The February 2023 Patch Tuesday Security Update Review

Table of Contents
- Microsoft Patches for February2023
- Adobe Patches for February2023
- Notable and Critical Microsoft Vulnerabilities Patched
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response with Patch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- Qualys Monthly Webinar Series
- This Month in Vulnerabilities & Patches
Microsoft and Adobe have released several monthly security fixes and updates for their products. Let’s take a look at the highlights of this month’s Patch Tuesday as we review and discuss the security updates.
Microsoft Patches for February 2023
Microsoft has patched 79 vulnerabilities this month, including 3 Microsoft Edge-related vulnerabilities that were fixed earlier this month. Overall, the updates include fixes for vulnerabilities in Windows OS and its components, such as Microsoft Protected Extensible Authentication Protocol (PEAP) and Windows iSCSI Discovery Service; Microsoft Office and Office Components; Microsoft Dynamics; Microsoft Exchange Server; Microsoft SQL Server; .NET core; .NET framework; 3D Builder and Print 3D. Azure family products such as Azure DevOps, Azure Machine Learning, Azure App Service on Azure Stack Hub, Azure Data Box Gateway, and Azure Stack Edge have also received security fixes this month.
Out of the 79 vulnerabilities fixed this month, 9 are rated as critical, and 67 are rated as important. Additionally, Microsoft has confirmed that 3 vulnerabilities are known to be exploited in the wild. Also noteworthy is that even though Microsoft had mentioned last month that it would no longer provide Extended Support for Windows 7, Windows 2008 SP 2, and Windows 2008 R2, Microsoft has still released a fix to address a vulnerability in Windows 2008 SP 2 and Windows 2008 R2. Microsoft has mentioned that it will continue to offer Extended Security Updates for Windows 2008 SP2 and Windows 2008 R2 for customers on Azure who need additional time to upgrade to newer versions of Windows Server.
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The February 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Type | Quantity | Severities |
| Elevation of Privilege Vulnerability | 12 | Important: 12 |
| Remote Code Execution Vulnerability | 38 | Important: 29 Critical: 9 |
| Information Disclosure Vulnerability | 8 | Important: 8 |
| Security Feature Bypass Vulnerability | 2 | Important: 2 |
| Denial of Service Vulnerability | 10 | Important: 10 |
| Spoofing Vulnerability | 8 | Important: 8 |
Adobe Patches for February 2023
Adobe has released a total of 9 advisories for the month of February. The advisories cover a total of 34 vulnerabilities, out of which 19 are rated critical that affect Adobe After Effects (3), Adobe FrameMaker (3), Adobe Bridge (5), Adobe Photoshop (3), Adobe Premier Rush (2), and Adobe Animate (3). All the vulnerabilities rated critical allow Arbitrary Code Execution. The advisories have a priority rating of 3 from Adobe, meaning none of the vulnerabilities addressed are known to be currently exploited, and Abode anticipates that they won’t be exploited in the future.
Notable and Critical Microsoft Vulnerabilities Patched
CVE-2023-21692, CVE-2023-21690, CVE-2023-21689 – Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
Microsoft PEAP is a secure implementation of Extensible Authentication Protocol (EAP) that provides encryption and authenticated Transport Layer Security (TLS) tunnel. CVE-2023-21692 and CVE-2023-21690 can be exploited by sending specially crafted malicious packets, whereas CVE-2023-21689 can be used to target server accounts through network calls to execute code remotely. All 3 vulnerabilities do not require special privileges or user interaction.
CVE-2023-21803 – Windows iSCSI Discovery Service Remote Code Execution Vulnerability
Windows iSCSI Discovery Service is a Windows Service that allows non-SMB Clients to access storage on a Windows host. The vulnerability affects only 32 bits versions of Windows. The vulnerability can be exploited by sending a maliciously crafted DHCP discovery request to a Windows Host running iSCSI Discovery Service. On successful exploitation, it will allow an attacker to execute code remotely. The vulnerability can only be exploited if the iSCSI Initiator client application is running. iSCSI Initiator client application is not enabled by default.
CVE-2023-21716 – Microsoft Word Remote Code Execution Vulnerability
CVE-2023-21716 affects both Microsoft SharePoint and Microsoft Office Applications. The vulnerability can be used in a Preview Pane attack. An attacker can send a malicious RTF payload (e.g., via email) that allows the attacker to execute commands without minimal or no user interaction. Microsoft has also provided a workaround for this vulnerability. Administrators need to enforce a Microsoft Office File Block policy to prevent opening RTF documents from unknown or untrusted sources. More details about the policy can be found at MS08-026: How to prevent Word from loading RTF files. If attackers can develop exploits for this vulnerability, it may become a popular choice for them in future Phishing campaigns.
CVE-2023-21718 – Microsoft SQL ODBC Driver Remote Code Execution Vulnerability
The vulnerability affects the Microsoft Open Database Connectivity (ODBC) interface, which allows applications to access data from various types of database management systems (DBMSs). The vulnerability can be exploited by an attacker tricking an unauthenticated user into connecting to an attacker controlled rogue SQL Database. The attacker can then return malicious data to a client (user) and cause arbitrary code execution on it.
CVE-2023-21808, CVE-2023-21815, CVE-2023-23381 – .NET / Visual Studio Remote Code Execution Vulnerability
Microsoft has not detailed much information about these vulnerabilities. However, based on the limited information available, CVE-2023-21808, CVE-2023-21815, and CVE-2023-23381 seem similar in nature and require an attacker to trick the victim to trigger this vulnerability to execute code in the context of the application.
Other Microsoft Vulnerability Highlights
Microsoft has patched a total 3 zero-day vulnerabilities that are confirmed to be exploited:
- CVE-2023-21823 is a vulnerability that affects Windows Graphic component used in various products such as Windows OS, Office desktop, and Mobile Apps. The vulnerability helps the attacker gain and execute code with SYSTEM privileges.
- CVE-2023-21715, a Security Features Bypass Vulnerability in Microsoft Publisher that lets attackers bypass Office macro policies used to block untrusted or malicious files. Microsoft has additionally mentioned that the vulnerability can be triggered using social engineering attacks to trick the victim into downloading a specially crafted file from a website.
- CVE-2023-23376, an Elevation of Privilege vulnerability, is the Windows Common Log File System Driver that allows attackers to gain SYSTEM privileges. No other information has been made public by Microsoft.
Microsoft has also disclosed a vulnerability that affects the end-of-life application Print 3D. Microsoft has affirmed that it will not release a patch to fix the vulnerability and that customers should update to the 3D Builder app.
Microsoft Dynamic has got fixes for 6 Cross-site Scripting Vulnerabilities. Microsoft has fixed 4 remote code execution bugs in Exchange Server. Azure DevOps has received patches for a Cross-site Scripting and Remote Code Execution vulnerability. Lastly, a spoofing vulnerability in Power BI Report Server has been addressed.
This month, nearly half of the CVEs disclosed by Microsoft are Remote Code Execution Vulnerabilities. We continue to see double-digit numbers in terms of fixes in the Elevation of Privilege and Denial of Server vulnerabilities.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions that are affected, including, but not limited to, .NET and Visual Studio, .NET Framework, 3D Builder, Azure App Service, Azure Data Box Gateway, Azure DevOps, Azure Machine Learning, HoloLens, Internet Storage Name Service, Microsoft Defender for Endpoint, Microsoft Defender for IoT, Microsoft Dynamics, Microsoft Edge (Chromium-based), Microsoft Exchange Server, Microsoft Graphics Component, Microsoft Office, Microsoft Office OneNote, Microsoft Office Publisher, Microsoft Office SharePoint, Microsoft Office Word, Microsoft PostScript Printer Driver, Microsoft WDAC OLE DB provider for SQL, Microsoft Windows Codecs Library, Power BI, SQL Server, Visual Studio, Windows Active Directory, Windows ALPC, Windows Common Log File System Driver, Windows Cryptographic Services, Windows Distributed File System (DFS), Windows Fax and Scan Service, Windows HTTP.sys, Windows Installer, Windows iSCSI, Windows Kerberos, Windows MSHTML Platform, Windows ODBC Driver, Windows Protected EAP (PEAP), Windows SChannel, Windows Win32K.
Downloads include Cumulative Updates, Monthly Rollups, Security Only, and Security Updates.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
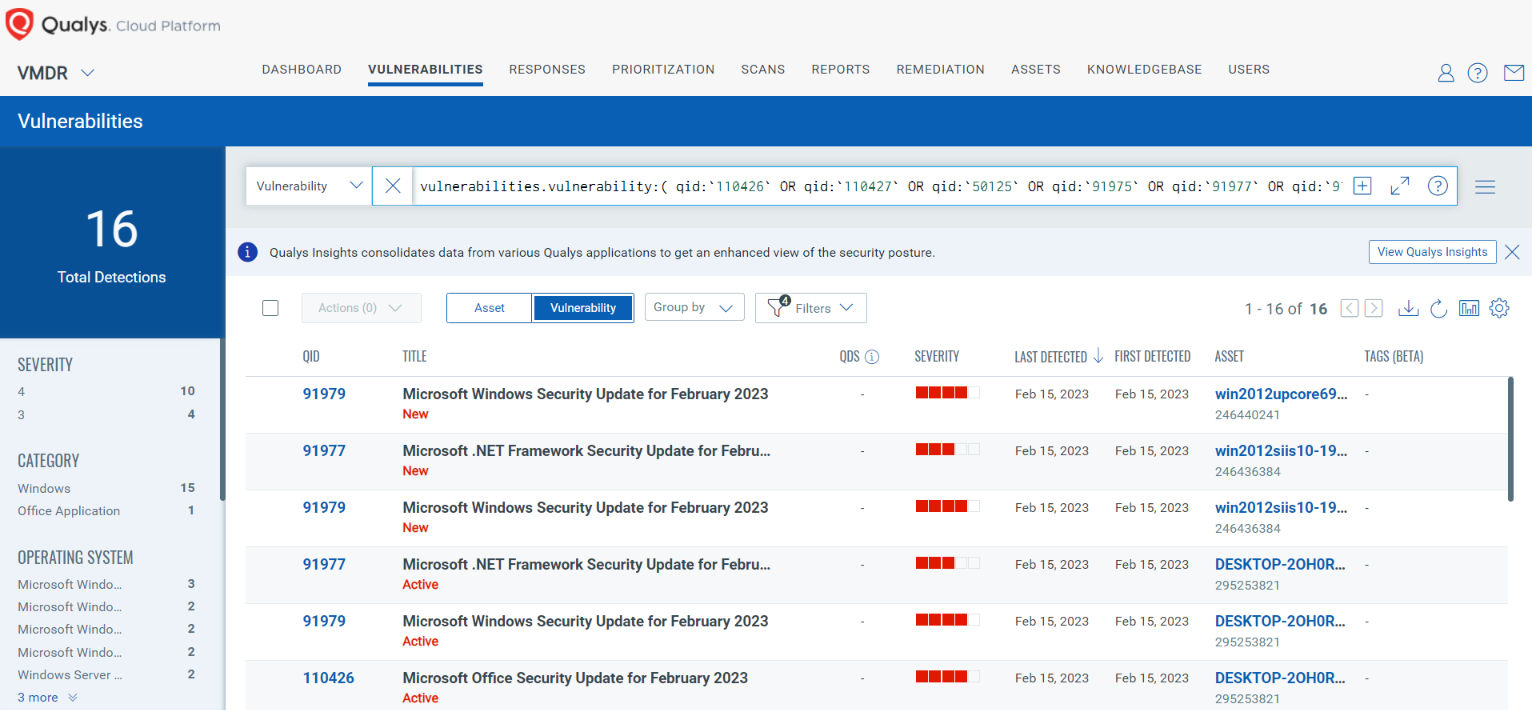
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:( qid:`110426` OR qid:`110427` OR qid:`50125` OR qid:`91975` OR qid:`91977` OR qid:`91978` OR qid:`91979` OR qid:`91980` OR qid:`91981` OR qid:`91982` OR qid:`91983` OR qid:`91984` OR qid:`91985` OR qid:`91986` )
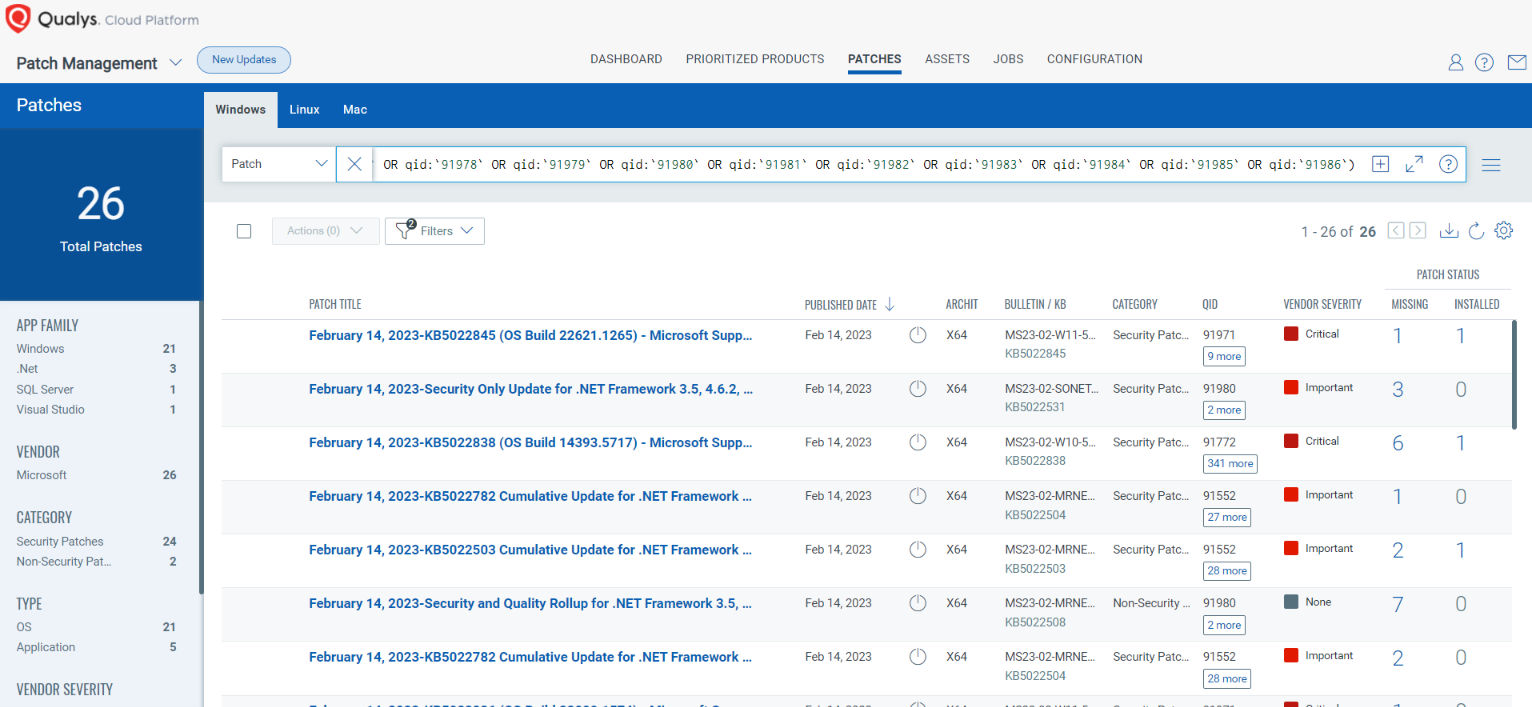
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
(qid:`110426` OR qid:`110427` OR qid:`50125` OR qid:`91975` OR qid:`91977` OR qid:`91978` OR qid:`91979` OR qid:`91980` OR qid:`91981` OR qid:`91982` OR qid:`91983` OR qid:`91984` OR qid:`91985` OR qid:`91986`)
EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of a vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
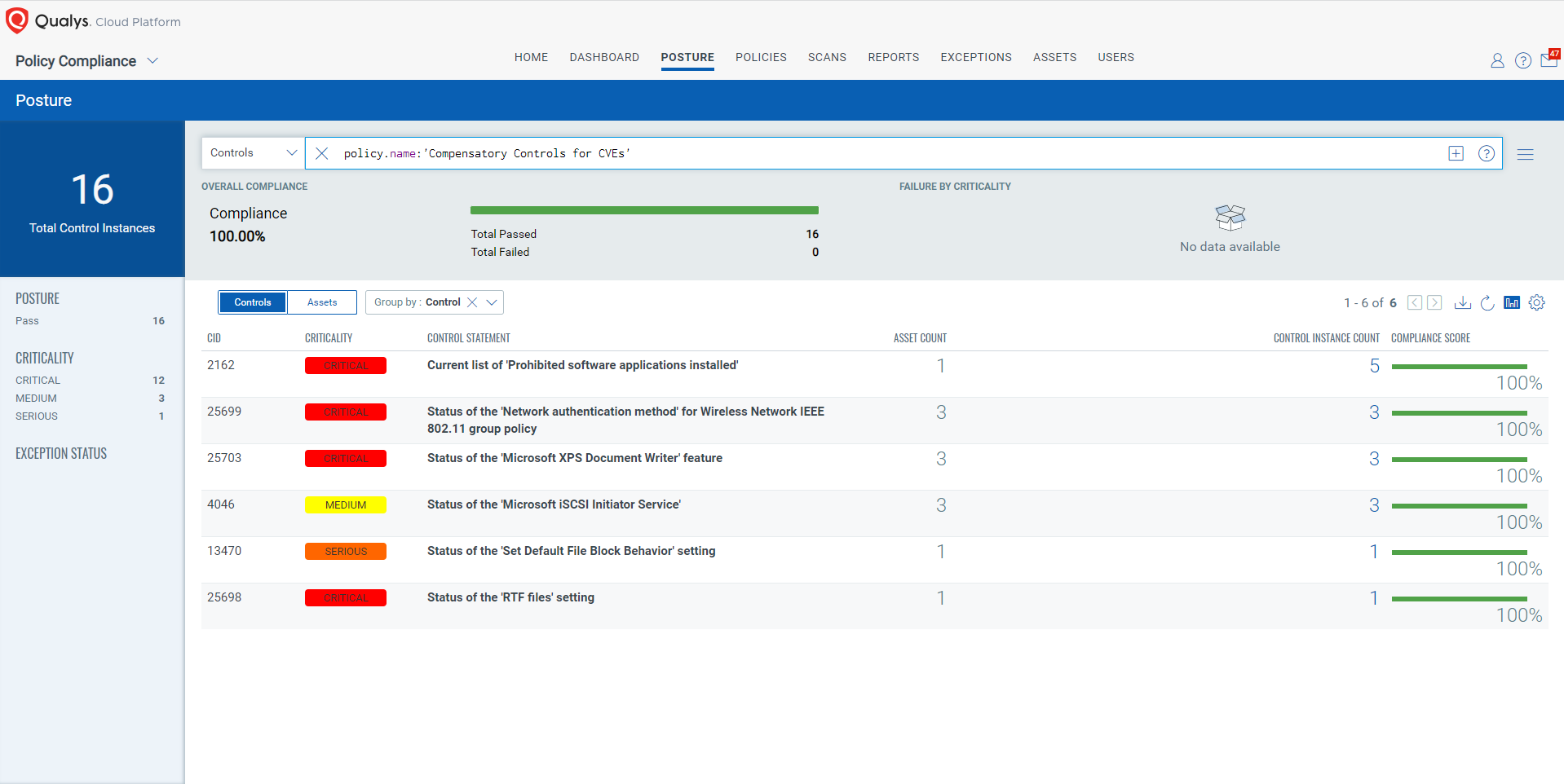
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-21716 | Microsoft Word Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8/10
Policy Compliance Control IDs (CIDs):
- 13470 Status of the ‘Set Default File Block Behavior’ setting
- 25698 Status of the ‘RTF files’ setting
CVE-2023-21713 | Microsoft SQL Server Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 8.8/10
Policy Compliance Control IDs (CIDs):
- 2162 Current list of ‘Prohibited software applications installed’
CVE-2023-21705 | Microsoft SQL Server Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 8.8/10
Policy Compliance Control IDs (CIDs):
- 2162 Current list of ‘Prohibited software applications installed’
CVE-2023-21689 | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8/10
CVE-2023-21690 | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8/10
CVE-2023-21692 | Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8/10
Policy Compliance Control IDs (CIDs):
- 25699 Status of the ‘Network authentication method’ for Wireless Network IEEE 802.11 group policy
CVE-2023-21804 | Windows Graphics Component Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 7.8/10
Policy Compliance Control IDs (CIDs):
- 25703 Status of the ‘Microsoft XPS Document Writer’ feature
CVE-2023-21803 | Windows iSCSI Discovery Service Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8/10
Policy Compliance Control IDs (CIDs):
- 4046 Status of the ‘Microsoft iSCSI Initiator Service’
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:

The next Patch Tuesday falls on March 14th, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the This Month in Vulnerabilities and Patches webinar.
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
https://blog.qualys.com/vulnerabilities-threat-research/patch-tuesday/2023/02/14/the-february-2023-patch-tuesday-security-update-review
Is missing the section: Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
That lists the specific QID’s that cover the February Microsoft updates.
No PM or VMDR QQL query, this month?