Securing Container Deployments with Qualys
With container adoption booming, security teams must protect the applications that DevOps teams create and deploy using this method of OS virtualization. The security must be comprehensive across the entire container lifecycle, and built into the DevOps pipeline in a way that is seamless and unobtrusive.
Accomplishing this requires an understanding of Docker container technology and the adoption of processes and tools tailored for these environments. In a recent webcast, Qualys Director of Product Management Hari Srinivasan, an expert on cloud and container security, outlined container security risks, use cases, and best practices.
Read on to learn about Srinivasan’s recommendations for gaining visibility into container assets, doing vulnerability analysis, and detecting drifting runtimes across your DevOps pipeline.
DevOps benefits, security challenges
Because they package an application and its dependencies without a guest OS, containers offer developers key advantages over VMs. For example, applications can be developed more quickly, are more lightweight and portable, and can be spun up and down faster. They also run consistently regardless of underlying computing environments. Containers can be run within virtual machines or on “bare metal” servers, and in clouds or on-premises.
All of these characteristics make containers “extremely interesting for DevOps teams,” he said.
In particular, containers are ideal for microservices, a popular architecture in which applications are structured as independent, small, and modular services. Unsurprisingly, by 2020 more than 50% of global organizations will be running containerized applications in production, up from less than 20% in 2017, according to Gartner. However, containers create their own security and compliance issues. In fact, security is the biggest challenge cited by organizations deploying containers, according to Forrester.
Container security issues include the use of un-validated software from public repositories, which often has unpatched vulnerabilities, and the deployment of containers with weak configurations, Srinivasan said. In addition, containers communicate directly with each other via exposed network ports in a way that bypasses host controls, and they are hard to track because they’re so ephemeral. Organizations also often lack proper governance to prevent unauthorized access to container environments.
“These are primary threats around containers,” he said.
Container security goals
As they map container security plans, security teams should pursue four main goals.
- Obtaining visibility across their container environment by discovering and tracking all deployments — on-premises and in clouds. “If you gain visibility about where your containers are deployed, you’ll be able to track the sprawl and scale of this container environment,” Srinivasan said.
- Manage vulnerabilities within containers, making sure your tool keeps false positives to a minimum, and prevent and detect intrusions.
- Choose container security tools that are adaptive and can be integrated with DevOps products via REST APIs or custom plug-ins.
- Rethink patching, because vulnerable containers are instead terminated and replaced.
When choosing a container security tool, organizations will find three different options.
The first type of tool is deployed within Docker hosts as an agent. This isn’t a good option if the security team lacks access to the host, which is often the case in public cloud environments, Srinivasan noted.
Then there are tools that are deployed within a container as a daemon or agent, but this option isn’t always favored by developers.
The third model — Qualys’ choice — are tools that deploy as “side-car” containers, running across every host alongside other containers. “This is adaptable and suitable for a wide range of environments,” he said.
Protecting the container pipeline with Qualys Container Security
The Qualys Container Security (CS) application gives security teams continuous discovery, tracking, and protection of containers in DevOps pipelines and deployments at any scale.
It has a native container sensor that can be downloaded as a Docker image and deployed as a side-car container on every Docker host. Since it is available as a Docker image, it can be managed easily with container orchestration tools and deployed across all the nodes of the cluster automatically.
With Qualys CS, organizations can protect all phases of container deployment — the build, ship, and runtime stages.
Build
“In the build phase, the primary goal from a security standpoint is to avoid having vulnerable images, or images with conflicts, from entering your repository,” he said.
This is especially important for images pulled wholly or in part from a public repository, a common developer practice.To keep unsafe images out of repositories, Qualys CS enables DevSecOps teams perform vulnerability analysis via REST APIs or via custom plug-ins for CI/CD tools.
Qualys CS has a plug-in for Jenkins, and soon will for other such tools including Bamboo, Microsoft VSTS, Git Lab, TeamCity, and CircleCI, Srinivasan said. After downloading the plug-in, the security team establishes “fail” thresholds for images, such as the presence of a specific vulnerability, or of any vulnerability above a certain severity level.
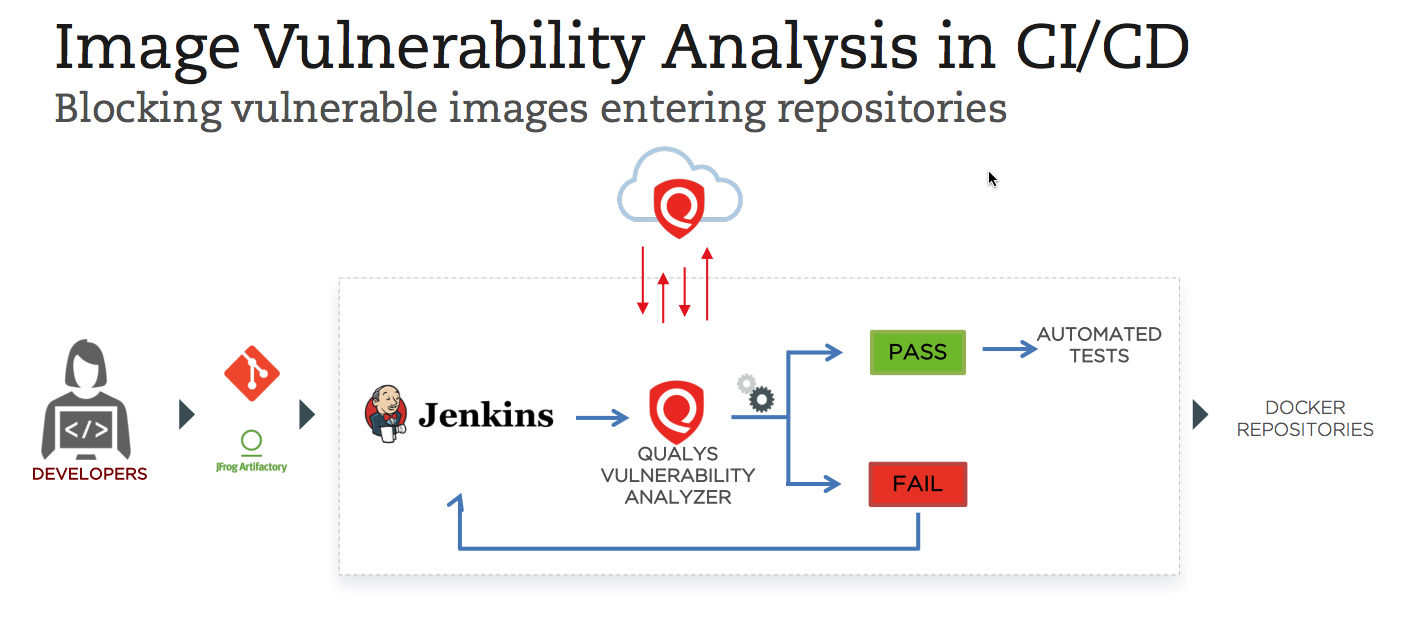
Developers get automatically notified if the image fails, and can access detailed information about the vulnerability for fixing the issue. “Developers have actionable data directly in the build environment itself, so they don’t need to leave their console. They have this information to remediate and update their image,” he said.
The security team can configure the security controls for Jenkins environments globally via the policy rules feature in their Qualys portal.
Ship
In this phase, organizations should inventory and scan for vulnerabilities the images already in their registries, which host and distribute images, and in their repositories, which are collections of related images.
With Qualys CS, organizations can inventory and scan images on on-premises registries like Artifactory and Nexus, and on cloud-based registries like the ones from Amazon AWS, Microsoft Azure and Google Cloud.
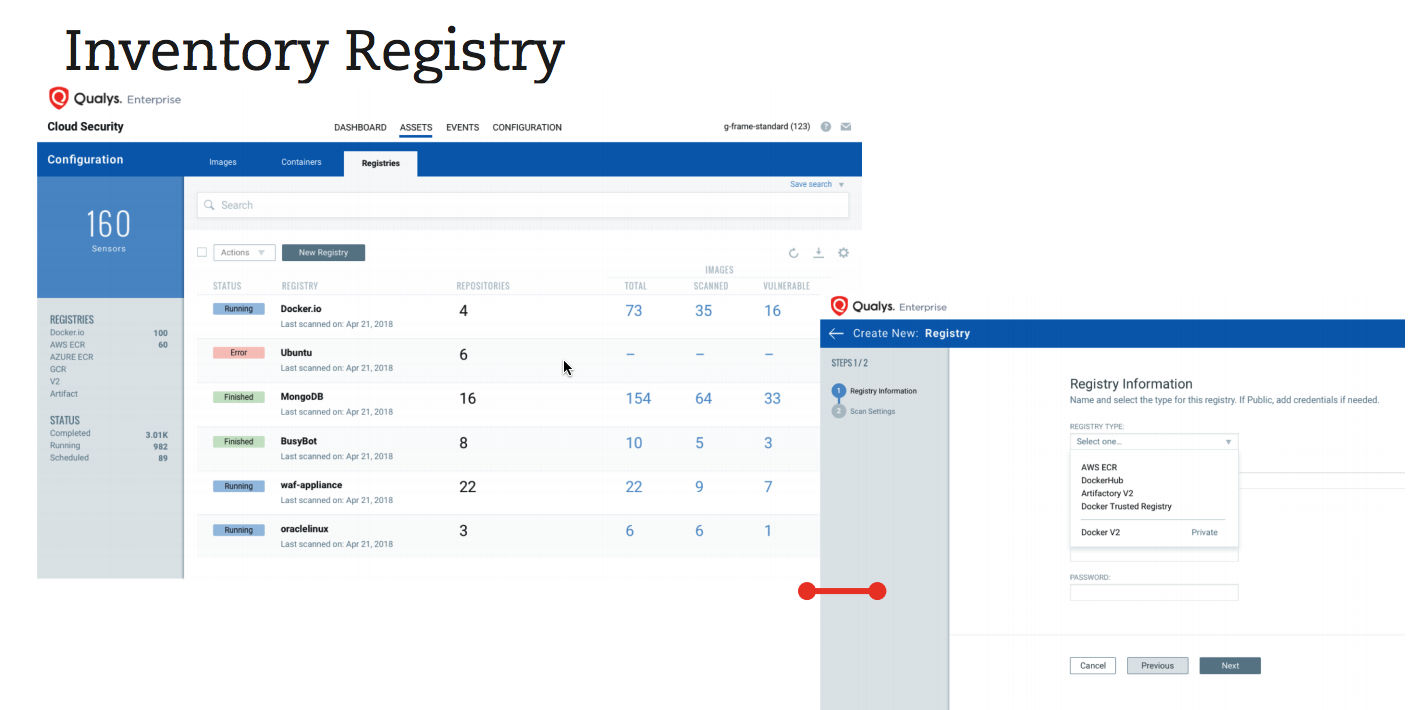
It’s important to schedule automated daily scans to detect newly-disclosed vulnerabilities and to check the new images being added to the repositories. That way, organizations can make sure they are “enforcing the standards to check for any new vulnerabilities that might creep into the process, or at the same time to ensure that anything in flight isn’t modified when the image moves from the build to the registry,” Srinivasan said
Another best practice is to check that images come from sources that are trusted and reputable, and that keep their images current and scrubbed of disclosed vulnerabilities. It’s recommended to use notary services to sign images and ensure only trusted images are being used in your environment.
Qualys CS will have support for adding policies to let users mark trusted repositories and registries, and flag and enforce any deviation from that policy.
“This will ensure that whatever you ship is what’s being run on your host, and at the same time providing you with the visibility into what registries are being used by your company, and what images are part of that registry,” he said.
Runtime
When container images are available for production use, it’s critical to have visibility and continuous monitoring of runtime environments, as well as to prevent and respond to breaches.
With Qualys CS, organizations can detect vulnerable containers, identify where they are, and assess their potential impact based on how widespread they are in the environment.
A key here is to flag containers already running on the system that are breaking off from the “immutable” behavior of their parent image, which could indicate a breach. As is well known, containers follow the image, so it’s key to identify the behavior of the containerized application and detect suspicious deviations, such as unexpected system calls, processes and communications.
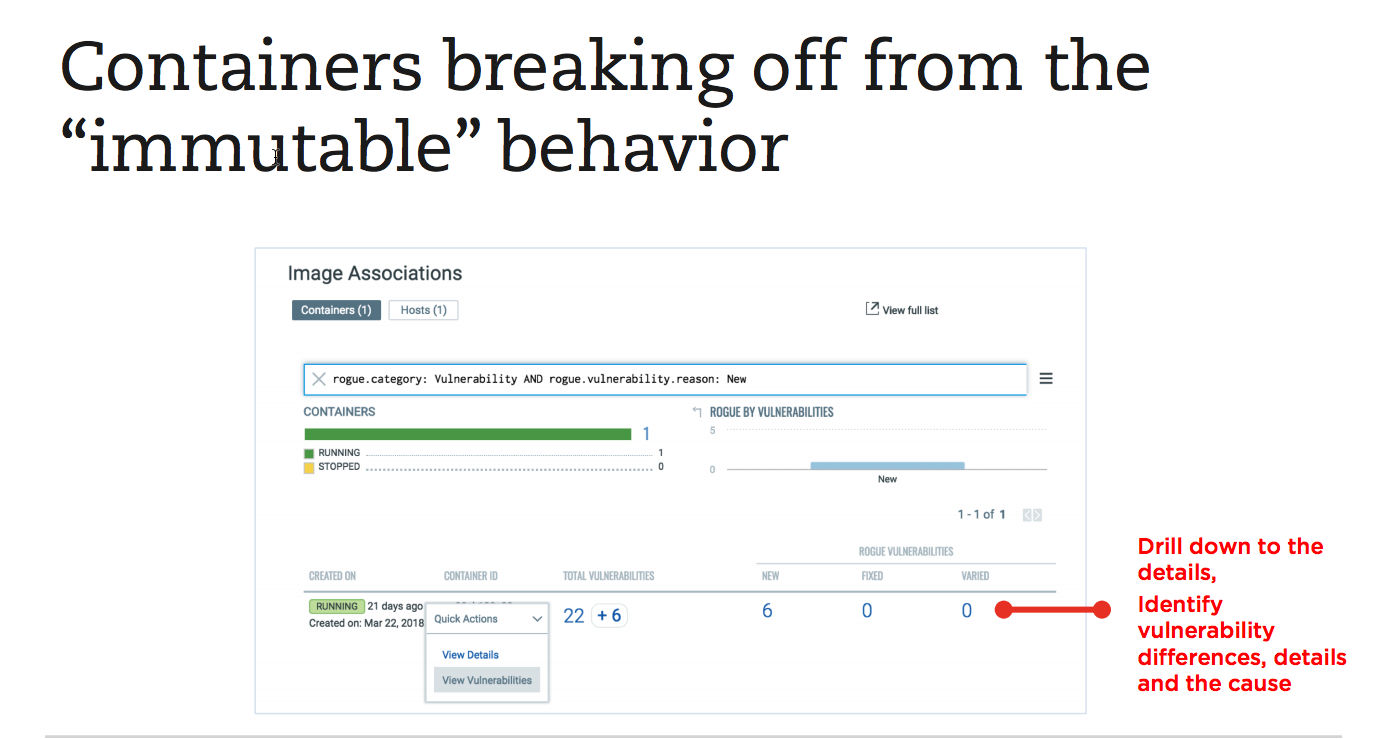
Qualys CS enables security teams to enforce countermeasures, such as blocking or quarantining these containers, and drill down into the details of the anomalies to understand the issues, Srinivasan said.
Qualys CS also lets security teams validate images against security policies, and block unapproved images from being spun up as containers through integration with orchestrators.
Secure your container environments with Qualys
We hope this post has helped you better understand the particular security challenges of containers, and how Qualys CS can help you address them throughout their lifecycle:
- Blocking vulnerable images from entering repositories during the build phase;
- Securing images pushed to your registries in the ship phase;
- And scanning in production during the runtime phase to identify and manage compromised containers.
“We provide complete coverage across your environment: build, ship and runtime,” Srinivasan said.
Please watch a recording of the webcast, in which Srinivasan provides a lot more details, gives a demo of Qualys CS, and answers questions from the audience.