Microsoft and Adobe Patch Tuesday April 2023 Security Update Review
Table of Contents
- Microsoft Patch Tuesday for April 2023
- Adobe Patches for April 2023
- Zero-day Vulnerability Patched in April Patch Tuesday Edition
- Other Critical Severity Vulnerabilities Patched in April Patch Tuesday Edition
- Other Microsoft Vulnerability Highlights
- Microsoft Release Summary
- Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
- Rapid Response with Patch Management (PM)
- EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
- EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
- Qualys Monthly Webinar Series
- This Month in Vulnerabilities & Patches
Microsoft released security updates to address 114 vulnerabilities in the April Patch Tuesday edition. The security advisories cover various vulnerabilities in different products, features, and roles. Let’s know more about this month’s Patch Tuesday details.
Microsoft Patch Tuesday for April 2023
Microsoft has addressed 114 vulnerabilities in this month’s Security Update, including 15 Microsoft Edge (Chromium-based) vulnerabilities. Microsoft has also addressed one zero-day vulnerability known to be exploited in the wild.
Seven of these 114 vulnerabilities are rated as critical and 90 as important. This month’s Patch Tuesday edition includes updates for vulnerabilities in Microsoft Office and Components; Microsoft Dynamics 365 Customer Voice, Microsoft Edge (Chromium-based), Microsoft Graphics Component, Windows Kernel, Windows Layer 2 Tunneling Protocol, Windows Lock Screen, Windows Netlogon, Windows Secure Socket Tunneling Protocol (SSTP), Windows Transport Security Layer (TLS), Windows Win32K, and more.
Microsoft has fixed several flaws in multiple software, including Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), Security Feature Bypass, and Spoofing.
The April 2023 Microsoft vulnerabilities are classified as follows:
| Vulnerability Category | Quantity | Severities |
|---|---|---|
| Spoofing Vulnerability | 6 | Important: 3 |
| Denial of Service Vulnerability | 9 | Important: 9 |
| Elevation of Privilege Vulnerability | 20 | Important: 20 |
| Information Disclosure Vulnerability | 10 | Important: 9 |
| Remote Code Execution Vulnerability | 45 | Important: 38 Critical: 7 |
| Security Feature Bypass Vulnerability | 8 | Important: 7 |
| Microsoft Edge (Chromium-based) | 15 |
Adobe Patches for April 2023
Adobe has released a total of six advisories for the month of April. The advisories cover a total of 56 vulnerabilities, out of which 49 are rated critical that affect Adobe Digital Editions (1), Adobe InCopy (1), Adobe Acrobat and Reader (14), Adobe Substance 3D Stager (10), Adobe Dimension (14), and Adobe Substance 3D Designer (9). All the advisories have a priority rating of 3 from Adobe, meaning none of the other vulnerabilities are known to be currently exploited. Adobe anticipates that they won’t be exploited in the future.
Zero-day Vulnerability Patched in April Patch Tuesday Edition
CVE-2023-28252: Windows Common Log File System Driver Elevation of Privilege Vulnerability
An attacker may exploit this vulnerability in a low-complexity attack. On successful exploitation, an attacker will gain SYSTEM privileges. Microsoft has mentioned in the advisory that the vulnerability is being exploited in the wild. Cybercriminals have used the vulnerability to deploy Nokoyawa Ransomware. The identity of the threat actor or APT group using Nokoyawa is yet to be disclosed. The attacks are happening in South and North America, regions across Asia, and SMBs in the Middle East.
Additionally, CISA has also added this vulnerability to its Known Exploitable Vulnerabilities Catalog.
Other Critical Severity Vulnerabilities Patched in April Patch Tuesday Edition
CVE-2023-21554: Microsoft Message Queuing Remote Code Execution Vulnerability (QueueJumper)
Message Queuing (MSMQ) is a protocol developed by Microsoft to ensure reliable communication between Windows computers across different networks, even when a host is temporarily not connected (by maintaining a message queue of undelivered messages).
The Windows message queuing service needs to be enabled for the system to be exploitable. This feature can be enabled using the Control Panel.
To exploit this vulnerability, an attacker must send a specially crafted malicious MSMQ packet to an MSMQ server to perform remote code execution on the server side.
CVE-2023-28219 & CVE-2023-28220: Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
Layer 2 Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used mainly by Internet Service Providers and Virtual Private Networks (VPNs). L2TP is one of the protocols that help in ensuring security and privacy by enabling a tunnel for Layer 2 traffic over a Layer 3 network.
To exploit this vulnerability, an attacker is required to win a race condition. An unauthenticated attacker could send a specially crafted connection request to a RAS server and perform remote code execution on the RAS server machine.
CVE-2023-28231: DHCP Server Service Remote Code Execution Vulnerability
Dynamic Host Configuration Protocol (DHCP) is a network server that helps clients successfully communicate on the network. The protocol provides an Internet Protocol (IP) host with its IP address.
An authenticated attacker may exploit this vulnerability by sending a specially crafted RPC call to the DHCP service. An attacker must gain access to the restricted network before performing the attack for successful exploitation.
CVE-2023-28232: Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability
Point-to-Point Tunneling Protocol enables secure data transmission from a remote client to a private enterprise server with the help of a virtual private network (VPN) across TCP/IP-based data networks.
The vulnerability arises when a user connects a Windows client to a malicious server. An attacker must perform additional actions to prepare the target environment for exploitation.
CVE-2023-28250: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
Pragmatic General Multicast (PGM) is a multicast computer network transport protocol best suited for applications like multi-receiver file transfer. The protocol provides a reliable sequence of packets to multiple recipients simultaneously.
The system will be exploitable if the Windows Message Queuing service is enabled. An attacker may send a specially crafted file over the network for remote code execution.
CVE-2023-28291: Raw Image Extension Remote Code Execution Vulnerability
An attacker must log on to the system to exploit the vulnerability. An attacker may trick a local user into opening a malicious file containing a specially crafted application to take control of the system.
To open the specially crafted file, an attacker must first convince the user to click a link, usually sent via an email or instant message.
Other Microsoft Vulnerability Highlights
- CVE-2023-21727 allows an attacker to perform remote code execution on the server side with the same permissions as the RPC service by sending a specially crafted RPC call to an RPC host.
- CVE-2023-28297 allows an attacker to gain SYSTEM privileges by running a specially crafted application. The specially crafted application may lead to remote code execution with elevated permissions.
- CVE-2023-28240, an attacker on the same subnet as the target system, may send a specially crafted packet to a server configured as a Network Load Balancing cluster host to exploit this vulnerability.
- An attacker can trigger CVE-2023-28275 by tricking an authenticated user into attempting to connect to a malicious SQL server via OLEDB. An attacker can perform remote code execution on successful exploitation.
- CVE-2023-24884, CVE-2023-24885, CVE-2023-24886, CVE-2023-24887, CVE-2023-24924, CVE-2023-24925, CVE-2023-24926, CVE-2023-24927, CVE-2023-24928, CVE-2023-24929, CVE-2023-28243 vulnerabilities allow an authenticated attacker to send a modified XPS file to a shared printer leading to remote code execution.
Microsoft Release Summary
This month’s release notes cover multiple Microsoft product families and products/versions that are affected, including, but not limited to .NET Core, Azure Machine Learning, Azure Service Connector, Microsoft Bluetooth Driver, Microsoft Defender for Endpoint, Microsoft Dynamics, Microsoft Message Queuing, Microsoft Office, Microsoft Office Publisher, Microsoft Office SharePoint, Microsoft Office Word, Microsoft PostScript Printer Driver, Microsoft Printer Drivers, Microsoft WDAC OLE DB provider for SQL, Microsoft Windows DNS, Visual Studio, Visual Studio Code, Windows Active Directory, Windows ALPC, Windows Ancillary Function Driver for WinSockWindows Boot Manager, Windows Clip Service, Windows CNG Key Isolation Service, Windows Common Log File System Driver, Windows DHCP Server, Windows Enroll Engine, Windows Error Reporting, Windows Group Policy, Windows Internet Key Exchange (IKE) Protocol, Windows Kerberos, Windows Network Address Translation (NAT, Windows Network File System, Windows Network Load Balancing, Windows NTLM, Windows PGM, Windows Point-to-Point Protocol over Ethernet (PPPoE), Windows Point-to-Point Tunneling Protocol, Windows Raw Image Extension, Windows RDP Client, Windows Registry, Windows RPC API, Windows Secure Boot, Windows Secure Channel.
Discover and Prioritize Vulnerabilities in Vulnerability Management, Detection & Response (VMDR)
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledgebase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability: ( qid:`110431` OR qid:`110432` OR qid:`110433` OR qid:`378386` OR qid:`92000` OR qid:`92002` OR qid:`92003` OR qid:`92004` OR qid:`92005` OR qid:`92006` OR qid:`92007` OR qid:`92008` )

Rapid Response with Patch Management (PM)
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches with one click.
The following QQL will return the missing patches for this Patch Tuesday:
(qid:`110431` OR qid:`110432` OR qid:`110433` OR qid:`378386` OR qid:`92000` OR qid:`92002` OR qid:`92003` OR qid:`92004` OR qid:`92005` OR qid:`92006` OR qid:`92007` OR qid:`92008`)

EVALUATE Vendor-Suggested Mitigation with Policy Compliance (PC)
Qualys Policy Compliance Control Library makes it easy to evaluate your technology infrastructure when the current situation requires implementation validation of vendor-suggested mitigation or workaround.
Mitigation refers to a setting, common configuration, or general best practice existing in a default state that could reduce the severity of the exploitation of a vulnerability.
A workaround is a method, sometimes used temporarily, for achieving a task or goal when the usual or planned method isn’t working. Information technology often uses a workaround to overcome hardware, programming, or communication problems. Once a problem is fixed, a workaround is usually abandoned. Source
The next Patch Tuesday falls on May 9th, and we’ll be back with details and patch analysis. Until next Patch Tuesday, stay safe and secure. Be sure to subscribe to the This Month in Vulnerabilities and Patches webinar.
The following Qualys Policy Compliance Control IDs (CIDs) and System Defined Controls (SDC) have been updated to support Microsoft recommended mitigation(s) for this Patch Tuesday:
CVE-2023-28250: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 4030 Status of the ‘Windows Message Queuing Service’
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
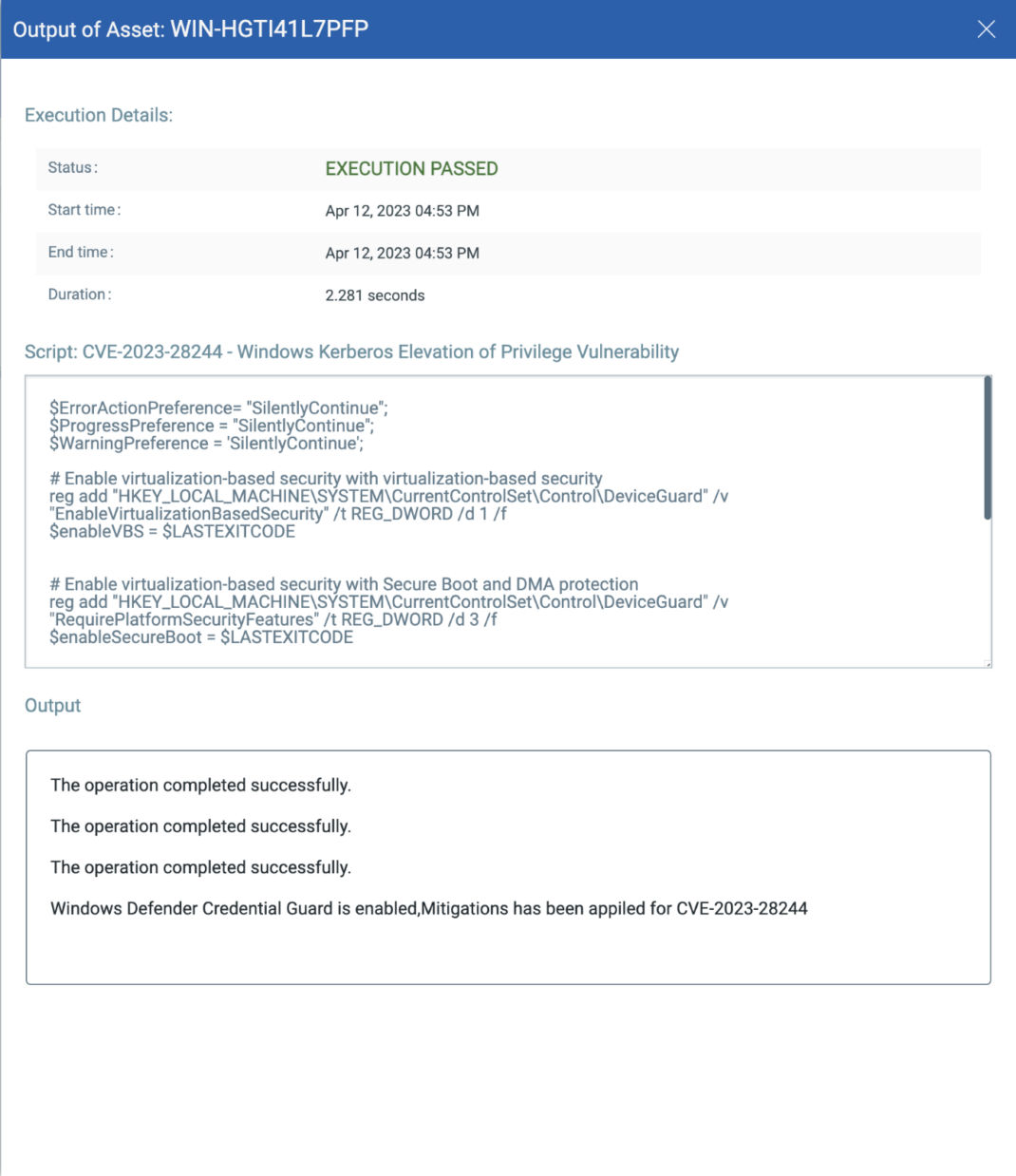
CVE-2023-28244: Windows Kerberos Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 8.1 / 7.1
Policy Compliance Control IDs (CIDs):
- 10472 Status of the ‘Turn On Virtualization Based Security’ setting
- 10475 Status of the ‘Turn On Virtualization Based Security (Select Platform Security Level)’ setting
- 10474 Status of the ‘Turn On Virtualization Based Security (Enable Virtualization Based Protection of Code Integrity)’ setting
- 13918 Status of ‘Turn On Virtualization Based Security: Require UEFI Memory Attributes Table’ group policy
- 10473 Status of the ‘Turn On Virtualization Based Security (Credential Guard Configuration)’ setting
- 16104 Status of the ‘Turn On Virtualization Based Security (Secure Launch Configuration)’ GPO setting
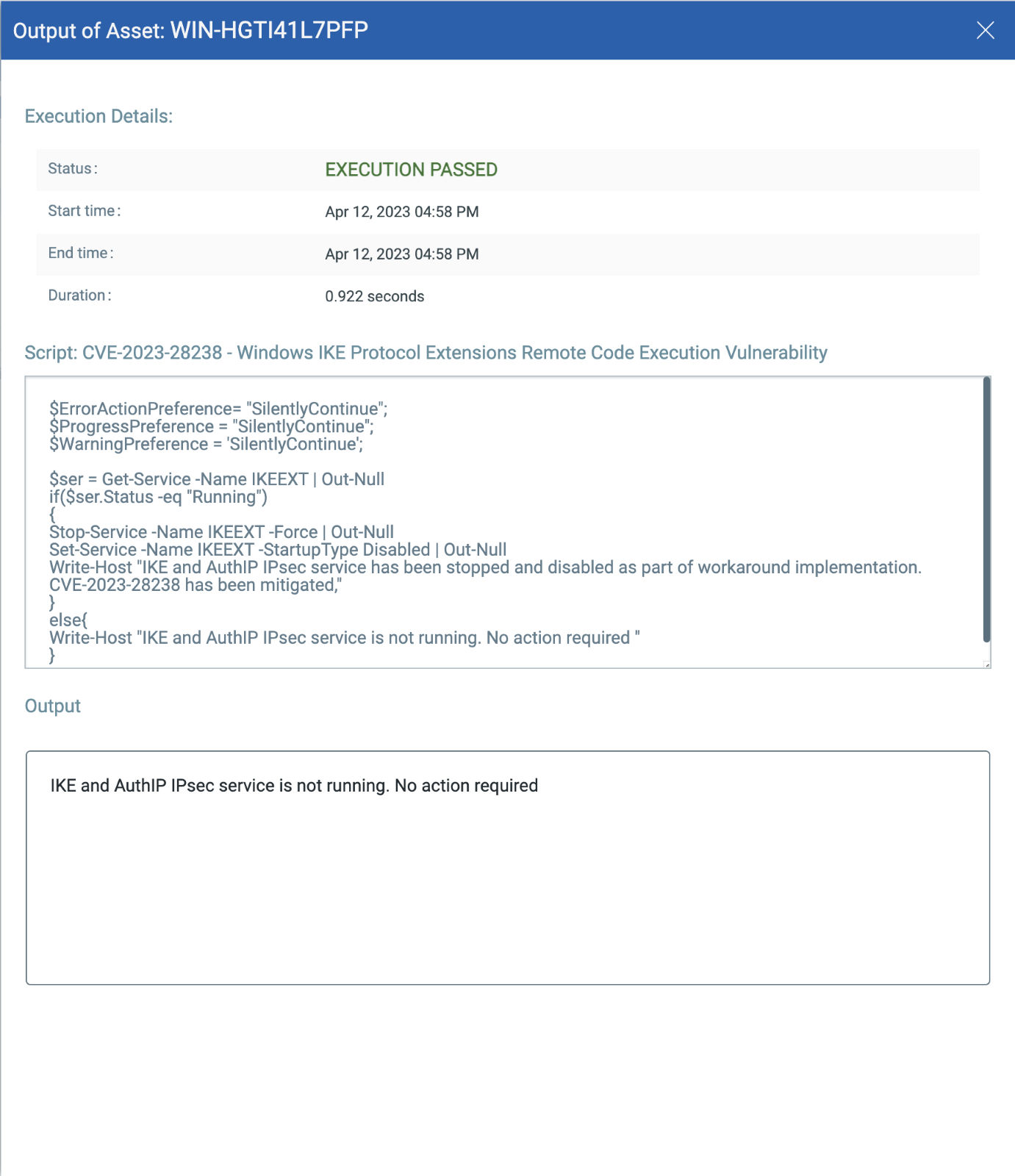
CVE-2023-28238: Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 7.5 / 6.5
Policy Compliance Control IDs (CIDs):
- 4026 Status of the Windows IKE and AuthIP IPsec Keying Modules service
- 14916 Status of Windows Services
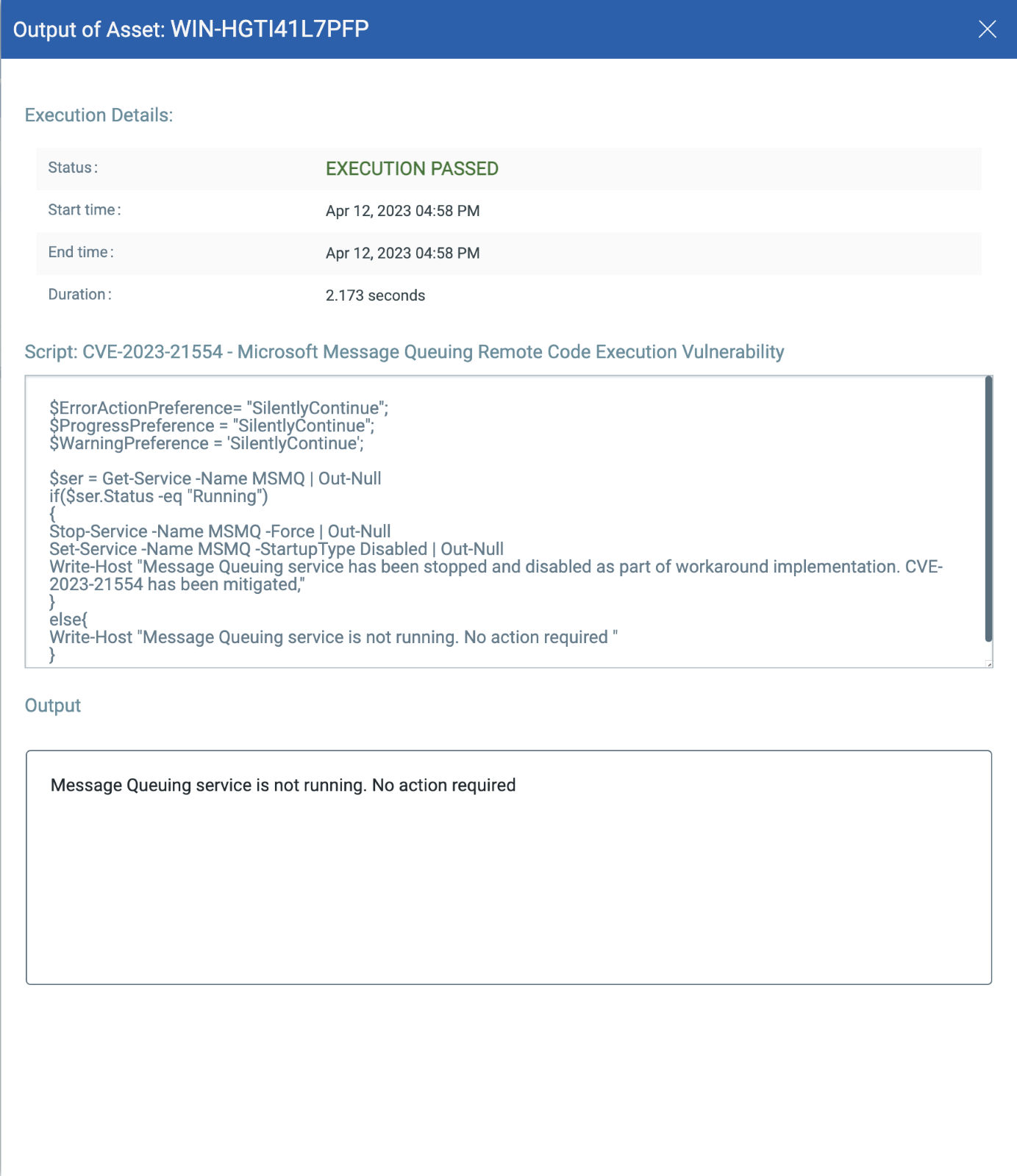
CVE-2023-21554: Microsoft Message Queuing Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 9.8 / 8.5
Policy Compliance Control IDs (CIDs):
- 4030 Status of the ‘Windows Message Queuing Service’
- 14916 Status of Windows Services
- 14297 Status of the open network connections and listening ports (Qualys Agent only)
The following QQL will return a posture assessment for the CIDs for this Patch Tuesday:
control.id: [4030,14916,14297,10472,10475,10474,13918,10473,16104,4026]

EXECUTE Mitigation Using Qualys Custom Assessment and Remediation (CAR)
Qualys Custom Assessment and Remediation (CAR) can be leveraged to execute mitigation steps provided by MSRC on vulnerable assets.
CVE-2023-21554: Microsoft Message Queuing Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
Exploitability Assessment: Exploitation More Likely
CVE-2023-28250: Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 9.8/10.
Exploitability Assessment: Exploitation More Likely

CVE-2023-28238: Windows Internet Key Exchange (IKE) Protocol Extensions Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5/10.
Exploitability Assessment: Exploitation Less Likely
CVE-2023-28244: Windows Kerberos Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
Exploitability Assessment: Exploitation Less Likely
Note: Scripts will be available in the CAR script library.
Qualys Monthly Webinar Series

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
These findings used to be reported in QID – enabling easy dashboard updating. Is this going to resume in future?
In recent previous months, we are reporting a number of Linux based vulnerabilities within the Patch Tuesday blog. Are these going to be separated in future to prevent customer reporting on Linux findings within Windows reporting?
The QID list is the same as for March 2023. Is that intentional ?