The March 2023 Patch Tuesday Security Update Review
Table of Contents
- Microsoft Patches for March 2023
- Adobe Patches for March 2023
- Zero-day Vulnerabilities Patched in March Patch Tuesday Edition
- Other Critical Severity Vulnerabilities Patched in March Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response withPatch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- Qualys Monthly Webinar Series
- This Month in Vulnerabilities & Patches
Microsoft has released its monthly security update for March 2023. This month’s updates addressed various vulnerabilities in different products. Let’s go through this month’s Patch Tuesday details and discuss the security updates.
Microsoft Patches for March 2023
Microsoft has addressed 101 vulnerabilities in the month of March, including 22 Microsoft Edge (Chromium-based) vulnerabilities. Microsoft has also addressed two zero-day vulnerabilities known to be exploited in the wild. CISA has also added those two vulnerabilities, CVE-2023-24880 and CVE-2023-23397, to its Known Exploitable Vulnerabilities Catalog after Microsoft released this month’s Patch Tuesday update.
Out of the 101 vulnerabilities, nine are rated as critical, 70 as important, and one as moderate. This month’s Patch Tuesday edition includes updates for vulnerabilities in Microsoft Office and Components; Microsoft Dynamics, Microsoft OneDrive, Microsoft Windows Codecs Library, Client Server Runtime Subsystem (CSRSS), Internet Control Message Protocol (ICMP), Microsoft PostScript Printer Driver.
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The March 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
|---|---|---|
| Spoofing Vulnerability | 10 | Important: 6 |
| Denial of Service Vulnerability | 4 | Important: 3 Critical: 1 |
| Elevation of Privilege Vulnerability | 21 | Important: 18 Critical: 3 |
| Information Disclosure Vulnerability | 15 | Important: 15 |
| Remote Code Execution Vulnerability | 27 | Important: 22 Critical: 5 |
| Security Feature Bypass Vulnerability | 2 | Important: 1 |
| Microsoft Edge (Chromium-based) | 22 | Important: 1 |
Adobe Patches for March 2023
Adobe has released a total of 8 advisories for the month of March. The advisories cover a total of 101 vulnerabilities, out of which 60 are rated critical that affect Adobe Commerce and Magento (4), Adobe Illustrator (4), Adobe Dimension (40), Adobe Creative Cloud (1), Adobe Photoshop (1), Adobe ColdFusion (2), and Adobe Substance 3D Stager (11). Adobe ColdFusion (APSB23-25) has a Priority rating of 1 because Adobe is aware that CVE-2023-26360 is being exploited in the wild. All the other advisories have a priority rating of 3 from Adobe, meaning none of the other vulnerabilities are known to be currently exploited. Adobe anticipates that they won’t be exploited in the future.
Zero-day Vulnerabilities Patched in March Patch Tuesday Edition
CVE-2023-23397 – Microsoft Outlook Elevation of Privilege Vulnerability
Microsoft is aware of the active exploitation of this vulnerability that could allow an attacker to access a user’s Net-NTLMv2 hash. The hash can be leveraged to carry out an NTLM Relay attack against another service to authenticate as the user.
The vulnerability can be exploited in a low-complexity attack by specially crafted emails sent by an attacker to connect the victim to an external attacker’s control UNC location. The mail will be triggered automatically when retrieved and processed by the Outlook client. This could result in exploitation BEFORE the email is viewed in the Preview Pane.
Ukraine’s Computer Emergency Response Team (CERT-UA) discovered the flaw and notified Microsoft about it, perhaps after observing it being utilized in attacks on the company’s services. As per Microsoft, the vulnerability was exploited in targeted attacks against a number of European companies in the military, transportation, energy, and government sectors.
The threat actor APT28 is thought to be responsible for the attacks. APT28 has been connected to the Main Directorate of the General Staff of the Military Forces of the Russian Federation (GRU).
CVE-2023-23397 has been used in attacks against up to 15 companies, with the most recent incident taking place in December of last year.
CVE-2023-24880 – Windows SmartScreen Security Feature Bypass Vulnerability
Microsoft has mentioned in the advisory that this vulnerability is being exploited in the wild. To exploit this vulnerability, an attacker must craft a malicious file to bypass the Mark of the Web (MOTW) defenses.
Mark of the Web (MOTW) is a Windows feature that protects users from downloading files from unreliable sources. Windows adds a hidden tag called the mark to files obtained from the Internet. The capability and usage of files with the MOTW tag are restricted.
Other Critical Severity Vulnerabilities Patched in March Patch Tuesday Edition
CVE-2023-1017 and CVE-2023-1018 – TPM2.0 Module Library Elevation of Privilege Vulnerability
These vulnerabilities were discovered and addressed earlier this month by the upstream vendor TCG in the advisory TCGVRT0007.
TPM (Trusted Platform Module) is a hardware-based technology that helps improve PC security. A TPM chip is widely used as a secure cryptoprocessor that provides hardware security through integrated cryptographic keys.
Implementing improper length checks may lead to buffer overflow; the buffer passed to the ExecuteCommand() entry point faces this overflow condition.
CVE-2023-1017 is an out-of-bounds write vulnerability that could allow an attacker to write 2 bytes past the end of that buffer with attacker-specified values. User-mode applications can trigger this vulnerability by sending malicious commands to TPM 2.0. An attacker can cause an out-of-bounds write to the root partition on a target running Hyper-V using malicious TPM commands from a guest VM.
CVE-2023-1018 is an out-of-bound read vulnerability that may allow an attacker to read 2 bytes past the end of that buffer.
Successful exploitation of these vulnerabilities may result in local information disclosure or elevation of privileges.
CVE-2023-21708 – Remote Procedure Call Runtime Remote Code Execution Vulnerability
Microsoft has put this vulnerability in the less likely to be exploited category. With a specially crafted RPC call to an RPC host, an attacker may exploit this vulnerability. An unauthenticated attacker may exploit this vulnerability to perform remote code execution on the server side with the same privileges as the RPC service.
CVE-2023-23392 – HTTP Protocol Stack Remote Code Execution Vulnerability
The critical severity vulnerability affects Windows 11 Systems and Windows Server 2022.
A server is vulnerable to the flaw if the following two conditions are met:
- Sever must use buffered I/O
- Binding has HTTP/3 enabled
A server that uses the HTTP Protocol Stack (HTTP.sys) to handle packets could be exploited by an unauthenticated attacker by sending a specially crafted packet to the server.
CVE-2023-23404 – Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability
Point-to-Point Tunneling Protocol enables secure data transmission from a remote client to a private enterprise server with the help of a virtual private network (VPN) across TCP/IP-based data networks.
The vulnerability requires an attacker to win a race condition to exploit this vulnerability. An unauthenticated attacker may send a specially crafted connection request to a RAS server that will lead to remote code execution on the RAS Server machine.
CVE-2023-23411 – Windows Hyper-V Denial of Service Vulnerability
An attacker can locally exploit this vulnerability in a low-complexity attack to affect the functionality of Hyper-V hosts as a Hyper-V.
Hyper-V provides hardware virtualization and allows the creation of virtual hard drives and virtual switches.
CVE-2023-23415 – Internet Control Message Protocol (ICMP) Remote Code Execution Vulnerability
The vulnerability affects the Internet Control Message Protocol (ICMP) network layer protocol. The protocol is used by multiple network devices to detect network communication issues.
To exploit this vulnerability, an attacker must send a low-level protocol error with a fragmented IP packet inside another ICMP packet in its header to the target system. An application on the target must be bound to a raw socket to execute the vulnerable code path.
CVE-2023-23416 – Windows Cryptographic Services Remote Code Execution Vulnerability
An affected system must import a malicious certificate to exploit this vulnerability successfully. An attacker may encourage an authenticated user to import a certificate on their system, upload it to a service that processes or imports certificates, or both.
Other Microsoft Vulnerability Highlights
- CVE-2023-23398 allows an attacker to trick a user into enabling content they cannot inspect. Using social engineering to convince a victim to download and open a specially constructed file from a website could result in a local attack on the victim’s computer.
- CVE-2023-23410 is an elevation of privilege vulnerability in the HTTP.sys web server implementation. The flaw allows an attacker to gain SYSTEM privileges on successful exploitation.
- CVE-2023-24861 is an elevation of privilege vulnerability in the Windows Graphic component. Successful exploitation of this vulnerability requires an attacker to win a race condition. An attacker may gain SYSTEM privileges after exploiting this vulnerability.
- CVE-2023-24876 is a remote code execution vulnerability that affects the Microsoft PostScript and PCL6 Class Printer Driver.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions that are affected, including, but not limited to, Azure, Microsoft Bluetooth Driver, Microsoft Edge (Chromium-based), Microsoft Graphics Component, Microsoft Office Excel, Microsoft Office Outlook, Microsoft Office SharePoint, Microsoft PostScript Printer Driver, Microsoft Printer Drivers, Office for Android, Remote Access Service Point-to-Point Tunneling Protocol, Service Fabric, Visual Studio, Windows Accounts Control, Windows Bluetooth Service, Windows Central Resource Manager, Windows Cryptographic Services, Windows Defender, Windows HTTP Protocol Stack, Windows HTTP.sys, Windows Internet Key Exchange (IKE) Protocol, Windows Kernel, Windows Partition Management Driver, Windows Point-to-Point Protocol over Ethernet (PPPoE), Windows Remote Procedure Call, Windows Remote Procedure Call Runtime, Windows Resilient File System (ReFS), Windows Secure Channel, Windows SmartScreen, Windows TPM, Windows Win32K.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
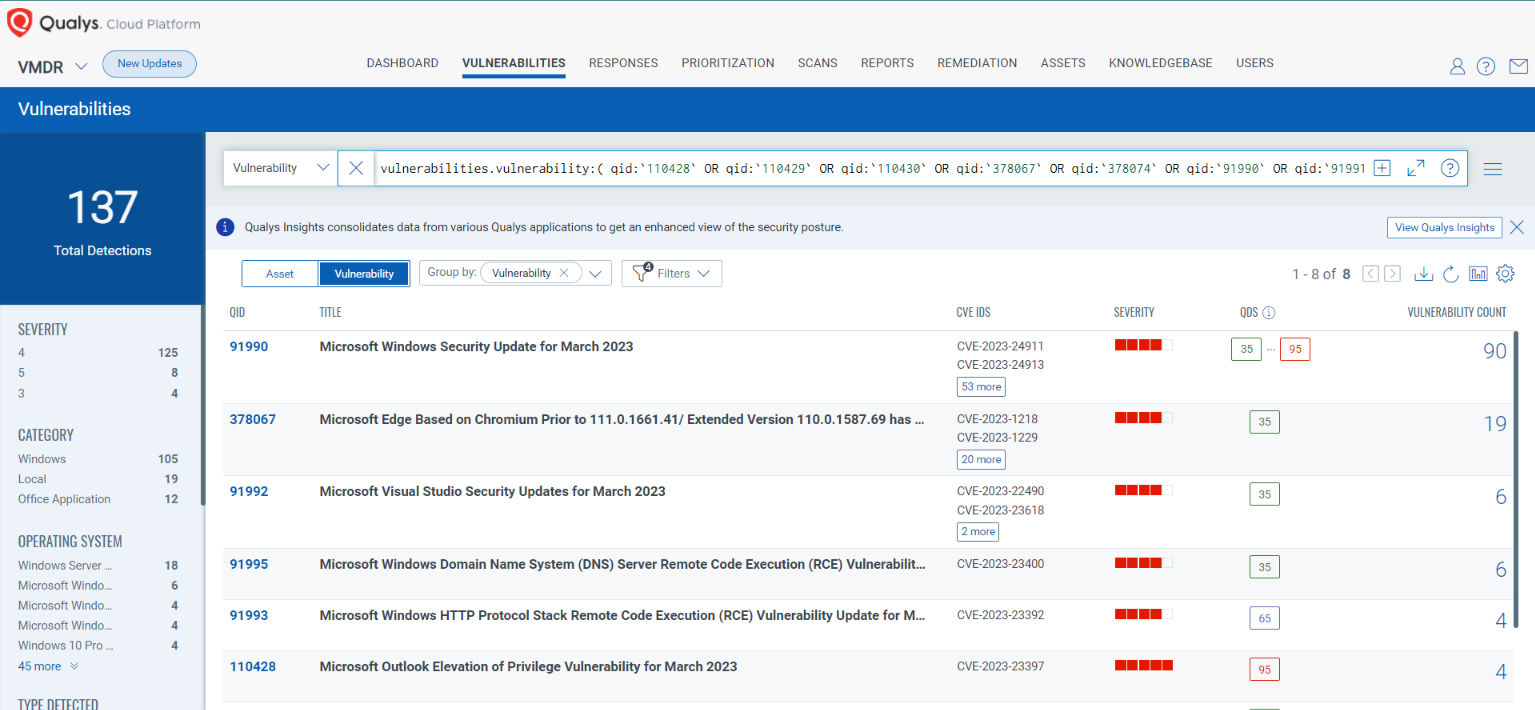
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:( qid:`110428` OR qid:`110429` OR qid:`110430` OR qid:`378067` OR qid:`378074` OR qid:`91990` OR qid:`91991` OR qid:`91992` OR qid:`91993` OR qid:`91995` )
Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
(qid:`110428` OR qid:`110429` OR qid:`110430` OR qid:`378067` OR qid:`378074` OR qid:`91990` OR qid:`91991` OR qid:`91992` OR qid:`91993` OR qid:`91995`)

EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
With Qualys Policy Compliance’s Out-of-the-Box Mitigation or Compensatory Controls reduce the risk of a vulnerability being exploited because the remediation (fix/patch) cannot be done now; these security controls are not recommended by any industry standards such as CIS, DISA-STIG.
Qualys Policy Compliance team releases these exclusive controls based on Vendor-suggested Mitigation/Workaround.
Mitigation refers to a setting, common configuration, or general best-practice existing in a default state that could reduce the severity of exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-23392 | HTTP Protocol Stack Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8/10
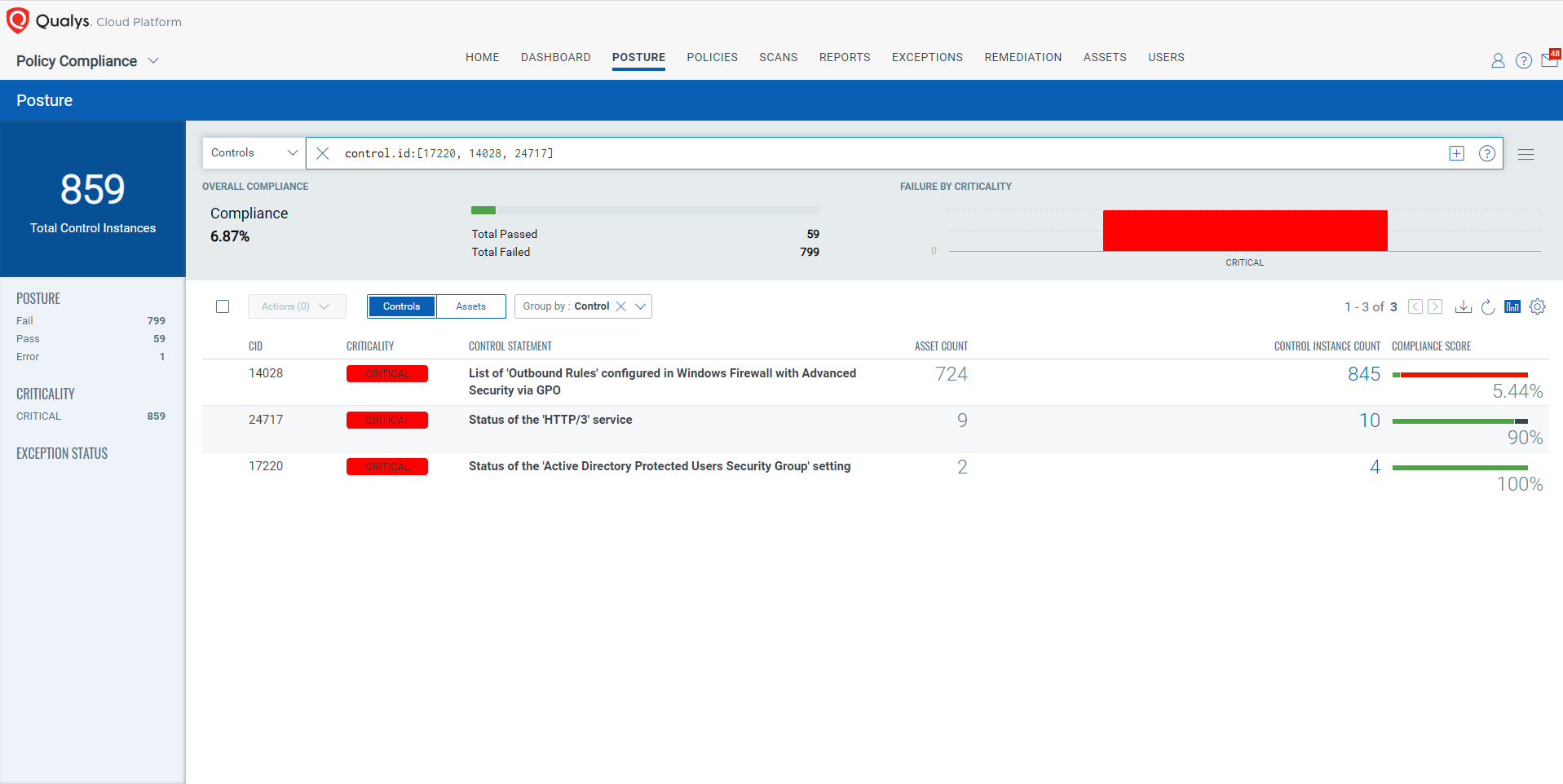
Policy Compliance Control IDs (CIDs):
- 24717 Status of the ‘HTTP/3’ service
CVE-2023-23397 | Microsoft Outlook Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 9.8/10
Policy Compliance Control IDs (CIDs):
- 17220 Status of the ‘Active Directory Protected Users Security Group’ setting
- 14028 List of ‘Outbound Rules’ configured in Windows Firewall with Advanced Security via GPO
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [17220, 14028, 24717]
The next Patch Tuesday falls on April 11th, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the This Month in Vulnerabilities and Patches webinar.
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.