Staying Safe in the Era of Browser-based Cryptocurrency Mining
 Qualys Malware Research Labs is announcing the release of Qualys BrowserCheck CoinBlocker Chrome extension to detect and block browser-based cryptocurrency mining, aka cryptojacking.
Qualys Malware Research Labs is announcing the release of Qualys BrowserCheck CoinBlocker Chrome extension to detect and block browser-based cryptocurrency mining, aka cryptojacking.
Cryptojacking
Cryptojacking attacks leverage the victim system’s resources via malicious JavaScript to mine certain cryptocurrencies. Attackers carry out these attacks by infecting popular sites with JavaScript that enables cryptojacking. Any visitor to such sites will download the JavaScript and unknowingly contribute its system resources to mine a cryptocurrency that is added to the attacker’s wallet. The resource-intensive mining process is carried out on victim systems typically consumes more than 70% of CPU, that reduces system performance, increases power consumption and can cause possible permanent damage to the system.
Because cryptojacking helps attackers earn cryptocurrency without spending a dime on mining infrastructure, it is very profitable. The overall cryptocurrency market capitalization has reached more than $270 billion as of July 2018 with more than 1700 active projects! There is a lot of money to be made for attackers leveraging these projects, and cryptomining is gradually moving to the center stage of threat landscape as an even more attractive option compared to the recent favorite ransomware campaigns.
Cryptojacking has also gone mainstream recently because it is safer for cyber criminals and webmasters than ransomware, which requires interaction with the victim to collect payment. And because cryptojacking is browser based, it is easier to infect victims than hacking into servers. As cryptomining becomes more resource-intensive over time in terms of compute power and electricity consumption required, stealing those resources is becoming more enticing to attackers.
Cryptojacking and Monero
Monero (XMR), a relatively new cryptocurrency, is becoming a more common target of cryptojacking attackers because its mining algorithm (CryptoNight) is designed for easy integration and because its privacy and anonymity features also benefit hackers. Monero’s proof-of-work mining algorithm can be used with desktop- or server-grade CPUs rather than custom-built specialized ASIC or GPU hardware that is required for traditional coin mining algorithms. This is an important aspect of new generation cryptocurrency, as it tries to be decentralized and avoid enabling a small set of users with access to specialized hardware from creating a mining monopoly. From an attacker’s standpoint, the possibility of making sizable profits off desktop-grade CPUs with added privacy is a lucrative option.
A popular technology used in most browser based cryptocurrency mining algorithms is WASM, short for WebAssembly. It is a binary executable format for the web that makes JavaScript execution within the browser quite efficient.
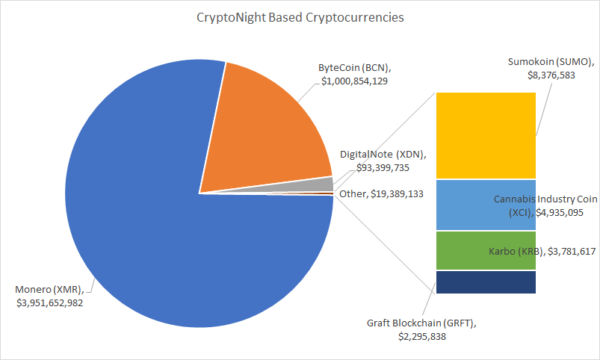
Fig. 1 CryptoNight based cryptocurrencies market capitalization, June 2018. Source: https://coinmarketcap.com
Infections
The security research blog Bad Packet Reports recently published an article that stated the presence of more than 100,000 sites that are currently infected with cryptojacking malware. Most of these sites seem to be compromised using an exploit for the Drupalgeddon 2. The attack exploits the vulnerability CVE-2018-7600, even after the patch has been available for several months already. [Side note: Always patch regularly!] There are reports of malware campaigns leveraging a recently released exploit for this vulnerability to compromise victims and inject coin mining scripts. Once a user visits these compromised sites, their system unwittingly contributes towards solving a crypto puzzle that benefits attackers.
To protect users from their computing resources being drained via unauthorized coin mining scripts running on your machine, one needs to block access to the following popular coin mining services:
- coinhive[.]com
- load[.]jsecoin[.]com
- crypto-loot[.]com
- coin-have[.]com
- ppoi[.]org
- cryptoloot[.]pro
- papoto[.]com
- coinlab[.]biz
Qualys BrowserCheck CoinBlocker Extension for Google Chrome
Based on extensive research from Qualys Malware Research Labs, we are announcing Qualys BrowserCheck CoinBlocker, a new Google Chrome browser extension to protect users from browser-based coin mining attacks.
Here are a few screenshots of Qualys BrowserCheck CoinBlocker in action:
Fig. 2 Qualys BrowserCheck CoinBlocker
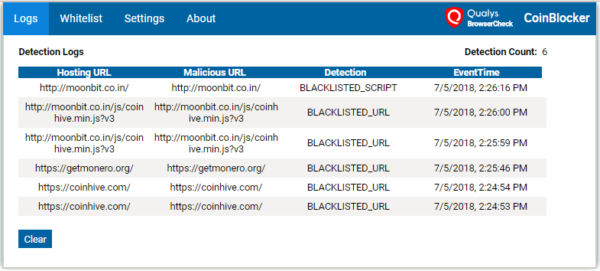
Fig. 3 Qualys BrowserCheck CoinBlocker Detection Logs
Qualys BrowserCheck CoinBlocker Extension relies not only on the domain blacklist but also uses heuristics to identify underlying cryptomining algorithms like CryptoNight (used for mining Monero) and its various artifacts.
Detecting Traditional Cryptomining Threats
Additionally, cryptomining is not just limited to browser-based scripts as we have seen certain attackers infect systems with a persistent malware that runs outside of a browser to perform cryptomining. To help detect such malware, security professionals can use Qualys Indication of Compromise (IOC) solution to gain 2-second visibility into coin mining and other malware across their entire organization. Qualys IOC includes behaviour-based malware family detection for the following coin mining threats:
- CryptoMinerA
- CryptoMinerB
- CryptoMinerC
- CryptoMinerD
- CryptoMinerE
- Neksminer
Cryptomining is a rising online threat that is expected to grow as digital currencies and blockchain technologies are getting wider acceptance. Attacker are employing various techniques to use unsuspecting users’ systems for malicious purposes. We advise our users to regularly scan systems for vulnerabilities using tools like Qualys BrowserCheck. Stay protected online from crypto-mining attacks with Qualys BrowserCheck CoinBlocker Chrome extension.
Hello team, this is a wonderful product. With the advent of bitcoin business and the increase in the users following bitcoin and related crypto products, I think it’ll be great if you could launch a video on how your product works and publish it on youtube or similar websites. This will be very helpful for a general user who doesn’t know why and how their machines become slaves to cryptojacking or mining.