March 2014 Patch Tuesday
Today Microsoft released the bulletins for March Patch Tuesday. We have five bulletins, MS14-012 to MS14-016, a light patch tuesday by all comparisons, even with Adobe chiming in with an update that is non-critical. If it wasn’t for the Internet Explorer (IE) patch that addresses the 0-day that was found during last month’s Patch Tuesday, one could call it almost uneventful.
Here is our lineup for today:
- MS14-012, a critical bulletin which addresses 18 vulnerabilities in all versions of IE, from IE6 on Windows XP, to IE11 on Windows 8.1. It also includes the fix for a 0-day vulnerability that was identified by FireEye on February 11, first on the website of the organization of the US Veterans of Foreign Wars. The attack used a previously unknown flaw in IE 10 (CVE-2014-0322), plus a known vulnerability in Adobe Flash to bypass ASLR protections and gave the attackers control over the computers visiting the site with that particular configuration. Microsoft has acknowledged the problem and provided a FixIT in KB2934088, but this is the permanent patch for the problem. Apply it as soon as possible.
- MS14-013, the second critical bulletin, addresses one critical vulnerability. The attack also uses the webpage vector, but rather than going against IE directly, involves the DirectShow Windows component. Microsoft states that exploitation is hard and gives it an exploitation index of 3, but you should give it priority in your patch cycle.
- The remaining bulletins, MS14-014, MS14-015 and MS14-016, are all rated important and do not provide Remote Code Execution (RCE) capabilities. MS14-014 is an ASLR bypass vulnerability that needs to be paired with a code execution vulnerability in order to become useful (see also the recent 0-day that used Adobe Flash exactly for that purpose). MS14-015 is a Windows Kernel driver fix addressing two CVEs, and MS14-016 is a change in the Windows API that allowed an attacker to bypass password shutout rules, which could be used in brute force attack attempts. Take a look at Microsoft SRD blog to see where ASLR fixes fit in overall.
- Adobe’s update to Flash (APSB14-08) addresses two vulnerabilities in Adobe Flash V12 and V11 on Windows, Mac OS X and Linux. Both are rated as important, meaning they cannot be used to gain remote code execution on the targeted platforms. Organizations that run Chrome or a modern version of IE will get their Flash update delivered through their browsers, others will need to update their software directly via Adobe.
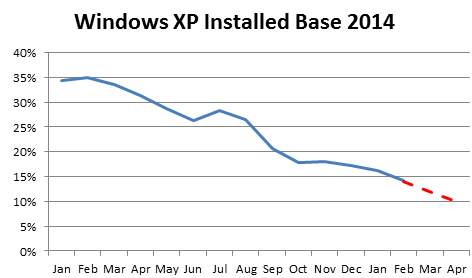
The other major Microsoft issue is the coming end-of-life of Windows XP. We are now less than 28 days away from the final set of patches that XP will receive. Nevertheless, we are not seeing a reduction in vulnerabilities. All of today’s bulletins apply to Windows XP and there is really no reason to expect any change in the near future: the majority of vulnerabilities found in the Windows OS and IE will apply also to Windows XP, but IT admins won’t have access to patches for these problems anymore. This will make any Windows XP machine an easy target for attackers, and within a few weeks, new tools will be developed that make these exploits widely available.Your best choice is to migrate away from Windows XP to a newer version of the operating system.
So far, you have done an incomplete job. In our latest survey of roughly 35 Million monthly scans, we are still seeing 14% of Windows XP machines, down from 16% In January and 17% in December of 2013. If that trend continues, we are projecting 10% by the end-of-life date, at least in the enterprise space that is covered by QualysGuard.
Two weeks ago at the RSA US 2014 conference in San Francisco Microsoft released a preview version of their EMET 5 (Enhanced Mitigation Experience Toolkit) security toolkit. EMET implements additional restrictions on Windows, monitoring programs for violations of policy and, optionally, shutting down the offending programs. It has been effective against all 0-day attacks of 2013 and 2014, starting with MS13-008, MS13-021, and MS13-038. In the known exploit against this month’s MS14-012, the attacker acknowledges that power and tests for the presence of EMET beforehand, proactively forfeiting when the EMET DLL is detected. I recommend IT admins to take a look at this toolkit and test its compatibility with their installations. The new EMET version 5 introduces a plugin whitelisting capability that could be a great asset in controlling browser plugins, for example only allowing Java to run on a controlled subset where the plugin is actually required.
That is it for this month’s bulletins, but stay tuned for more coverage about XP in the SMB and home market, plus a breakdown of the numbers that takes geography into account.