Citrix ADC and Gateway Remote Code Execution Vulnerability (CVE-2019-19781)

Last updated on: September 7, 2020
Update January 17, 2020: A new detection in Qualys Web Application Scanning was added. See “Detecting with Qualys WAS” below.
Citrix released a security advisory (CVE-2019-19781) for a remote code execution vulnerability in Citrix Application Delivery Controller (ADC) and Citrix Gateway products. The vulnerability allows an unauthenticated remote attacker to execute arbitrary code on the system. Once exploited, remote attackers could obtain access to private network resources without requiring authentication.
During the week of January 13, attacks on Citrix appliances have intensified. Because of the active attacks and the ease of exploitation, organizations are advised to pay close attention.
About CVE-2019-19781
The vulnerability affects all supported versions of Citrix ADC and Citrix Gateway products. As Citrix did not disclose many details about the vulnerability, the mitigation steps suggest the VPN handler fails to sufficiently sanitize user-supplied inputs. The exploit attempt would include HTTP requests with ‘/../’ and ‘/vpns/’ in the URL. The responder policy rule checks for string “/vpns/” and if user is connected to the SSLVPN, and sends a 403 response as seen below.
add responder policy ctx267027 “HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\”/vpns/\”) && (!CLIENT.SSLVPN.IS_SSLVPN || HTTP.REQ.URL.DECODE_USING_TEXT_MODE.CONTAINS(\”/../\”))” respondwith403
Detecting with Qualys VM
Qualys has issued QID 372305 for Qualys Vulnerability Management that includes authenticated and remote detections of vulnerabilities present in affected Citrix products. This QID is included in signature version VULNSIGS-2.4.788-2.
QID 372305 : Citrix ADC And Citrix Gateway Arbitrary Code Execution Vulnerability (CTX267027)
The QID contains a remote and an authenticated signature to check the presence of vulnerability in Citrix Products.
You can search for this new QID in AssetView or within the VM Dashboard by using the following QQL query:
vulnerabilities.vulnerability.qid:372305
vulnerabilities.vulnerability.cveId:`CVE-2019-19781`
This will return a list of all impacted hosts.
You can also create a Dashboard to track all Citrix vulnerabilities as shown in the template below:
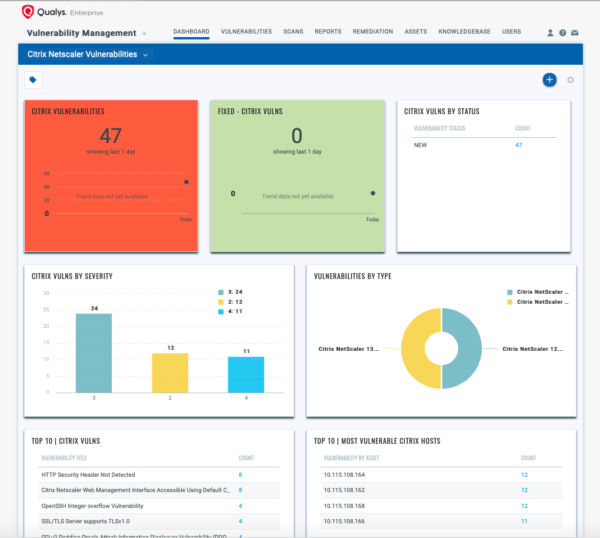
Detecting with Qualys Threat Protection
The fastest way to locate vulnerable hosts is though the Qualys Threat Protection Live Feed as seen here:
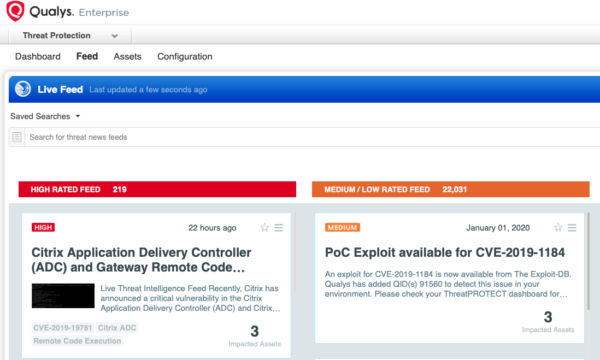
Simply click on the Impacted Assets number to see a list of hosts with this vulnerability.
Detecting with Qualys WAS
Qualys has released QID 150273 in Qualys Web Application Scanning (WAS) that includes a passive detection of vulnerabilities present in the affected Citrix products.
QID 150273 : Citrix ADC And Citrix Gateway Arbitrary Code Execution Vulnerability (CTX267027)
This detection is useful for customers using Qualys WAS in their environments, and it has the advantage of detecting both at the root level of the target being scanned and at the starting URL of the web application as specified in the WAS configuration.
The passive detection works by sending an HTTPS request and looking for evidence of the vulnerability in the response. If the scanned application is vulnerable, the QID will be reported in your Qualys WAS scan report.
Mitigation
Customers are recommended to apply Citrix’s Mitigation Steps for CVE-2019-19781 as soon as possible.
Customers can check their systems for exploit attempts using “grep” for requests that contain “vpns” and “..”.
A patch is expected from Citrix by the end of January 2020, and organizations are advised to install that patch as soon as it is available.