Patch Tuesday April 2014
Tuesday, April 8, 2014 – today Microsoft came out with the bulletins for April Patch Tuesday. It is a small release with only four bulletins, MS14-017 to MS14-020, a light patch Tuesday for the second month in a row.
But the Microsoft bulletin is not the most important item this month (even though MS14-017 fixes the current Word 0-day), but rather two other items: the new HeartBleed bug that impacts OpenSSL, and the arrival of Windows XP end of life. I will tackle each in turn:
Heartbleed
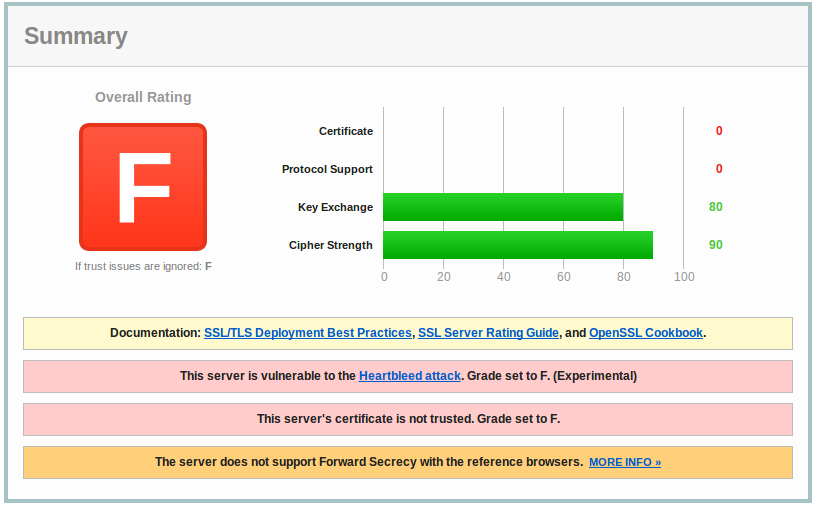
Yesterday a vulnerability in OpenSSL was disclosed that actually overshadows this Microsoft Patch Tuesday. The so-called “Heartbleed” vulnerability (CVE-2014-0160) is present in all recent OpenSSL versions and can be used to get information from the server that uses OpenSSL, for example, your web server. A remote attacker can get access to your private encryption key and would then be able to decipher the encrypted traffic to and from the website. A patch is available in OpenSSL 1.0.1g, alternatively one can recompile the OpenSSL version in use without the vulnerable “heartbeat” extension. Look to your Linux distro maintainer for updates. We have added the detection for the issue into SSLLabs and into QualysGuard, but stay tuned as we will be providing more information on affected distribution and products.
Windows XP End of Life
Windows XP first came to market in 2001 and was by all measures a tremendously successful operating system. It is fast, user friendly and intuitive. With the introduction of Service Pack 2 in 2004 several important security features were added, such as a default-on firewall (which severely curtailed the spread of network worms) and the Security Center, a one-stop shop for the security settings – firewall, automatic updates and AV protection. This year, after a 13 year run, it is “game over” for Windows XP. Microsoft has introduced 3 new operating systems since (Vista, Windows 7 and Windows 8) and all are better equipped than XP, at least as far as security is concerned.
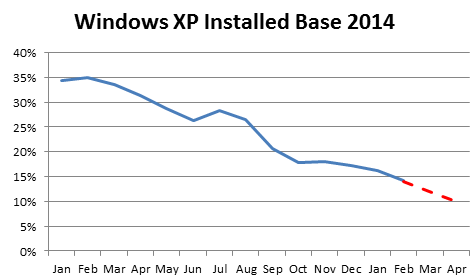
Not all of you have migrated away from Windows XP; our measurements show over 10% of you are still on XP, both in the Enterprise sector:
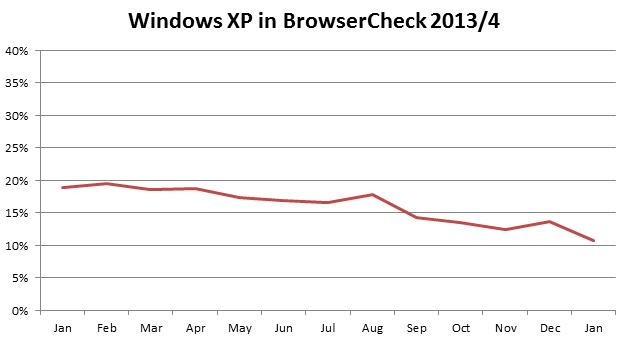
and also in the SMB/home sector (Qualys BrowserCheck users)
That is better than the 30% often quoted for general Internet users (admittedly Qualys users are probably more security-conscious than the average user), but is still a very unhealthy posture. I expect Windows XP defensibility to deteriorate quickly over the next few weeks and months as attackers will find ways to exploit certain aspects of the operating system, internet browser, mail programs, office software (Office 2003 is also EOL) and even third-party programs such your PDF reader (Adobe says they will not update Adobe Reader on XP anymore). There are certainly ways to harden the setup, including using a different browser and e-mail program, installing EMET (http://support.microsoft.com/kb/2458544) and implementing additional safeguards such as whitelisting, but the question remains: Isn’t this more work than upgrading to a fully supported system in the first place?
But let’s get back to our bulletins for today:
- MS14-017, the top bulletin, addresses 3 vulnerabilities in Microsoft Word, including the 0-day in the RTF (Rich Text Format) parser. The problem was first disclosed by Microsoft in KB2953095 on March 24, where Microsoft acknowledges the existence of exploits in the wild. Microsoft credits the Google Security team with the discovery. As a workaround Microsoft recommends disabling the opening of RTF files with Word, which can be automated with the provided FixIt MSI. The exploit has since been circulated widely and can be found on VirusTotal, meaning we are pretty close to a much wider usage by attackers. The attack vector is a self-contained RTF document that the user has to open with Microsoft Word, resulting in Remote Code Execution (RCE). Our recommendation: Patch Microsoft Word as quickly as possible.
- MS14-018, the second critical bulletin addresses six vulnerabilities in Internet Explorer (IE) and affects all versions from IE6 to IE11. Microsoft gives this bulletin an exploitability index rating of “1”, meaning that attacks can be expected with the next 30 days. The attack vector would be a malicious webpage that the user has to browse. Patch together with MS14-017.
- MS14-019 and MS14-020 are bulletins that cover Windows and Microsoft Publisher. Both provide Remote Code Execution to an attacker, but have lower viability than MS14-017 or MS14-018. The Windows vulnerability only works under very special conditions and Publisher in only sparsely installed and does not have any known exploits. Patch within your normal patch cycle.
Together with the detection for MS14-017 to MS14-020 we are also releasing two additional QIDs that “detect” the end-of-life status for both Windows XP and Office 2003:
- 105543 EOL/Obsolete Operating System: Microsoft Windows XP Detected
- 105544 EOL/Obsolete Software: Microsoft Office 2003 Detected
Adobe is releasing a new version of their Flash player in APSB14-09 which addresses four vulnerabilities, including one that was disclosed at the PWN2OWN contest last month. It is rated critical for Windows and Macintosh and should be high on your list to patch.