GDPR Is Here: Assess the Security Configurations of Your IT Systems
In prior installments of this GDPR compliance blog series, we’ve discussed the importance of key security practices such as IT asset inventory and vulnerability management. Today, we’ll focus on another core component for GDPR: policy compliance.
As we’ve stated before, to comply with the EU’s General Data Protection Regulation (GDPR), organizations must show they’re doing all they can to protect their EU customers’ personal data. Thus, InfoSec teams must provide a rock-solid security foundation that gives organizations superior data breach prevention and detection.
With a strong IT policy compliance program, organizations can deploy and manage their IT environment according to applicable government regulations, industry standards and internal requirements.
For organizations, it’s critical to establish a lifecycle for managing assets and controls to protect the data they contain. One must continuously: identify IT assets and scope, define control objectives, automate control assessment, prioritize fixes, and ultimately remediate the security configuration problems.
To be effective, this entire process must be trackable by auditors and must maintain the proper reports and dashboards necessary to drive continuous improvement. Organizations must have this knowledge not only to properly protect their EU customers’ personal data — the regulation’s core goal — but also to comply with other GDPR requirements.
After gaining complete visibility into their IT assets, organizations can create data maps and decide which technical controls it needs to secure EU residents’ personal data in a way that meets GDPR’s considerable expectations and strict requirements.

Qualys Policy Compliance Can Help with GDPR
With Qualys Policy Compliance (PC), organizations can validate and track access to the files and databases on the systems involved in the storage and processing of this data, wherever it resides — on premises, in clouds or on endpoints.
Qualys PC also helps organizations eliminate security configuration exposures, thus reducing the risk of unauthorized access, and enforce proper security controls with out-of-the-box mandate-based reporting for GDPR requirements.
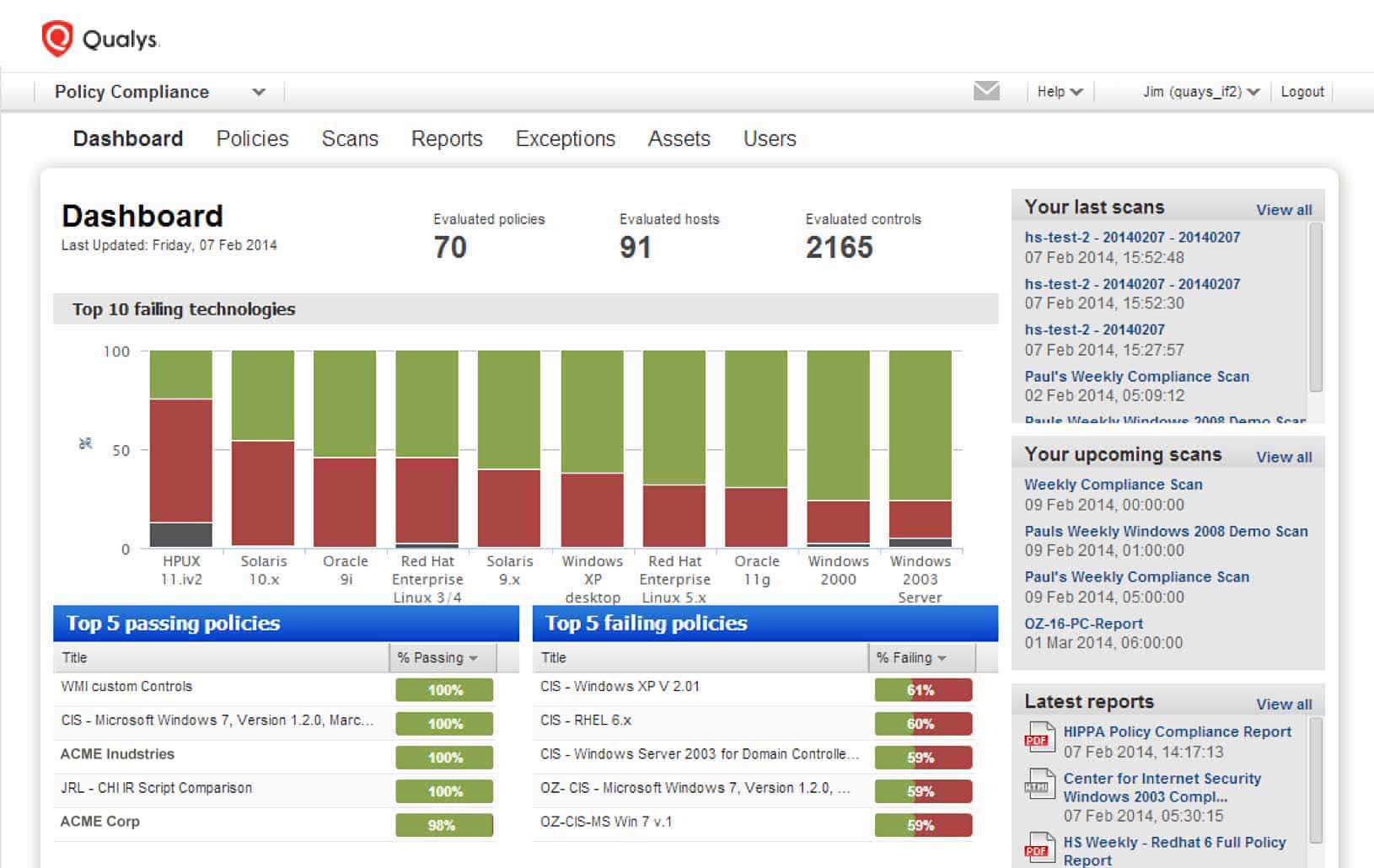
Among its many features and capabilities, Qualys PC provides organizations:
- complete visibility of their IT assets’ compliance status on premises, in cloud instances, and endpoints
- native templates and custom controls tailored for particular regulations including GDPR and other EU regional standards, as well as industry standards such as CIS Benchmark and DISA STIG
- the ability to automate the evaluation of requirements against multiple standards, so organizations can identify issues quickly and prevent configuration drift
- a repeatable and auditable process for compliance management with prioritized remediation reports and exception management workflow
- compliance data available in dashboards and reports for different constituents: CxOs, auditors, risk managers, IT
In addition to GDPR, Qualys PC can help you comply with many other regulatory, industry and internal IT policy requirements. It covers more than 100 CIS certified policies, more than 40 vendor and mandate policies and over 120 versions of 60-plus technologies.
This breadth of coverage and versatility makes Qualys PC uniquely qualified to help your organization overcome the challenges of IT policy compliance today, caused by trends such as:
- IT compliance requirements are increasing in number and complexity, as governments issue more regulations, industry groups release more mandates and organization’s own internal departments generate more policies.
- IT environments that were previously homogeneous, residing mostly on premises, are increasingly hybrid and distributed, as organizations pursue digital transformation benefits via the adoption of technologies such as cloud computing, mobility, IoT and others.
- The threat landscape is constantly changing, as hackers get more aggressive and their attacks more sophisticated, while the consequences of suffering security breaches are increasingly dire for affected organizations.

As part of the highly-scalable Qualys Cloud Platform, PC doesn’t require any software to install nor maintain — it’s accessed from the cloud via a web browser — and supports both remote scanning or agent-based assessment.
Along with PC, Qualys offers a growing suite of cloud-based, self-managed security and compliance apps for the needs of all your InfoSec and compliance teams, including those in charge of protecting on premises systems, public cloud infrastructure, web apps, DevSecOps environments and endpoint devices.
With Qualys PC, you will end up with the right controls and a repeatable assessment process for GDPR, so you can define compliance objectives, prioritize and remediate fixes, and document compliance in reports.
In our next post in this blog series, we’ll look into the importance of file integrity monitoring within the realm of your GDPR readiness efforts.
(Tim White is a Director of Product Management at Qualys)
To learn more about how Qualys solutions can help you become GDPR compliant, visit qualys.com/gdpr where you can download our free interactive guide.
Read the other blog posts in this GDPR series:
GDPR Is Here: Achieve Superior Data Breach Prevention and Detection with Qualys
GDPR Is Here: Manage Vulnerabilities and Prioritize Threat Remediation
GDPR Is Here: Assess Risk from Vendors and from Internal Teams