Cryptomining is all the rage among hackers, as DDoS amplification attacks continue
 In this week’s InfoSec news review we’ll dive into cryptomining, get the latest on DDoS amplification, go over recent data breaches, and check out another vendor claiming it can crack iPhones.
In this week’s InfoSec news review we’ll dive into cryptomining, get the latest on DDoS amplification, go over recent data breaches, and check out another vendor claiming it can crack iPhones.
I, me, mine
The freight train that’s cryptomining shows no sign of slowing down, and the cyber security implications are intensifying accordingly.
This week alone, Microsoft detected and disrupted a massive cryptomining malware campaign, a Tesla AWS account got hijacked, a new mining worm was discovered, and Kaspersky researchers warned about increased sophistication of infection methods.
While there is a legitimate component to this business, malicious hackers eager to profit are aggressively breaching networks and infecting devices — PCs, IoT systems, smartphones, servers — to steal computing power for mining virtual currencies.

The creation and verification process of virtual currencies like Bitcoin and Monero involves solving lengthy and complex mathematical calculations that require large amounts of computing power. Those involved in this “blockchain” process earn money from it, and the payouts have skyrocketed as the value of these cryptocurrencies has dramatically increased in the past several months.
That has attracted the attention both of legitimate players — individuals and businesses — and, unfortunately, of bad actors, who are using malware to gain unauthorized access to systems they then leverage for mining.
“Exploit kits are now delivering coin miners instead of ransomware. Scammers are adding coin mining scripts in tech support scam websites. And certain banking trojan families added coin mining behavior,” Microsoft’s Windows Defender team stated in its blog post.
Between September and January, the number of websites hosting cryptomining scripts spiked 725%, Cyren Security Lab said recently. That figure includes domains that are hosting these scripts knowingly, as well as those that have been breached.
Cryptomining attacks are purposefully stealthy and silent: They avoid noticeably disrupting breached systems’ operations in order to remain undetected. “For coin miner malware, persistence is key. These types of malware employ various techniques to stay undetected for long periods of time in order to mine coins using stolen computer resources,” reads Microsoft’s blog post.
Thus, cryptomining gives hackers “all of the financial upside” of ransomware and other attacks without having to engage the victim and while drawing less law enforcement attention, Cisco’s Talos unit explained in late January.
As industry analyst Jason Bloomberg put it in a Forbes column recently, “ransomware is oh, so 2017,” as “smart hackers have turned to illicit cryptomining to fill their coffers” lured by a perfect storm of “easy money, slim chance of detection, and billions of unsuspecting targets that may not even care they’ve been hacked.”
Last month, Imperva reported that cryptomining now drives almost 90% of all remote code execution attacks. Kaspersky Lab put the number of users attacked by malicious miners at 2.7 million in 2017, up 50% from 2016. And according to Check Point, 23% of global organizations were affected in January by the Coinhive crypto-mining malware.
Meanwhile, Malwarebytes Labs ranks malicious cryptomining as its top detection since September. While acknowledging that malicious cryptomining appears to be far less dangerous to the user than ransomware, Malwarebytes Labs warned that its effects should not be underestimated. “Indeed, unmanaged miners could seriously disrupt business or infrastructure critical processes by overloading systems to the point where they become unresponsive and shut down,” reads the Malwarebytes Labs post.
Organizations that have been compromised in recent months include the U.K.’s Information Commissioner’s Office (ICO), U.S. federal courts, Australian state governments, and the LA Times newspaper.
Attack targets have included vulnerable Jenkins servers, unsecured Docker containers, Microsoft Windows systems, and browsers. Hackers have used multiple types of attack vehicles, including malvertising, email, malware-laced apps, targeted hits, and exploit kits.
For example, the coin mining campaign detected by Microsoft’s Windows Defender team this week used variants of the Dofoil/Smoke Loader malware in the form of sophisticated trojans with “advanced cross-process injection techniques, persistence mechanisms, and evasion methods.”
The Dofoil trojans attacked Explorer.exe with a “process hollowing” code-injection technique that created a new instance of the “c:\windows\syswow64\explorer.exe” process and replaced the legit code with malware.
“The hollowed Explorer.exe process then spins up a second malicious instance, which drops and runs a coin mining malware masquerading as a legitimate Windows binary, wuauclt.exe,” Microsoft explained. Dofoil uses a customized mining application that can mine different cryptocurrencies. To avoid detection, Dofoil modifies the registry, according to Microsoft.
And let us not forget good, old physical — aka, real world — security breaches. The Associated Press reported that crooks stole 600 servers from data centers in Iceland that were being used for cryptomining. The servers, which haven’t been found, are worth $2 million, and were swiped in a series of four heists in December and January. So far, 11 people have been arrested in connection with the investigation.
Memcached servers used for DDoS attacks
Last week, we reported on the troubling trend among hackers of using unprotected Memcached servers to dramatically amplify the intensity of their DDoS attacks. GitHub was on the receiving end of such a DDoS attack last week, which at the time was considered the most intense ever.
Well, that record lasted for only a few days. This week, Arbor Networks detected an even stronger DDoS attack against an unnamed customer of a U.S.-based service provider. The attack, according to Arbor Networks, reached 1.7Tbps at its peak and utilized the same Memcached reflection/amplification attack vector involved in the GitHub attack, which peaked at 1.35Tbps.
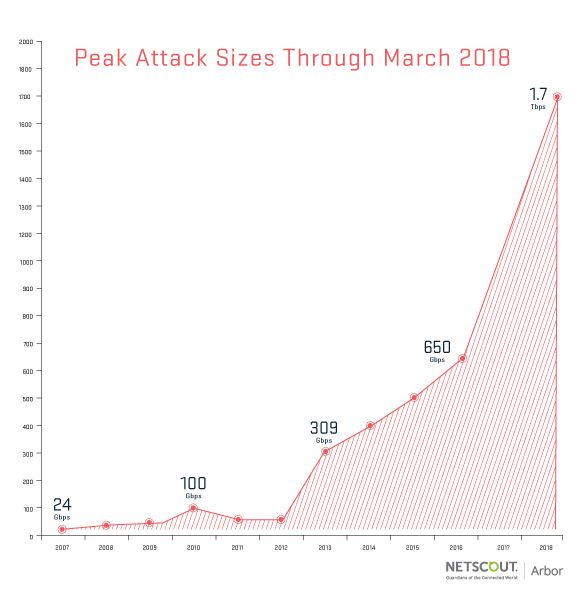
The open source Memcached software is meant to be used behind firewalls on internal networks to boost server performance, but many organizations have made them available from the Internet, and hackers are using them to significantly boost their DDoS attacks.
“While the internet community is coming together to shut down access to the many open Memcached servers out there, the sheer number of servers running Memcached openly will make this a lasting vulnerability that attackers will exploit,” reads Arbor Networks’ blog post.
For detailed information about this trend, in which attackers leverage the User Datagram Protocol (UDP), check out the write-ups from Akamai, Link11 and Cloudflare.
“An attacker spoofing the UDP address of their intended victim can send just a small packet of data to a Memcached server, tricking it into blasting as much as 50,000 times more data in response,” wrote security analyst Graham Cluley. “The result? A data tsunami.”
In encouraging news, eWeek reported on Friday that patching efforts were starting to make a dent on these amplified DDoS attacks, according to the latest data gathered by Arbor and Cloudflare. “We’re still seeing lots of them, but their average size is considerably smaller due to ongoing cleanup and mitigation efforts,” Steinthor Bjarnason, senior network security analyst at Arbor’s Netscout unit, told eWEEK.
Another digital forensics vendor claims it can crack iPhones
On the heels of Cellebrite’s recent claims that it can unlock and extract data from devices running all modern iOS versions including the most recent one, another digital forensics vendor is quietly making similar promises.
Forbes reported this week that a “mysterious” company called GrayKey is distributing marketing materials that describe online and offline tools that allow it to unlock devices running iOS 10 and iOS 11, including the latest iPhone X.

Forbes’ February report on Cellebrite’s claims — which extend to Android devices as well — generated a lot of concern among privacy and security experts.
Cellebrite has been telling its customers, which are primarily government, military and corporate investigative teams, that it’s able to unlock and extract data from devices running iOS 11, such as the iPhone X, as well as other iPhones, iPads and iPods.
Concerns center on the possibility that whatever technique and knowledge Cellebrite — and now apparently GrayKey — may possess could fall into the hands of criminals, be independently replicated by bad actors, or be abused by governments.
The situation also highlights the ongoing tug-of-war between tech vendors and law enforcement agencies, as the former resist watering down encryption on their products, while the latter argue they need access to devices and data for their investigations.
Speaking of law enforcement’s distaste for strong encryption
This week FBI Director Christopher Wray, speaking at Boston College’s second annual cybersecurity summit, reiterated his agency’s opposition to “unbreakable encryption,” saying it creates “a major public safety issue,” according to a CSO Magazine report.
Saying that in fiscal 2017 FBI investigators failed to retrieve the contents of 7,775 devices to which judges had granted them access, Wray “made an impassioned appeal for help from the tech sector and the security community,” CSO reported.
In related news, it transpired this week that the FBI has established close collaboration with Best Buy’s Geek Squad team of computer repair technicians. According to documents obtained by the Electronic Frontier Foundation (EFF), the FBI has been paying Geek Squad staffers for years for tips about illegal material they may find in the computers they’re fixing.
Data breach included with your meal, your video game and your credit report

The Applebee’s restaurant chain recently discovered malware in the POS (point of sale) systems of more than 160 of its eateries. At risk: Customers’ names, credit and debit card numbers, expiration dates and card verification codes.
The incidents occurred in recent months, going back to November of last year, but Applebee’s didn’t discover the issue until mid-February.
“We’re seeing more of these types of breaches happening… it’s an industry wide problem as more retailers look to an ecosystem of providers to bring in third party systems like point of sale and inventory management solutions,” Fred Kneip, CEO of security firm CyberGRX told Threatpost. “As of today a lot of stores are playing catch up with security, and it can take months or years to realize that compromises have happened on third party systems.”
Meanwhile, customers of games developer Nippon Ichi Software (NIS) America are also at risk for credit card fraud and ID theft, after two of its online stores — NIS America and SNKonlinestore — were hacked.

The breach occurred on Jan. 23 and wasn’t discovered until Feb. 26. Compromised data included customer name, address, credit card number, expiration date, security code, and email address.
According to the email NIS America sent to customers — as re-printed by NintendoLive.com — customers were redirected to an external web page where their information was captured, before being sent back to the company’s online store to complete the transaction.
And in the latest chapter of the monster data breach that just keeps on giving, Equifax disclosed that there are another 2.4 million Americans whose personal data was stolen by hackers in last year’s infamous and massive hack. That ups the total of people affected to about 148 million. The data thieves accessed Equifax’s systems and data by exploiting the Apache Struts CVE-2017-5638 vulnerability, for which a patch was available.
In other InfoSec news …
- Duo Security, which provides a two-factor authentication app, is detailing a serious flaw it recently fixed in its product as well as the flaw’s root cause — SAML vulnerabilities — which also affects third-party products and services. “Duo disclosed the problem responsibly late last year, and after giving vendors – including itself – time to fix the bug, has now gone public with an excellent and educational explanation of what went wrong,” writes Lisa Vaas in Sophos’ Naked Security blog.
- Facebook’s Oculus Rift VR headsets temporarily stopped working after the company let its security certificate lapse.
- MoviePass CEO Mitch Lowe set off privacy alarms when he boasted this week during a keynote address that his company’s eponymous app has such an ability to track its subscribers — including via GPS data — that “we know all about you.” After the inevitable backlash, the company the next day announced it was removing the app’s location tracking features.
With the Qualys Cloud Platform and its suite of natively integrated, self-updating security and compliance Cloud Apps, Qualys provides automated, continuous and scalable prevention and response. Qualys offers customers complete and instant visibility of IT assets wherever they reside — on premises, in clouds, and remote endpoints; comprehensive and continuous vulnerability management; granular assessment of secure system configurations; monitoring of file integrity; web application scanning and firewall; detection of compromise; and multiple other security and compliance solutions.