How Policy Compliance Plays a Mitigation Role to Protect Your System
Vulnerabilities can be serious threats. Once found, system administrators try everything to restore security, such as patching and mitigating. Patching is always the first choice since it’s normally the definitive way to resolve the vulnerability. However, system administrators will sometimes need to mitigate, especially in two cases:
Case 1. A patch has not been released by the vendor.
Case 2. Patching the vulnerability isn’t a high priority in the customer’s environment but still needs to be addressed.
Many vulnerabilities can be mitigated by changing a specific configuration setting in the OS or application. In this blog post, I use HTTPoxy as an example of how Qualys Policy Compliance can play an important role in this type of mitigation by identifying and reporting on all your systems that don’t have the desired configuration.
HTTPoxy
On July 18, 2016, a vulnerability named HTTPoxy was announced, affecting server-side web applications that run in CGI and CGI-like environments. It comes down to a simple namespace conflict because RFC 3875 (CGI) puts the HTTP Proxy header from a request into the environment variables as HTTP_PROXY, and unfortunately, HTTP_PROXY is also a popular environment variable used to configure an outgoing proxy. So, if a vulnerable HTTP client makes an outgoing HTTP connection, while running in a server-side CGI application, then a malicious attacker can use the HTTP Proxy header to control where the vulnerable HTTP client proxies the outgoing request to.
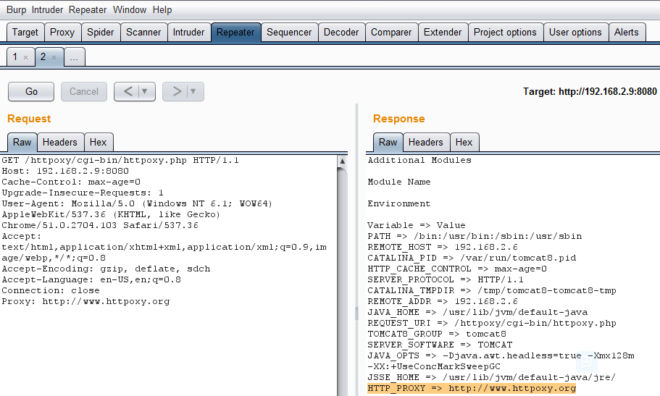
As a demo, please refer to the following screenshot which was processed by Apache Tomcat on Ubuntu:
So following section 4.1.18 in RFC 3875, if the protocol used is HTTP, then the HTTP header field name is converted to uppercase, all occurrences of “-” are replaced with “_”, and “HTTP_” is prepended to give the meta-variable name. Users need to be aware of that when using an vulnerable HTTP client to construct an outgoing HTTP request since it can be overwritten with a malicious value.
Policy Compliance Can Play a Mitigation Role
For mitigations that are implemented via a specific configuration, Qualys Policy Compliance can check your systems and report those that don’t have the configuration and are therefore still at risk, so that you can update those systems.
The HTTPoxy site and the official Apache advisory describe the methods to patch or mitigate this vulnerability. Some applications have released a new official patch or version, while others have not. Apache Tomcat, for example, has not yet released a new version to officially fix the vulnerability, but has a few configuration-based options (among others) for mitigation.
One such mitigation is to prevent using the CGI servlet by setting “privileged” to “false” on the Context element for your web application. In this case, customers can use the following Qualys Policy Compliance CID to scan all their related targets and find those that don’t have this configuration.
CID 9614 – Status of the ‘privileged’ attribute within ‘context.xml’ file
For Apache HTTP Server, customers can use the following CIDs to detect the status of related modules, which advise customers to disable if they are not necessary for your system:
CID 10585 – cgi_module
CID 10586 – cgid_module
CID 10588 – isapi_module
CID 10589 – fcgid_module
CID 10590 – proxy_fcgi_module
For customers who follow the advisory to enable `header_module` and set “RequestHeader unset Proxy early” for keeping the CGI feature and removing “Proxy” from the header, the following CIDs can help you to detect if all your targets have them set:
CID 10587 – Status of headers_module module
CID 10591 – Status of “RequestHeader” directive at the server level
So now you can see how Policy Compliance can help protect your systems by identifying those that are not configured to mitigate this issue. This enables your IT teams to then update their configurations. In the future, we will have more to say about vulnerability mitigation from Policy Compliance.
Reference:
- https://httpoxy.org/
- https://www.apache.org/security/asf-httpoxy-response.txt
- https://tools.ietf.org/html/rfc3875