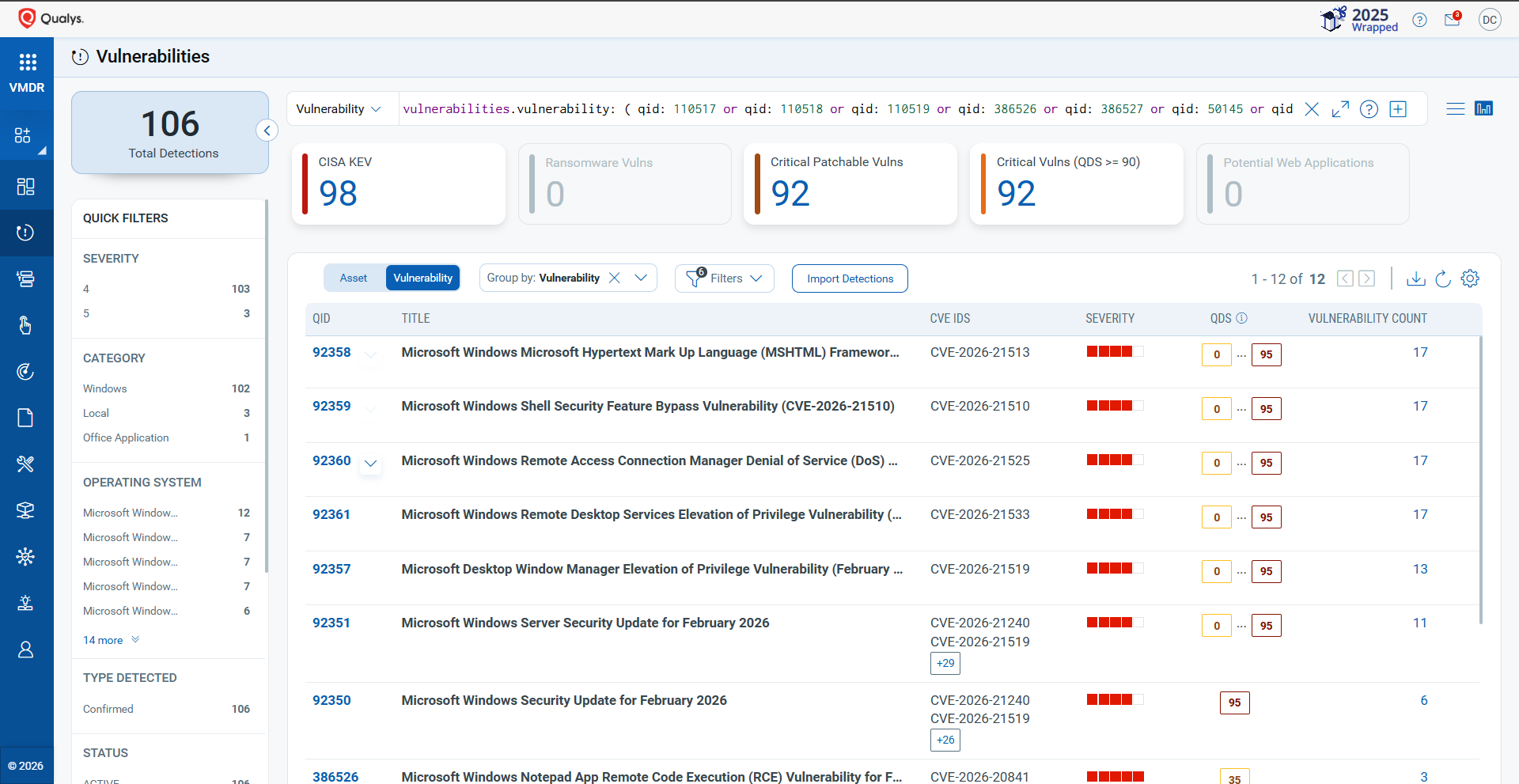
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid: 110517 or qid: 110518 or qid: 110519 or qid: 386526 or qid: 386527 or qid: 50145 or qid: 92350 or qid: 92351 or qid: 92352 or qid: 92353 or qid: 92354 or qid: 92355 or qid: 92356 or qid: 92357 or qid: 92358 or qid: 92359 or qid: 92360 or qid: 92361 )
Rapid Response with TruRisk™ Eliminate
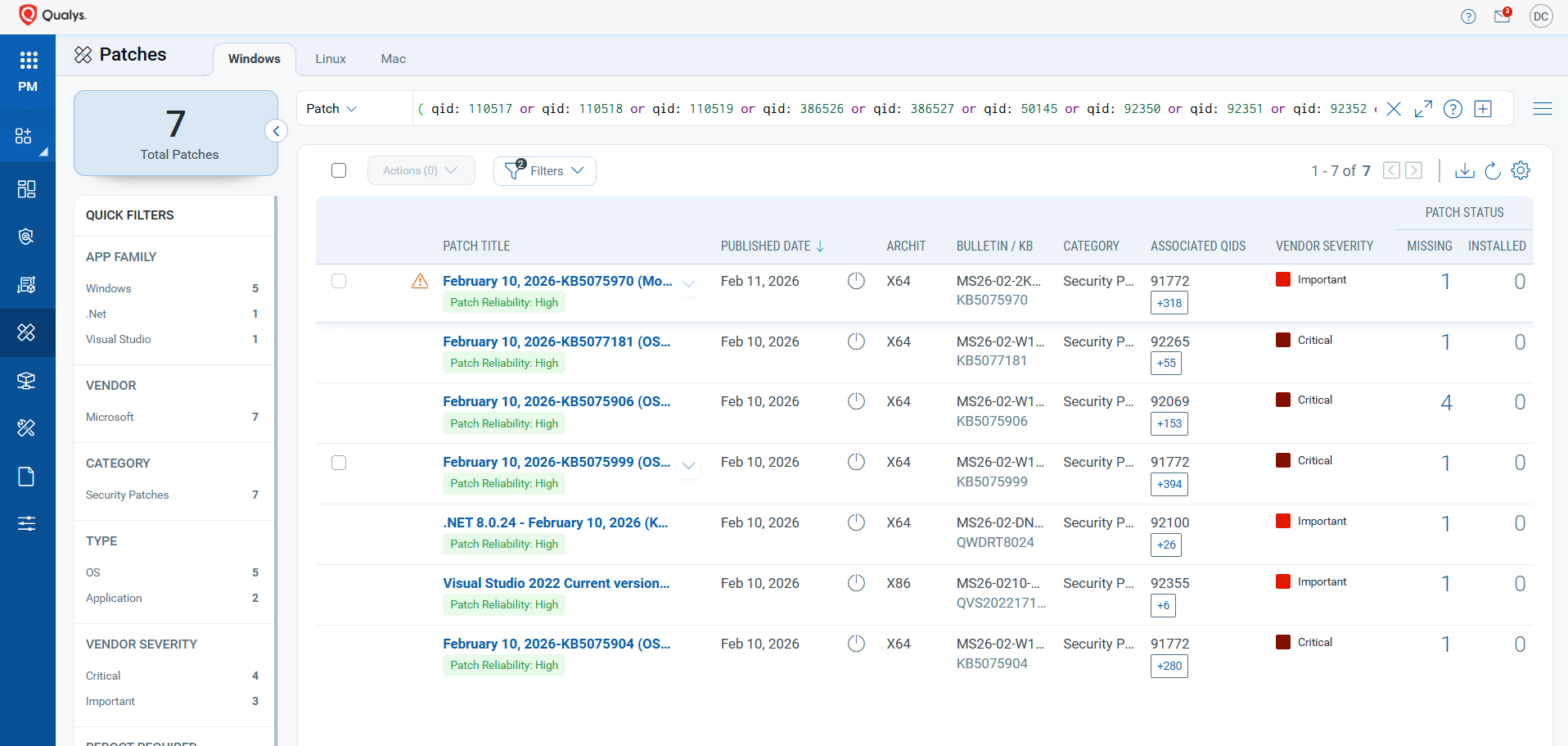
Patch to the Latest Version
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
( qid: 110517 or qid: 110518 or qid: 110519 or qid: 386526 or qid: 386527 or qid: 50145 or qid: 92350 or qid: 92351 or qid: 92352 or qid: 92353 or qid: 92354 or qid: 92355 or qid: 92356 or qid: 92357 or qid: 92358 or qid: 92359 or qid: 92360 or qid: 92361 )
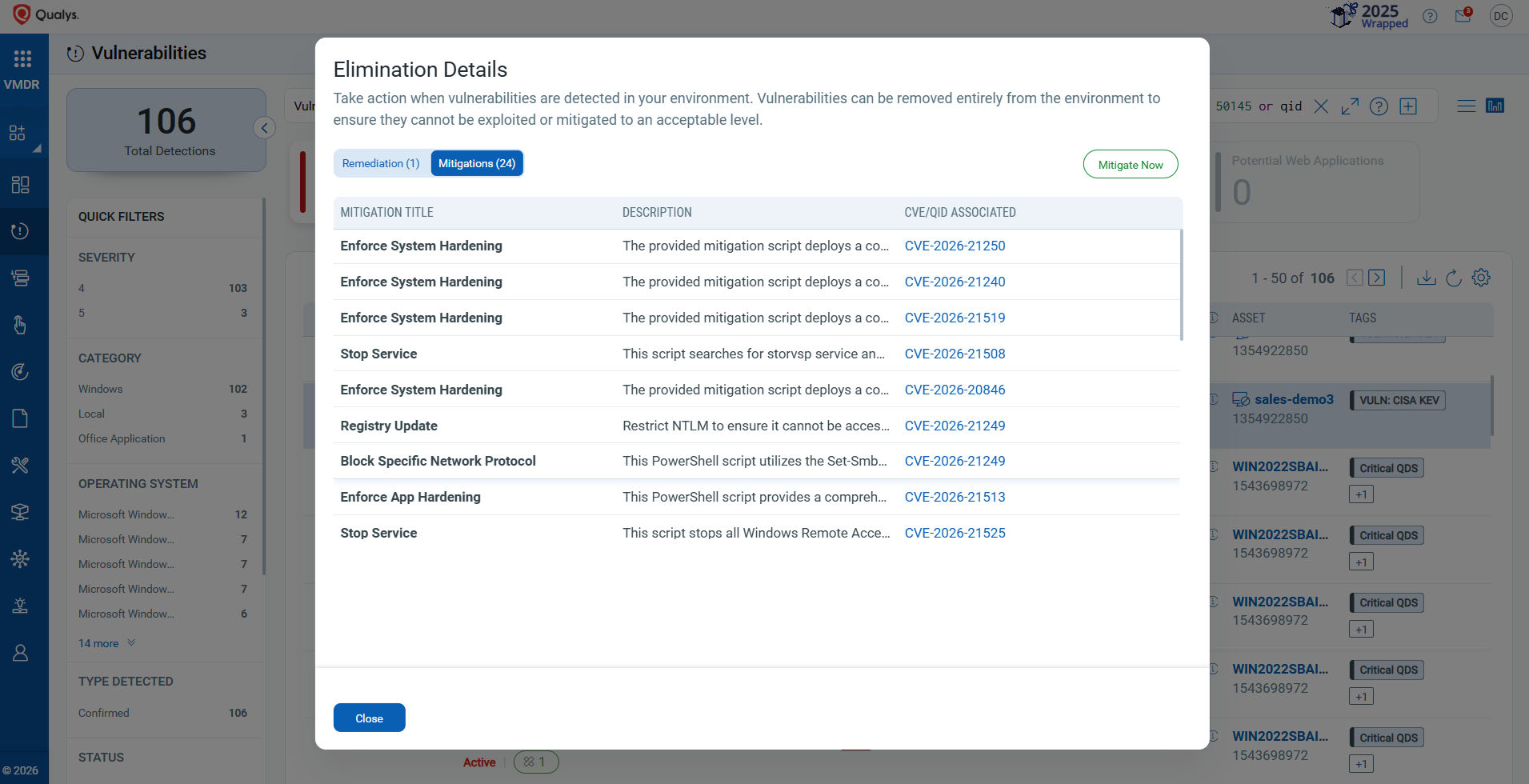
Mitigation: Reducing Risk Until Remediation
Not every team can patch immediately due to operational challenges. TruRisk™ Eliminate enables security teams to apply mitigation controls that immediately lower exposure and reduce the Qualys Detection Score (QDS).
As a first set of our mitigant signature set, we have Qualys-created mitigations for the following 34 vulnerabilities: CVE-2026-21249, CVE-2026-21525, CVE-2026-21533, CVE-2026-21510, CVE-2026-21508, CVE-2026-21237, CVE-2026-21234, CVE-2026-20846, CVE-2026-21232, CVE-2026-21240, CVE-2026-21250, CVE-2026-21222, CVE-2026-21239, CVE-2026-21245, CVE-2026-21254, CVE-2026-21231, CVE-2026-21243, CVE-2026-21513, CVE-2026-21253, CVE-2026-21537, CVE-2026-21527, CVE-2026-21246, CVE-2026-21235, CVE-2026-21261, CVE-2026-21259, CVE-2026-21258, CVE-2026-21511, CVE-2026-21514, CVE-2026-21260, CVE-2026-21229, CVE-2026-21244, CVE-2026-21255, CVE-2026-21247, and CVE-2026-21248.
For vulnerabilities in Windows services where local or remote exploitation vectors exist, our mitigants modify configuration by modifying registry keys and, where applicable, service policy files. These mitigations apply to affected components, including the Routing and Remote Access Service (RRAS), Capability Access Manager Services, Hyper-V, Microsoft SharePoint, Connected Devices Platform, Telephony API service, Windows Tablet Input services, Windows Wallet Service, and Client-Side Caching. Additionally, this mitigant set addresses denial-of-service, elevation-of-privilege, remote code execution, and information disclosure risks in these core Windows subsystems.
Qualys TruRisk Mitigate product customers receive these scripts as part of the monthly Patch Tuesday signature set.
The next Patch Tuesday is scheduled for March 10, and we will provide details and patch analysis at that time. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the ‘This Month in Vulnerabilities and Patches’ webinar.’
Qualys Monthly Webinar Series
The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management, Detection & Response (VMDR), and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those highlighted in this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches