Detecting Apache Struts 2 Namespace RCE: CVE-2018-11776
Table of Contents

A new remote code execution vulnerability in Apache Struts 2, CVE-2018-11776, was disclosed yesterday. While this vulnerability does not exist with a default configuration of Struts, it does exist in commonly seen configurations for some Struts plugins.
Update August 24, 2018: A dashboard for this vulnerability is now available to download.
The Vulnerability
Struts improperly validates namespaces, allowing for OGNL injection, and can lead to full remote code execution on the target system. For a more detailed technical look at the vulnerability, please see our Threat Protection blog on this topic. Struts versions 2.3.34 and 2.5.16 and before are impacted.
Recommended Response
Due to the ease of exploitation and relatively common configuration that is required, this vulnerability should be patched immediately for all applications that use Struts 2. Patched versions are Struts 2.3.35 and 2.5.17. A publicly available PoC has already been published, and active attacks against this vulnerability are most likely imminent.
Detections
Vulnerabilities in application frameworks are challenging to programmatically detect with traditional VM scanning, and multiple methods of detection are needed to ensure that Struts is found.
Because of this, Qualys has implemented two QIDs for detecting CVE-2018-11776 in Qualys Vulnerability Management:
- QID 13251 – This detection includes both remote and authenticated checks:
- Remote – This detection sends a specifically crafted payload in the request to check for command execution in .action, .go, .do, .jsp and .xhtml files under common web directories.
- Authenticated (Linux/Unix) – This executes ps -ef command, looks for the presence of the Tomcat process and finds the location of struts2-core-x.jar file. We are investigating using this method on other middleware technologies.
- QID 371151 – This authenticated scan detection uses our Tomcat auth to specify the location of the Tomcat configuration file. Once a Tomcat auth record is added, this detection reads the Tomcat location from the config and searches for struts-core.x.jar file under sub directories. It extracts the version from .jar file and compares with vulnerable Struts versions.
- Both QIDs are included in Vulnerability Signatures version VULNSIGS-2.4.403-3 or later
Qualys has also implemented a QID for detecting CVE-2018-11776 in Qualys Web Application Scanning:
- QID 150250 – This is an active detection within WAS that sends a specially-crafted payload to the scanned web application. A vulnerable application will show evidence of a command executing on the server and QID 150250 will be reported.
In addition to scanning, Qualys recommends that application frameworks such as Struts be documented in an Application Portfolio or CMDB to ensure all components of an application are recorded and can be audited for these kinds of vulnerabilities.
Protection
Even prior to the disclosure of this RCE vulnerability, Qualys Web Application Firewall users were already protected from exploits by every possible out-of-the-box template and generic policy. These templates, developed by security experts for Qualys WAF programmable inspection engine, are constantly tested against latests threats for the best detection rate and least false-positives.
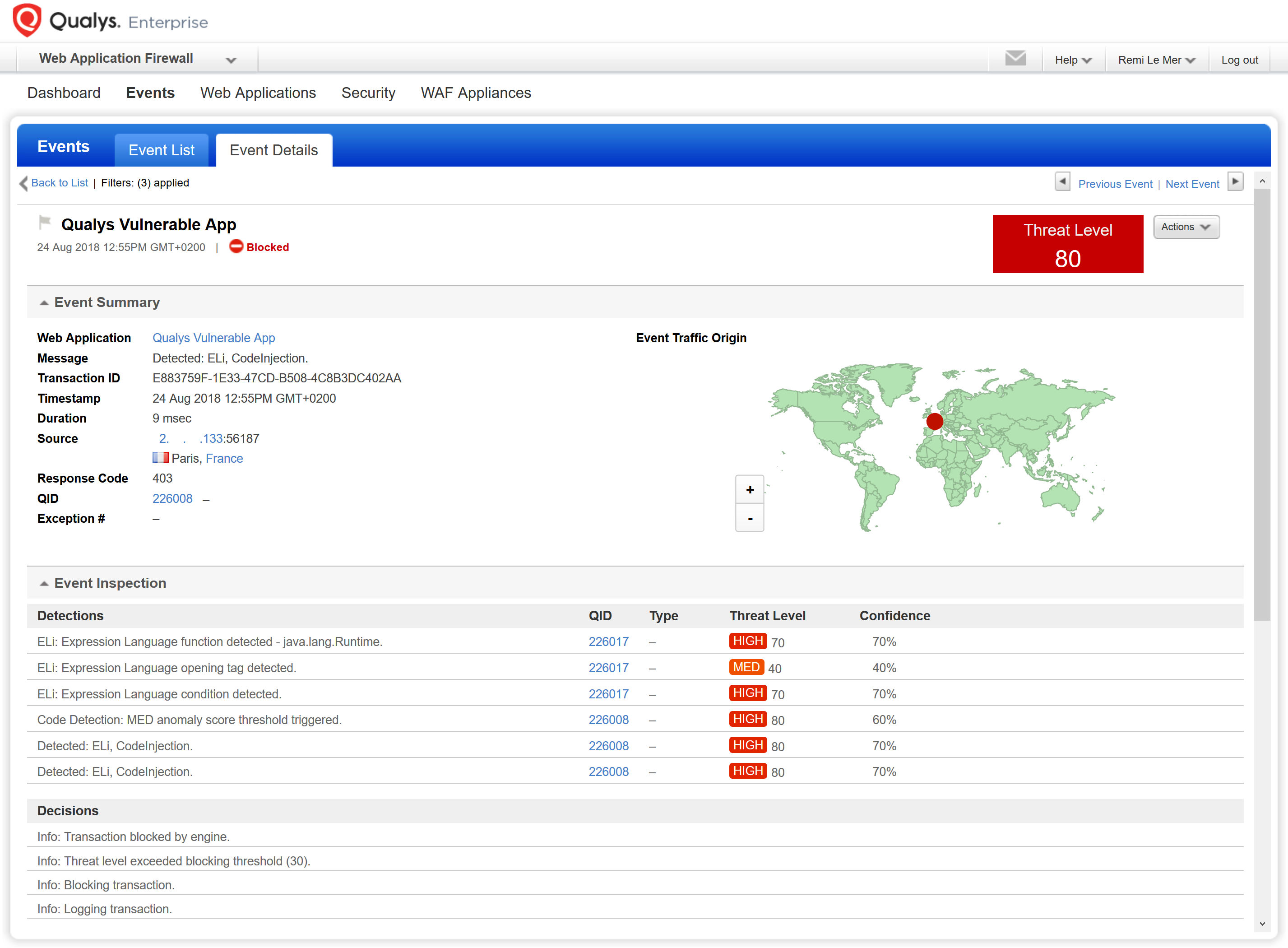
Customers using manual policies instead of templates were potentially not protected though, depending on ELI (Expression Language Injection), CI (Code Injection) and RCE (Remote Command Execution) sliders settings, along with the blocking threshold.
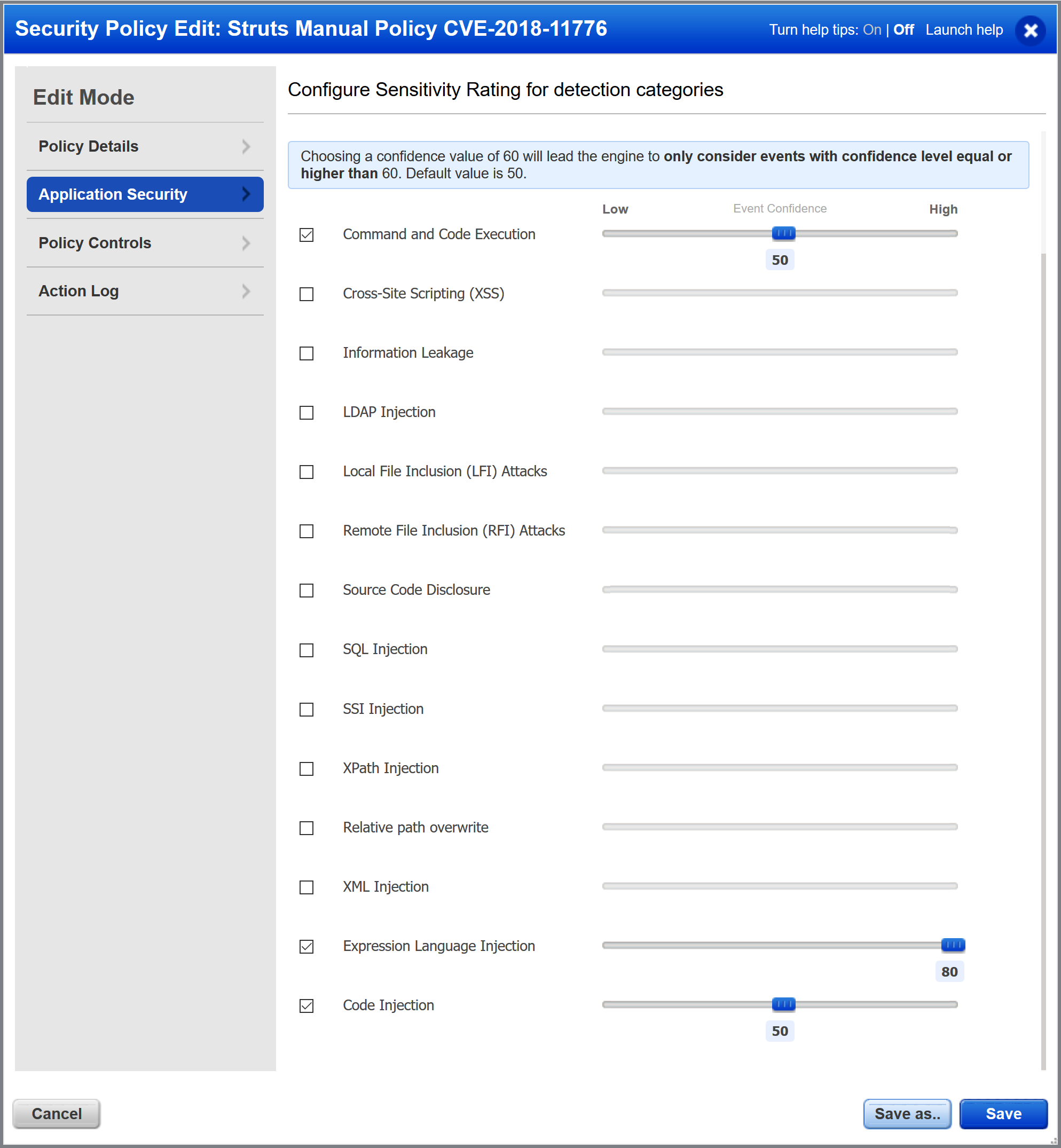
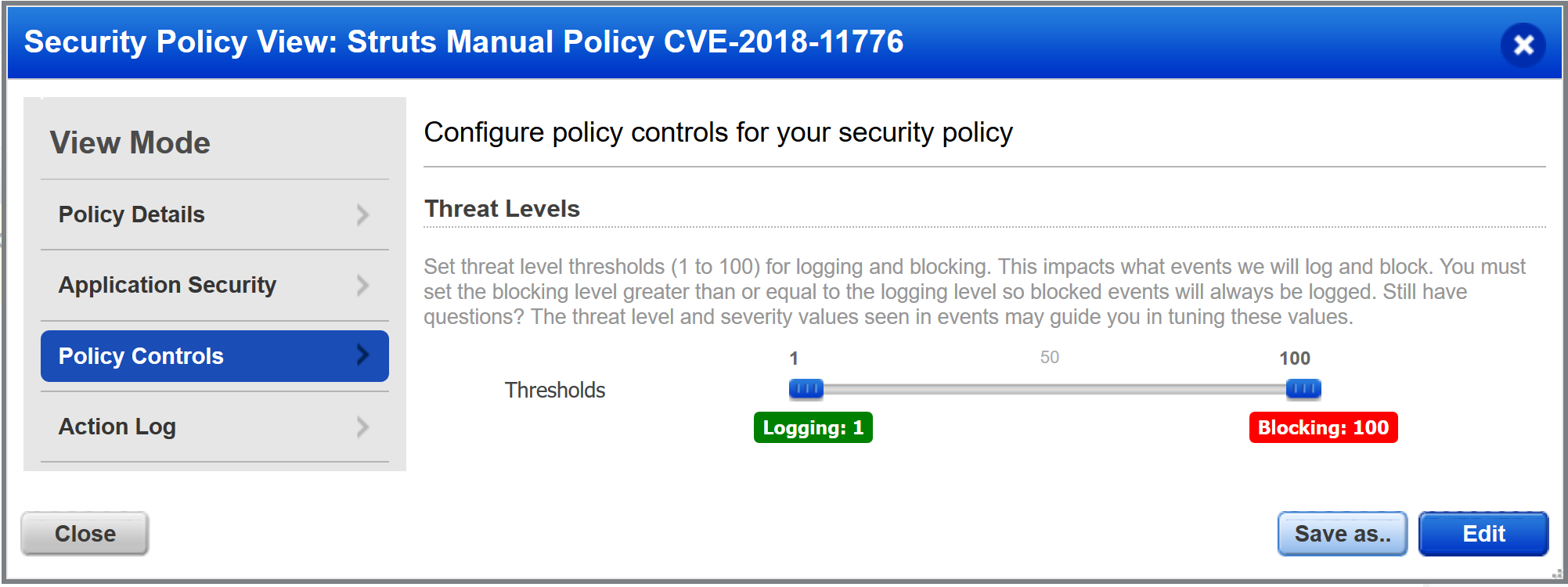
Mitigating CVE-2018-11776 is possible by using the following methods:
- native protection using a generic policy (QID-226017: Expression Language Injection and QID-226008: Remote Command Execution)
- for those using a manual policy instead of an out-of-the-box template, you can alternatively create a custom rule with the following condition: request.path DETECT “qid/150178”
- or of course, by applying a virtual patch to QID-150250 from within the WAS module ; which is equivalent to creating the rule manually, but quicker.
Today’s example – like “drupalgeddon2” a few months ago (CVE-2018-7600) – demonstrates how blocking zero-days is possible with Qualys WAF, without needing to define manual rules, giving CISO and IT Security organizations time for implementing sustainable fixes, while providing them with a tool to monitor and report any attempt to exploit the vulnerability.