Security News: Hackers Aim Ransomware at Big Cos., as Experts Call for Swift Patching of Struts Bug
Ransomware raids aimed at specific targets with big pockets. Another Struts vulnerability — but scarier than last year’s. An Android spyware that records your phone calls. These are some of the security news that have caught our attention.
New Struts Bug Should Be Patched Yesterday
 Apache patched a serious remote code execution vulnerability (CVE-2018-11776) affecting all supported versions — 2.3 to 2.3.34 and 2.5 to 2.5.16 — of the widely used Struts Java application framework. The bug is considered more dangerous than the one disclosed last year in Struts that was exploited in the massive data breach at Equifax.
Apache patched a serious remote code execution vulnerability (CVE-2018-11776) affecting all supported versions — 2.3 to 2.3.34 and 2.5 to 2.5.16 — of the widely used Struts Java application framework. The bug is considered more dangerous than the one disclosed last year in Struts that was exploited in the massive data breach at Equifax.
In the Apache security bulletin, the vulnerability is rated “Critical” and users are advised to immediately upgrade to Struts 2.3.35 or Struts 2.5.17.
The remote code execution becomes possible “when using results with no namespace and in same time, its upper action(s) have no or wildcard namespace” and “when using url tag which doesn’t have value and action set,” the bulletin reads.
Organizations should upgrade to the patched Struts versions even if their applications aren’t vulnerable to this bug. “An inadvertent change to a Struts configuration file may render the application vulnerable in the future,” stated Semmle, whose security researcher Man Yue Mo discovered this vulnerability.
Upgrading should take first priority, considering that Struts is widely used for public web apps, vulnerable systems are easy to identify, and the bug is easy to exploit, according to the company.
“A hacker can find their way in within minutes, and exfiltrate data or stage further attacks from the compromised system. It’s crucially important to update affected systems immediately; to wait is to take an irresponsible risk,” said Pavel Avgustinov, a Semmle VP.
Writing in the Qualys blog, Product Management Director Jimmy Graham noted that the vulnerability does not exist with a default configuration of Struts, but that “it does exist in commonly seen configurations for some Struts plugins.”
“Due to the ease of exploitation and relatively common configuration that is required, this vulnerability should be patched immediately for all applications that use Struts 2,” Graham wrote. Qualys has defined two QIDs to detect this vulnerability (QID 13251 and QID 371151), and created dynamic dashboards to visualize it.
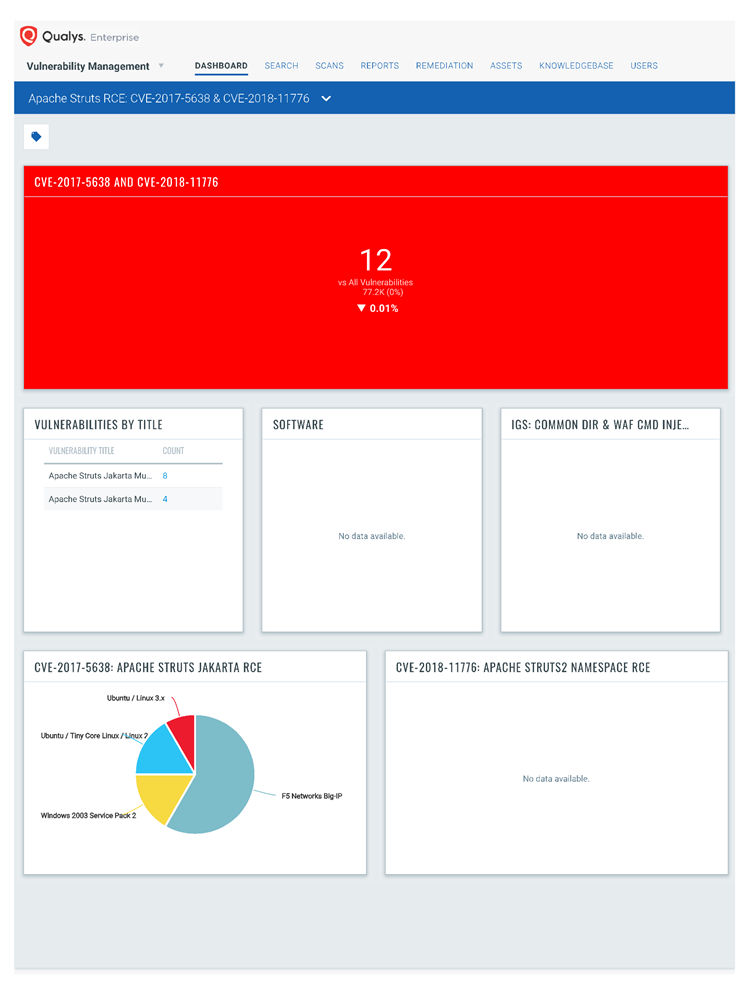
Graham also describes how the Qualys Web Application Firewall (WAF) can mitigate the vulnerability.
More information:
Apache Struts 2 namespace Remote Code Execution Vulnerability: CVE-2018-11776 (Qualys)
Apache Struts 2 Flaw Uncovered: ‘More Critical Than Equifax Bug’ (ThreatPost)
Admins Urged: Stop Everything and Patch New Apache Struts Flaw (InfoSecurity)
Experts Urge Rapid Patching of ‘Struts’ Bug (Krebs on Security)
PoC Code Surfaces to Exploit Apache Struts 2 Vulnerability (ThreatPost)
Ransomware Campaign Attacks Selected Organizations
 Cyber thieves recently began attacking handpicked corporations with ransomware and demanding skyhigh bitcoin payments.
Cyber thieves recently began attacking handpicked corporations with ransomware and demanding skyhigh bitcoin payments.
The criminals are deliberately targeting specific large businesses, and they’re using ransomware called Ryuk that’s designed for tailored attacks. They reportedly netted more than $600,000 during the campaign’s first two weeks.
“Its encryption scheme is intentionally built for small-scale operations, such that only crucial assets and resources are infected in each targeted network with its infection and distribution carried out manually by the attackers,” CheckPoint researchers wrote.
The implication is that prior to each attack, “extensive network mapping, hacking and credential collection” is conducted by the miscreants, believed to have ties to the notorious hacker collective Lazarus Group and be experienced in targeted attacks, according to the researchers.
More information:
This new ransomware campaign targets business and demands a massive bitcoin ransom (ZDnet)
Ryuk Ransomware Emerges in Highly Targeted, Highly Lucrative Campaign (ThreatPost)
Ryuk Ransomware Crew Makes $640,000 in Recent Activity Surge (BleepingComputer)
T-Mobile Hacked, Millions Affected
Personal information of 2 million T-Mobile customers, including encrypted passwords, may have been accessed by hackers via a breached API on August 20.
The compromised data may have included names, billing zip codes, phone numbers, email addresses, and account numbers, but not financial information nor Social Security numbers, according to the company. T-Mobile hasn’t provided further details on the nature of the attack.
On related news, customer security PINs from T-Mobile and AT&T were found to be accessible due to unrelated flaws in partners’ websites, according to BuzzFeed. Apple’s online store exposed the T-Mobile data, while the website of phone insurance company Asurion exposed AT&T’s data. Both companies fixed the flaws after being alerted to them.
Access to a mobile account PIN could let a hacker “easily commandeer your phone number and use it to trick the SMS-based authentication designed to verify your identity when you log on to your bank, email provider, or social media accounts,” wrote Nicole Nguyen in BuzzFeed.
Meanwhile, a security researcher was able to enter a Sprint employee portal protected by weak credentials, and said customer data could have been accessed.
More information:
Passwords Part of Data Breach, T-Mobile Admits: What to Do Now (Tom’s Guide)
Why T-Mobile’s Data Breach Should Be a Wake-Up Call (Motley Fool)
2 Million T-Mobile Customers Are Hit by a Data Breach (Consumer Reports)
T-Mobile, AT&T customer account PINs were exposed by website flaws (Engadget)
Android Malware Records Calls, Takes Videos
 Malware that infects Android devices and conducts extensive snooping has been discovered bundled in a malicious app that mimics a legitimate one.
Malware that infects Android devices and conducts extensive snooping has been discovered bundled in a malicious app that mimics a legitimate one.
Called Triout, the spyware stealthily can record phone calls, log incoming text messages, take videos, snap photos, collect location data and transmit everything it collects to a command and control center, according to Bitdefender, which discovered it.
“The malware was first observed lurking in an app, repackaged to look identical to a legitimate Android app called ‘Sex Game.’ It was available in the Google Play store starting in 2016, but has since been removed,” a ThreatPost article reads.
More information:
Android ‘Triout’ spyware records calls, sends photos and text messages to attackers (CSO)
This Android spyware records calls and sends your pictures and location to hackers (ZDnet)
New Android Triout Malware Can Record Phone Calls, Steal Pictures (BleepingComputer)
In Other News …
- Cyber thieves stole payment card information from Cheddar’s Scratch Kitchen restaurants in 23 U.S. states for two months late last year, potentially affecting almost 600,000 customers.
- Apple was hacked by a 16-year old Australian boy who told authorities he dreamed of working at the company.
- Adobe issued out-of-band fixes for remote code execution vulnerabilities in Photoshop CC, barely a week after its scheduled monthly set of patches.
- Spyfone, a company that lets parents and employers monitor mobile devices, left an AWS S3 storage bucket unprotected, exposing all manner of personal data from thousands of customers.