Graboid: Revenge of the Worms
This week saw news of self-propagating worms in the container landscape to perform unsanctioned computation tasks such as cryptojacking. This blog post is intended for Qualys customers and partners to understand how such container attacks work, provide security best practice recommendations & walkthrough related Qualys product portfolio functionality.
Background
Containers usage is mainstream today and enterprises are leveraging containers for their workload deployments across a number of different types of private and public cloud infrastructure. This has been driven mainly by development, devops teams for reasons relating to development velocity & infrastructure utilization/efficiency.
As with any new technology, the security conversations often lag technology adoption. Containers are no different. Best intentions of developers, devops teams not withstanding it does require a well thought out security strategy to think through the attack surface for containers and put in place a security program/tooling to address related risks.
What’s New?
Qualys threat research has been tracking developments (1, 2, 3, 4) in the container threat landscape given the widespread usage of containers and the risks the container attack surface poses to enterprises. This year saw new frontiers in the container threat landscape with attacks on the ecosystem (Docker Hub breach, DockerHub Malware).
This week saw news of self-propagating worms in the container landscape to perform unsanctioned computation tasks such as Cryptojacking. When Cryptomining is done without authorization it is referred to as Cryptojacking. While the security implications are alarming, in elastic public cloud environments these incidents have financial implications as well.
How Do These New Container Threats Work?
At a high level, attackers find a weak point in the container pipeline and introduce the malicious code into a container image. Some examples include:
- Compromising a container host via a vulnerability and introducing containers with malicious code. The most recent incidents have leveraged insecure container engines as the attack point. (Don’t expose the docker socket in an insecure manner. Secure it).
- Without any authentication or authorization, a malicious actor can take full control of the Docker Engine (CE) and the host. The attacker leverages this entry point to deploy and spread the worm.
- Supply chain attacks by introducing malicious container images in the container pipeline (e.g. Container Registry, Container Repository)
- Compromising a running container and introducing malicious code
Qualys Security Best Practice Recommendations
Qualys recommends the following security best practices for customers with concerns around these latest types of container attacks.
- Secure your container hosts in the scope of a vulnerability management and an EDR program. Qualys Vulnerability Management, Indication of Compromise, Threat Protection, and File Integrity Monitoring are products that address these use cases.
- Include your container hosts in scope of a compliance program to check for misconfigurations around open Docker hosts, etc. Qualys Policy Compliance has a number of controls in place to address such use cases, e.g. CIS Benchmarks for Docker
- Shift left with a comprehensive DevSecOps container security program. Qualys Container Security addresses use cases for container security across the container pipeline. In particular Qualys CS provides comprehensive inventory of containers via various sensors (Qualys Cloud Agent, Qualys Network Scanner, Qualys Container Sensor) and provides for security assessment of containers (Vulnerability scanning) and runtime protection (Dynamic hardening of containers).
Qualys Product Walkthrough for Use Cases Related to this Attack Scenario
- Qualys Global IT Asset Inventory – Utilize Qualys’s free offering to get visibility into container hosts, container images and running containers. (Via Qualys Network Scanner, Qualys Cloud Agent).

- Qualys Policy Compliance – Obtain compliance posture of container deployments. Specific controls available to customers include CIS Docker benchmarks. Some specific examples below
- Controls available to check for security configuration posture of the Docker Daemon (Docker Socket)
- Status of the TLS key file (‘tlskey’ flag) set for the Docker daemon on the host system (Control ID 10765 , Signature 810014)
- Status of the TLS certificate file (‘tlscert’ flag) set for the Docker daemon on the host system (Control ID 10766, Signature 810015)
- Status of the TLS CA certificate file (‘tlscacert’ flag) set for the Docker daemon on the host system (Control ID 10767 , Signature 810016)
- Status of the TLS authentication (‘tlsverify’ flag) set for the Docker daemon on the host system (Control ID 10768, Signature 810017)
- For customers using an authorization plugin for the docker daemon, Qualys Policy compliance has the following controls
- Status of the use of authorization plug-in for the Docker daemon on the host system (Control ID 10772, Signature 810022)
- Controls available to check for security configuration posture of the Docker Daemon (Docker Socket)
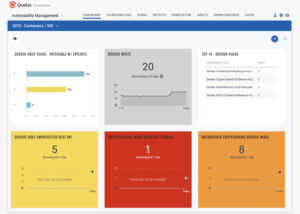
- Qualys Vulnerability Management – Utilize to obtain vulnerability posture of container hosts. Following is a list of detections Qualys has in place to detect vulnerabilities, compromised container images (Current, Coming shortly)
- Qualys Container Security – Utilize to obtain enhanced inventory, security posture of container images, running containers across the container pipeline (CICD build scanning, Registry scanning, Running container scanning). This requires installing the Qualys container sensor on the docker host. Qualys recommends the following security workflows as part of a container security program to proactively detect exposure to such threats, detect compromised containers and remediate accordingly.
-
- Obtain container inventory via your existing Qualys deployments (Network Scanner, Cloud Agent). Install Qualys Container Security Sensor to obtain enhanced visibility, security posture.
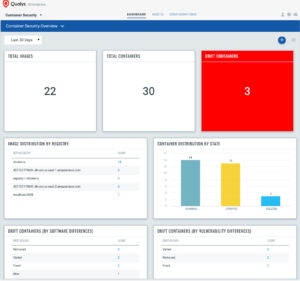
- Detect container drift from underlying container image (Drift by vulnerabilities, Drift by software packages). These could stem from malicious behaviors from compromised containers.
-
- Detect unknown images (potentially malicious) via a flexible QQL query in Qualys Container Security
- Look for images which are not from specific registries: not(repo.registry:`docker.io`)
- Look for images which are not scanned in CICD pipeline and/or the registry: not source:[CICD, REGISTRY]
- Utilize Qualys Container runtime security from our layered insight acquisition. More specifically this offering is a function-level firewall that allows customers to block granular behaviors (e.g. httpd spawning a shell) and thus harden containers against attacks leveraging vulnerabilities (e.g. Runc vulnerability). This is integrated into the Qualys platform and is going to be available shortly to customers as part of an early preview
- Detect unknown images (potentially malicious) via a flexible QQL query in Qualys Container Security
As someone once supposedly said, “History doesn’t repeat, it rhymes”. Et Tu Containers? Time for folks to update this wikipedia page here with the latest in the worm threat landscape.
For existing customers, please contact your Technical Account Manager to set up a free trial for any of the Qualys cloud apps mentioned above.