New ‘Silence’ Banking Trojan copies Carbanak to Steal from Banks (Analysis with IOCs)
Dark Reading is reporting on a new banking trojan called ‘Silence’ that mimics techniques similar to the Carbanak hacker group targeting banks and financial institutions. The attack vector is similar – target individuals using spear-phish emails to trick them into running a malicious attachment which will connect to download a dropper to further infect the user’s machine. This attack does not use an exploit against a vulnerability, but rather takes advantage of social engineering to fool the user into executing the malicious payload and infecting their machine.
Silence is interesting in that the trojan’s capabilities include a screen grabber that will take multiple screenshots of the user’s active monitor and upload the real-time stream to a command and control server for monitoring by the adversary. This technique allows the threat actor to identify which users have access to specific banking applications, systems, and accounts that they can use for financial gain.
Typical of most targeted organized crime attacks, anti-virus detection is low and slow to respond. As of 48 hours after first detection, less than 50% of anti-virus vendors have detections for this Trojan as reported by VirusTotal. For enterprises that are not running the latest virus signature definitions or not configured for highest detection level due to excessive resource consumption on the endpoint impacting user experience, the Silence Trojan will be missed and will continue operate without detection. Carbanak operated from the end of 2013 to early 2015 (15+ months) without detection and the hacker group was able to exfiltrate $1 Billion from financial institutions over that time period.
Visibility Beyond Anti-Virus: Use Qualys Indication of Compromise (IOC) to find ‘Silence’ Trojan
Qualys Indication of Compromise (IOC) is a cloud app that leverages the same single lightweight Qualys Cloud Agent that enterprises already deploy on servers, user endpoints, and cloud instances for Vulnerability Management, Policy Compliance, and Asset Inventory.
Qualys IOC running on Cloud Agent uses an optimized capability to collect and send file, process, mutex, registry, network connections, and corresponding metadata to the Qualys Platform for cloud-based storage, querying, and processing for assets on and off the network. Event metadata includes MD5 and SHA256 file hashes, process arguments, mutex process names and PIDs, network connections, and more.
Searching for Silence Trojan file hashes is simple and fast using the web-interface and backend Elasticsearch and Cassandra architecture of the Qualys Platform.
MD5
- 404d69c8b74d375522b9afe90072a1f4 [dropper]
- 15e1f3ce379c620df129b572e76e273f
- D2c7589d9f9ec7a01c10e79362dd400c
- 1b17531e00cfc7851d9d1400b9db7323
- 242b471bae5ef9b4de8019781e553b85 [screen activity gathering module]
- 324D52A4175722A7850D8D44B559F98D
- 6a246fa30bc8cd092de3806ae3d7fc49 [C&C communication module]
- B43f65492f2f374c86998bd8ed39bfdd
- cfffc5a0e5bdc87ab11b75ec8a6715a4
Qualys IOC Hunting
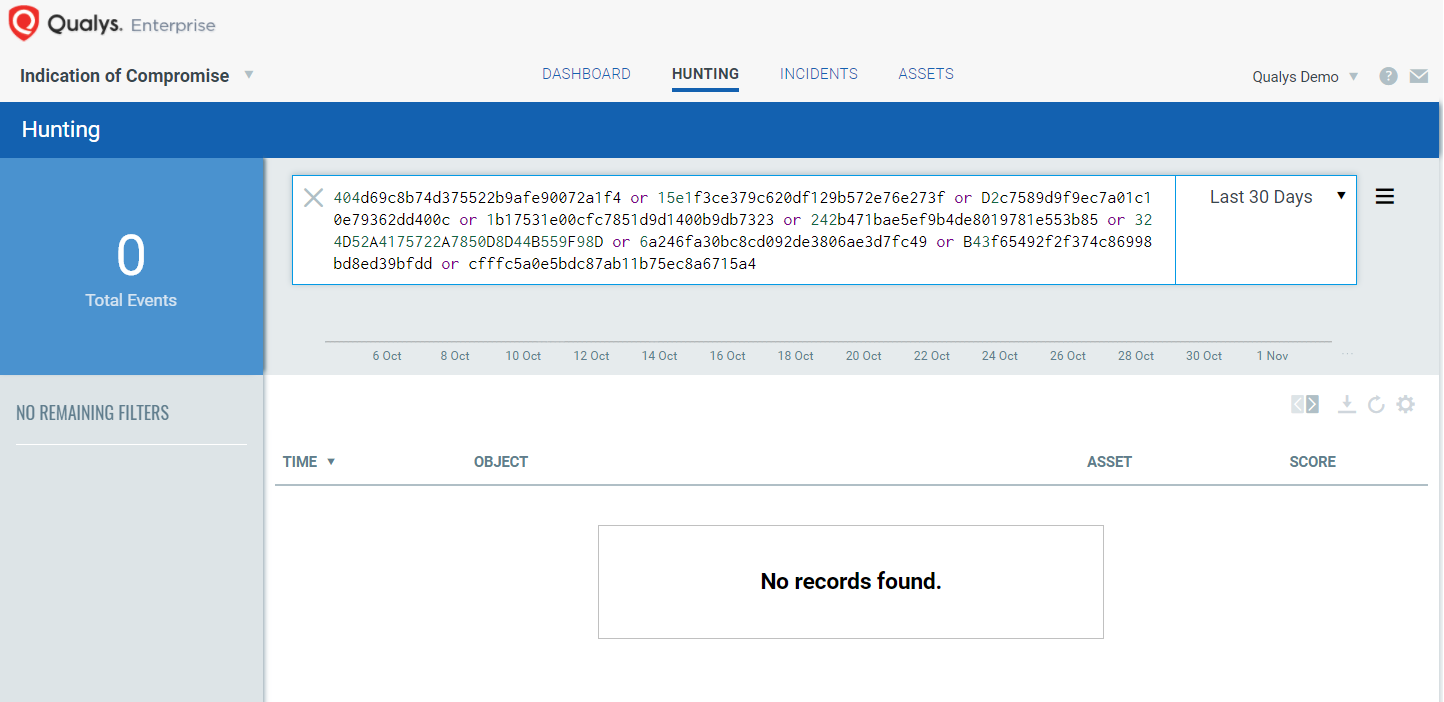
Create a search widget with conditional formatting to display in real-time when any endpoint running Qualys IOC finds file hashes attributed to the Silence Trojan.
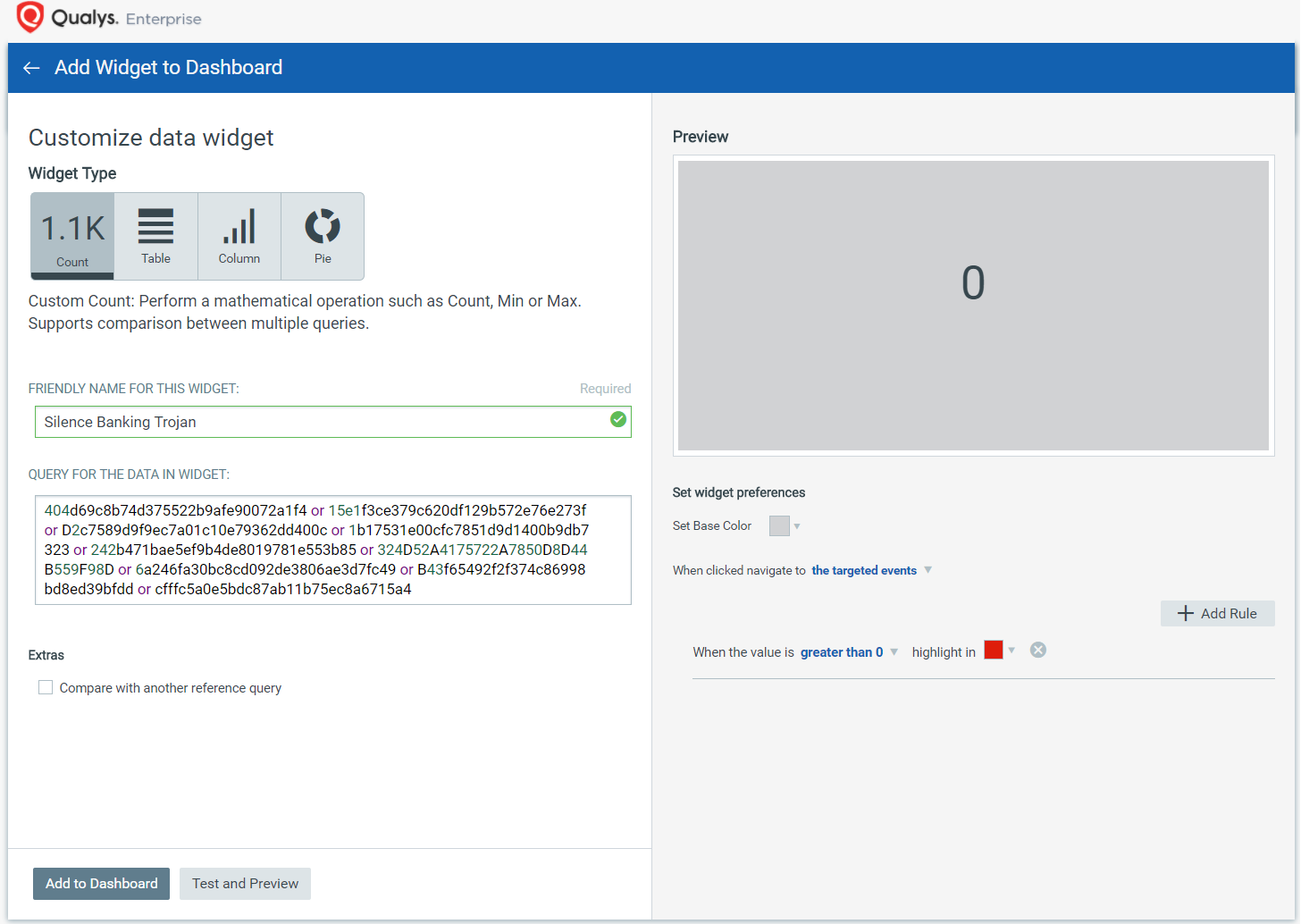
The search widget drills into the hunting capabilities to search by hash, file/process name, mutex, registry, network connection, and many other event metadata including complex Boolean and nested search logic.
Learn More about Qualys IOC
Qualys Indication of Compromise expands the capabilities of the Qualys Cloud Platform to deliver threat hunting, detect suspicious activity, and confirm the presence of known and unknown malware for devices both on and off the network. Leveraging the same Qualys Cloud Agent already deployed for an organization’s asset inventory, vulnerability management, and policy compliance programs, Qualys now consolidates even more security functions.