QSC18 Virtual Edition: Vulnerability Risk Management
 When vulnerability risk management is proactive, organizations don’t have to hurriedly react to attacks that exploit bugs for which patches are available, as happened with WannaCry.
When vulnerability risk management is proactive, organizations don’t have to hurriedly react to attacks that exploit bugs for which patches are available, as happened with WannaCry.
“The vast majority of WannaCry remediation took place as an emergency type process,” Jimmy Graham, a Qualys Director of Product Management, said during QSC18 Virtual Edition.
It’s key to have an integrated breach prevention program with asset inventory, vulnerability management, threat prioritization and patch management, he said.
Graham also outlined how Qualys can help customers comprehensively and proactively manage their vulnerability risk.
Read on to learn more.
WannaCry: A cautionary tale
Long before WannaCry erupted, organizations should have patched the vulnerability that the ransomware exploited. Instead, WannaCry infected 300,000-plus systems, disrupting critical operations globally.
Microsoft disclosed the Windows vulnerability (MS17-010) in mid-March 2017, rating it “Critical,” and issued a patch. In mid-April, the vulnerability became more dangerous with the EternalBlue exploit’s release.
When the attack began in mid-May, organizations had had two months to patch. Yet, Qualys data shows widespread patching was triggered by WannaCry.
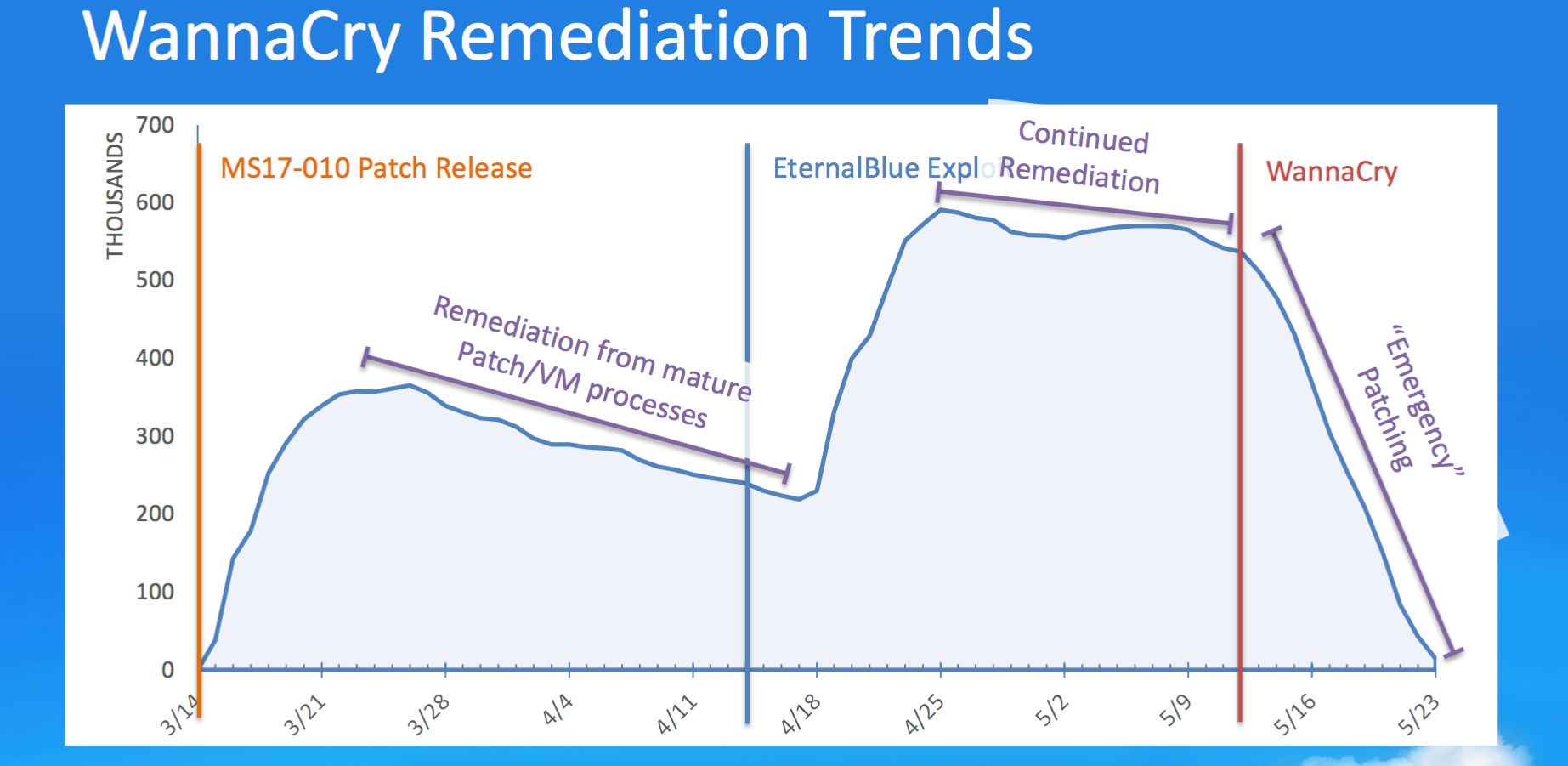
“Many more organizations should have been on that first batch that were remediating based on patch availability,” he said.
Patch management tips
Mature vulnerability risk management programs allow organizations to proactively remediate as patches are released, based on prioritization analysis.
Patch management should be done routinely, in sync with vendor patch cycles. “You shouldn’t have to wait for a vulnerability detection to start that patch management process,” he said.
Patch management should operate independently, with vulnerability management acting as a “check” on the remediation process. It’s also advisable to use agent-based scanning, and do frequent authenticated scans, so patching’s effectiveness becomes quickly clear.
“If you’re waiting a week to scan your systems, that’s a week before you know whether your remediation is working,” Graham said.
The value of integrated tools
An isolated patch management tool that’s not integrated with your asset inventory and vulnerability assessment apps carries disadvantages. In this scenario, correlating vulnerabilities to patches is hard and time-consuming, and prioritizing remediation becomes difficult.
Verifying that the patch cycle will resolve all prioritized vulnerabilities is another challenge when different IT teams must share this data via reports and spreadsheets. “There’s no good way to confirm that those patches are fixing the vulnerabilities,” he said.
A siloed patch management tool also slows down the time to remediation, making it hard to be nimble about patching high-profile vulnerabilities in particular. Comprehensiveness of coverage is affected, as on premises tools often can’t patch roaming and remote assets, or they only patch assets from one OS, like Windows or Linux.
Qualys Patch Management
Qualys Patch Management (PM), which enters beta in Q3, addresses challenges of existing products by:
- Discovering missing patches on assets
- Correlating with vulnerabilities from scans
- Prioritizing remediation based on real time threat information
- Providing broad, agent-based OS coverage, including Windows, MacOS, and Linux
With Qualys PM, Quayls rounds out its breach prevention stack, which includes IT asset visibility with the AssetView service and Asset Inventory app (beta), vulnerability detection with Qualys Vulnerability Management, and threat prioritization with Qualys Threat Protection.
Qualys VM detects vulnerabilities across all IT assets — on-premises, in clouds and at remote endpoints. Qualys AV combines vulnerability information with assets’ inventory data, providing a unified view of IT and security data. Qualys AI refines asset data by normalizing and enriching it. Qualys Threat Protection layers real time threat information on top of the vulnerability detections, for prioritizing remediation across all assets.
Qualys PM’s key features
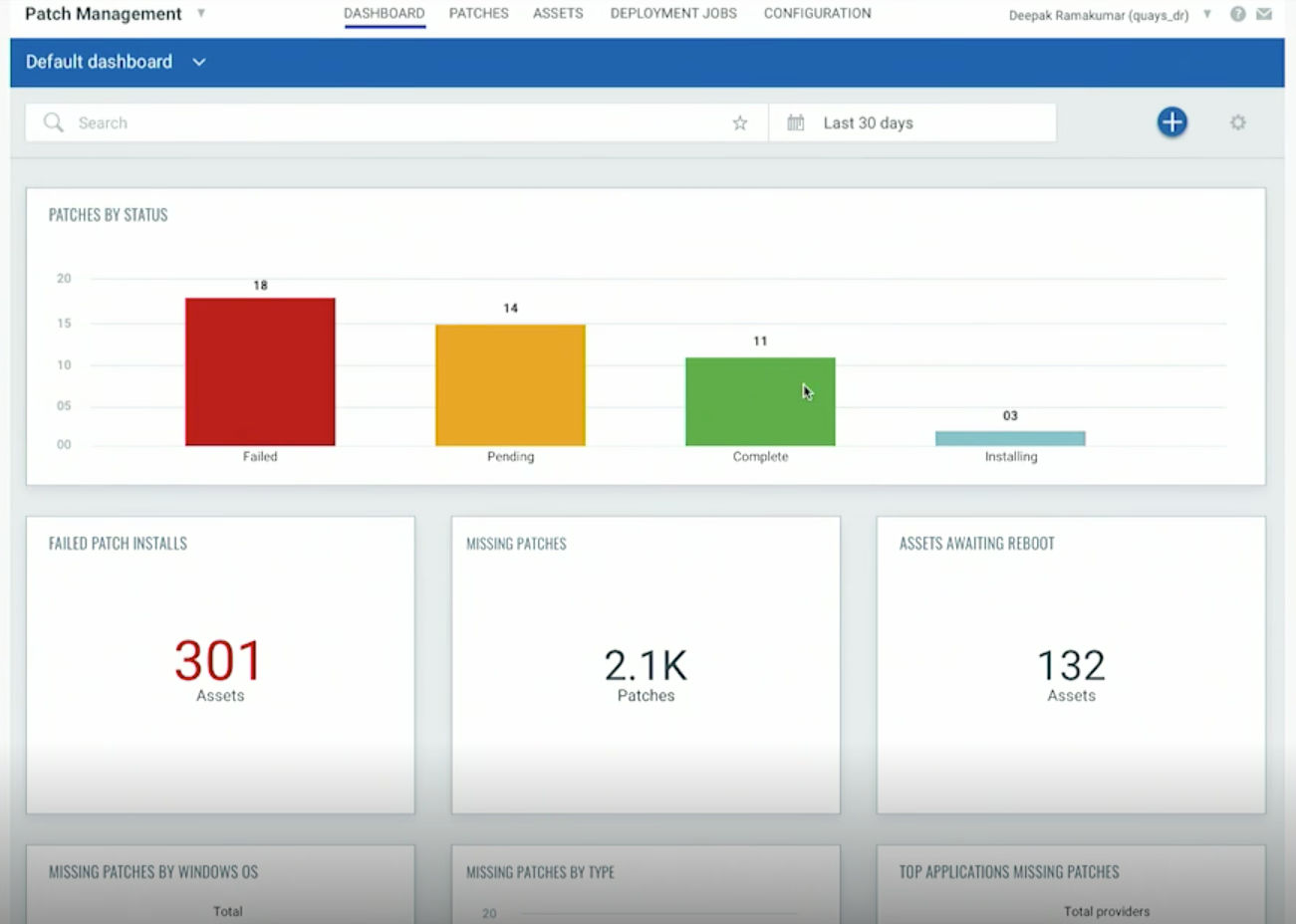
Qualys PM keeps organizations up to date on missing patches. It evaluates patch detections on the same schedule as vulnerabilities, and recommend by default a patch’s most current version. Its configurable dashboards and reporting functionality allows organizations to track patch status.
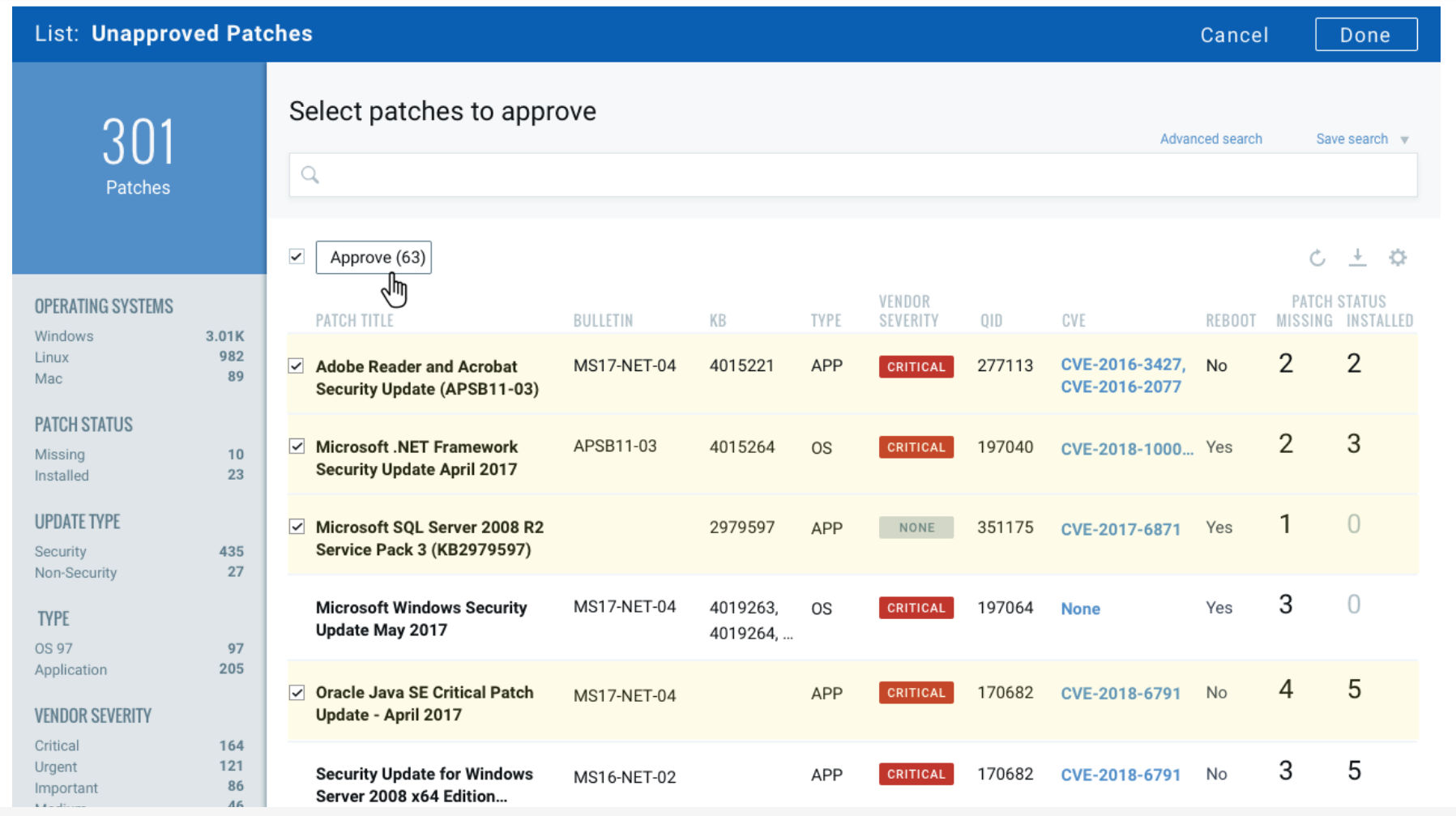
Qualys PM also correlates vulnerability and patch data, so organizations know which vulnerabilities are fixed by a specific patch, as well as which patches fix a specific vulnerability.
Because it uses the Qualys Cloud Agent, as other Qualys apps do, Qualys PM simplifies tasks for security teams, which can use the same agent for multiple apps. The agent allows Qualys PM to work on internal, roaming and cloud-based assets.
Qualys PM can be used for scheduled patching, and for one-off jobs, like emergency patches. It unifies reporting and visibility, so organizations have in one place all the information about vulnerabilities, patches, and issues that must be remediated urgently.
With Qualys PM, organizations can shift from reaction mode to proactive operational security. “It allows IT and security to speak the same language in the context of assets and vulnerabilities,” Graham said.
Watch the on-demand version of Graham’s presentation, which goes into detail on these and other topics, features demos of Qualys PM and other apps, and includes a Q&A with the audience.